2025-1-27 14:0:0 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
Executive Summary
As part of our ongoing mission to identify emerging threats to mobile security, our zLabs team has been actively tracking a phishing campaign impersonating the United States Postal Service (USPS) which is exclusively targeting mobile devices. This campaign employs sophisticated social engineering tactics and a never-before-seen means of obfuscation to deliver malicious PDF files designed to steal credentials and compromise sensitive data.
Background
PDF (Portable Document Format) documents have become an indispensable tool in the enterprise landscape, offering a universal and reliable way to share information across platforms and devices. Renowned for their consistent formatting, ease of use, and compatibility, PDFs are used extensively for contracts, reports, manuals, invoices, and other critical business communications. Their ability to incorporate text, images, hyperlinks, and digital signatures while maintaining integrity makes them ideal for enterprises prioritizing professionalism and compliance. Due to their ubiquitous use and appearance to be ‘tamper-proof’, users have developed a natural, but dangerous, assumption that all PDF’s are safe. And now, cybercriminals are actively exploiting that false confidence.
The widespread use of PDFs is introducing significant security risks to the enterprise, particularly when targeted to mobile devices. PDFs have become a common vector for phishing attacks, malware, and exploits due to their ability to embed malicious links, scripts, or payloads. On mobile platforms, where users often have limited visibility into file contents before opening, these threats can easily bypass traditional security measures. The portability and accessibility that make PDFs so valuable also means that sensitive data can be inadvertently exposed if proper protections are not in place. Without robust mobile threat defense mechanisms, particularly on-device scanning, enterprises face the risk of data breaches, credential theft, and compromised workflows via seemingly harmless PDF files.
Findings
The investigation into this campaign uncovered over 20 malicious PDF files and 630 phishing pages, indicating a large-scale operation. Further analysis revealed a malicious infrastructure, starting with landing pages designed to steal data, that could potentially impact organizations across 50+ countries. This campaign employs a complex and previously unseen technique to hide clickable elements, making it difficult for most endpoint security solutions to properly analyze the hidden links.
In this blog, we will detail this innovative evasion technique and demonstrate how Zimperium’s Mobile Threat Defense (MTD) solution effectively detects malicious files leveraging such methods, providing essential protection against these evolving PDF and mishing threats.
Composition of the Mishing Campaign
There has been a significant increase in mishing campaigns overall, with PDFs now emerging as a notable attack vector used to exploit mobile users. This tactic leverages the perception of PDFs as safe and trusted file formats, making recipients more likely to open them. One such campaign we observed is delivered through SMS messages and includes a PDF file containing a malicious link (Fig. 1). The original PDF sample analyzed by our zLabs team features deceptive text designed to redirect users to a fraudulent website, aiming to steal sensitive information. Notably, the PDF employs an unconventional technique to embed the malicious link, allowing it to bypass detection by numerous endpoint security solutions. This strategy highlights the evolving tactics of cybercriminals, who exploit both trusted file formats and advanced evasion methods to deceive users and compromise their data.

Introduction to PDF Format
As mentioned earlier, the PDF provides a reliable, platform-independent way to present documents, ensuring consistent display across various operating systems and software environments. PDFs can incorporate a wide range of content, including text, images, hyperlinks, video, 3D models, interactive forms, and more.
The structure of a PDF is hierarchical and consists of four main components: the header, body, cross-reference table, and trailer. The header defines the PDF version used in the document. The body contains the objects that outline the document’s layout and structure. These objects, which can reference each other, include:
- Names: Used for assigning unique identifiers.
- Strings: Represent text and are enclosed in parentheses (…).
- Arrays: Ordered collections of other objects, delimited by square brackets […].
- Dictionaries: Key-value pairs, where keys are Name objects and values can be any other object type. Dictionaries are enclosed in double angle brackets <<…>>.
- Streams: Contain embedded data, such as images or code, which may be compressed. Streams are represented by a dictionary specifying the stream’s length using the /Length key and encoding using /Filters.
- Indirect Objects: Objects with unique IDs, defined by the “obj” and “endobj” keywords. Other objects can reference them using these IDs.
The cross-reference table stores the byte offset of each object within the file, enabling random access and efficient retrieval. Its entries point to the location of each object. The trailer provides a reference to the cross-reference table and to the document’s root object, facilitating proper document loading by the PDF reader.
Analysis of the Malicious PDF
In PDF files, links are typically represented using the /URI tag. This tag is part of an Action Dictionary object, specifically within a Go-To-URI action, which instructs a PDF viewer to navigate to a Uniform Resource Identifier (URI), usually a web address (URL).
An example of a Go-To-URI action dictionary appears as follows:

Where:
- /Type /Action: Identifies this dictionary as an action.
- /S /URI: Specifies the action type as “Go-To-URI”.
- /URI (http://www.example.com): Contains the actual URI string. The URI is enclosed in parentheses.
The PDFs used in this campaign embed clickable links without utilizing the standard /URI tag, making it more challenging to extract URLs during analysis. Our researchers verified that this method enabled known malicious URLs within PDF files to bypass detection by several endpoint security solutions. In contrast, the same URLs were detected when the standard /URI tag was used. This highlights the effectiveness of this technique in obscuring malicious URLs.
Catalog object
The analysis of the malicious PDF began with the Catalog object (Fig. 2), which is fundamental to a PDF file’s structure. Acting as the entry point, it references critical elements like pages, metadata, and outlines (bookmarks). In this case, the Catalog object pointed to object 2, representing the root of the page tree, a dictionary of type /Pages. This root defines the hierarchical structure of the document’s pages.

Pages object
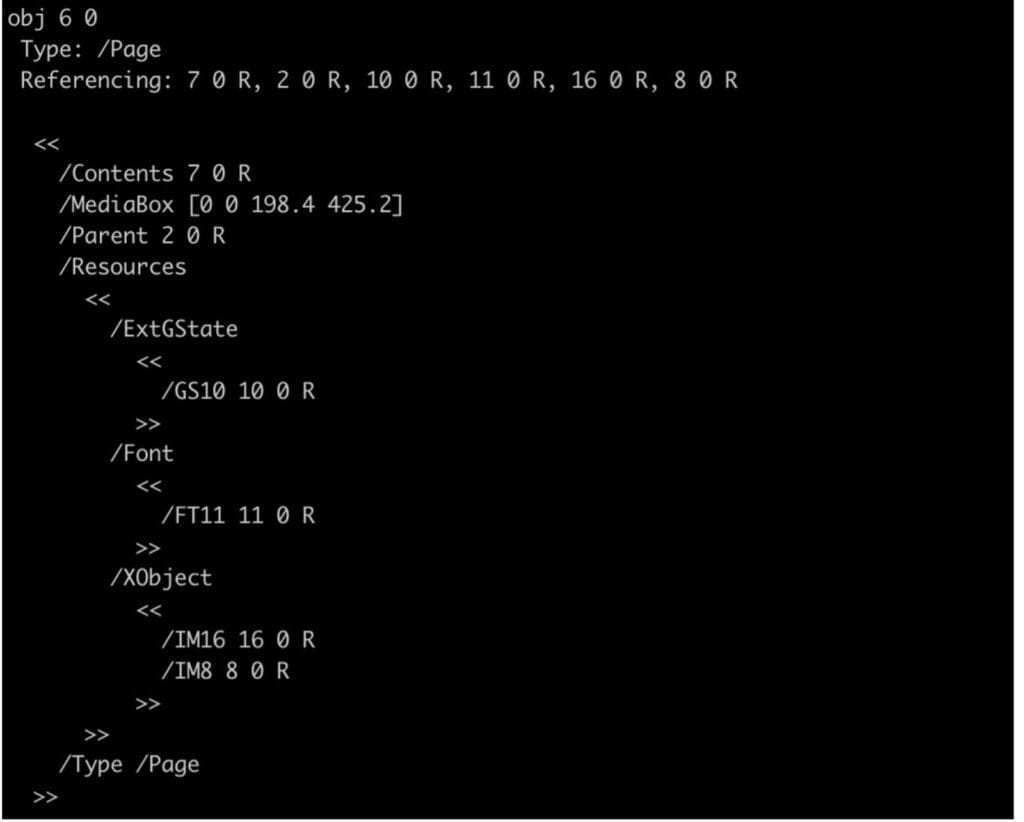
The /Pages object (Fig.3), another crucial part of the hierarchical structure of a PDF document, represents the root of the page tree and organizes the individual pages of the document. The /Kids entry is an array pointing to child objects. Here, it referenced object 6 0 R, representing a specific page within the PDF document. Each page is defined by a Page object, which outlines its contents, resources, and layout. Some of the key attributes of a Page object are:
- /MediaBox: Defines the size of the page.
- /Contents: References the content stream object(s) that describe the text, images, and graphics to be displayed on the page.
- /Resources: Contains references to all the resources (e.g., fonts, images, graphics states) required by the content on the page.


The Page object in this PDF (Fig. 4) contained several resources, including two XObjects. The /XObject entry (External Object) acts as a repository for external objects that can be reused within the content stream. These objects are essentially reusable content elements, like images, forms (Form XObjects), or PostScript fragments. In this case, the XObjects referenced two images (Fig. 5).

Font object
Another object referenced from the /Page object is the /Font object (Fig. 4).
Font objects define typefaces and include information like encoding and font data to ensure accurate text rendering. This object utilized the /ToUnicode attribute, pointing to object 12, which mapped character codes to Unicode values. This mapping enabled precise text extraction and search by correlating Character IDs (CIDs) with their Unicode equivalents. In this case the stream contains the map shown in Fig. 6.

| CID | Value | CID | Value | ||
| <0026> | U+0046 | F | <016C> | U+006B | k |
| <0057> | U+0050 | P | <016F> | U+006C | l |
| <005E> | U+0053 | S | <0175> | U+006D | m |
| <0068> | U+0055 | U | <0176> | U+006E | n |
| <007A> | U+0059 | Y | <017D> | U+006F | o |
| <0102> | U+0061 | a | <0189> | U+0070 | p |
| <010F> | U+0062 | b | <018C> | U+0072 | r |
| <0110> | U+0063 | c | <0190> | U+0073 | s |
| <011A> | U+0064 | d | <019A> | U+0074 | t |
| <011E> | U+0065 | e | <01B5> | U+0075 | u |
| <0128> | U+0066 | f | <01C0> | U+0076 | v |
| <0150> | U+0067 | g | <01C7> | U+0079 | y |
| <015A> | U+0068 | h | <0357> | U+003A | : |
| <015D> | U+0069 | i | <0358> | U+002E | . |
| <0169> | U+006A | j | <036C> | U+002F | / |
The Character IDs (CIDs) from the table above are available to be used in object 6 (the /Page object).
Object 6 defines various resources and references an additional object, object 7, as its content source. Object 7 is a stream object compressed using the Flate algorithm, requiring decompression (“deflation”) before its contents can be examined.

Decompression of the stream reveals the underlying elements, specifically describing the page’s graphical and textual operations, as illustrated in the accompanying image Fig.8.

This stream holds the structure used by PDF readers to render links and text. Some text, such as “Text 3,” may not be immediately visible, as depicted in Fig. 7. Decompressing the stream reveals the underlying components, detailing the graphical and textual operations of the page, as shown in Fig. 8. The stream includes PDF content operators, which instruct the viewer on how to render the page’s content. Among these, the link associated with the “Text 3” object is embedded, allowing it to be clickable despite the text itself being hidden. While various operators are used, the Tj operator is commonly employed to display text strings, directing the viewer to render the specified text.
The operators used to create hidden, clickable text are as follows:
- BT and ET: Begin and end a text object.
- 1 1 1 RG: Sets the stroke color to white.
- 1 1 1 rg: Sets the fill color to white.
- Tf: Sets the font and font size, in this case /FT11 281 Tf (FT11 is declared in the obj 11 explained above)
- Tm: Sets the text matrix,
- Tj: Shows a text string
- TD: Moves the text position.
The Tj operator is typically used to display text strings enclosed in parentheses. In this case, it utilizes a font named /FT11, defined in object 11. This specific font uses the previously described character mapping scheme to obscure the actual URL, “https[:]//jytdnuspsjrf[.]com/update/,” within the displayed text.
This obfuscation technique is further enhanced by placing object 16 (an XObject) in the middle of the written URL, creating the appearance of a clickable button. While this method is effective in certain PDF viewers, such as Chrome and macOS Preview, it may not function in others, like the default Ubuntu Linux viewer (Evince). Here, the hidden text serves as a trigger for the clickable area defined by the XObject.
Landing Page
Upon clicking the “Click Update” button, the user was redirected to a USPS phishing webpage (Fig. 9) that simulated a delivery issue.

Users were prompted to provide personal details, including name, address, email, and phone number (Fig. 10).

Upon clicking the “Update Immediately” button (Fig. 11), a subsequent form requested further information, where the entered data was packaged up, encrypted, and transmitted to a malicious Command and Control (C&C) server while also being stored locally in the user’s browser.

An analysis of the malicious webpage’s JavaScript code revealed that the local storage keys were MD5 hashes of variable names. The values were JSON objects containing the victim’s submitted information, encrypted using the Rabbit stream cipher. This stored data enabled the attackers to identify whether a user had already completed the first form, allowing them to bypass it if the information was already present.

Additionally, to verify the validity of the provided credit card details, the malicious JavaScript leverages the API from the external service https://binlist.net/.
An analysis of the captured network traffic (Fig. 12) showed that the data was encrypted using the Rabbit stream cipher. Notably, separate keys were utilized for encrypting requests and decrypting server responses. The key “magicCat-response” was employed for decrypting responses, while “magicCat-request” was used for decrypting requests.

Finally, analysis of the webpage revealed multilingual support, indicating the attackers’ ability to target a wide range of countries and services to harvest confidential user data. This level of localization suggests this may be part of a phishing kit. The supported languages include:
Zimperium vs. Phishing and Malicious PDFs
Zimperium provides enterprises with robust protection against malicious PDFs, including those containing phishing links, through its advanced mobile security solutions. Leveraging its unique on-device AI-based detection engine, Zimperium can identify malicious PDFs and embedded phishing links in real time, even when devices are offline. By analyzing PDFs directly on the device, Zimperium ensures that privacy is never compromised, as no sensitive data is sent to the cloud for analysis.
With Zimperium, enterprises gain a comprehensive defense against evolving PDF-based attacks, including sophisticated phishing campaigns and zero-day exploits. This approach not only protects sensitive data and systems but also ensures user privacy, enabling organizations to maintain security, productivity, and compliance in an increasingly hostile threat landscape.

Fig.14: Zimperium Phishing detection
IOCs
The IOCs for this campaign can be found here.
The post Hidden in Plain Sight: PDF Mishing Attack appeared first on Zimperium.
*** This is a Security Bloggers Network syndicated blog from Blogs Archive - Zimperium authored by Fernando Ortega. Read the original post at: https://www.zimperium.com/blog/hidden-in-plain-sight-pdf-mishing-attack/
如有侵权请联系:admin#unsafe.sh

