2024年发现ICONICS Suite SCADA系统五个高危漏洞,影响10.97.2及更早Windows版本,可能导致权限提升、数据泄露或系统崩溃。Palo Alto Networks提供工业OT安全服务及Cortex系列工具应对威胁。 2025-3-7 16:3:35 Author: buaq.net(查看原文) 阅读量:4 收藏
Multiple Vulnerabilities Discovered in a SCADA System
2024年对ICONICS Suite SCADA系统进行安全评估,发现五个高危漏洞(CVE-2024-1182至CVE-2024-9852),影响版本10.97.2及更早Windows版本。这些漏洞可能导致权限提升、数据泄露或系统崩溃。Palo Alto Networks提供工业OT安全服务及Cortex系列工具以应对威胁。
2025-3-7 11:0:44
Author: unit42.paloaltonetworks.com(查看原文)
阅读量:9
收藏
Executive Summary
In early 2024 we conducted a security assessment of a Supervisory Control and Data Acquisition (SCADA) system named ICONICS Suite and identified five vulnerabilities in versions 10.97.2 and earlier for Microsoft Windows. We coordinated with the ICONICS security team, which released multiple security patches in 2024 to resolve some of these issues and published timely security advisories with workarounds for the rest.
Table 1 shows the five vulnerabilities.
| CVE Identifier | Vulnerability Description | Score |
| CVE-2024-1182 | DLL Hijacking in Memory Master Configuration (MMCFG) leading to Elevation of privileges. | 7.0 - High |
| CVE-2024-7587 | Incorrect Default Permissions vulnerability in GenBroker32, included in the installers for ICONICS GENESIS64 version 10.97.3 and prior, Mitsubishi Electric GENESIS64 version 10.97.3 and prior and Mitsubishi Electric MC Works64 all versions. Allowing an authenticated attacker to disclose or tamper with confidential information and data contained in the products, or cause a denial-of-service (DoS) condition. | 7.8 - High |
| CVE-2024-8299 | Uncontrolled Search Path Element vulnerability in ICONICS GENESIS64 all versions, Mitsubishi Electric GENESIS64 all versions and Mitsubishi Electric MC Works64 all versions allows a local authenticated attacker to execute a malicious code by storing a specially crafted DLL in the application’s folder. | 7.8 - High |
| CVE-2024-8300 | Dead Code vulnerability in ICONICS GENESIS64 version 10.97.2, 10.97.2 CFR1, 10.97.2 CRF2 and 10.97.3 and Mitsubishi Electric GENESIS64 version 10.97.2, 10.97.2 CFR1, 10.97.2 CRF2 and 10.97.3 allowing an authenticated attacker to execute a malicious code by tampering with a specially crafted DLL. | 7.0 - High |
| CVE-2024-9852 | Uncontrolled Search Path Element vulnerability in ICONICS GENESIS64 all versions, Mitsubishi Electric GENESIS64 all versions and Mitsubishi Electric MC Works64 all versions allows a local authenticated attacker to execute a malicious code and elevation of privileges by storing a specially crafted DLL in a specific folder. | 7.8 - High |
Table 1. CVEs found in ICONICS Suite.
ICONICS Suite is a SCADA solution suite that has hundreds of thousands of installations in over 100 countries. This suite is commonly used in critical infrastructure sectors such as:
- Government
- Military
- Manufacturing
- Water and wastewater
- Utilities & Energy
On unpatched ICONICS installations without any workarounds or remediations, these vulnerabilities could lead to escalation of privileges, DoS and in specific circumstances, even full system compromise:
- Attackers could perform DLL hijacking, by substituting legitimate ICONICS DLL files with malicious DLL files that have the legitimate files' names. This could potentially lead to arbitrary code execution, system integrity compromise and persistent attacker access.
- Attackers could escalate their privileges, gaining unauthorized access to restricted resources, executing malicious actions or even causing a DoS on the affected system.
- Attackers could manipulate critical files, modifying configuration settings or replacing legitimate binaries with malicious ones. This could potentially result in unauthorized access, data manipulation, elevation of privileges, trust relationship abuse or even full system compromise.
- In combination, these vulnerabilities pose a risk to the confidentiality, integrity and availability of a system.
Palo Alto Networks customers are better protected from the threats discussed in this post with the following products and services:
- Industrial OT Security is the Palo Alto Networks operational technology (OT) solution with security services that work within our Next-Generation Firewall (NGFW).
- Cortex XDR and XSIAM detect known and novel DLL hijacking attacks.
- Cortex Cloud can assist in identifying malware that uses DLL hijacking techniques.
- Cortex Xpanse can also provide customer visibility into externally exposed OT services and devices.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Vulnerabilities |
Technical Analysis
ICONICS Suite is used in numerous OT applications, including automation, data analysis and industrial internet of things (IIoT)/cloud integration. The following analysis details vulnerabilities discovered within the ICONICS Suite versions 10.97.2 and 10.97.3 for Windows platforms, which can compromise its effectiveness and security.
ICONICS Suite features a diverse range of servers, including the following:
- Building Automation and Control Networks (BACnet) server: BACnet is a data protocol designed to enable communication between different electronic devices (e.g., alarms, motion sensors, air conditioning units and heaters).
- Open Platform Communications (OPC) servers: OPC servers are used to facilitate communication between various software and hardware components, particularly in automation and industrial control systems.
- HTTP servers: HTTP servers provide connectivity and remote monitoring capabilities.
We found vulnerabilities in ICONICS Suite versions 10.97.2 and 10.97.3, and they may also exist in earlier versions. According to our telemetry from public internet scans, several dozen ICONICS servers are accessible from the internet, making them particularly vulnerable to attackers.
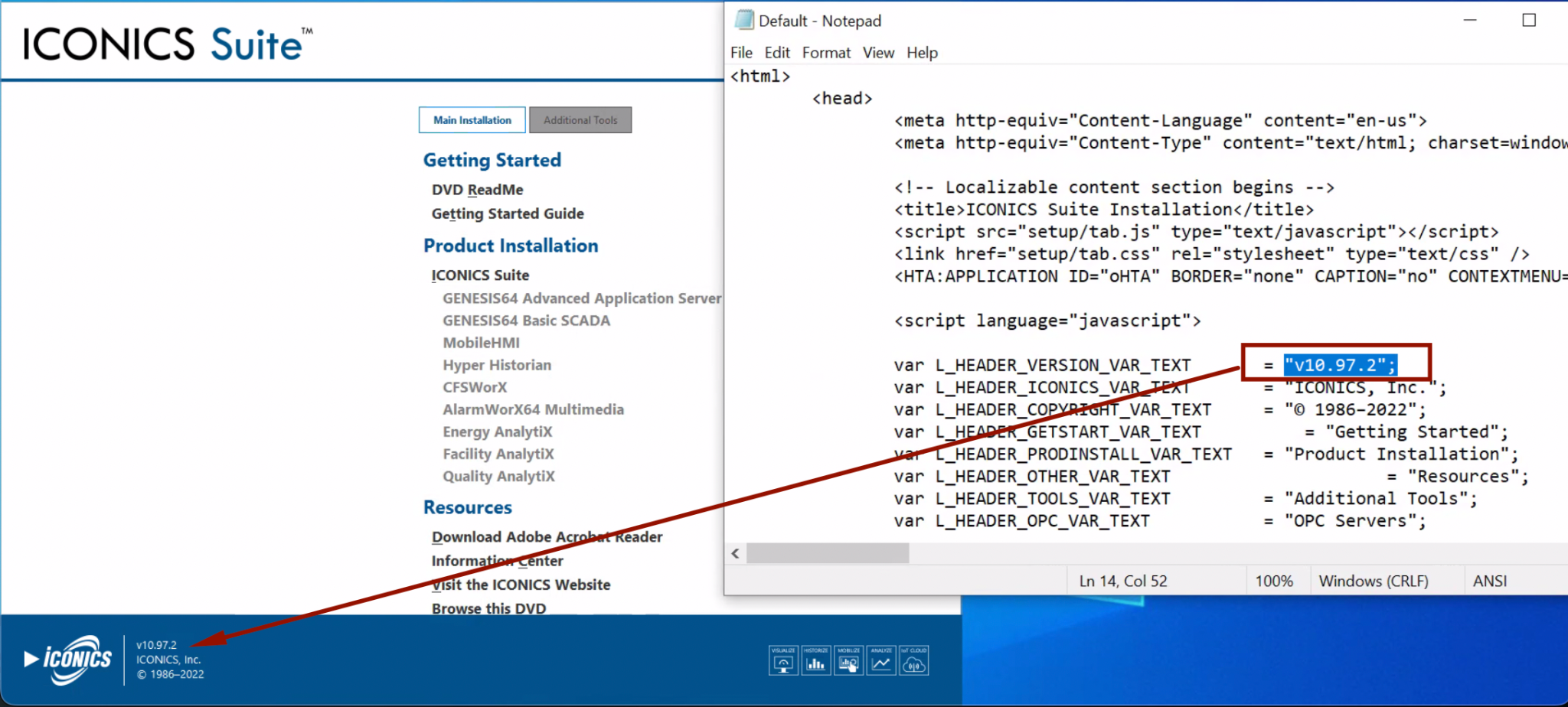
Figure 1 shows the welcome page for an installation of ICONICS Suite on a Windows host where it displays its version number.
Incorrect Default Permissions Vulnerability in GenBroker32 – CVE-2024-7587
GENESIS64 is a suite of tools that helps establish connectivity with OT device protocols like BACnet and Modbus. It also facilitates communication with OPC servers.
OPC servers enable various software packages, serving as OPC clients, to retrieve data from a process control device, like a programmable logic controller (PLC) or a distributed control system. However, ICONICS requires a GenBroker communications utility to communicate with legacy implementations of OPC servers.
GenBroker is part of the GENESIS32 and GENESIS64 software solutions. The GenBroker communications utility has a 32-bit version called GenBroker32 and a 64-bit version called GenBroker64.
GENESIS32 is currently at version 9.7 and contains the vulnerable GenBroker32 utility. For a variety of reasons, ICONICS recommends using GENESIS64 instead, and GENESIS64 uses the non-vulnerable GenBroker64 utility by default. Additionally, GenBroker32 should not be installed on top of GENESIS64.
However, a user could inadvertently add the vulnerable GenBroker32 utility during or after installing GENESIS64. This addition triggers permission changes in a critical directory containing key binaries and configuration files for the ICONICS Suite, resulting in overly permissive settings that grant system-wide user access to this directory.
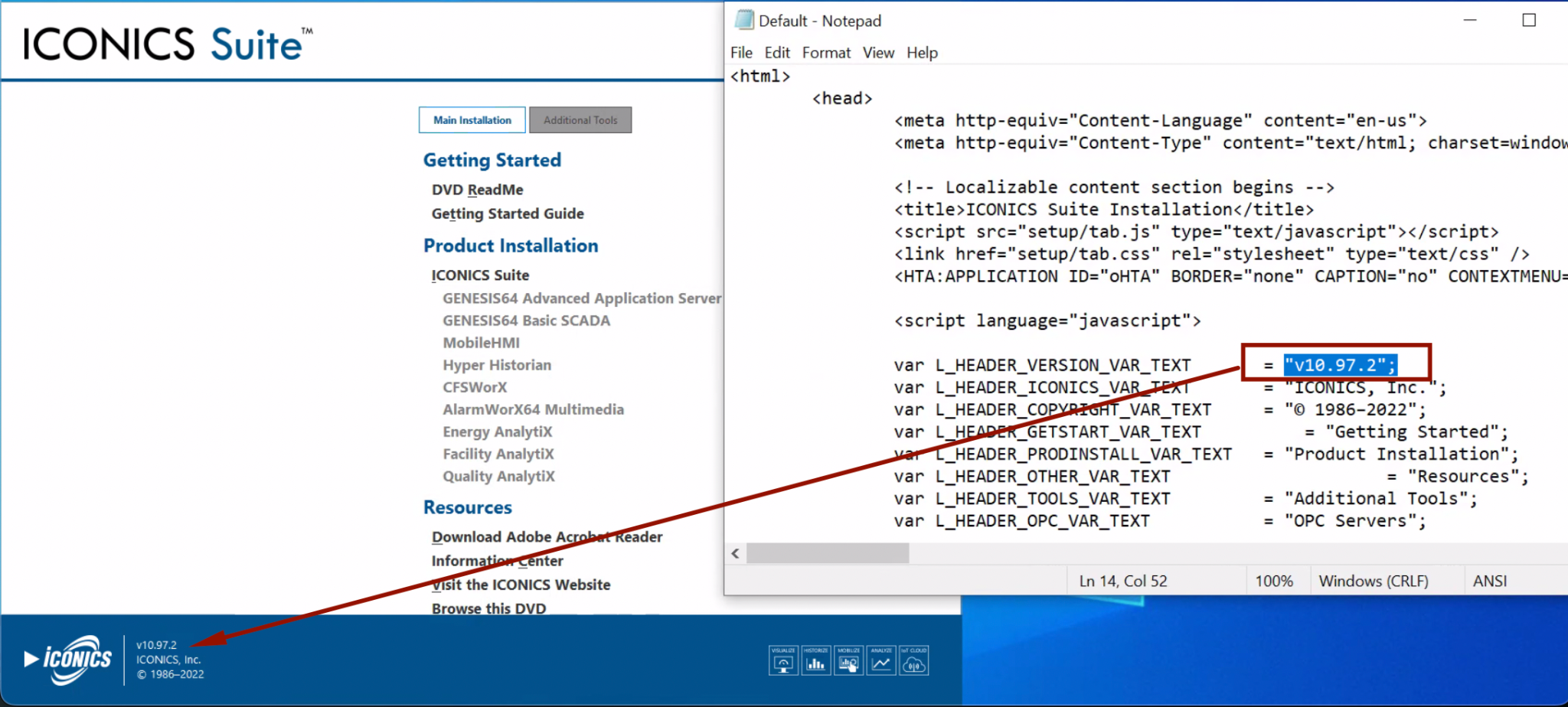
Figure 2 shows the version of GENESIS32 we installed during our security assessment.
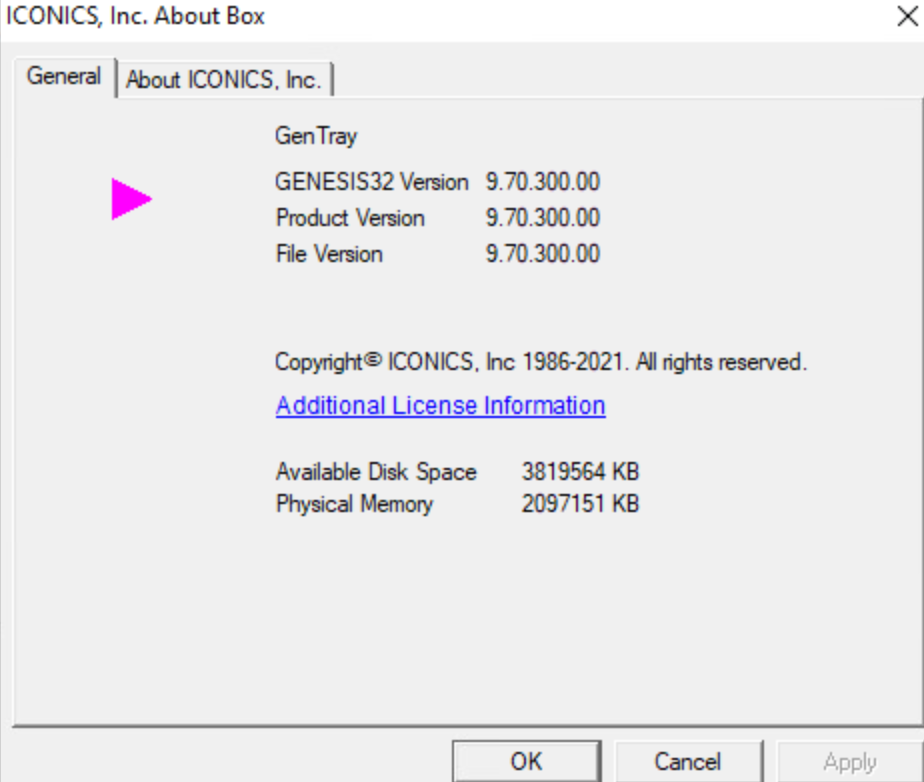
In our security assessment, after installing version 10.97.2 of the ICONICS Suite, the configuration page offered an option to install GenBroker, even when GenBroker64 was already installed. This option is labeled “GenBroker” and actually installed the vulnerable GenBroker32 utility. This GenBroker option did not indicate that GenBroker64 was pre-installed or that it would install the 32-bit version.
Users unaware of these details might inadvertently install GenBroker32. Figure 3 illustrates the associated GenBroker option available as an additional tool for an ICONICS Suite v10.97.2 installation on a Windows host.
We used a Windows installer package editor named Orca to inspect the ICONICS MSI file that installs GenBroker32.
Figure 4 shows the GenBroker32 installer ICONICS GenBroker.msi in Orca to view the LockPermissions table.
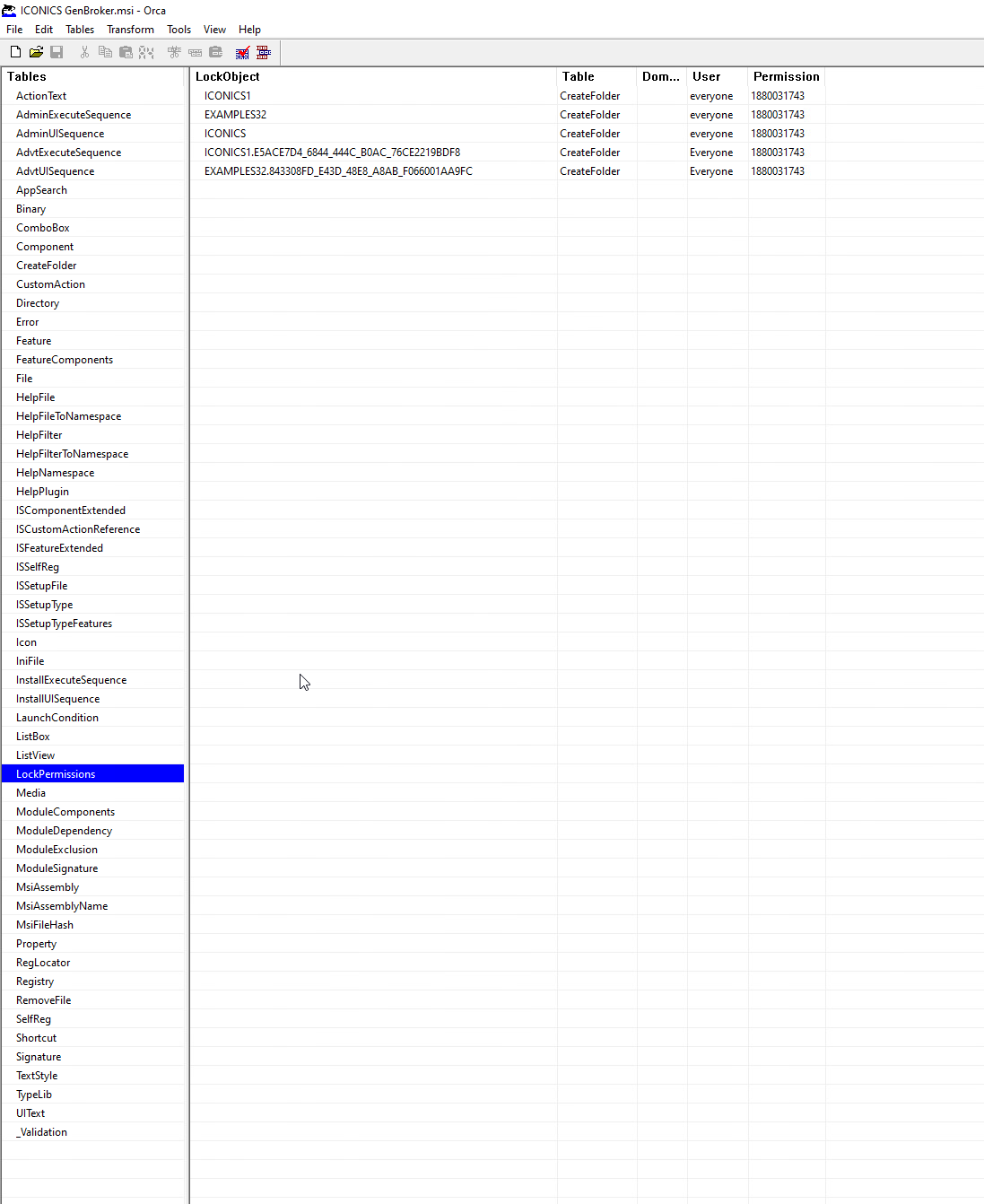
As shown in Figure 4, all objects listed in the LockPermissions table can perform a CreateFolder operation and set the owner as everyone. The third entry indicates the ICONICS directory under C:\ProgramData, and this entry grants every user of the system the permission to read, write and modify the contents of that directory.
Further analysis revealed that this GenBroker32 installer performs a SetSecurityFile operation to set the discretionary access control list (DACL) as Allow-Everyone for the directory C:\ProgramData\ICONICS.
Figure 5 shows a Process Monitor display filtered to reveal the SetSecurityFile operations performed when we ran the GenBroker32 installer.
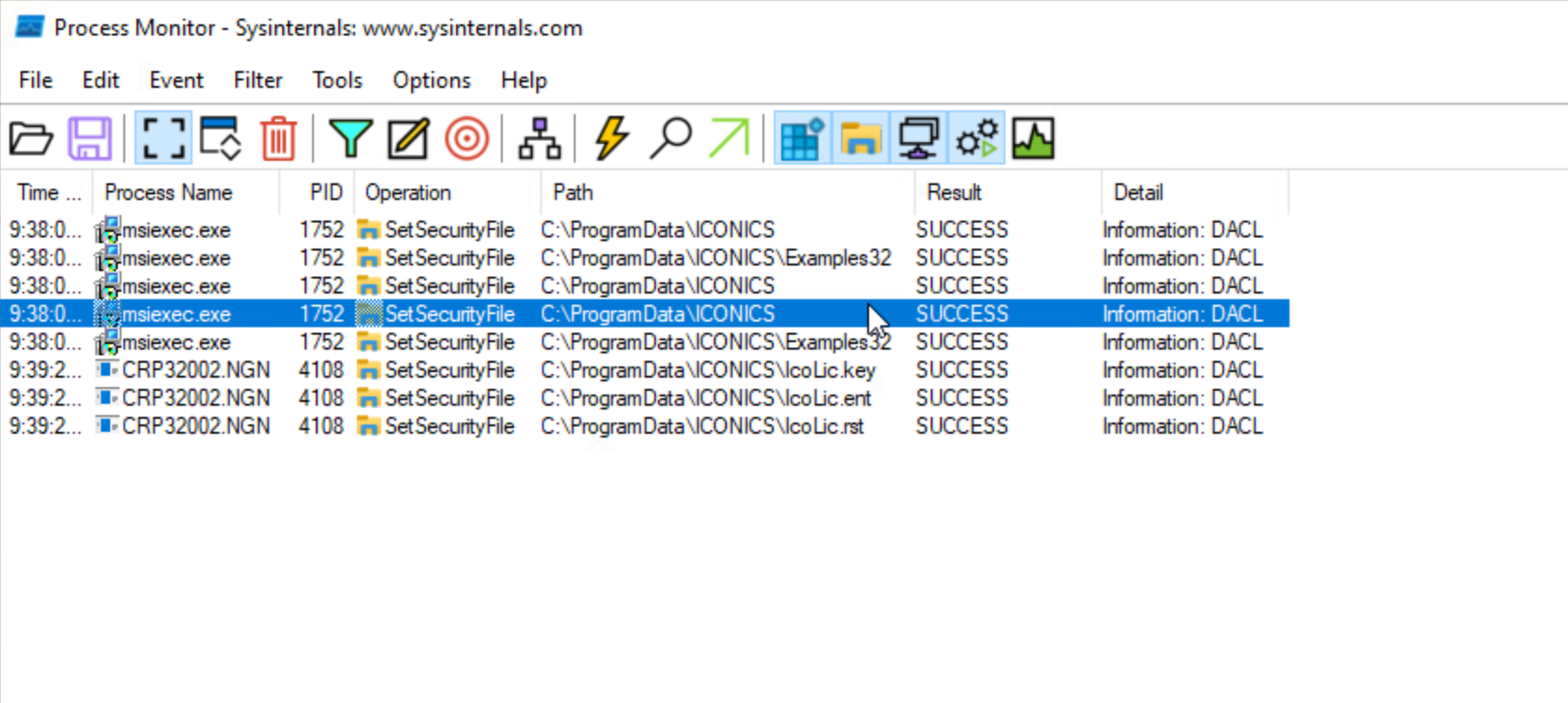
Figures 6 and 7 illustrate the changes caused by the installation of GenBroker32 using the Get-Acl utility in PowerShell. Figure 6 depicts the state before installing GenBroker32, where only the administrator user (zingbox) has full access. Figure 7 shows the modified access after installing GenBroker32, reflecting the full access granted to every logged user on the system.
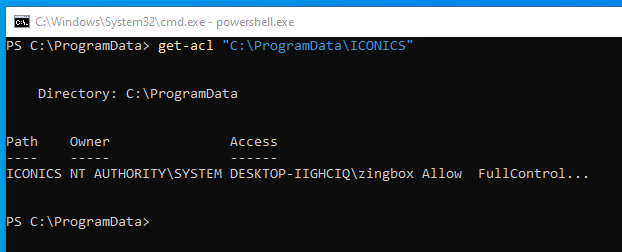
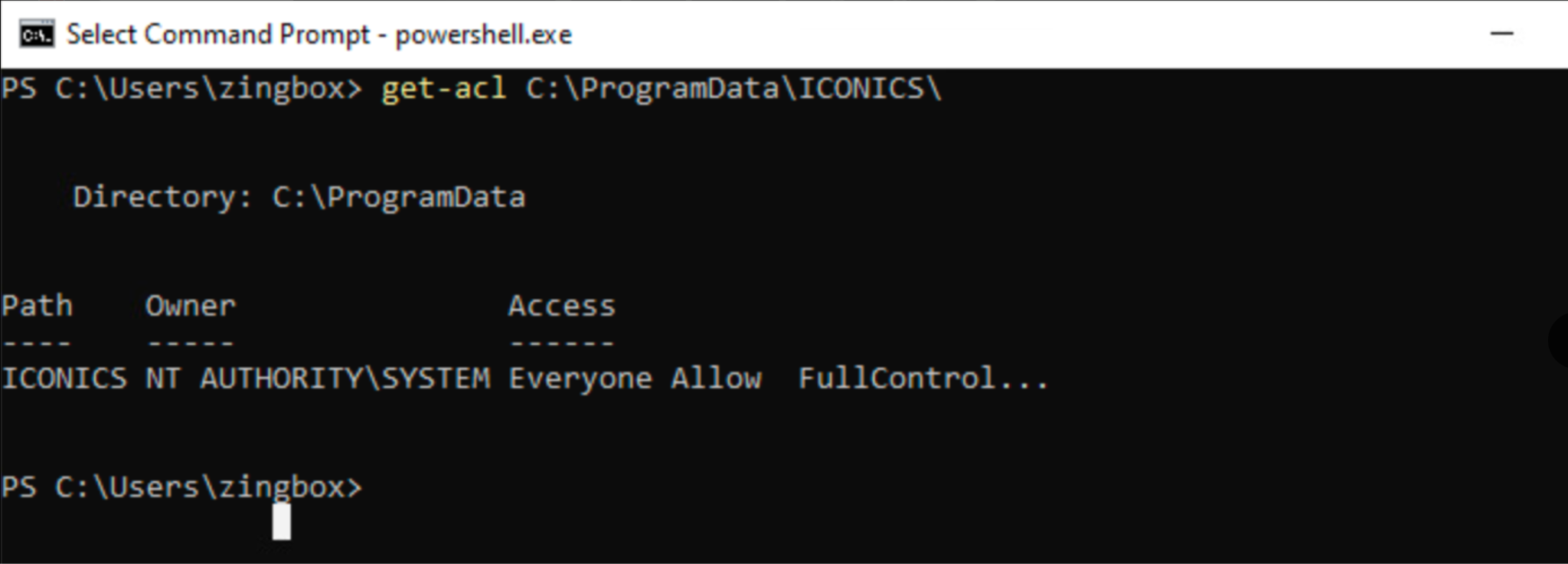
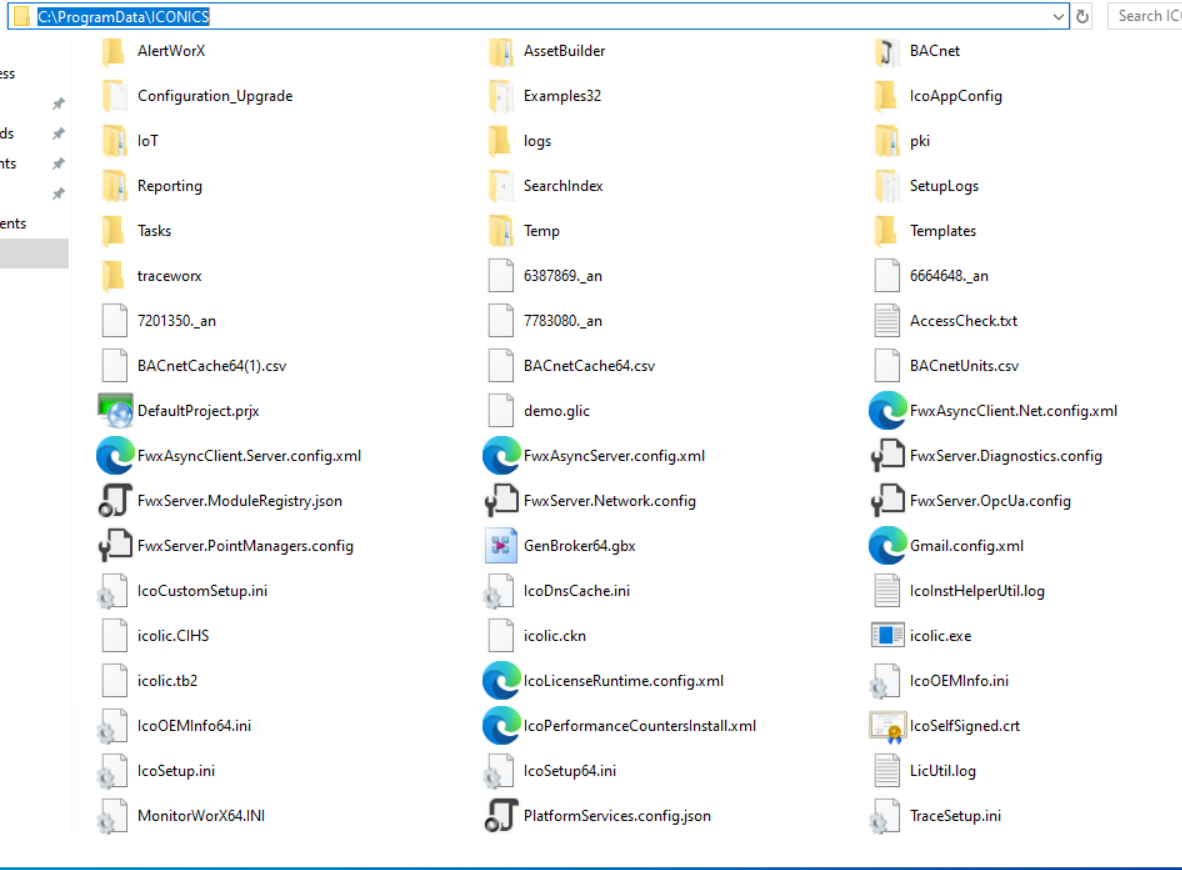
The C:\ProgramData\ICONICS directory contains critical configuration, reporting and logging files for the ICONICS Suite. This directory also contains a binary that an administrator can execute to renew the product’s license. Moreover, the read, write and execute permissions on this directory expose the system to a wide array of attacks.
Figure 8 shows the content of C:\ProgramData\ICONICS, which includes sensitive files that an attacker can easily hijack if they have full access permissions to this directory, such as the access provided through GenBroker32.
DLL Hijacking in MMCFG Leading to Elevation of Privileges – CVE-2024-1182
Phantom DLL hijacking is a cybersecurity attack method where an attacker takes advantage of the way applications load DLLs. Phantom DLL hijacking involves reintroducing an obsolete, non-existing or no longer used legitimate DLL back into the system.
The attacker modifies the obsolete DLL to perform malicious activities, such as:
- Arbitrary code execution
- Persistence
- System integrity compromise
- Elevation of privileges
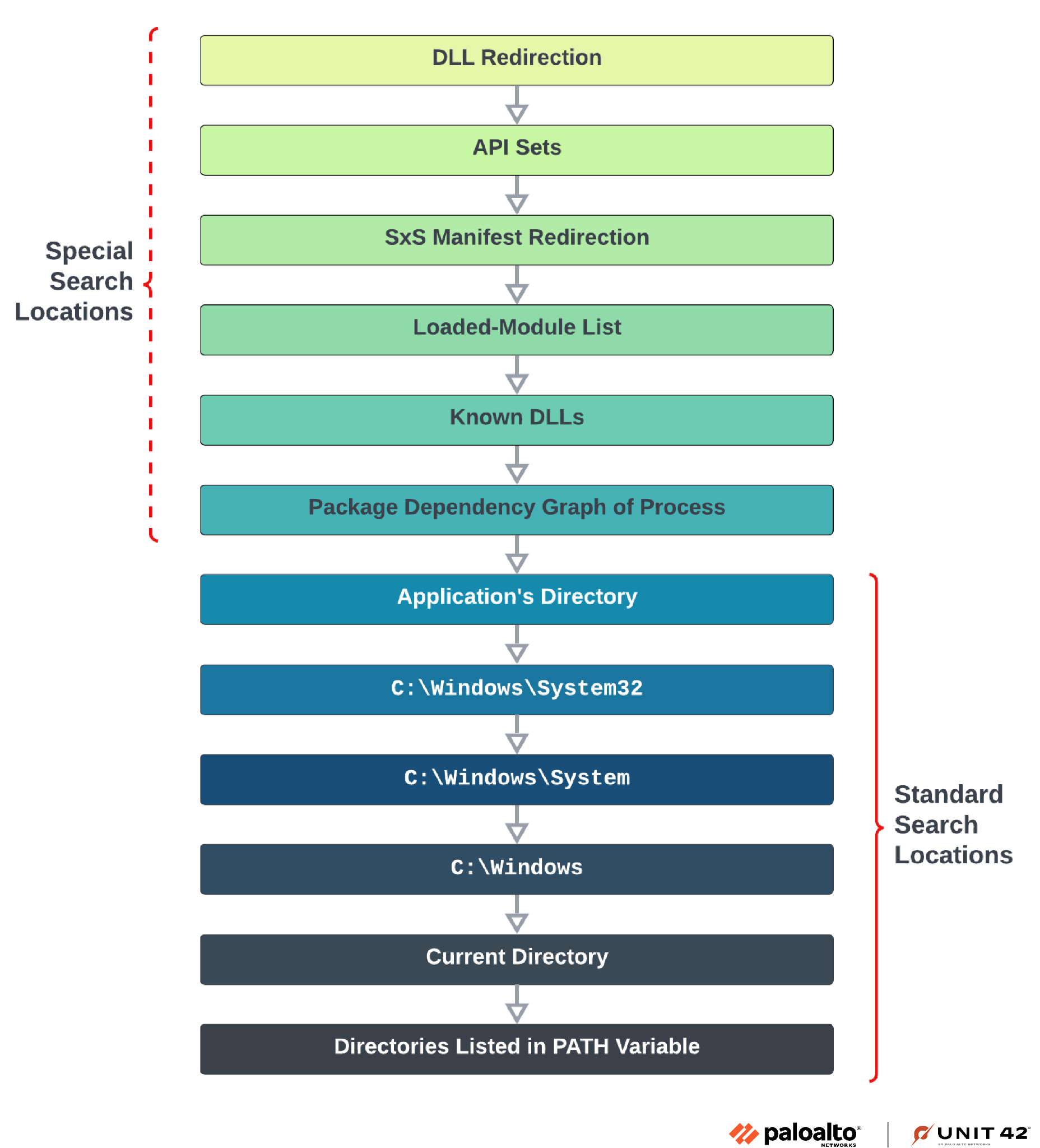
By abusing the Windows DLL search order (shown in Figure 9), an attacker can place the malicious DLL in a directory where the system will eventually look for it and load it. More details on this method can be found in the Unit 42 post Intruders in the Library: Exploring DLL Hijacking under the "Phantom DLL Loading" section.
During our security assessment, we discovered this vulnerability in the ICONICS Suite due to an outdated SMS software development kit (SDK) for Derdack's Message Master. This outdated Message Master SMS SDK at version 2.0 was developed by Derdack but has been deprecated for approximately 15 years with no ongoing support.
While no longer maintained, the Message Master SMS SDK is still integrated into the ICONICS Suite AlarmWorX MMX module. This module is responsible for facilitating SMS and pager alerts. When those applications use Message Master SMS SDK, they are exposed to the underlying vulnerabilities present in the Message Master SMS SDK.
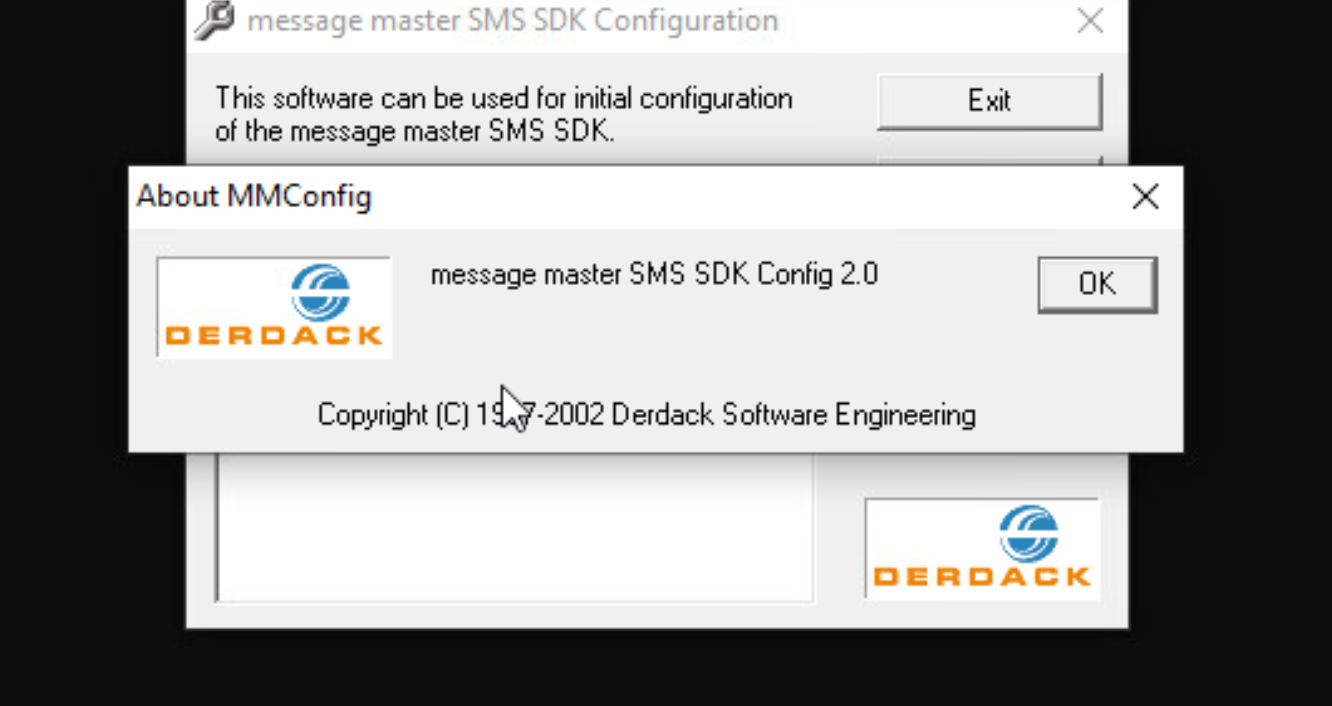
Figure 10 shows version 2.0 in the About window of the Message Master SMS SDK.
When a user initiates an ANSI modem, it starts the Memory Master configuration tool MMCfg.exe. This tool is integrated into the Pager Agent component of AlarmWorX64 MMX to facilitate the ANSI modem connections.
During execution, MMCfg.exe attempts to load a file named REVERB1.dll. However, due to improper DLL path specification and the absence of this DLL in the system directory, Windows eventually looks for this DLL in the current working directory.
An attacker can use the vulnerable MMCfg.exe file for DLL hijacking by placing a malicious DLL named REVERB1.dll in a directory where the attacker has write and execute permissions. As a result, the attacker can elevate privileges on the system.
Figure 11 shows a Process Monitor view filtered to show CreateFile and LoadImage operations performed by MMCfg.exe for the malicious DLL during our security assessment, resulting in arbitrary code execution.
![Image 11 is a screenshot of the ProcessMonitor window for sysinternals[.]com. Inset into the screenshot is the Windows terminal showing the phantom DLL hijacking.](https://unit42.paloaltonetworks.com/wp-content/uploads/2025/03/word-image-863686-138563-11.png)
Dead Code Vulnerability and Uncontrolled Search Path Element Vulnerability in ICONICS GENESIS64 – CVE-2024-8299, CVE-2024-8300, CVE-2024-9852
Similar to the previously described vulnerability, we found multiple vulnerable processes generated by ICONICS GENESIS64 that could be exploited through phantom DLL hijacking, and attackers could exploit these processes for the following purposes:
- Persistence
- Stealth
- Trust relationship abuse
- Deceiving Endpoint Detection and Response (EDR) and monitoring systems
Additionally, MelSim2ComProc.exe and MMXCall_in.exe, which are present in GENESIS64, are integrated within critical components of the ICONICS Suite such as AlarmWorX64 MMX that require administrator privileges to work. As a consequence, under some scenarios where AlarmWorX64 MMX invokes these applications, they will inherit administrator privileges. This makes AlarmWorX64 MMX vulnerable to the same type of DLL hijacking attack as the vulnerabilities previously described in CVE-2024-1182.
We confirmed that the following software components are vulnerable to phantom DLL hijacking through the following DLL file names:
- MelSim2ComProc.exe using Sim2ComProc.dll: MelSim2ComProc.exe relies on Sim2ComProc.dll in a directory at C:\Program Files\ICONICS\GENESIS64\Compnents\Communication. However, since the DLL is not present in the system directories, MelSim2ComProc.exe eventually looks for Communication\Sim2ComProc.dll in the current working directory.
- An attacker could place Sim2ComProc.dll in a directory called Communication inside the current working directory, which the attacker has control and write access to, making the application load the attacker’s malicious DLL.
- Figure 12 shows Process Monitor filtered to show a successful attempt at DLL hijacking for MelSim2ComProc.exe using Sim2ComProc.dll during our security assessment.
![Image 12 is a screenshot of the ProcessMonitor window for sysinternals[.]com. The highlighted line is for Load Image operation.](https://unit42.paloaltonetworks.com/wp-content/uploads/2025/03/word-image-868812-138563-12.png)
- MMXCall_in.exe using libdxxmt.dll and libsrlmt.dll: MMXCall_in.exe serves as a “call in agent” for AlarmWorX64 MMX. Due to improper DLL path specification, it looks for the missing librarylibdxxmt.dll or libsrlmt.dll files in the current working directory.
- Attackers could place a malicious DLL named libdxxmt.dll or libsrlmt.dll in the current working directory where MMXCall_in.exe is executed, to make the application load their malicious DLL.
- Figure 13 shows Process Monitor filtered to show a successful attempt at DLL hijacking for MMXCall_in.exe using libdxxmt.dll during our security assessment.
![Image 13 is a screenshot of the ProcessMonitor window for sysinternals[.]com. The highlighted line is for IRP_MJ_CREATE operation.](https://unit42.paloaltonetworks.com/wp-content/uploads/2025/03/F13-786x376.png)
Figure 14 shows Process Monitor filtered to show a successful attempt at DLL hijacking for MMXCall_in.exe using libsrlmt.dll during our security assessment.
![Image 14 is a screenshot of the ProcessMonitor window for sysinternals[.]com. It shows an array of malicious_dll files.](https://unit42.paloaltonetworks.com/wp-content/uploads/2025/03/F14-786x389.png)
We have been working in collaboration with the ICONICS security team to fix these issues. ICONICS has released security patches to address these issues.
Conclusion
People often overlook the possibility of attackers abusing privileged file system operations, regardless of the danger they can pose to systems running these processes, especially when these vulnerabilities are found in OT environments.
The discovery of vulnerabilities within the ICONICS Suite, as identified in versions 10.97.3 and earlier for Windows platforms, highlights the importance of robust security measures. Proactive measures can help mitigate these vulnerabilities and safeguard against potential exploitation.
Palo Alto Networks offers solutions such as the Industrial OT Security service, integrated with NGFW subscriptions. This service can detect and prevent malicious activities, including malicious artifacts in transit and anomalous command access to OT field devices.
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- Industrial OT Security is designed to:
- Use machine learning techniques to detect abnormal behavior in engineering workstations and field devices
- Raise alerts in the event of a compromised environment, based on anomalous command access
- Integrate with XSOAR to detect devices running a vulnerable version of the ICONICS Suite, becoming proactive with standardized, automated and enforceable processes
- Cortex XDR and XSIAM are designed to:
- Detect known and novel DLL hijacking attacks, using the new generic Analytics DLL Hijacking tag
- Prevent the execution of known and unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module
- Protect against credential gathering tools and techniques using the new Credential Gathering Protection available from Cortex XDR 3.4
- Cortex XDR Pro is designed to detect post-exploit activity, including credential-based attacks, with behavioral analytics
- Cortex Cloud:
- When paired with XSIAM, Cortex Cloud is enabled to block malicious processes from operating within the cloud environment
- Cortex Cloud is designed to prevent the execution of known and unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
- Cortex Xpanse is designed to:
- Provide a complete, accurate and continuously updated inventory of all global internet-facing assets, including exposed OT services and devices
- Enable discovery, evaluation and mitigation of cyberattack surface risks
- Facilitate evaluation of supplier risk
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Additional Resources
- Multiple Vulnerabilities in GENESIS64TM and MC Works64 [PDF] – Mitsubishi
- ICSA-24-184-03 – ICS Advisory
- Information Disclosure, Information Tampering and Denial of Service (DoS) Vulnerability in GENESIS64TM and MC Works64 [PDF] – Mitsubishi
- ICSA-24-296-01 – ICS Advisory
- Multiple Vulnerabilities in GENESIS64TM and MC Works64 [PDF] – Mitsubishi
- ICSA-24-338-04 – ICS Advisory
- Intruders in the Library: Exploring DLL Hijacking – Unit 42, Palo Alto Networks.
- A Link to the Past. Abusing Symbolic Links on Windows [PDF] – James Forshaw, Google Project Zero
- Symbolic-Link-Testing-Suite – James Forshaw, Google Project Zero
文章来源: https://unit42.paloaltonetworks.com/vulnerabilities-in-iconics-software-suite/
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh