
2025-1-23 15:45:27 Author: securityboulevard.com(查看原文) 阅读量:2 收藏

In November 2024, we investigated Docker Hub, the leading public container registry, uncovering a significant security issue affecting modern containerized environments. Our analysis of 200,000 publicly available Docker images revealed 30,000 unique secrets hidden within 19,000 images—a staggering 10% of the dataset.
As the most widely used container registry, Docker Hub stores millions of public images, many unintentionally exposing critical credentials, API keys, and other sensitive information. Our research focused on images tied to production environments, uncovering a troubling trend:
- 85% of secrets were embedded in cached image layers, which are immutable and often overlooked – not to mention deleted layers.
- Even more alarming, 1,200 secrets (4%) were active and verifiable, with some remaining valid for over a year. This highlights poor secret hygiene alongside the risk of exposure.
Adding to the severity, 99% of the images containing active secrets were pulled in 2024, demonstrating how quickly attackers could exploit exposed credentials in real-world scenarios.
These findings emphasize a critical vulnerability: as organizations increasingly adopt containerized workflows and rely on registries, they risk unknowingly exposing secrets. This opens the door for attackers, putting entire CI/CD pipelines and production environments at risk.
To address this challenge, we are excited to launch our secrets detection solution for leading container registries, including Docker Hub, JFrog Artifactory, Amazon ECR, Azure Container Registry, and Google Artifact Registry.
Why Container Security Registries Matter
Container images are the foundation of modern development, ensuring applications run consistently across environments, eliminating the "it works on my machine" problem by ensuring uniform behavior from local development to production. Their lightweight, portable nature enables seamless deployment across distributed infrastructures, making scalability straightforward. By combining reliability, flexibility, and efficiency, containers have become indispensable in software development.
Container Registries as the Foundation of Modern Development
Container registries are essential for storing and managing container images, acting as a centralized hub for deployment-ready resources. They provide:
- Centralized Storage: Registries securely store container images and metadata for retrieval during deployment.
- Repository-Based System: Images are organized into repositories with version tags, enabling easy access and management.
- Distribution Platform: Registries streamline the distribution of images across environments, from local testing to global production.
- Public and Private Options: Organizations can opt for public registries, private registries for internal usage only, or a mix of both.
Container registries are widely adopted because they address critical operational and security needs. By integrating seamlessly with CI/CD pipelines, registries enable rapid testing, deployment, and iteration.
However, their widespread use, proximity to production environments, and critical role in deployment pipelines make container registries an appealing attack surface for cybercriminals.
How Secrets End Up in Container Images and Registries
Secrets often end up in container images due to common mistakes during development and image creation. Key reasons include:
- Hardcoding Secrets in Code: Developers may directly embed sensitive credentials, such as API keys or passwords, into application code, which gets packaged into container images.
- Misconfigured Dockerfiles: Commands like ENV or RUN in Dockerfiles can inadvertently expose sensitive data during the build process.
Once embedded in images, these secrets are likely to be found in both public and private container registries, increasing the risk of exposure.
The Risks of Private Registries
While public registries are often scrutinized for security risks, private container registries can be even more prone to leaks due to a misplaced sense of safety within an internal perimeter. Organizations usually assume that private registries are inherently secure because they're not publicly accessible, leading to complacency in enforcing strict security measures. This "safe zone" mentality results in weaker access controls, less frequent vulnerability and secret scanning, and reliance on outdated or unverified images.
Introducing GitGuardian's Secrets Detection for Container Registries
GitGuardian's new integration enables secrets detection in 5 leading container registries, whether they're public or private:
- Docker Hub
- JFrog Artifactory
- Amazon ECR
- Azure Container Registry
- Google Artifact Registry
With these integrations, organizations can extend their monitored perimeter to include repositories within these container registries, scanning images for exposed secrets.
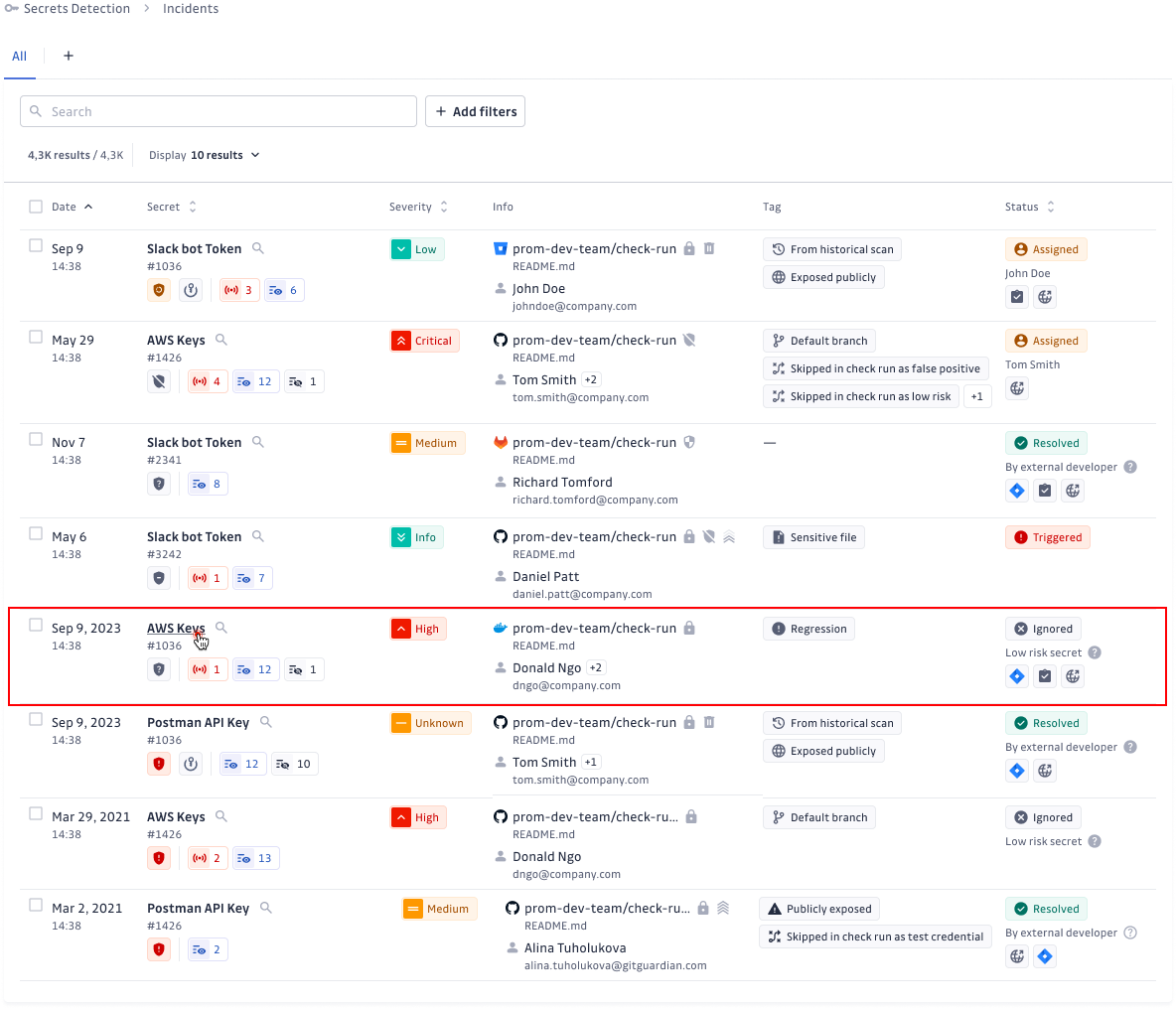
Our research into Docker Hub revealed that secrets in cached layers often persist unnoticed, making them a critical risk. GitGuardian's integration directly addresses this issue by scanning all layers, including cached ones, to uncover hidden vulnerabilities.
How to Get Started
Setting up any container registry integration is simple. Follow these steps to start detecting secrets in your container registries:
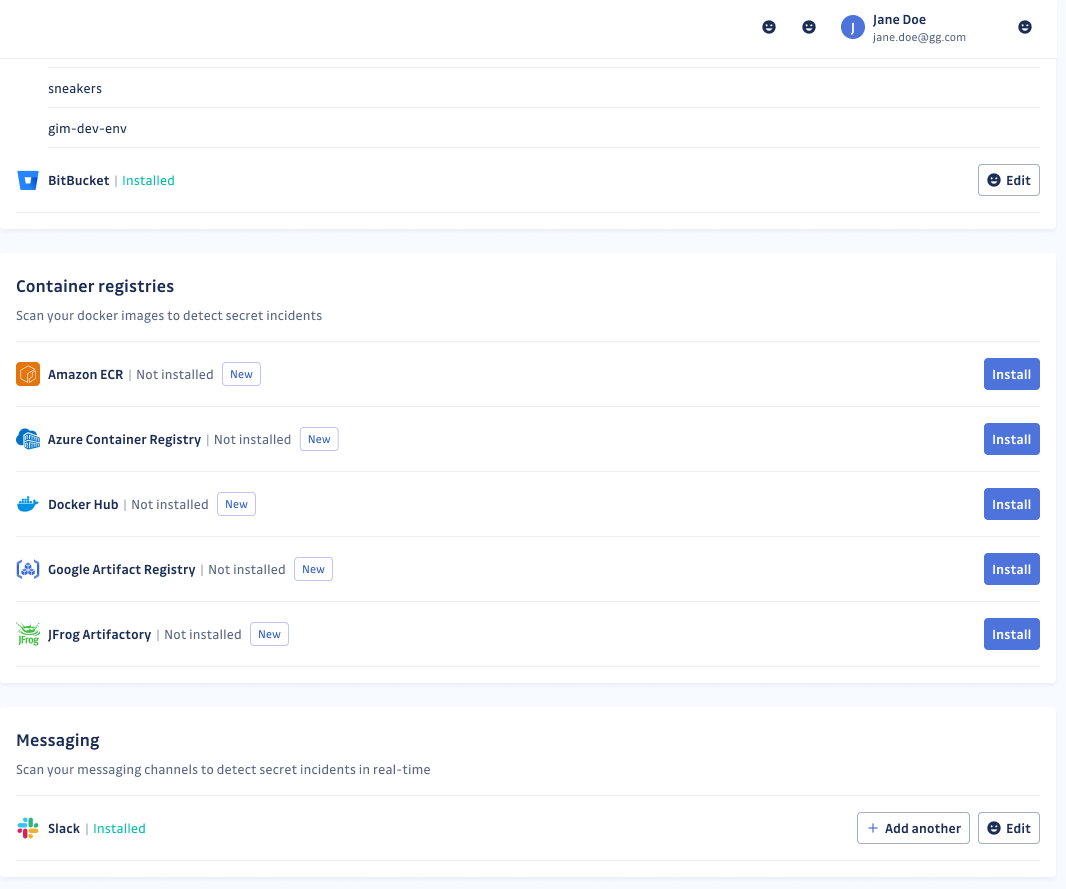
- Navigate to the Sources integration page
- Select the container registry you want to monitor
- Configure the integration
- Follow the guided workflow to connect your container registry to GitGuardian.
- Ensure you have the required permissions (Owner or Manager role) to complete the setup.
- Start monitoring!
Once integrated, GitGuardian will begin scanning all monitored repositories within your container registry for exposed secrets, and list incidents in your dashboard.
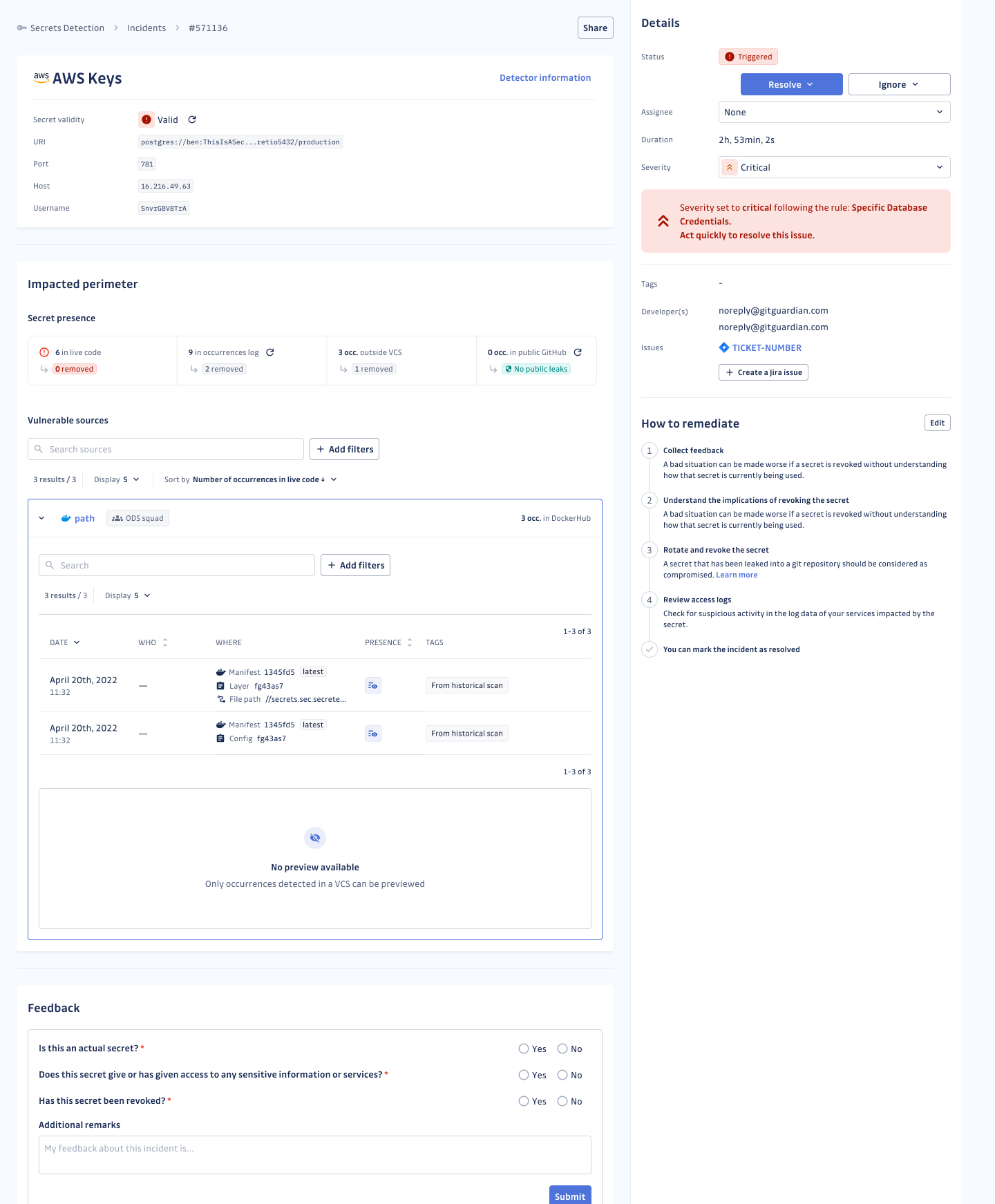
Best Practices for Securing Your Container Registry
By combining these best practices, organizations can establish a robust security framework for their container registries, significantly reducing the risk of exposure and ensuring a secure pipeline from development to production.
Start by Securing Your Images
The cornerstone of container registry security is ensuring that your images are secure before they are ever pushed to registries. Detecting and removing secrets during the build stage is essential to prevent inadvertent exposure and downstream vulnerabilities.
We've created a Docker Security Best Practices cheat sheet, designed for DevOps engineers and security professionals, and a guide on managing secrets in Docker effectively.
For a quick and impactful improvement, you can dramatically enhance your security with minimal effort by integrating ggshield into your workflow.
Shift Security Left
The earlier you identify and remediate vulnerabilities, the better. By adopting a shift-left approach, developers can catch security issues, including exposed secrets, during coding or build time rather than after deployment.
Integrating security tools, such as GitGuardian's ggshield, into your IDE or pre-commit hooks ensures secrets are caught and addressed as early as possible in the development lifecycle.
Implement Secrets Management
Secrets should never be embedded in container images. Instead, rely on dedicated secrets management solutions such as HashiCorp Vault, CyberArk Conjur, or AWS Secrets Manager to securely store and retrieve secrets.
GitGuardian's integrations with Secrets Managers provide organizations with centralized secrets visibility, reducing blind spots and enforcing vault usage. Eventually, this ensures that container registries remain secure.
Limit Access to Your Container Registry
Restricting access to container registries is fundamental to securing them. Use the least privileged access controls to ensure only authorized users and services can push or pull images. Regularly review and audit roles to prevent over-permission and enforce best practices.
Securing the Invisible Infrastructure
Secrets exposed in public or private container registries are not just vulnerabilities; they're a systemic risk that can compromise entire pipelines, threaten sensitive data, and erode trust in the software supply chain. This challenge is compounded by the false sense of security that private container registries often foster. But attackers do not discriminate; they exploit the weakest link, public or private.
To truly secure containerized environments, we need a paradigm shift. Security can no longer be an afterthought—it must be an integral part of the development lifecycle. From detecting secrets with ggshield when building images to leveraging GitGuardian integration with leading container registries, organizations must embrace a proactive, comprehensive approach to securing their infrastructure.
Take the first step towards securing your container registries. Contact our Customer Success team to become one of our first users.
*** This is a Security Bloggers Network syndicated blog from GitGuardian Blog - Take Control of Your Secrets Security authored by Ferdinand Boas. Read the original post at: https://blog.gitguardian.com/container-registries/
如有侵权请联系:admin#unsafe.sh

