
2024-12-23 17:0:20 Author: www.bleepingcomputer.com(查看原文) 阅读量:2 收藏

Two WordPress plugins required by the premium WordPress WPLMS theme, which has over 28,000 sales, are vulnerable to more than a dozen critical severity vulnerabilities.
The bugs could enable a remote, unauthenticated attacker to upload arbitrary files to the server, execute code, escalate privileges to administrator level, and perform SQL injections.
The WPLMS theme is a learning management system (LMS) for WordPress, used primarily by educational institutions, corporations providing training, and e-learning providers. It also offers integration with WooCommerce for selling courses.
Vulnerabilities in WPLMS theme
Patchstack vulnerability researchers found a total of 18 security issues in the WPLMS and VibeBP plugins and present in a recent report 10 of the most significant ones.
Here’s a summary of the flaws impacting the WPLMS theme:
- CVE-2024-56046 (CVSS 10.0): Allows attackers to upload malicious files without authentication, potentially leading to remote code execution (RCE).
- CVE-2024-56050 (CVSS 9.9): Authenticated users with subscriber privileges can upload files, bypassing restrictions.
- CVE-2024-56052 (CVSS 9.9): Similar to Subscriber+ but exploitable by users with student roles.
- CVE-2024-56043 (CVSS 9.8): Attackers can register as any role, including Administrator, without authentication.
- CVE-2024-56048 (CVSS 8.8): Low-privilege users can escalate to higher roles, such as Administrator, by exploiting weak role validation.
- CVE-2024-56042 (CVSS 9.3): Attackers can inject malicious SQL queries to extract sensitive data or compromise the database.
- CVE-2024-56047 (CVSS 8.5): Low-privilege users can execute SQL queries, potentially compromising data integrity or confidentiality.
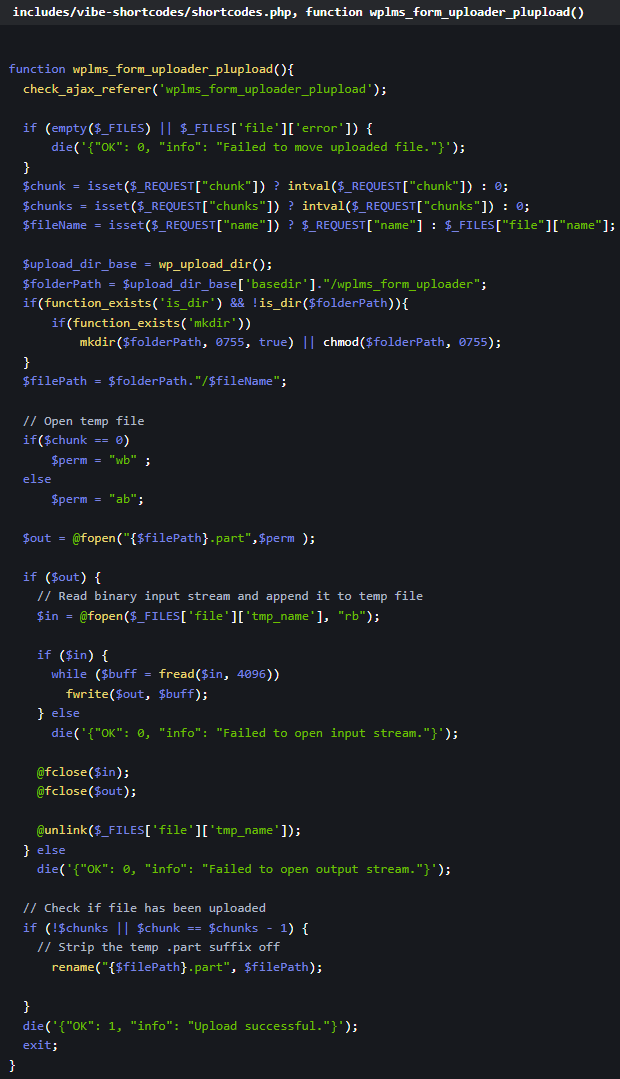
Source: Patchstack
And for VibeBP:
- CVE-2024-56040 (CVSS 9.8): Attackers can register as privileged users without authentication.
- CVE-2024-56039 (CVSS 9.3): SQL queries can be injected by unauthenticated users, exploiting poorly sanitized inputs.
- CVE-2024-56041 (CVSS 8.5): Authenticated users with minimal privileges can perform SQL injection to compromise or extract database information.
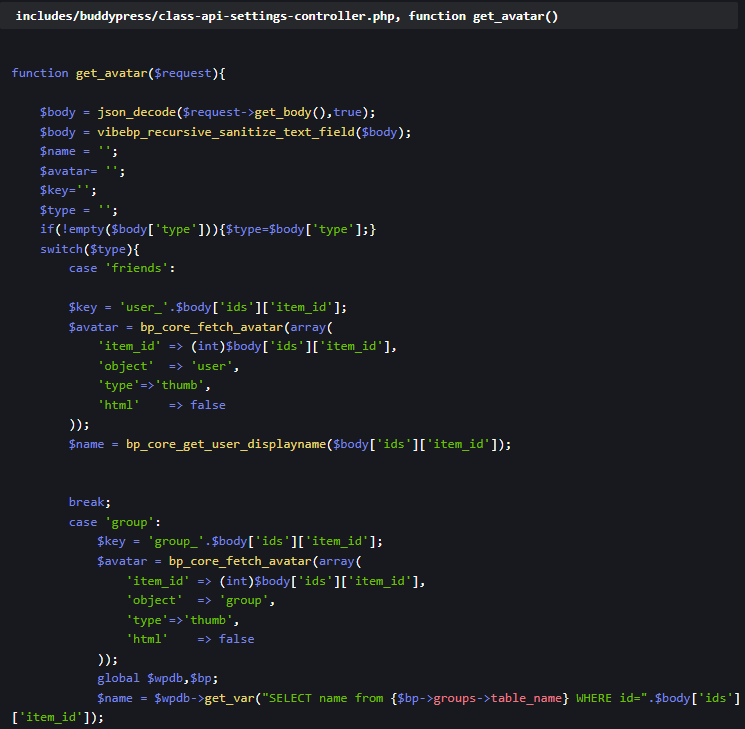
Source: Patchstack
Users of WPLMS should upgrade to version 1.9.9.5.3 and newer, while VibeBP should be upgraded to 1.9.9.7.7 or later.
As a general security advice, Patchstack suggests that websites enforce secure file uploads, SQL query sanitation, and role-based access controls.
Patchstack found the vulnerabilities and on March 31 notified Vibe Themese, the developer of WPLMS, of the issues. Between April and November, the developer tested multiple patches until they were able to fix all the vulnerabilities.
Vibe Themes collaborated with Patchstack to make sure that the delivered fix addresses all the bugs.
如有侵权请联系:admin#unsafe.sh