Apache Tomcat存在路径等价漏洞(CVE-2025-24813),利用反序列化未信任数据允许上传任意文件并执行远程代码。攻击需特定配置但常见,建议升级至11.0.3、10.1.35或9.0.99版本以修复。 2025-3-19 19:6:51 Author: www.horizon3.ai(查看原文) 阅读量:6 收藏
Apache Tomcat Path Equivalence Vulnerability
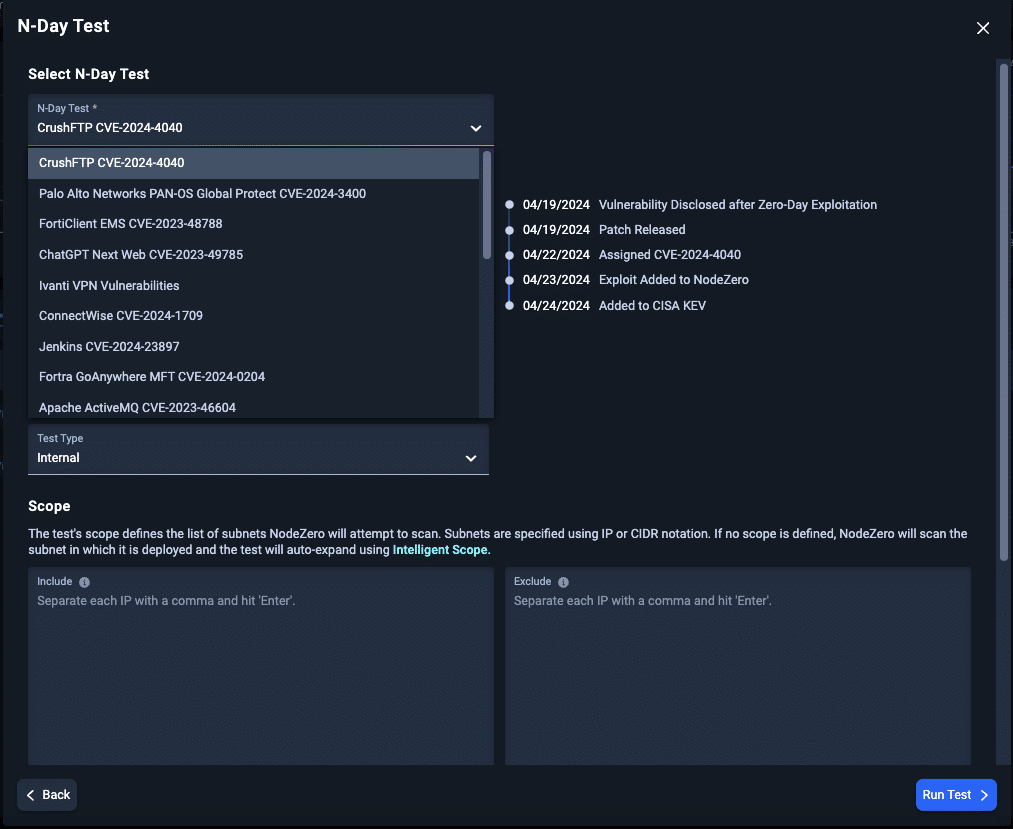
A Rapid Response card and targeted test have been released for CVE-2025-24813 against Apache Tomcat. The vulnerability uses deserialization of untrusted data that enables an unauthenticated attacker to upload arbitrary files and potentially perform remote code execution. The attack requires a non-default configuration of Apache Tomcat but the configuration changes are common enough that it is being actively exploited in the wild.
Recommended mitigations are to update to Apache Tomcat versions 11.0.3, 10.1.35 or 9.0.99 depending on the version currently deployed in the client environment.
Rapid Response N-Day Testing
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
如有侵权请联系:admin#unsafe.sh
