搭建跨虚拟机 WinDbg 调试环境有点麻烦,我将记录一下搭建方法。
要求:
· Windows 10 VM(VMWare)
· 在该VM中安装了WinDbg
KD 网络通信
参考文档如下,但并不实用:
网络设置
· 将主机虚拟机clone到目标虚拟机
· 向两个VM添加第二个网络接口(:
· 确保WinDbg 支持接口硬件
· 在特定的“ LAN网段”上进行设置
· 将主机设置为192.168.0.1/24
· 将目标设置为192.168.0.2/24
· 允许从该接口通过主机防火墙访问所有内容
· 确保可以从目标 ping 主机
WinDbg设置,target
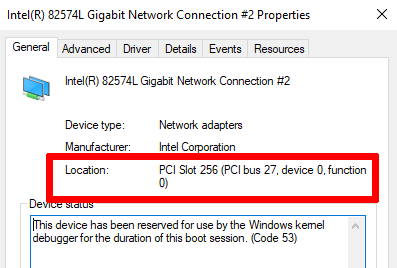
· 转到设备管理器以查找NIC(LAN段之一)的属性,并记下总线,设备和功能编号
· 在shell中,运行busparams,查找KEY值,用更安全的方式替换这些值:
bcdedit /dbgsettings net HOSTIP:192.168.0.1 PORT:50000 KEY:TO.TO.TU.TU nodhcp
bcdedit /set "{dbgsettings}" busparams 27.0.0
bcdedit /debug on如果需要有关各种选项的更多信息,请参阅文档。
WinDbg设置,host:
· 运行WinDbg
· 配置符号路径有两种方法:
cache*c:\MySymbols;srv*https://msdl.microsoft.com/download/symbols
· 使用“文件->符号文件路径”
· 设置_NT_SYMBOL_PATH环境变量
· 开始Kernel Debug会话(Ctrl-K)
· 输入 KEY,按OK(端口50000应该是默认端口)
· (可选)在LAN网段接口上运行Wireshark,以确保数据包到达接口
连接通信
现在,可以重新启动target机器,并且应该在host的WinDbg Shell中获得以下内容:
Connected to target 169.254.221.237 on port 50000 on local IP 192.168.0.1. You can get the target MAC address by running .kdtargetmac command. Connected to Windows 10 18362 x64 target at (Fri Mar 27 14:41:52.051 2020 (UTC + 1:00)), ptr64 TRUE Kernel Debugger connection established.
由于nodhcp在target的配置中指定了该选项,因此源IP在“自动IP”范围内。因此,如果host的防火墙没有完全打开,请确保允许此范围。
可以通过反汇编一些符号来确保一切正常:
0: kd> u ZwQueryInformationProcess nt!ZwQueryInformationProcess: fffff803`697bec50 488bc4 mov rax,rsp fffff803`697bec53 fa cli fffff803`697bec54 4883ec10 sub rsp,10h fffff803`697bec58 50 push rax fffff803`697bec59 9c pushfq fffff803`697bec5a 6a10 push 10h fffff803`697bec5c 488d055d750000 lea rax,[nt!KiServiceLinkage (fffff803`697c61c0)] fffff803`697bec63 50 push rax
常用命令
symbols
.reload /f => force symbol reload .reload /unl module => force symbol reload for a module that's not loaded
disassembly
u address => disassembly (ex: u ntdll+0x1000). "u ." => eip u . l4 => 4 lines from eip
breakpoints, running
bc nb => clear bp nb
bd nb => disable bp nb
bc/bd * => clear/disable all bps
bp addr => set bp
bp /1 addr => bp one-shot (deleted after first trig)
bl => list bp
ba => hardware bp
ba r 8 /p addr1 /t addr2 addr3
=> r==break RW access ;
8==size to monitor ;
/p EPROCESS address (process) ;
/t thread addresse
addr3 == actual ba adress
bp addr ".if {command1;command2} .else {command}"
p => single steppct => continue til next call or ret gu => go til next ret
data
da - dump ascii db - dump bytes => affiche byte + ascii dd - dump DWords dp - dump pointer-sized values dq - dump QWords du - dump Unicode (16 bit characters) dw - dump Words deref => poi(address)
editing:
ed addr value => set value at given address eq => qword a addr => assemble (x86 only) at this address (empty line to finish=)
structures:
dt nt!_EPROCESS addr => dump EPROCESS struct at addr
State, processes, etc
lm => list modules kb, kv => callstack !peb => peb of current process !teb => teb of current thread !process 0 0 => display all les processes !process my_process.exe => show info for "my_process.exe" !sd addr => dump security descriptor
drivers:
!object \Driver\ !drvobj Asgio2 => dump \Driver\Asgio2
devices:
!devobj Asgio2 => dump \Device\Asgio2
memory:
!address => dump address space !pte VA => dump PTEs for VA
本文翻译自:https://syscall.eu/blog/2020/03/29/windbg-vm/如若转载,请注明原文地址:
如有侵权请联系:admin#unsafe.sh
