VMRay Labs团队在2025年1月发现了多种新型恶意软件行为和工具滥用,并新增了多种威胁检测机制。包括入口点注入、直接从公共平台加载资源、滥用macOS代码签名工具、枚举显示适配器以及利用易受攻击的驱动程序(BYOVD)攻击等新威胁识别器(VTI)。此外,团队还改进了智能链接引爆(SLD)功能,并新增了针对伪造发件人、e.trustifi.com域名和雅虎附属链接的触发规则。同时,团队还添加了新的YARA规则来检测Metasploit shellcode变种、Phishkit.RandLoad和BruteRatel C2框架等恶意活动。 2025-2-11 14:18:25 Author: www.vmray.com(查看原文) 阅读量:9 收藏
The Labs team at VMRay actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cyber threat landscape.
In January 2025, the VMRay Labs team has been focused on the following:
1) New VMRay Threat Identifiers to detect:
- Entrypoint injection
- Hotlinking directly from public platforms
- Code signing tool abuse on macOS
- Enumeration of display adapters
- Bring Your Own Vulnerable Driver (BYOVD) attacks
2) New Smart Link Detonation triggers for:
- Spoofed sender VTI
- e.trustifi.com
- Yahoo affiliate links for redirection
3) New YARA rules for:
- Metasploit shellcode variants
- Phishkit.RandLoad
- BruteRatel C2 detection
Now, let’s delve into each topic for a more comprehensive understanding.
In a few last blog posts, we introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score, which greatly contributes to the ultimate Verdict of the sample, is presented to you in the VMRay Platform after a completed analysis. Here’s a recap of the new VTIs that we added, or improved in the past month.
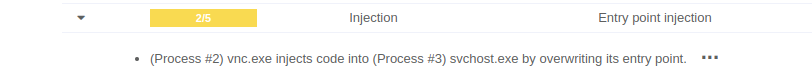
Detecting entrypoint injection
Category:Process Injection
MITRE ATT&CK® Technique:T1055
Entrypoint Injection is a code injection technique where attackers modify the entry point of a newly created process that is in a suspended state. This allows them to inject and execute malicious code within the context of a legitimate application, often evading security defenses.
Characteristics of entrypoint injection:
- Exploiting trust – security tools often trust legitimate processes, making malicious execution harder to detect.
- A new process needs to be created – unlike other techniques such as Thread Hijacking, or some special versions of Process Hollowing that just target running processes.
How attackers exploit entrypoint injection?
- Creating a suspended process – the target process is spawned but paused before execution.
- Modifying the entrypoint – the attacker overwrites the original entry point instructions with shellcode.
- Resuming execution – when resumed, the process runs the injected code instead of its intended logic.
Our new VTI is designed to detect malicious code modifications for processes which have been created in a suspended mode.
Detecting hotlinking directly from public platforms
Category: Heuristics
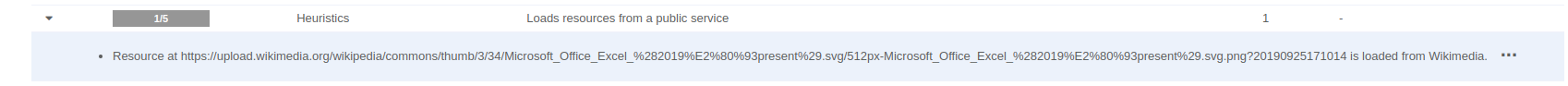
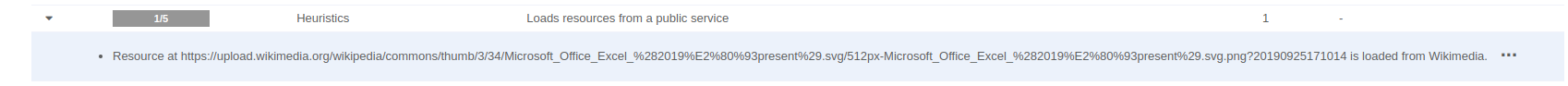
Phishing websites are getting increasingly sophisticated, but sometimes, even the smallest clues can give them away. Recently, VMRay identified a trick used by cybercriminals that looks harmless at first glance – a website loading an Excel logo directly from Wikipedia.
Why is this suspicious?
Legitimate organizations usually follow certain professional standards when building their websites. They avoid something called “hotlinking,” which is when you directly use an image hosted on another website, like Wikipedia, rather than hosting it yourself. Here’s why this practice is normally avoided:
- Copyright concerns – using someone else’s image directly without permission can lead to legal trouble.
- Professionalism – it’s considered poor practice and signals a careless approach.
When a website breaks these norms, it raises red flags. A phishing site, for example, might hotlink an Excel logo from Wikipedia because the attackers want to quickly create convincing content without spending time on proper design or legality. While hotlinking could be a sign of carelessness, it’s often associated with phishing or some other malicious intent. Phishing websites aim to deceive users into thinking they’re on a legitimate site, like a bank or an email provider, to steal sensitive information.
To protect against this, VMRay has introduced a new VTI designed to flag websites or files that load resources, like logos, directly from public platforms.
Detecting code signing tool abuse on macOS
Category:Defense Evasion
MITRE ATT&CK® Technique: T1553.002
Code signing is a legitimate security mechanism that developers use to digitally sign their software. This process ensures that the software originates from a trusted source and has not been tampered with. When a user installs a signed application, macOS verifies the signature against the developer’s public key. If the signature is valid and trusted, the software installs without triggering security warnings.
How attackers exploit code signing on macOS?
In a recent sample submitted by one of our customers, we observed the misuse of the codesign tool to self-sign a downloaded executable. This tactic can trick macOS into allowing execution without user prompts, which is a clear attempt to evade built-in security protections.
The analyzed sample executed a malicious command, with several parts raising suspicion. Let’s dive into some key steps that should trigger an alert:
- Downloading an executable from an external server – the script uses
curlto fetch an executable from a remote URL. This is a common technique used by malware to download additional payloads dynamically. - Manipulating file attributes to bypass security checks –
chmod +x ~/Library/filename– grants execution permissions, as macOS blocks execution by default for downloaded files. - Self-signing without a valid certificate – the command
codesign --force --deep --sign - ~/Library/filenameuses-as the signature, which means self-signing without a trusted Apple Developer ID. This prevents macOS from flagging the file as “Unsigned,” increasing the chances of successful execution.
These steps, when combined, create a stealthy way for malware to bypass macOS security mechanisms and execute malicious code without alerting the user. To address this technique, our latest VTI will trigger an alert whenever the codesign tool is executed within a macOS malware sample.
Detecting enumeration of display adapters
Category: Discovery
This technique enables developers to enumerate display devices and obtain details like device names, descriptions, and statuses. However, it can be exploited by malware authors in several ways. Here’s how:
- System fingerprinting and reconnaissance. By iterating through connected display devices, malware can gather key system details, and tailor their attack strategies accordingly including:
- Number of monitors – useful for detecting multi-monitor setups.
- Display adapter names – helps identify hardware specifications.
- Mirrored or virtual displays – can reveal sandbox or VM environments.
- Evasion techniques against sandboxes. Many malware detection systems run in virtualized environments (VMs) that have distinct display configurations (e.g., a single display adapter or specific virtual GPU names). Using
EnumDisplayDevices, malware can:- Detect if it’s running inside a VM and avoid executing if a virtual environment is detected.
- Identify headless environments (systems with no active displays), often used for automated analysis.
- Screen capture and surveillance. Malicious actors using screen capture APIs to take screenshots for data collection.
To stay ahead of this technique, our new VTI will trigger whenever a sample attempts to enumerate display devices. This ensures that suspicious activity involving display enumeration is detected early, helping security teams respond proactively to potential threats.
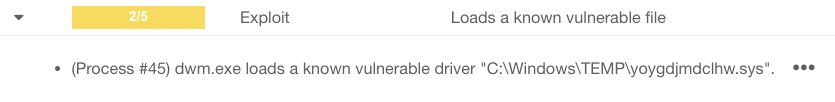
Detecting Bring Your Own Vulnerable Driver (BYOVD) attacks
Category: Exploit
MITRE ATT&CK® Technique: T1068
In our November 2024 blog post, we introduced the concept of Bring Your Own Vulnerable Driver (BYOVD) attacks and discussed how attackers exploit legitimate but flawed drivers to bypass security defenses. Now, we’re taking detection a step further with a new VTI to catch these attacks in action.
A BYOVD attack is a cyberattack where hackers exploit vulnerabilities in legitimate drivers, a small program that controls hardware components like printers or video cards, to gain deep control over a system.
Because drivers run inside the kernel (the core of an operating system), they have the highest level of privileges. If a driver has security weaknesses, attackers can abuse it to disable security tools, like EDR (Endpoint Detection and Response) systems, making it much harder to detect their activities.
The main trick behind BYOVD attacks is that many drivers are signed by trusted vendors, meaning they are verified as safe. However, if a signed driver has a security flaw, attackers can:
- Load the vulnerable driver onto the victim’s machine.
- Exploit the driver’s flaws to gain admin-level (or even kernel-level) access.
- Disable security software, allowing them to execute malicious activities undetected.
Previously, we introduced a YARA rule to detect certain files commonly associated with BYOVD attacks. Now, we’re adding an extra layer of protection: a new VTI that triggers if a driver that is known to be vulnerable is loaded.
In January 2025, we’ve made several improvements to the Smart Link Detonation (SLD) mechanism in our Platform products. If you haven’t read about it yet – SLD is a feature that enables the automatic evaluation and detonation of appropriate hyperlinks in document and email samples. This time, we’ve added new detonation rules, which allows for even greater capability of this feature to capture malicious URLs.
New SLD trigger based on Spoofed Sender
Phishing emails are a common vector for delivering malicious links and files. To maximize their effectiveness, attackers rely on sender spoofing, a tactic where an email appears to come from a trusted source, such as your boss, a colleague, or a well-known organization. This deception increases the likelihood of user interaction, making spoofed emails a critical security concern. To combat sender spoofing, the VMRay Platform already includes a VMRay Threat Identifier (VTI) that detects when a spoofed sender is present in an email.
What’s new with SLD tackling this threat?
With our latest enhancements, the Smart Link Detonation feature nowperforms recursive analysis on all URLs found within a submitted email that originates from a spoofed sender, discovered using our existing VTI. This is a crucial upgrade significantly improving our ability to detect phishing threats before they reach users. This means:
- Every link in the email is automatically analyzed, regardless of where it appears: whether in the body of the message or hidden in attachments.
- The system digs deeper into these links, detonating and examining the behaviors of the pages they lead to.
By combining Smart Link Detonation with the spoofed sender VTI, VMRay offers a comprehensive approach to identifying and stopping emails exploiting spoofed sender technique.
New domain trigger for e.trustifi.com
Trustifi is a cloud-based email security platform designed to protect organizations from phishing, malware, and business email compromise. However, like many legitimate services, it can be abused by attackers to host phishing content.
Recently, our team at VMRay discovered a previously unknown phishing site hosted on e.trustifi.com, a legitimate domain used for secure message exchange. In this case, attackers abused Trustifi’s services to host and distribute phishing content, sending messages that trick users into clicking links leading to phishing pages, all under the guise of secure communication.
To help counter this, we’ve implemented a new rule that triggers our SLD feature for any links associated with e.trustifi.com. This ensures that links from this domain are automatically detonated in a secure environment, helping to detect potential threats before reaching end users.
New SLD trigger for Yahoo affiliate links for redirection
Recently, we observed aPDF document that contained a link to a phishing page. The link was disguised as a redirector, using a Yahoo mobile app affiliate link:
https://mobile.mail.yahoo.com/apps/affiliateRouter?brandUrl=… While this link may seem legitimate at first glance, it’s actually designed to redirect users to a phishing site and misuse Yahoo’s branding to gain trust and hide the actual phishing page.
To tackle this, we’ve added a new trigger for our Smart Link Detonation feature. Now, if a link like this is encountered, it automatically activates the SLD to safely analyze and detonate any phishing pages that could be hidden behind these redirectors.
New rule to detect Metasploit shellcode variants
Metasploit is a popular tool used by cybersecurity experts to test vulnerabilities in systems. While it’s a legitimate framework, its open-source nature means that hackers can also abuse it to hijack systems and control them remotely.
A particular risk from Metasploit are shellcodes: small executable pieces of code designed to exploit vulnerabilities and gain unauthorized access to a system. These shellcodes are commonly embedded in files or encoded to hide their true intentions and bypass traditional security measures.
To enhance our detection capabilities, we’ve introduced a new YARA rule that targets Metasploit-generated shellcodes. Previously, encoded shellcodes might have slipped through the cracks, especially if they weren’t accompanied by scripts or loaders that are often used to execute the code.
With this new rule:
- Shellcode used in Metasploit reverse shells will be detected, immediately flagging the analysis as malicious.
- Malicious verdicts will be more accurate, especially when these shellcodes are paired with other execution mechanisms or loaders.
New YARA rule to support latest phishkit
The Phishkit.RandLoad is the latest phishkit we’ve detected. Here’s how it operates:
- Dynamic URL generation – instead of using a static URL, Phishkit.RandLoad creates the final phishing URL on the fly. This is done using a function called
generateRandomString, which makes the URL appear random and harder to detect. The functiongenerateURLthen assembles the full phishing URL. - Use of iframes – the phishing page uses iframes, which are like windows within a webpage that display content from another site. In this case, the attackers use an iframe to display a fake version of a legitimate Microsoft login page, tricking users into entering their credentials.
- Deceptive pre-text – the phishing email campaigns created by RandLoad appear to be related to invoices or subscription renewals, making the email look like something important that needs immediate attention.
To combat this threat, we’ve added a new YARA rule to automatically detect and flag any suspicious files or activity related to Phishkit.RandLoad.
New rules for BruteRatel C2 detection
The BruteRatel C2 (Command and Control) framework is a commercial cybersecurity tool designed to help professionals simulate real-world cyberattacks. It allows security teams to mimic the tactics and techniques used by cyber adversaries to test and strengthen their defenses.
Again, like many powerful tools, BruteRatel C2 has also been exploited by malicious actors. While originally intended for legitimate security testing, cybercriminals have repurposed the framework to conduct unauthorized attacks, taking advantage of its evasion features to bypass traditional security measures and avoid detection.
One of the most concerning uses of BruteRatel C2 has been in recent Latrodectus delivery chains, a notorious malware campaign. This shows just how dangerous it can be in the hands of attackers, as they use it to deploy payloads and control compromised systems remotely.
To combat this threat, we’ve made several important updates over the past month. New signatures have been added to detect various public and leaked versions of BruteRatel C2.
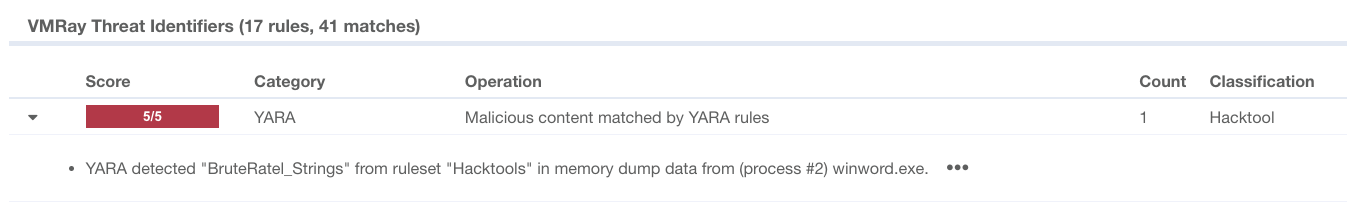
We do hope our constant research of new malware trends and the features we together bring to our products help you in the navigation of the complex landscape of cybersecurity. Stay tuned for our February signature and detection updates, planned to be published in the weeks ahead. Furthermore, soon we’ll release the latest version – 2025.1.0 – of the VMRay Platform, with some great new features and enhancements.
如有侵权请联系:admin#unsafe.sh