OverviewPIXM recorded a massive uptick in spearphishing activity as employees returned to wor 2025-1-25 20:46:5 Author: pixmsecurity.com(查看原文) 阅读量:18 收藏
Overview
PIXM recorded a massive uptick in spearphishing activity as employees returned to work following the holidays and January snow storms. These included sophisticated business email compromises, password protected Google Docs shares and targeting corporate credentials on personal email accounts. We also saw an uptick in Amazon attacks in particular. Here are some examples and highlights.
Phishing URLs
Here is a list of examples of phishing websites that we discovered that we recommend you update your threat intelligence with these URLs.
dcvnewsyr1[.]dcrdcoveris[.]top/
zn[.]pemitolax[.]ru/
ultracustomgroup[.]appsforcourt[.]com
shaftdrillers[.]appdocumentvault[.]com
r.bitualicar[.]ru
resonant-abaft-timpani[.]glitch[.]me
amy4standardelectricc[.]org
managesafety[.]zem[.]gjb[.]mybluehost[.]me
continuesignin-amznprime[.]makosi[.]com
manageaccounts[.]calcadosvip[.]com/
Password Protected Google Doc from a Trusted Sender
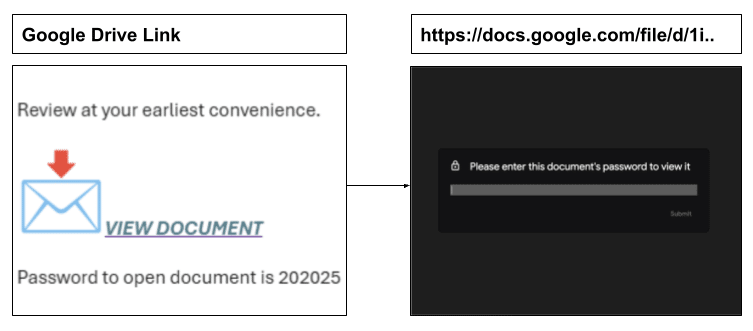
On Jan 7, a staff member at a Washington organization received a spearphishing email from a valid sender address at a partner educational organization. The spearphishing email contained a link to a password protected Google Doc file along with the password required to open the file.
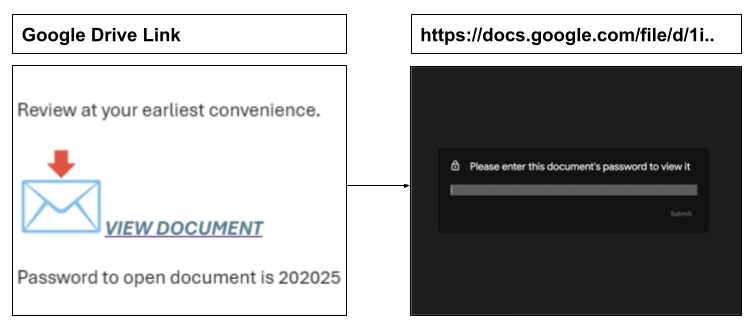
Upon clicking the link, the staff member was directed to a Google Docs site and prompted to enter the password.
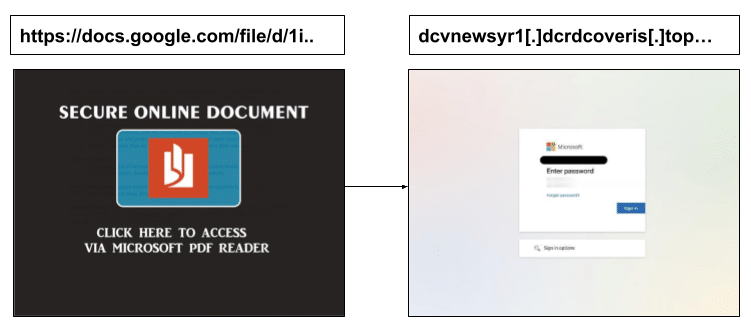
After entering the password, the user sees a ‘Secure Online Document’, prompting them to access via Microsoft PDF reader. Clicking this, in turn, led them to a zero day credential harvester.
Attacks like this standout because they incorporate numerous stealthy features. They involve a trusted mailbox at a partner organization that has been compromised. Like other widespread phishing campaigns delivered within Google infrastructure, this one is delivered via Google docs. It further evades any mailbox security architecture by requiring a password to resolve the link. Finally, only when a real user enters the password and clicks the PDF reader are they directed to the phishing page.
Corporate Credentials Clicked Outside of a Corporate Mailbox
Across organizations in Texas and Georgia, many phishing attacks got clicked that targeted corporate credentials but that failed to even leave a trace in the corporate mailbox. These were all likely clicked in the personal mailbox or other business collaboration applications. Many of these were hosted on Russian infrastructure and, based on the domain structure, were created using a common domain generation algorithm (DGA).
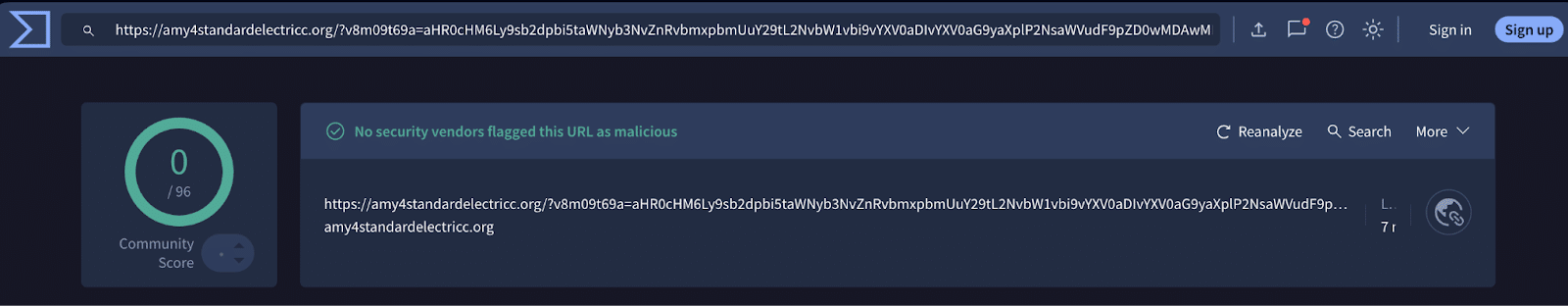
Since these are delivered outside the scope of corporate mailbox protection, they commonly go undetected for long periods of time by the community of security vendors.
Other notable tactics included emails with subjects referring to translating voice messages that mimic similar communications within their organization. We also saw a large uptick in Amazon phishing attacks targeting folks’s personal accounts on their work devices.
Suggested Actions
- Add the specified domains above to your block lists.
- Focus awareness efforts on high-risk credentials.
- Educate users that phishing in their personal email can pose serious risks to their organization.
- Educate users that phishing attacks can be delivered via password protected attachments as well as via legitimate Google infrastructure.
If you would like a demo of Pixm to learn more about our AI technology and how we can help protect your customers, sign up here.
Questions or Feedback
PIXM Threat Research Team
[email protected]
如有侵权请联系:admin#unsafe.sh
