Heavily obfuscated batch file loads XWorm hosted on GitHub
VMRay Labs found a multi-stage obfuscated batch script 2025-1-20 11:12:21 Author: www.vmray.com(查看原文) 阅读量:16 收藏
VMRay Labs found a multi-stage obfuscated batch script 2025-1-20 11:12:21 Author: www.vmray.com(查看原文) 阅读量:16 收藏
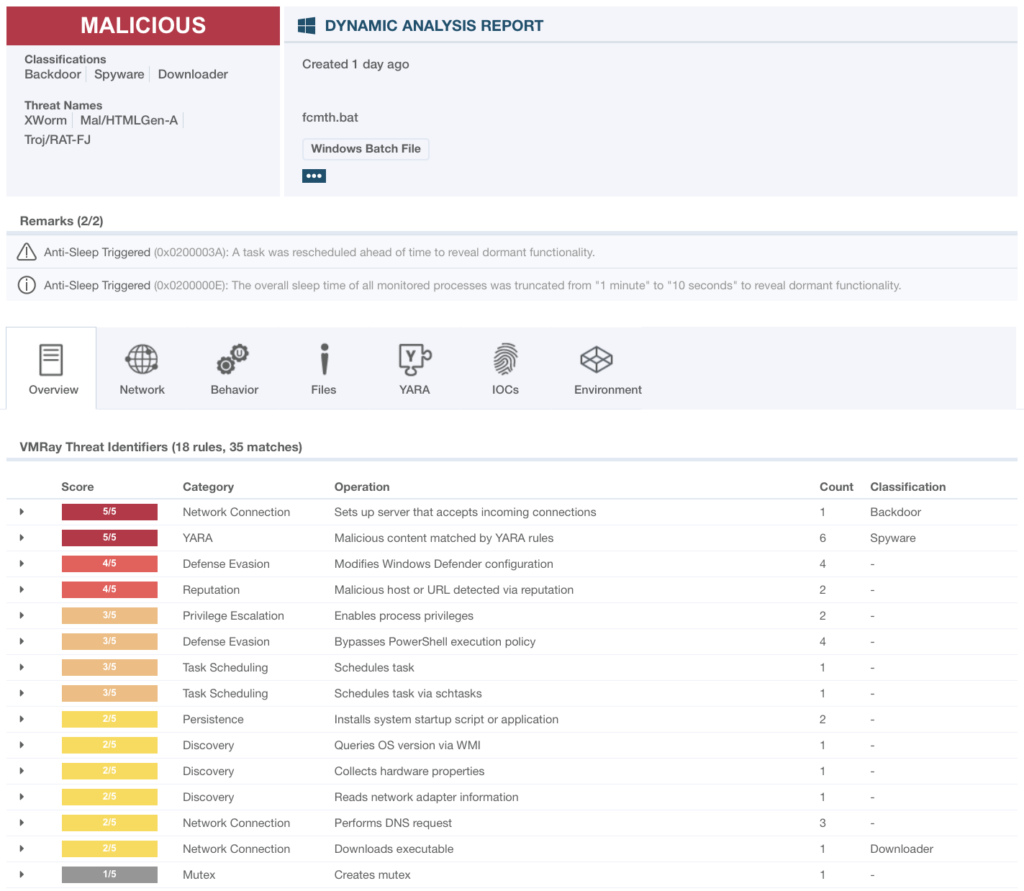
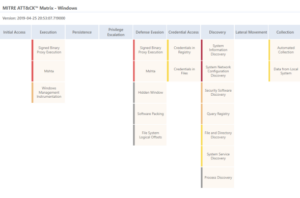
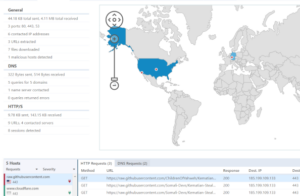
VMRay Labs found a multi-stage obfuscated batch script with low detections on VirusTotal which downloads and executes XWorm from GitHub.
The sample uses a UTF-16 Byte Order Marker and an open source Batch obfuscator to hinder manual analysis.
The sample had 7/61 detections on VirusTotal as of January 17th, 2025.
7 / 61 detections on VirusTotal
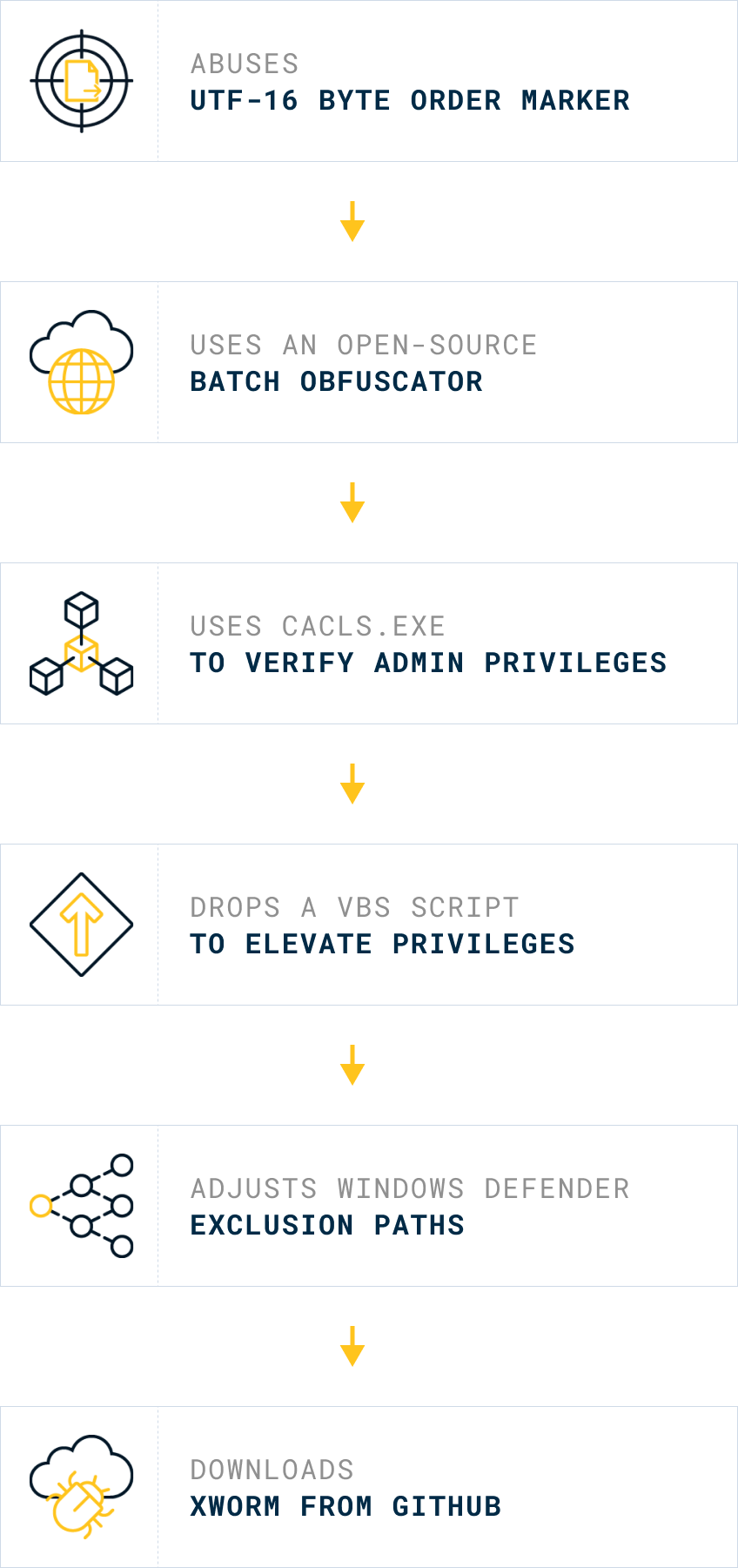
In a nutshell:
- Low detection rate on VirusTotal (7/61)
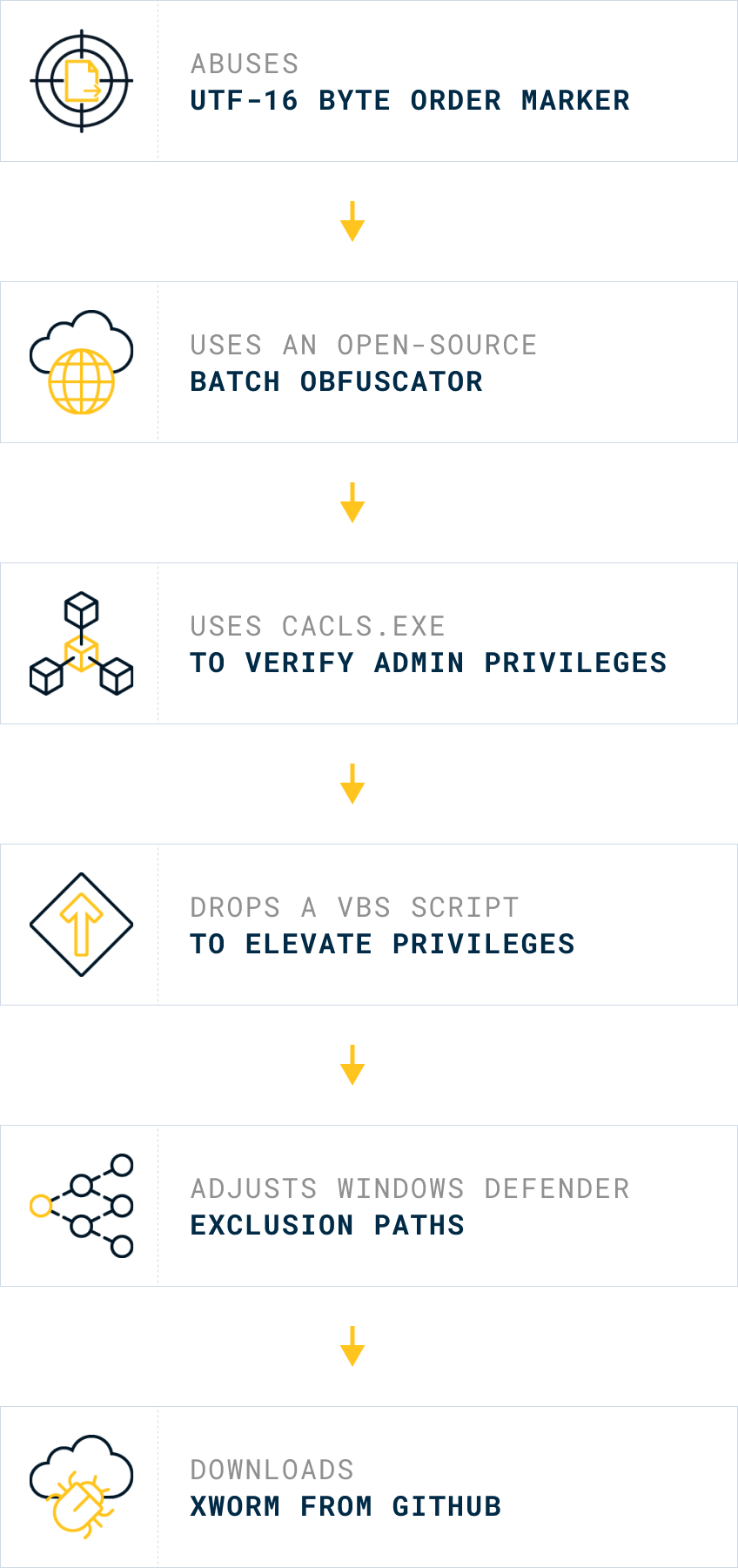
- Abuses UTF-16 Byte Order Marker to confuse text editors (0xFFFE)
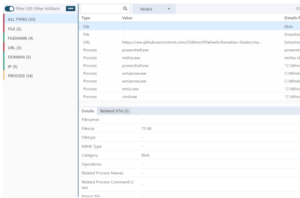
- Uses an open-source Batch obfuscator with multi-staged symbol mapping to build strings during execution
- Uses cacls.exe to verify whether the process is running with admin privileges
- Drops a VBS script to prompt a UAC dialog to elevate privileges
- Adjusts Windows Defender exclusion paths via PowerShell
- Downloads an instance of XWorm from a GitHub repository into a hidden file and executes it
- Batch → VBS → Batch → GitHub → XWorm
Dive deeper into the report
Sample SHA256:
96cc09ef13054fe37778f15fa87202e727832895f9712f68a18618fcb5c24ef1
Explore how you can use these insights



文章来源: https://www.vmray.com/heavily-obfuscated-batch-file-loads-xworm-hosted-on-github/
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh