January 27, 2025 4 Minute Read 2025-1-27 14:0:0 Author: www.trustwave.com(查看原文) 阅读量:11 收藏
4 Minute Read
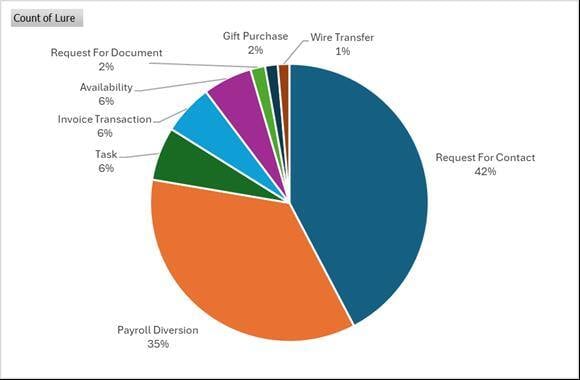
There was some good, bad, and neutral news when it comes to email threats in December 2024, according to new data compiled by Trustwave SpiderLabs’ MailMarshal email security team. Trustwave SpiderLabs’ PageML, which is used in MailMarshal’s Blended Threat Module (BTM), flagged 19 million malicious URLs for VirusTotal, of which 2.2 million detections were only picked up by Trustwave. The team reported that 25% of all incoming spam emails were in fact phishing attacks of some type. This was driven by huge Japanese phishing campaigns and the use of various phishing-as-a-service platforms (PaaS). Trustwave SpiderLabs found the increasing use of legitimate and semi-legitimate Remote Monitoring and Management tools (RMM) used in attacks. The positive finding was that the number of malicious attachments noted in these attacks was down 1% for the month. On the neutral side of the conversation, Trustwave SpiderLabs noted threat groups continued to use HTML and PDF attachments to launch phishing and malware attacks. Additionally, QR phishing (or quishing) and HR-themed phishing campaigns remained ongoing. Let’s examine what malware and methodologies attackers used to inject into their target’s organization. The most common executables, which are frequently enclosed in ZIP and RAR archives, found by Trustwave SpiderLabs in December include: Trustwave SpiderLabs found that PDFs were also commonly used in malware and spam campaigns. PDF files can be embedded with malicious scripts or links, making them a popular choice for attackers. PDF files with phishing links were often found in documents for fake job offers and invoices. The team found that HTML attachments continued as the number one malware attachment. This is likely because HTML attachments are easily disguised as legitimate emails. These are often used to redirect users to phishing websites or to deliver malicious code. Notably, the Tycoon 2FA campaign leveraged HTML attachments to mimic Office 365 two-factor authentication portals, tricking users into entering their login credentials and one-time passcodes. December saw HTML as the favored type of attachment, being used 36.7% of the time, followed by PDFs, 27.3%, and EXE23, 18.3%. HTML and PDF files for phishing were fueled by PaaS kits like Tycoon and Rockstar2FA. These kits are favored due to their easy-to-use tools, which allow attackers to bypass email filters and redirect victims to phishing pages. These often mimic Office 365 login screens. To a lesser extent, phishers are using DOC and XLS files. Other findings in phishing attacks included: BEC emails are overwhelmingly sent via free webmail platforms. This chart shows the top freemail sources for BEC in MailMarshal Cloud from the last month. However, BEC emails sent using mass mailing platforms were continued from November into December, with around 250 samples received through MailMarshal Cloud. Some recent trends include: The pie chart below shows the types of BEC lures used in the message body over the last month. The top lure is still Request for Contact where threat actors are sending short emails asking for mobile number/WhatsApp contact. Luckily, Trustwave receives multiple samples of what threat actors use for their phishing attacks, so we can give you a quick look at how they look, read, and attempt to fool the recipient. Some emails were a bit specific about the topic, such as client request. In this example, the fraudster invites the victim to a meeting or discussion. This is used as a pretext to ask for the victim’s phone number. Now let’s see how the various spam “themes” were used in December. As noted earlier, phishing emails now comprise about 25% of all spam sent. This mass phishing capability is driven by PaaS platforms and other phishing kits. Powered by advanced AI, MailMarshal is a Secure Email Gateway that blocks phishing, BEC, and malware threats that other solutions overlook, including complex threats hidden in images and QR codes. MailMarshal’s Key Features: Trustwave MailMarshal doesn’t just check the box—it transforms email security into a strategic advantage for organizations looking to protect against the ever-evolving threat landscape. By combining advanced technology and real-time intelligence, MailMarshal offers unmatched threat prevention, reduces risk, and strengthens security resilience across your organization.Malware
Email Malware Attachment Types: Last Month
December’s Business Email Compromise (BEC) Findings

Figure 1. Top freemail sources for BEC in MailMarshal Cloud from the last month.

Figure 2. Types of BEC lures used in the message body over the last month.What a BEC Email Looks Like

Figure 3. Email example, in which the fraudster invites the victim to a meeting or discussion.Email Spam Types: December

Figure 4. Spam type distributions.How Trustwave MailMarshal Protects Against Email-Based Attacks
Secure Your Email Now with Trustwave MailMarshal
如有侵权请联系:admin#unsafe.sh