
Executive summaryIn recent developments, a sophisticated malware stealer strain crafted i 2023-12-18 22:51:0 Author: levelblue.com(查看原文) 阅读量:0 收藏
Executive summary
In recent developments, a sophisticated malware stealer strain crafted in the Go programming language has been discovered by LevelBlue Labs, posing a severe threat to both Windows and macOS operating systems.
As of the time of publishing of this article, traditional antivirus solutions have low or even non-existent detection rates, making it a stealthy and formidable adversary.
Key takeaways:
- The malware is equipped with an extensive array of commands from its Command and Control (C&C) server.
- JaskaGO can persist in different methods in infected system.
- Users face a heightened risk of data compromise as the malware excels at exfiltrating valuable information, ranging from browser credentials to cryptocurrency wallet details and other sensitive user files.
Background
JaskaGO contributes to a growing trend in malware development leveraging the Go programming language. Go, also known as Golang, is recognized for its simplicity, efficiency, and cross-platform capabilities. Its ease of use has made it an attractive choice for malware authors seeking to create versatile and sophisticated threats.
While macOS is often perceived as a secure operating system, there exists a prevalent misconception among users that it is impervious to malware. Historically, this misbelief has stemmed from the relative scarcity of macOS-targeted threats compared to other platforms. However, JaskaGO serves as a stark reminder that both Windows and macOS users are constantly at risk of malware attacks.
As the malware use of file names resembling well-known applications (such as “Capcut_Installer_Intel_M1.dmg”, “Anyconnect.exe”) suggest a common strategy of malware deployment under the guise of legitimate software in pirated application web pages.
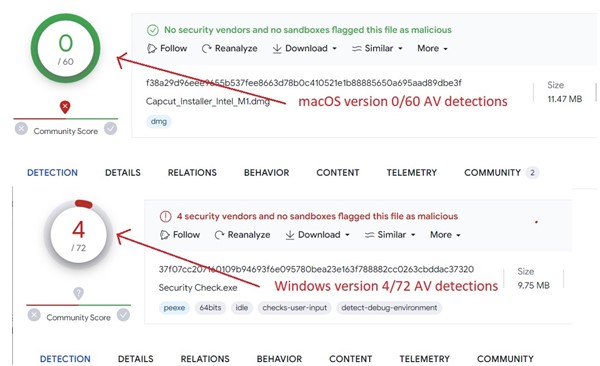
The first JaskaGo sample was observed in July 2023, initially targeting Mac users. Following this opening assault, dozens of new samples have been identified as the threat evolved its capabilities and developed in both macOS and to Windows versions; its low detection rate is evident by its recent sample by anti-virus engines. (Figure 1)
 .
.
Figure 1. As captured by LevelBlue Labs: Anti-virus detection for recent JaskaGO samples within VirusTotal.
Analysis
Upon initial execution, the malware cunningly presents a deceptive message box, displaying a fake error message, claiming a missing file. This is strategically designed to mislead the user into believing that the malicious code failed to run. (Figure 2)
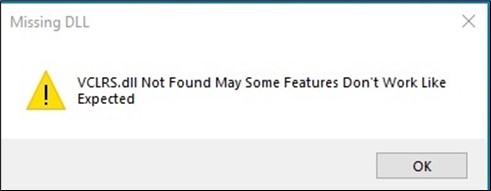
Figure 2. As captured by LevelBlue Labs: Fake error message.
Anti-VM
The malware conducts thorough checks to determine if it is operating within a virtual machine (VM). This process begins with the examination of general machine information, where specific criteria such as the number of processors, system up-time, available system memory, and MAC addresses are checked. The presence of MAC addresses associated with well-known VM software, such as VMware or VirtualBox, is a key indicator. (Figure 3)
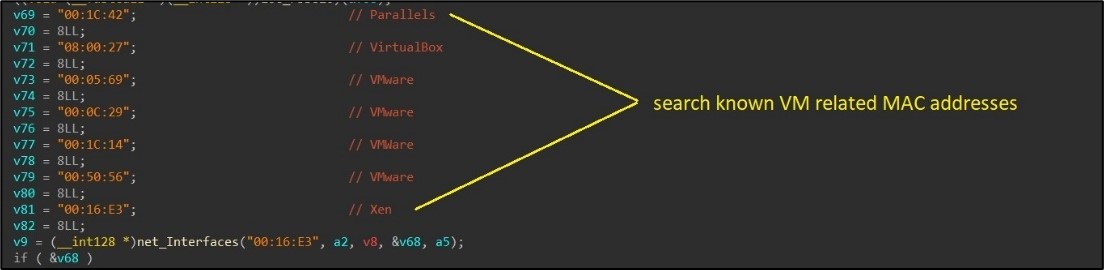
Figure 3. As captured by LevelBlue Labs: Looking for VM related MAC addresses.
Additionally, the malware's Windows version searches for VM-related traces in both the registry and the file system. (Figure 4)
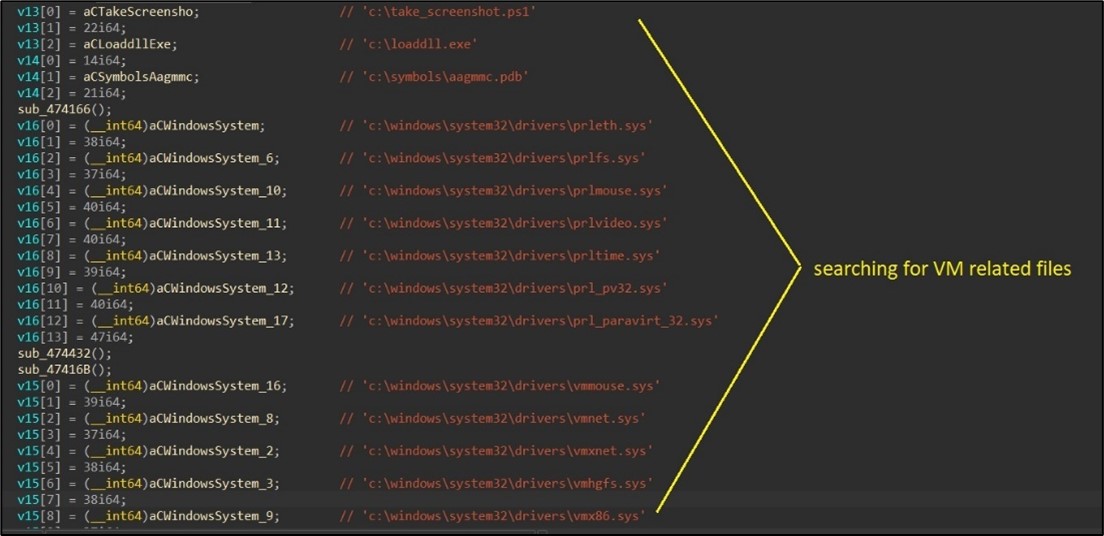
Figure 4. As captured by LevelBlue Labs: Looking for VM related files.
Should the malware detect that it is running within a virtual environment, it randomly executes one of the following commands:
- Ping Google.
- Create File on Desktop (e.g., config.ini).
- List files on the user's desktop.
- List local IP addresses.
- Make a simple HTTP GET request to https://www.web3api.com.
- Print a random number.
- Create a directory with a random name in the user's home directory.
- Print a random string.
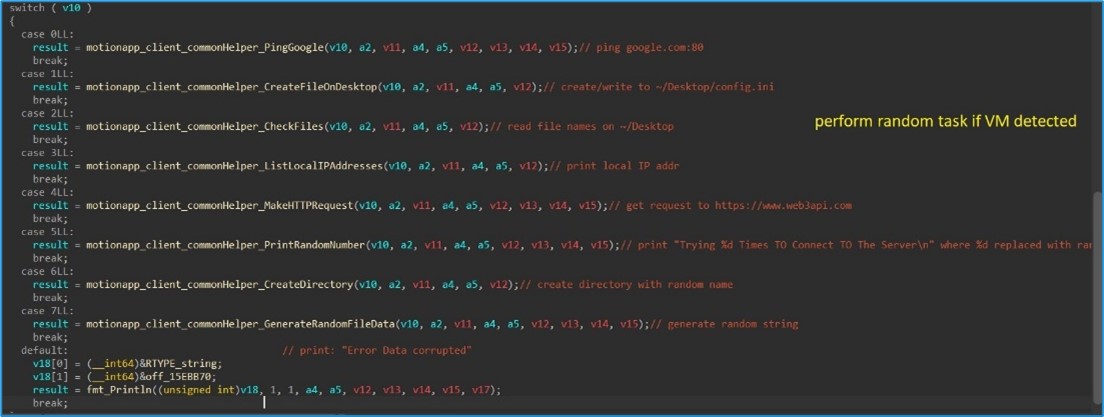
Figure 5. As captured by LevelBlue Labs: Perform random task.
Handle C&C commands
If the VM detection is bypassed, JaskaGO proceeds to collect information from the victim and establishes a connection to its command and control for further actions. (Figure 6)
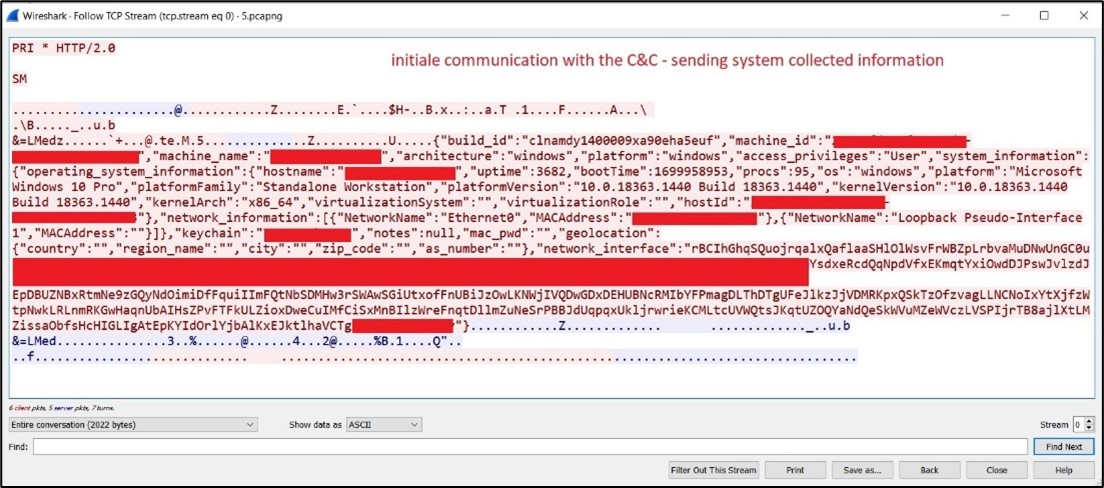
Figure 6. As captured by LevelBlue Labs: Communication with the C&C.
The malware continuously queries its command and control server, awaiting instructions. The potential commands include:
- Creating persistence for the malware (details in the subsequent section).
- Stealer functionalities: collecting information from the infected device and transmitting it to the command and control server.
- Pinging the command and control.
- Executing shell commands.
- Displaying alert messages.
- Retrieving running process list.
- Executing files on disk or in memory.
- Writing to the clipboard:a common tactic for stealing cryptocurrency funds.
- Performing a random task (like those in the VM detection section).
- Downloading and executing additional payloads.
- Initiating the process to exit (self).
- Initiating the process to exit and delete itself.
Stealer
JaskaGO is equipped with extensive data exfiltration capabilities. It stores acquired data in a specially created folder, zipping and sending it to the malware's threat actor when ready.
Browser stealer
While default support includes information theft from Chrome and Firefox browsers, the malware can be configured to target additional browsers. The collected browser information includes:
- Browser credentials.
- History.
- Cookies: Files and folders - “Cookies”, “cookies.sqlite”, Network”.
- Password encryption keys key4.db - Stores the master key to decrypt all passwords stored in logins.json.
- Profile files (profile.ini, ^Profile\d+$).
- Login information - “Login Data” folder.
Crypto currency stealer
The malware searches for browsers crypto wallets extension under the folder browser’s extension folder "ֿLocal Extension Settings". In addition, it supports receiving a list of wallets to search for and upload to the server.
Files
The malware can receive a list of files and folders to exfiltrate.
Persistence mechanisms
Windows
In the Windows version, the malware establishes persistence through two methods:
- Service Creation: The malware creates a service and initiates its execution.
- Windows Terminal "Profiles": Uncommon but effective, JaskaGO creates a Windows Terminal profile by generating the file "C:\users$env:UserName\AppData\Local\Packages\Microsoft. WindowsTerminal_*\LocalState\settings.json." This file is configured to run automatically on Windows reboot, launching a PowerShell process to execute the malware. Further details on this technique can be found here. (Figure 7)
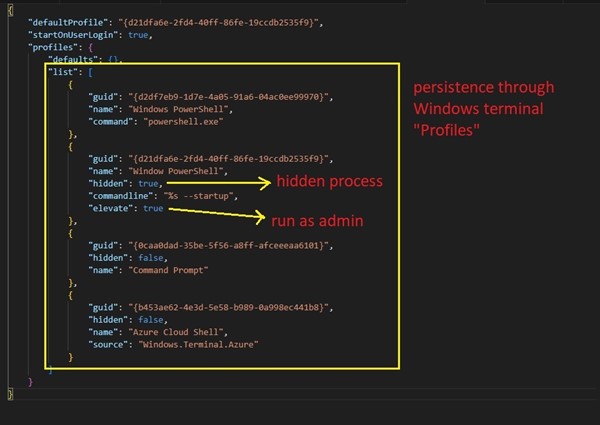
Figure 7. As captured by LevelBlue Labs: Windows persistence.
macOS
On macOS, JaskaGO employs a multi-step process to establish persistence within the system:
- Execution as Root: The malware initiates its execution with an attempt to run itself with root privileges.
- Disabling Gatekeeper: Gatekeeper, a security feature on macOS, is systematically disabled by the malware using the command “spctl --master-disable". This action aims to bypass security checks and facilitate unhindered operation.
- JaskaGO duplicates itself, adopting the name format "com.%s.appbackgroundservice," with %s being replaced by a randomly generated string. This renaming tactic helps obfuscate the malware's presence on the system.
- LaunchDaemon / LaunchAgent Creation: To ensure persistence, based on successful root access, the malware creates either the LaunchDaemon "/Library/LaunchDaemons/Init.plist" (if root) or LaunchAgent “/Library/LaunchAgents/service.plist” (if not root). This configuration ensures that the malware is automatically launched during system startup, further embedding itself into the macOS environment. (Figure 8)
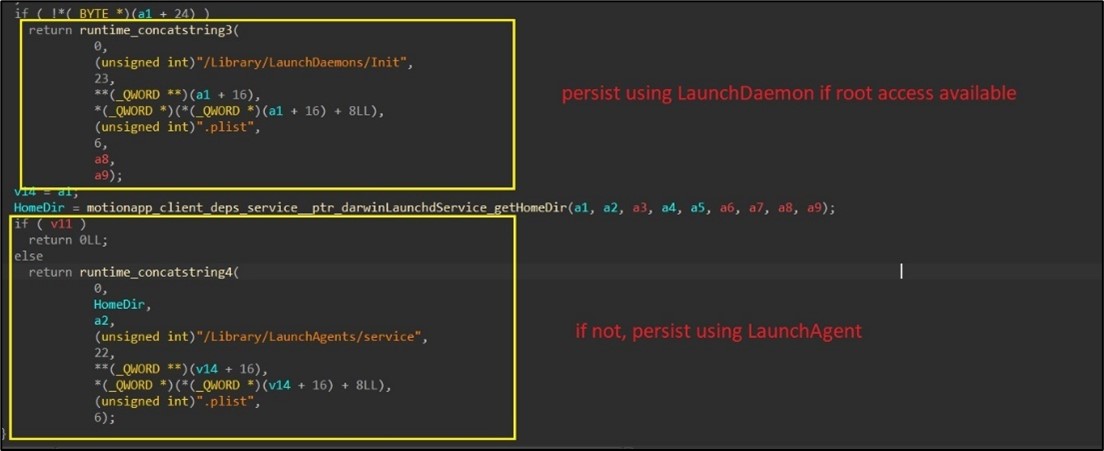
Figure 8. As captured by LevelBlue Labs: macOS persistence.
Conclusion
JaskaGO, a cross-platform threat, stands as a compelling example of the evolving threat landscape. It challenges the widely held notion of macOS invulnerability, highlighting the shared vulnerability of both Windows and macOS systems. Employing sophisticated anti-VM tactics, JaskaGO sidesteps automatic analysis, making it a formidable challenge for detection. Its persistence mechanisms reveal a determined effort to embed itself within systems, while its stealer capabilities transform the malware into a dangerous threat, extracting sensitive information from unsuspecting victims.
Associated indicators (IOCs)
The following technical indicators are associated with the reported intelligence. A list of indicators is also available in the OTX Pulse. Please note, the pulse may include other activities related but out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
7bc872896748f346fdb2426c774477c4f6dcedc9789a44bd9d3c889f778d5c4b |
Windows malware hash |
|
SHA256 |
f38a29d96eee9655b537fee8663d78b0c410521e1b88885650a695aad89dbe3f |
macOS malware hash |
|
SHA256 |
6efa29a0f9d112cfbb982f7d9c0ddfe395b0b0edb885c2d5409b33ad60ce1435 |
Windows malware hash |
|
SHA256 |
f2809656e675e9025f4845016f539b88c6887fa247113ff60642bd802e8a15d2 |
Windows malware hash |
|
SHA256 |
85bffa4587801b863de62b8ab4b048714c5303a1129d621ce97750d2a9a989f9 |
Windows malware hash |
|
SHA256 |
37f07cc207160109b94693f6e095780bea23e163f788882cc0263cbddac37320 |
Windows malware hash |
|
SHA256 |
e347d1833f82dc88e28b1baaa2657fe7ecbfe41b265c769cce25f1c0e181d7e0 |
Windows malware hash |
|
SHA256 |
c714f3985668865594784dba3aeda1d961acc4ea7f59a178851e609966ca5fa6 |
Windows malware hash |
|
SHA256 |
9b23091e5e0bd973822da1ce9bf1f081987daa3ad8d2924ddc87eee6d1b4570d |
Windows malware hash |
|
SHA256 |
1c0e66e2ea354c745aebda07c116f869c6f17d205940bf4f19e0fdf78d5dec26 |
Windows malware hash |
|
SHA256 |
e69017e410aa185b34e713b658a5aa64bff9992ec1dbd274327a5d4173f6e559 |
Windows malware hash |
|
SHA256 |
6cdda60ffbc0e767596eb27dc4597ad31b5f5b4ade066f727012de9e510fc186 |
macOS malware hash |
|
SHA256 |
44d2d0e47071b96a2bd160aeed12239d4114b7ec6c15fd451501c008d53783cf |
Windows malware hash |
|
SHA256 |
8ad4f7e14b36ffa6eb7ab4834268a7c4651b1b44c2fc5b940246a7382897c98e |
Windows malware hash |
|
SHA256 |
888623644d722f35e4dcc6df83693eab38c1af88ae03e68fd30a96d4f8cbcc01 |
Windows malware hash |
|
SHA256 |
3f139c3fcad8bd15a714a17d22895389b92852118687f62d7b4c9e57763a8867 |
Windows malware hash |
|
SHA256 |
207b5ee9d8cbff6db8282bc89c63f85e0ccc164a6229c882ccdf6143ccefdcbc |
macOS malware hash |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the following MITRE ATT&CK Matrix techniques:
-
- TA0003: Persistence
- T1543: Create or Modify System Process
- T1543.001: Launch Agent
- T1543.003: Windows Service
- T1543.004: Launch Daemon
- T1543: Create or Modify System Process
- TA0007: Discovery
- T1082: System Information Discovery
- T1057: Process Discovery
- T1082: System Information Discovery
- T1518: Software Discovery
- T1518.001: Security Software Discovery
- TA0011: Command and Control
- T1571: Non-Standard Port
- TA0010: Exfiltration
- T1020: Automated Exfiltration
- T1041: Exfiltration Over C2 Channel
- TA0003: Persistence
如有侵权请联系:admin#unsafe.sh