2025-1-23 22:6:34 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
In today’s interconnected digital ecosystems, securing Non-Human Identities (NHIs) has become a critical focus. NHIs—representing machines, applications, containers, and microservices—outnumber human identities exponentially and serve as essential components in modern IT infrastructures. However, their growing volume and complexity have created a vast, dynamic attack surface.
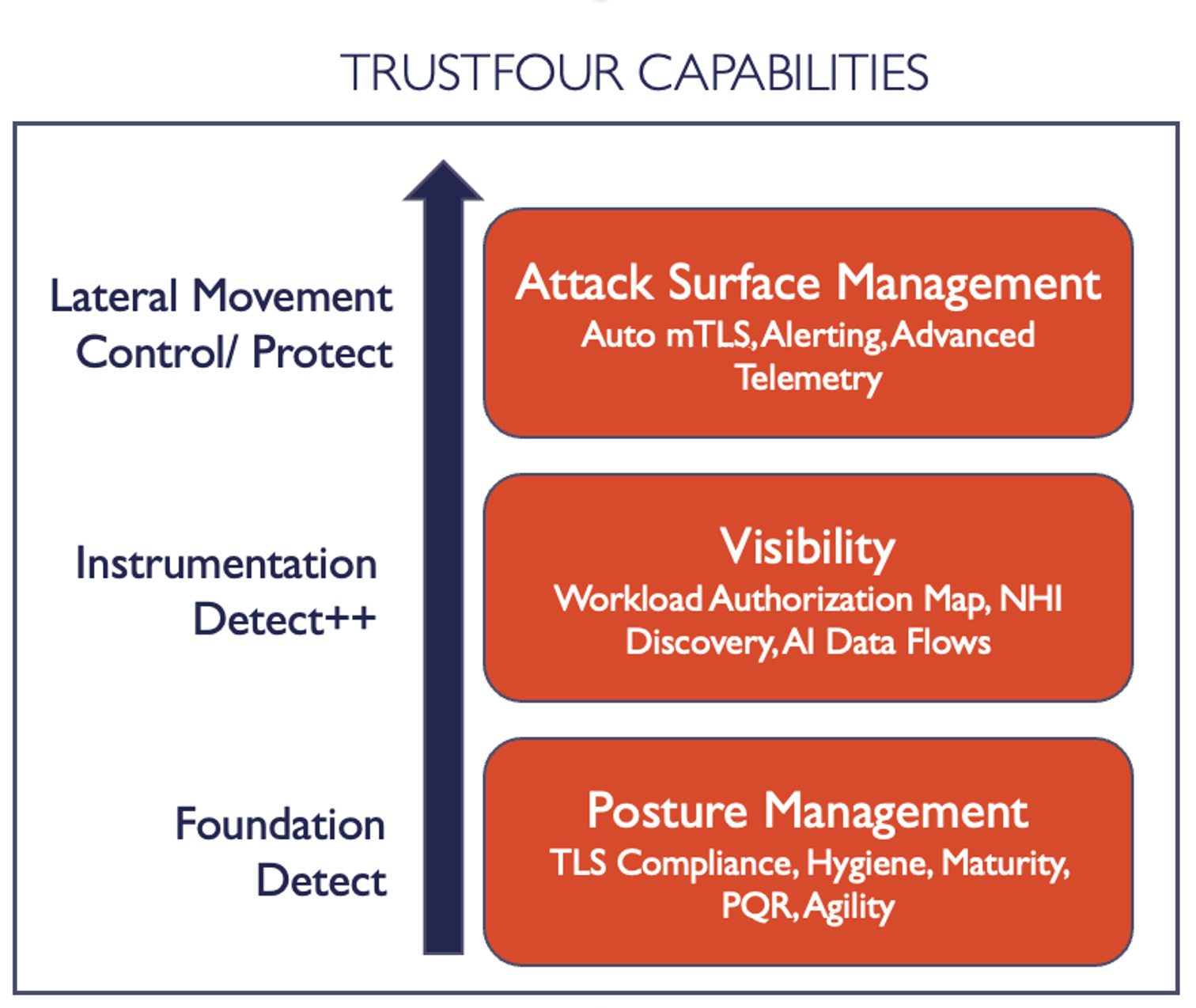
TrustFour addresses these challenges with its three-layer framework for NHI Posture and Attack Surface Management, a comprehensive approach that prioritizes compliance, visibility, and proactive defense. Let’s delve into each of these layers and explore how they collectively bolster NHI security.
Layer 1: Posture Management – Compliance Hygiene, Crypto Agility, and Cybersecurity Maturity
The foundation layer forms the bedrock of TrustFour’s framework, emphasizing posture management by ensuring that NHI environments are built on robust, compliant, and resilient foundations.
- Compliance Hygiene: This ensures adherence to industry standards and regulations governing identity management, encryption, and secure connections. NHIs often handle sensitive data and communications, making compliance essential to reduce regulatory risks and maintain trust.
- Crypto Agility: With cryptographic standards and protocols constantly evolving, maintaining agility ensures that systems can seamlessly adapt to newer algorithms and standards, protecting NHIs from vulnerabilities associated with deprecated cryptography.
- Cybersecurity Maturity: Organizations are encouraged to evaluate and enhance their NHI security capabilities over time. TrustFour provides metrics and benchmarks for continuous improvement, driving a culture of proactive security.
This layer ensures that NHIs are configured and managed with a strong baseline of security best practices, reducing the likelihood of misconfigurations and vulnerabilities.
Layer 2: Visibility – Discovery, Reporting, and Workload Authorization Mapping
Visibility is the cornerstone of effective security management. In this layer, TrustFour provides organizations with tools to gain comprehensive insight into their NHI environments.
- Discovery and Reporting: TrustFour identifies all NHIs in use within the live environment and compares this real-time data against records in identity providers. This ensures that only authorized identities are active and provides clarity into shadow NHIs that may evade traditional security oversight.
- Workload Authorization Maps: These maps illustrate the relationships and authorized connections between workloads, helping to visualize the intended communication paths and detect deviations. Unauthorized connections or unexpected traffic flows can indicate potential security risks or ongoing attacks.
By offering real-time visibility into NHI environments, TrustFour enables organizations to address discrepancies quickly, uncover hidden risks, and maintain an accurate understanding of their dynamic ecosystems.
Layer 3: Attack Surface Management – Auto mTLS, Advanced Telemetry, and Proactive Defense
The third layer focuses on attack surface reduction and threat management, leveraging cutting-edge technologies to prevent unauthorized lateral movement and detect malicious activity.
- Auto mTLS (Mutual Transport Layer Security): This feature ensures that all communication between workloads is encrypted and authenticated. By enforcing mTLS, TrustFour blocks unauthorized lateral movement, significantly reducing the blast radius of any potential breach.
- Advanced Telemetry: TrustFour collects and analyzes data from honeypots, tripwires, and application data-in-transit. This telemetry provides valuable insights into both normal and anomalous behaviors, enabling rapid detection of threats.
- Notable Alerting: Alerts are generated for any suspicious activity, including attempts to bypass mTLS, unauthorized connections, or deviations from workload authorization maps.
- AI-Driven Analysis: TrustFour leverages advanced AI engines to continuously analyze telemetry data, identify emerging threats, and refine security strategies.
This layer empowers organizations to proactively defend their NHI environments, mitigating risks before they escalate into critical incidents.
The Synergy of the Three Layers
The strength of TrustFour’s NHI Posture and Attack Surface Management framework lies in the synergy between its three layers:
- Posture Management ensures NHIs are built on secure, compliant, and resilient systems.
- Visibility provides the insights needed to understand and monitor the dynamic NHI environment.
- Attack Surface Management reduces risks and provides advanced tools to detect and mitigate threats.
Together, these layers create a robust, multi-faceted approach to NHI security, empowering organizations to maintain trust and resilience in their digital ecosystems.
Conclusion
As NHIs continue to play an increasingly vital role in IT infrastructures, securing them requires more than traditional identity and access management strategies. TrustFour’s three-layer framework for NHI Posture and Attack Surface Management provides a comprehensive solution, combining compliance hygiene, visibility, and proactive defense to address the unique challenges of NHI security.
By adopting this framework, organizations can significantly reduce their attack surfaces, enhance their security posture, and stay ahead of the evolving threat landscape. Whether it’s protecting critical workloads, ensuring secure communications, or proactively detecting threats, TrustFour’s approach ensures that NHIs remain secure and resilient.
如有侵权请联系:admin#unsafe.sh