2025-1-24 16:0:44 Author: securityboulevard.com(查看原文) 阅读量:1 收藏

If you spend time on video game forums, you might have noticed posts from users discussing their accounts being hacked or stolen, often mentioning the loss of games or items linked to their accounts. At Castle, we know these incidents are often caused by credential-stuffing attacks, where bots exploit reused passwords, or phishing scams tricking users into giving up their credentials.
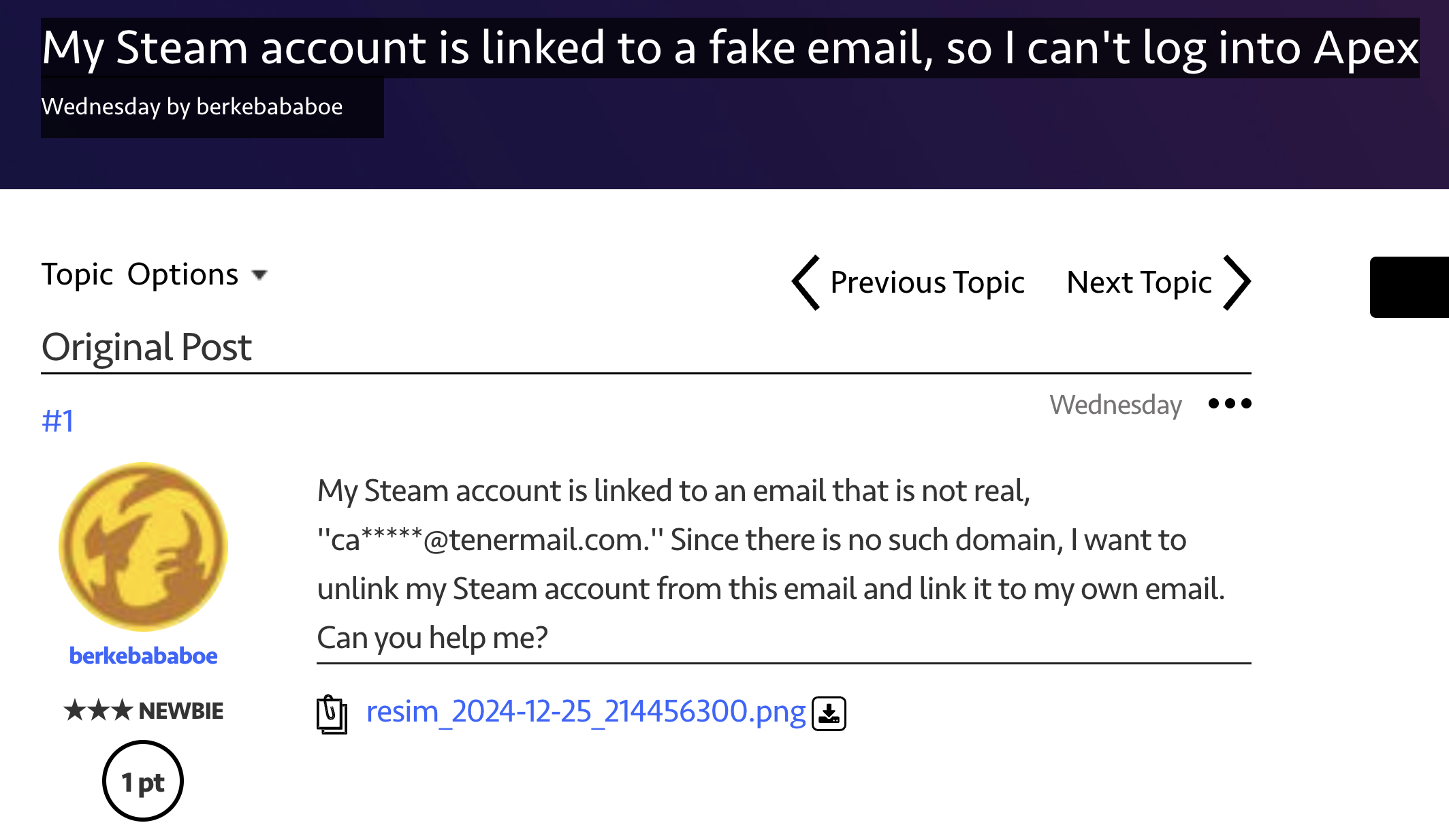
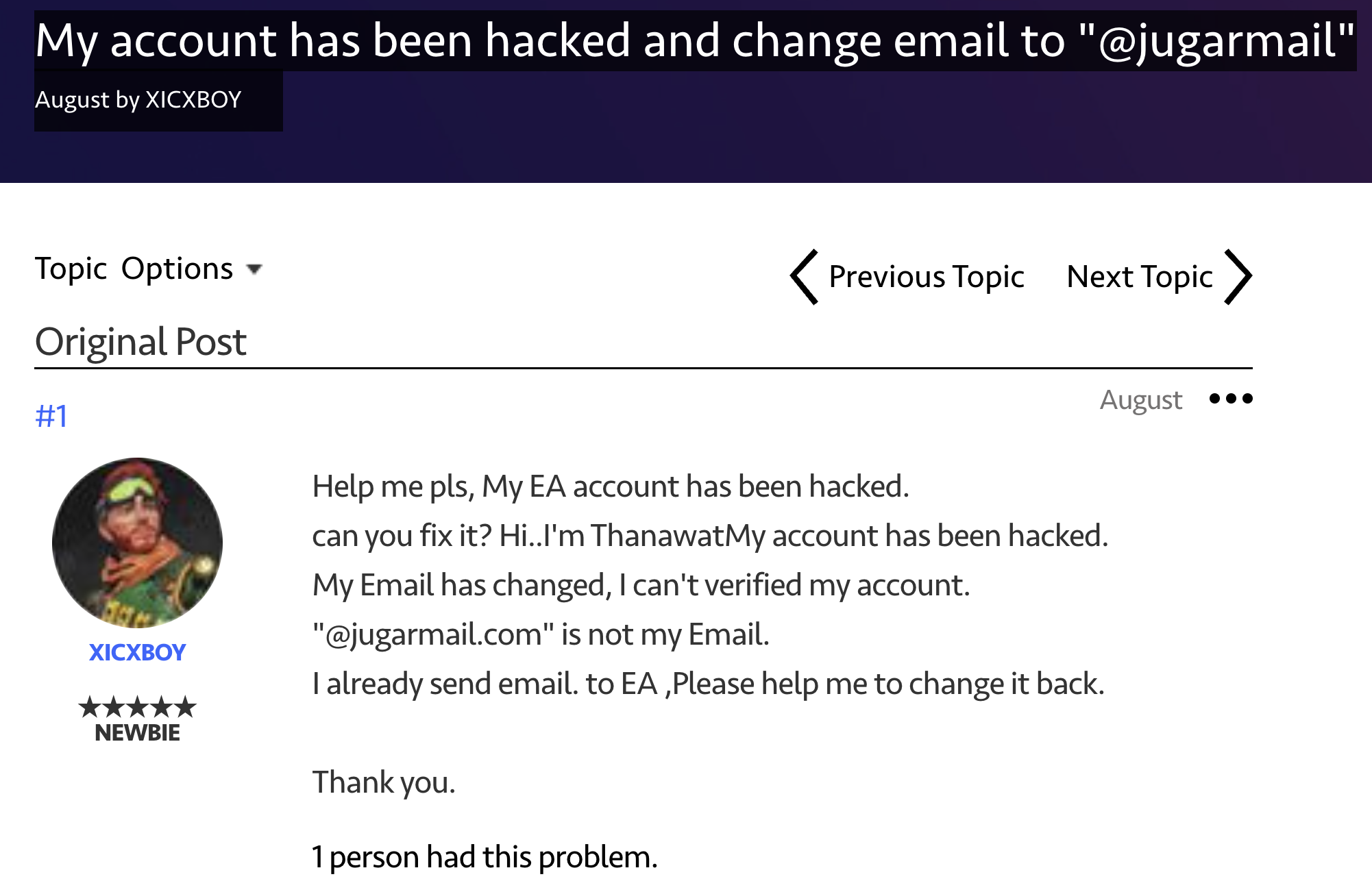
Why do fraudsters like to steal video game accounts?
The early days of video games where buying the game in a physical store was enough to play are over. The video game ecosystem has modernized, and so do fraudsters: you can buy your video games online, using the credit card registered on your preferred gaming platform. You can also buy shiny new skins and virtual game money to buy better in-game items.
It’s not uncommon for certain user accounts on gaming platforms and stores like Steam, to hold hundreds of video games. Thus, it’s tempting for fraudsters to steal these accounts to resell them on specialized marketplaces.
The screenshot below, taken from lolz[.]market, shows how fraudsters can easily upload stolen accounts in batches using the “Mass upload” feature.
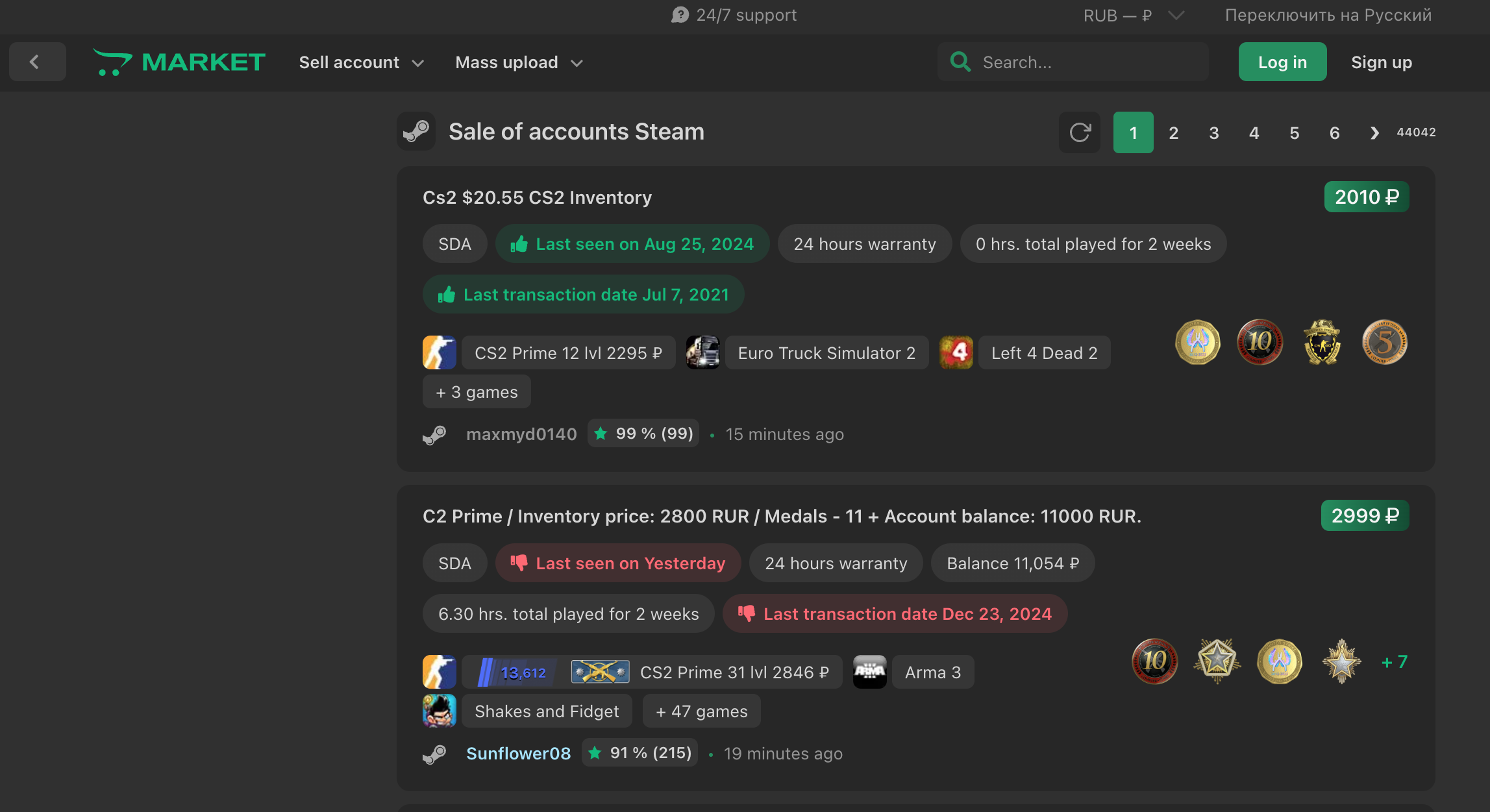
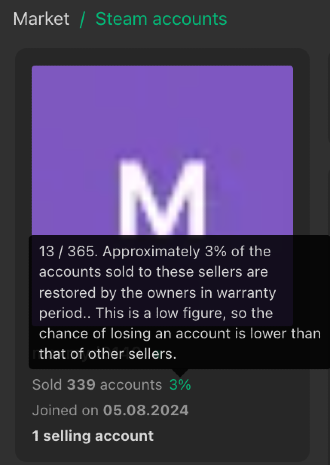
Certain sellers have sold more than 300 accounts.
But it doesn’t stop there, since certain users register their credit cards in their accounts, fraudsters can use these registered credit cards to buy video games or make in-app purchases from stolen accounts, cf screenshot below.
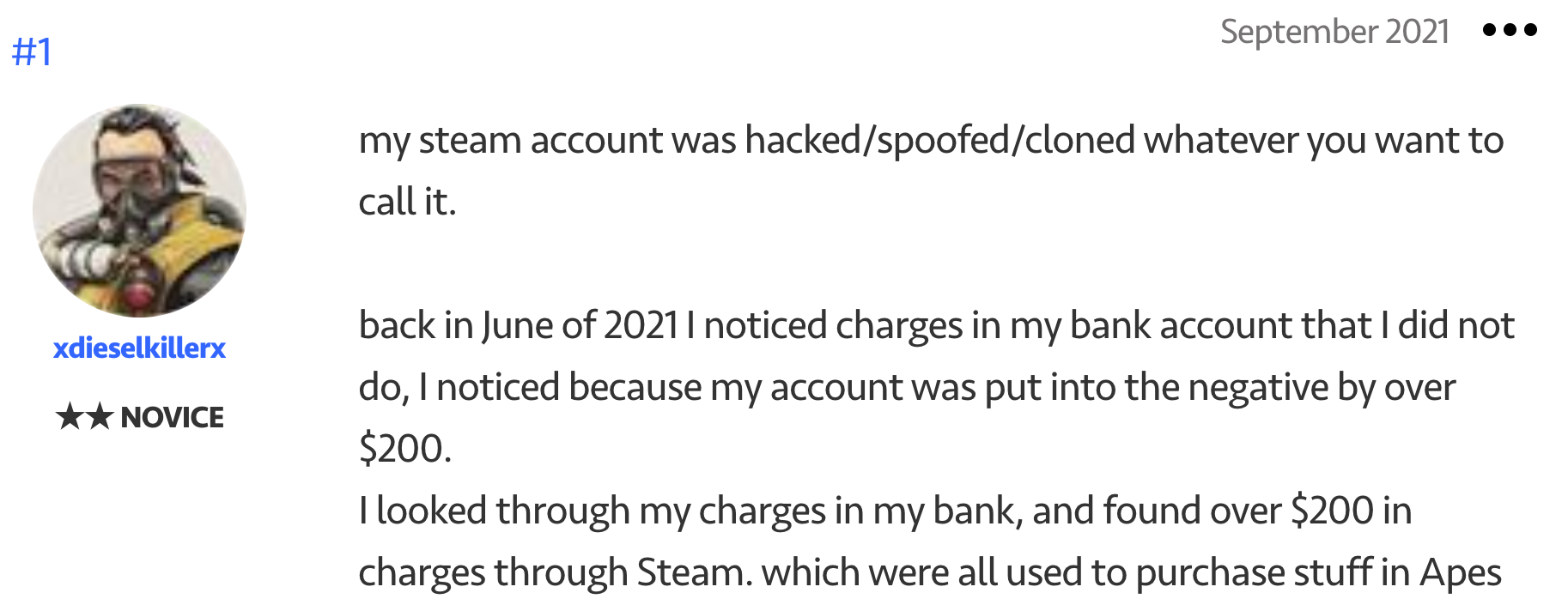
Once the registered credit is used to buy in-app money or stuff, it can be difficult to trace back the fraud if the in-app objects bought/money is transferred to another player.
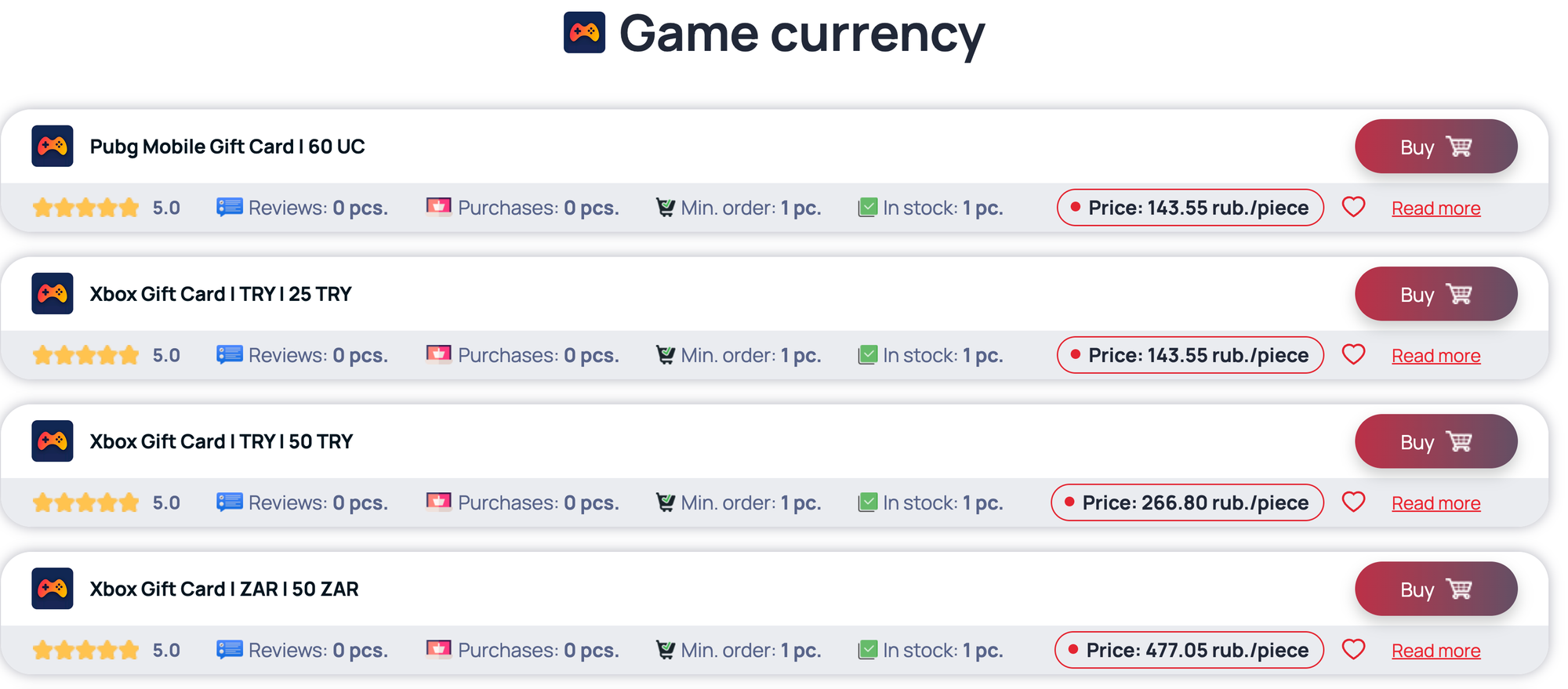
These credit cards can also be used to buy gift cards that can be resold against real-world money (cf screenshot below).
Besides gaming platforms, certain video game accounts can also be resold at a high value if the account has:
- A high level;
- Valuable in-game equipment/items;
- Skins.
Once compromised, attackers can either sell the whole account on a marketplace or against in-game money or sell the valuable in-game items against real/virtual game money.
Moreover, old accounts tend to have a better reputation than newly created accounts and can be used to conduct in-game scams or spread phishing links.
To summarize, fraudsters attempt to steal video game (platform) accounts to:
- Resell stolen accounts that hold several video games on gaming platforms like Steam/PSN etc
- Leverage the credit card(s) registered on the stolen accounts to buy video games or make in-app purchases
- Resell accounts with high-level characters or characters with valuable in-game items
- Leverage the trust of old accounts to conduct in-game scams and spread malware/phishing links
Account fraud is accessible to non-bot experts
A quick look into Telegram fraudster groups quickly exposes several Open Bullet configurations to conduct credential stuffing attacks, i.e. steal user accounts, against video game websites and gaming platforms.
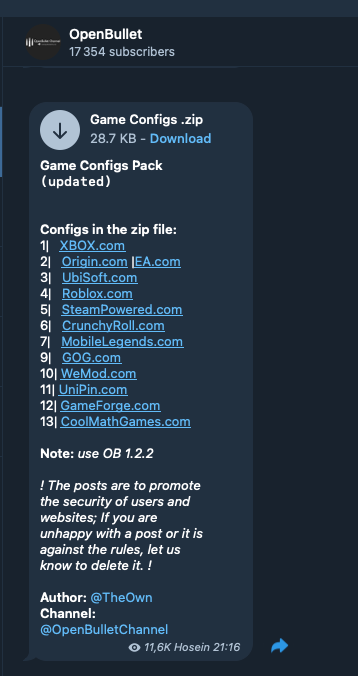
These open tools and bot attack configurations make it easy for non-expert users to conduct large-scale attacks against video game platforms, even when they implement basic protection techniques, such as IP-based rate limiting and traditional CAPTCHAs.
Consequences of account fraud for video games (platforms)
Successful credential-stuffing attacks conducted against gaming platforms can have different consequences:
- Loss of Trust and Reputation: Credential stuffing leads to stolen accounts and assets, frustrating users who lose trust in the platform. Negative experiences spread quickly online, pushing players toward competitors with better security.
- Legal and Regulatory Risks: Weak security can result in breaches that violate data protection laws like GDPR, leading to fines, lawsuits, and regulatory penalties that damage the company’s credibility.
- Financial Strain: Account fraud discourages spending, increases refund requests, and drives up support costs, cutting into profits and limiting the ability to invest in platform improvements.
Conclusion
Video game platforms are prime targets for credential-stuffing attacks, where fraudsters exploit compromised accounts for personal gain. Once they seize control, attackers often change account credentials to lock out the rightful owner. These accounts are then monetized in various ways, such as being sold on illicit marketplaces or used to make unauthorized purchases like gift cards, in-game items, and skins.
The consequences of such attacks extend beyond individual losses. Gaming companies may face a decline in player trust and reputation, exposure to legal and regulatory penalties, and reduced player spending due to security concerns. To maintain their credibility and financial stability, gaming platforms must prioritize robust security measures to protect their users from these pervasive threats.
Credential-stuffing attacks are a constant threat to video game platforms. Traditional methods alone are not enough to defend against these increasingly sophisticated attacks. That’s why Castle employs a multi-layered approach powered by advanced machine learning (ML), analyzing all available signals—from device fingerprinting to advanced residential proxy detection and user behavioral analysis.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Sebastian Wallin. Read the original post at: https://blog.castle.io/how-bots-and-fraudsters-exploit-video-games-with-credential-stuffing/
如有侵权请联系:admin#unsafe.sh

