2025-1-28 15:45:39 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏

By Avia Yaacov, Product Manager, Pentera
Cryptojacking. It’s not as loud as ransomware or headline-grabbing data breaches, but it’s quietly draining resources and racking up costs. Instead of locking you out of your systems, cryptojacking silently hijacks your computing power—whether it’s on your servers or in the cloud—and mines cryptocurrency without you even knowing.
It’s costing companies more than they realize, and it’s time to address this threat before it causes more harm.
In 2023, cryptojacking attacks surged by 659%, according to SonicWall. For every $1 worth of cryptocurrency mined, companies are left paying around $53 in cloud costs. And since cryptojacking doesn’t immediately disrupt systems like ransomware, it often goes unnoticed—leaving organizations to discover the damage long after it’s been done.
With more businesses shifting to cloud environments and containerized infrastructures, cryptojackers are finding new ways to exploit these systems. The question is: how do you defend your organization against an attack that’s designed to stay hidden?
What is Cryptojacking and How Does it Sneak In?
Cryptojacking involves the unauthorized use of your computing resources—whether it’s your CPU, GPU, or cloud infrastructure—to mine cryptocurrency like Bitcoin or Monero. The goal isn’t to steal your data, but your processing power. And attackers have developed several methods to get cryptomining code into your systems.
Here’s how they typically infiltrate:
- Drive-by Downloads: When users visit compromised websites, malicious cryptomining scripts can automatically execute in the background. The BianLian ransomware group used this approach in 2023, spreading cryptomining scripts to unknowing visitors.
- Phishing Emails: Click on a link or download a file from a phishing email, and you could be unknowingly downloading cryptomining malware. In 2024, a campaign using obfuscated SVG files bypassed defenses and deployed cryptojacking malware.
- Unpatched Vulnerabilities: Attackers love unpatched systems. Cryptojackers often exploit vulnerabilities in Apache servers, for example, to spread cryptomining malware across networks.
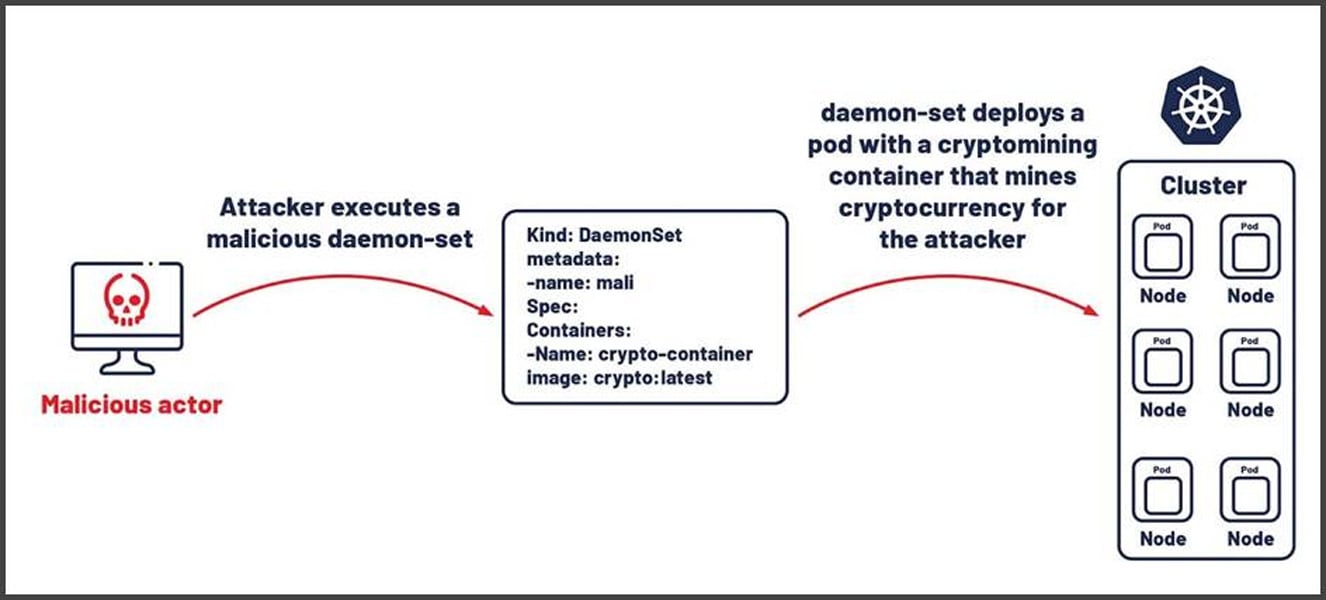
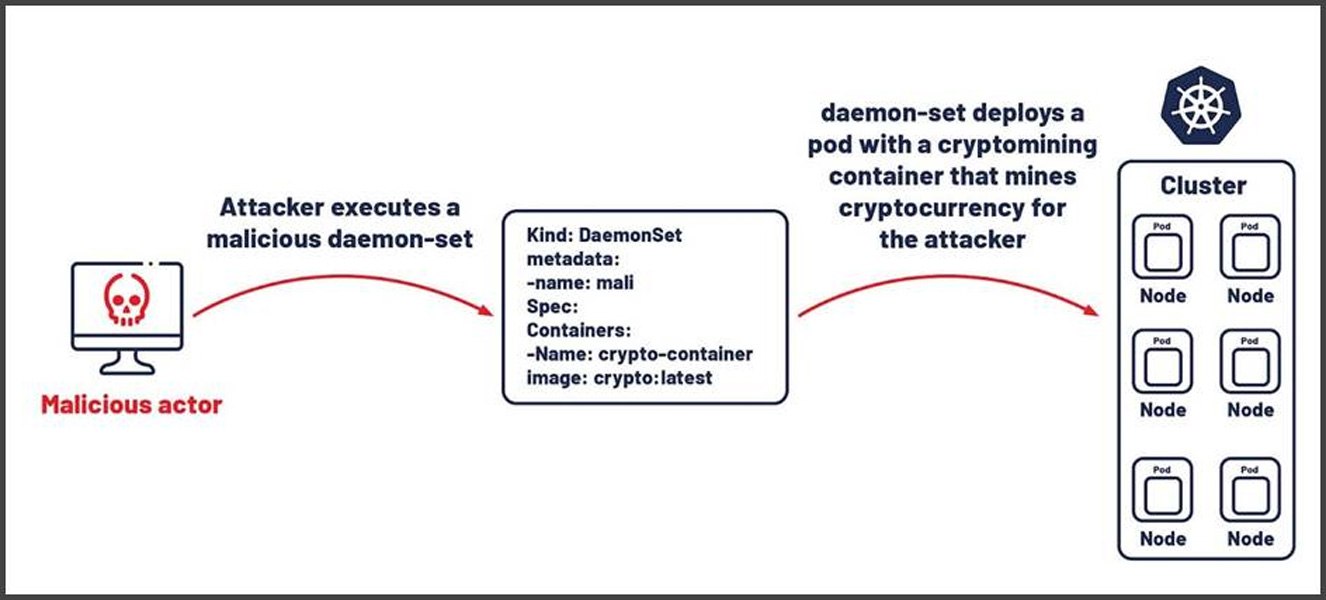
- Containerized Environments: As more companies adopt containers, cryptojackers are embedding mining scripts within container images stored in public repositories. The 2024 Commando Cat campaign exploited exposed Docker APIs to deploy cryptominers.
Why Should You Care? The Real-World Impact of Cryptojacking
While cryptojacking might seem like a minor inconvenience compared to data theft, its impact can be far more costly than most businesses realize.
- Performance Takes a Hit: Cryptojacking drains your CPU and GPU resources, which slows down your systems. This results in sluggish performance, making it difficult for your servers to handle legitimate traffic. Additionally, the excessive power consumption increases energy bills, strains hardware, and can lead to overheating or equipment damage. Users experience delays and productivity suffers.
- Cloud Costs Surge: Cryptojacking on cloud environments can lead to skyrocketing bills. Since cloud providers charge based on resource usage, compromised virtual machines or containers running mining malware consume vast amounts of CPU, GPU, and memory, resulting in unexpected and often astronomical bills.
- Downtime and Productivity Losses: Overworked systems can crash or slow down to the point where operations grind to a halt. It may not lock you out like ransomware, but cryptojacking can cause significant productivity loss.
- Security Vulnerabilities: Cryptojackers often exploit the same vulnerabilities that can lead to larger, more damaging attacks. Given that they already have a foothold on the compromised resource, the attacker can leverage that at any time to take a different attack tactic for further system compromise - a common secondary risk of cryptojacking.
Real-World Case Studies: Where Cryptojacking Hits Home
Cryptojacking doesn’t just target smaller organizations. Major enterprises across industries, from tech to healthcare, have fallen victim to these attacks.
A tech company saw its AWS cloud resources hijacked for cryptomining, resulting in $100,000 of unexpected cloud costs. Meanwhile, a healthcare provider experienced critical performance issues, with cryptojacking slowing down their systems and indirectly exposing sensitive data.
In 2024, incidents surged across multiple sectors. The notorious TeamTNT group exploited exposed Docker daemons, compromising cloud infrastructure, while another campaign targeted Docker Engine APIs to infiltrate containerized environments.
Even enterprise-grade tools weren’t spared: a critical Atlassian Confluence vulnerability allowed attackers to deploy XMRig miners within corporate networks. Misconfigured Kubernetes clusters became a prime target for deploying Dero miners, while the Migo malware compromised Redis servers by disabling security features to hijack computing resources.
This growing threat underscores the importance of proactive defenses to avoid potentially devastating financial and operational consequences.
How to Detect and Prevent Cryptojacking: Practical Solutions
To stay ahead of cryptojackers, organizations need a proactive, multi-layered defense. Here’s how to get started:
- Endpoint Protection: Today’s endpoint security tools often include cryptojacking detection. They monitor spikes in resource consumption and flag unusual activity, alerting admins to cryptomining scripts before they cause significant harm.
- Network Monitoring: Cryptojacking often leaves traces in network traffic. Tools that analyze traffic patterns for unusual connections to mining pools which are networks that combine computing power from compromised systems to mine cryptocurrency more efficiently can help detect and prevent cryptojacking early on.
- Cloud Monitoring: Platforms like AWS CloudWatch and Azure Monitor can help track spikes in CPU or GPU consumption. A sudden jump in resource consumption could be a sign of cryptojacking.
But it’s not enough to simply deploy these tools. They need to be configured correctly and continuously updated to ensure they’re effective against the latest cryptojacking threats.
Continuous Validation: Keeping Your Defenses Strong
Even the most advanced tools can’t guarantee 100% protection. Without regular testing and validation, gaps in your defenses may still exist. This is where continuous security validation comes in.
Continuous validation ensures your defenses are always up-to-date by safely emulating cryptojacking attacks.
Using safe versions of replicated cryptojacking malware, test how well your systems can withstand an attack before your environment is challenged in the wild.
The Bottom Line
Cryptojacking may be stealthy, but its impact is anything but. From inflated cloud bills to sluggish performance and indirect security risks, it’s a growing threat that companies can’t afford to ignore. But with a proactive approach organizations can stay ahead of cryptojackers and keep their resources protected.
By continuously testing your systems with Pentera, you’ll know whether your defenses are strong enough to block cryptojacking before it costs your business more time, money, and security.
Get in touch with Pentera for a demonstration.
Sponsored and written by Pentera.
如有侵权请联系:admin#unsafe.sh