Trustwave SpiderLabs发现网络攻击者利用虚假CAPTCHA验证诱骗用户执行恶意PowerShell脚本,通过多阶段过程部署信息窃取软件如Lumma和Vidar。 2025-3-12 17:3:0 Author: www.trustwave.com(查看原文) 阅读量:24 收藏
4 Minute Read
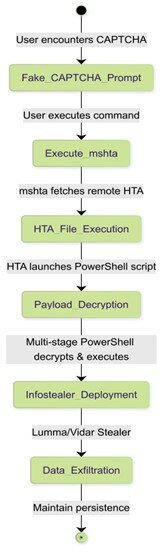
During an Advanced Continual Threat Hunt (ACTH) investigation in early February 2025, Trustwave SpiderLabs discovered a resurgence of fake CAPTCHA verifications designed to deceive victims into executing malicious PowerShell scripts. This campaign employs a multi-stage PowerShell execution process, ultimately delivering infostealers such as Lumma and Vidar. SpiderLabs comprehensively analyzed the attack chain, covering the initial infection vectors, staged payload execution, and decryption mechanisms. These instances are also not the first time the team has investigated the malicious use of CAPTCHA. Earlier reports include Unveiling the CAPTCHA Escape: The Dance of CAPTCHA Evasion Using TOR and Dissecting a Phishing Campaign with a CAPTCHA-based URL. The attack begins when a user encounters a deceptive CAPTCHA verification on a compromised or malicious website. Instead of validating the user's identity, the CAPTCHA prompts the user to execute a PowerShell command. The attack starts with executing a PowerShell command, tricking the victim into believing it is part of a CAPTCHA verification process. The HTA file (RUKE.mp4) is executed using mshta, which then downloads and runs the next stage of the PowerShell script. This facilitates further infection and the execution of malicious payloads. An earlier investigation showed the adversary was agnostic when it came to the payload name and extension. The HTA file (RUKE.mp4) decrypts into a next-stage PowerShell script, which then downloads and executes additional payloads, advancing the infection chain. This Python script extracts the encrypted data by performing a simple subtraction cipher where each numerical value in the BSMz array is reduced by 634 to reveal the original character. The decrypted PowerShell command contains another staged PowerShell payload, which, when Base64-decoded, reveals yet another layer of PowerShell code, likely responsible for executing additional commands or downloading further payloads. The decoded PowerShell script dynamically retrieves and executes a method from the .NET Marshal class to decrypt SecureString data. Further decoding of the data reveals another PowerShell command that runs in hidden mode with the execution policy bypassed, dynamically retrieves a malicious URL, and downloads a payload using Net.WebClient, and executes it while obfuscating command names to evade detection. The decrypted PowerShell script retrieves and executes a staged PowerShell code from https://60d427489[.]kliplubuziy[.]shop/e290ec7eeb84ea465f4d2e1441fec32d[.]stage. It’s important to note that the site where the PowerShell code is staged differs in each campaign. The retrieved PowerShell script is notably large in file size, suggesting an attempt to evade sandbox or emulation-based detection mechanisms, as many security solutions impose execution limits on script size to mitigate analysis. The XOR key in this function is stored in $GZluzrkhPzWWrrywFFx, which is converted into a byte array ($TcOWXyfVrAsomtTr) using UTF-8 encoding. This key is then used in an XOR operation against the Base64-decoded payload ($nAGDWAuwiDTowy), producing the decrypted PowerShell script, which is stored in $SsiVDvLVzWszljN and returned for execution. During the investigation, we observed similar patterns of decryption routines in different campaigns. Based on our investigation, the decrypted XOR key is AMSI_RESULT_NOT_DETECTED. The decimal value of the same XOR key was observed in another campaign. Since we have the encrypted data and XOR key, with the help of the python code below, we can extract the final PowerShell payload: The final PowerShell script decodes and executes a Base64-encoded payload containing the Lumma Stealer malware, delivering and running the infostealer on the compromised system. The investigation of the final payload reveals Lumma Stealer not only exfiltrates sensitive data but also downloads additional infostealers, including Telegram bot-based HijackLoader. Further analysis confirms the delivery of a Golang-based backdoor, expanding the attack's persistence and control capabilities. The Golang-based HijackLoader is distributed through a malicious software package disguised as ‘TiVo Desktop’, a revoked signed executable. The package size of approximately 700MB strongly indicates a defense evasion tactic, likely aiming to bypass sandbox analysis and antivirus scanning by artificially inflating file sizes to hinder detection. File Hash Lumma Stealer: Vidar Stealer: HijackLoader: Network: MITRE Hunt Package Execution: Privilege escalation: Defense evasion: Credential access: Discovery: Command and Control: Trustwave's recent revamp of its Advanced Continual Threat Hunt (ACTH) with a new patent-pending methodology enables Trustwave to conduct threat hunts and monitor our customers as this campaign continues. Trustwave offers ACTH as an option in Trustwave's Managed Detection and Response Services. For more information, please read Trustwave Revamps Continual Threat Hunting Enabling Significantly More Hunts and Unique Threat Findings.Attack Chain Overview
Step-by-Step Execution
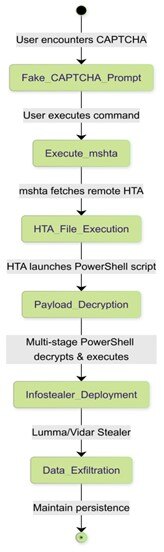
Figure 1. Step-by-Step Execution.Initial PowerShell Execution
Malicious PowerShell Execution Command
![]()
Figure 2. Malicious PowerShell Execution Command.
Figure 3.HTA File Execution and Decryption

Figure 4.Decryption Mechanism
Python-Based Decryption Logic
def decrypt_message(BSMz):decrypted_text = ''.join([chr(num - 634) if num >= 634 else '?' for num in BSMz])return decrypted_text# Given encrypted arrayBSMz = [charcode here]# Decrypt the messagedecrypted_message = decrypt_message(BSMz)print(decrypted_message)Multi-Stage PowerShell Decryption

Figure 5. Multi-Stage PowerShell Decryption.
Figure 6. The decoded PowerShell script dynamically retrieves and executes a method from the .NET Marshal class to decrypt SecureString data.
Figure 7.
Figure 8.
Figure 9.
Figure 10.
Figure 11.![]()
Figure 12.Final Routine to Drop Infostealers
import base64# Read and convert decimal data from the file# data.txt is the encoded decimal datawith open("data.txt", "r") as file:decimal_data = [int(x) for x in file.read().strip().split(',')]# Define XOR keyxor_key = b"AMSI_RESULT_NOT_DETECTED"# Convert to bytes and decode Base64decoded_data = base64.b64decode(bytes(decimal_data))# Apply XOR decryptiodecrypted_data = bytes(decoded_data[i] ^ xor_key[i % len(xor_key)] for i in range(len(decoded_data)))# Output the resultprint(decrypted_data.decode())Final Payload: Deployment of Lumma and Vidar Infostealers
![]()
Figure 13.Appendix
322579b54e4c6fecabeee9cdb75233d8d67ee7ae28a09bf7f6d33118a9d0752717190c7e5163b5c115e3d470f568ee5f218261DAA1AEBD5484B29BF7F959B57A188[.]114[.]97[.]3185[.]195[.]97[.]57191[.]101[.]230[.]18172[.]67[.]149[.]66hxxps[://]t[.]me/m08mbkhxxps[://]wirybringero[.]shop/apihxxps[://]farmagrupodw[.]com/temp/Elated[.]exehxxps[://]www[.]suarakutim[.]com/temp/wspconfig[.]rpmhxxps[://]www[.]suarakutim[.]com/temp/hosebird[.]rpmhxxps[://]steamcommunity[.]com/profiles/76561199724331900hxxps[://]steamcommunity[.]com/profiles/76561199820567237cryptocurrencytrends[.]clickguardeduppe[.]comtoppyneedus[.]bizT1053.005 - Scheduled Task/Job: Scheduled TaskT1059.001 - Command and Scripting Interpreter: PowerShellT1059.003 - Command and Scripting Interpreter: Windows Command ShellT1204.002 - User Execution: Malicious FileT1548.002 - Abuse Elevation Control Mechanism: Bypass User Account ControlT1036.003 - Masquerading: Rename System UtilitiesT1218.010 - System Binary Proxy Execution: Regsvr32T1562.002 - Impair Defenses: Disable Windows Event LoggingT1564.003 - Hide Artifacts: Hidden WindowT1552.001 - Unsecured Credentials: Credentials In FilesT1555.003 - Credentials from Password Stores: Credentials from Web BrowsersT1012 - Query RegistryT1033 - System Owner/User DiscoveryT1082 - System Information DiscoveryT1518 - Software DiscoveryT1614 - System Location DiscoveryT1071 - Application Layer ProtocolT1571 - Non-Standard PortT1102 - Web Service
如有侵权请联系:admin#unsafe.sh