
2024-12-23 12:30:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:5 收藏
A new Microsoft 365 phishing-as-a-service platform called "FlowerStorm" is growing in popularity, filling the void left behind by the sudden shutdown of the Rockstar2FA cybercrime service.
First documented by Trustwave in late November 2024, Rockstar2FA operated as a PhaaS platform facilitating large-scale adversary-in-the-middle (AiTM) attacks targeting Microsoft 365 credentials.
The service offered advanced evasion mechanisms, a user-friendly panel, and numerous phishing options, selling cybercriminals access for $200/two weeks.
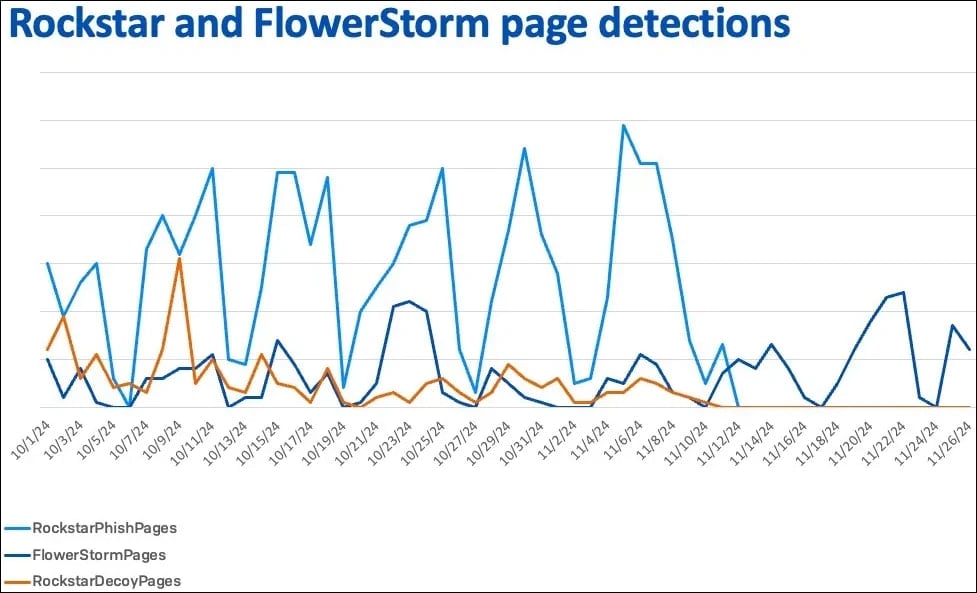
According to Sophos researchers Sean Gallagher and Mark Parsons, Rockstar2FA suffered from a partial infrastructure collapse on November 11, 2024, making many of the service's pages unreachable.
Sophos says this does not appear to be the result of law enforcement action against the cybercrime platform but rather a technical failure.
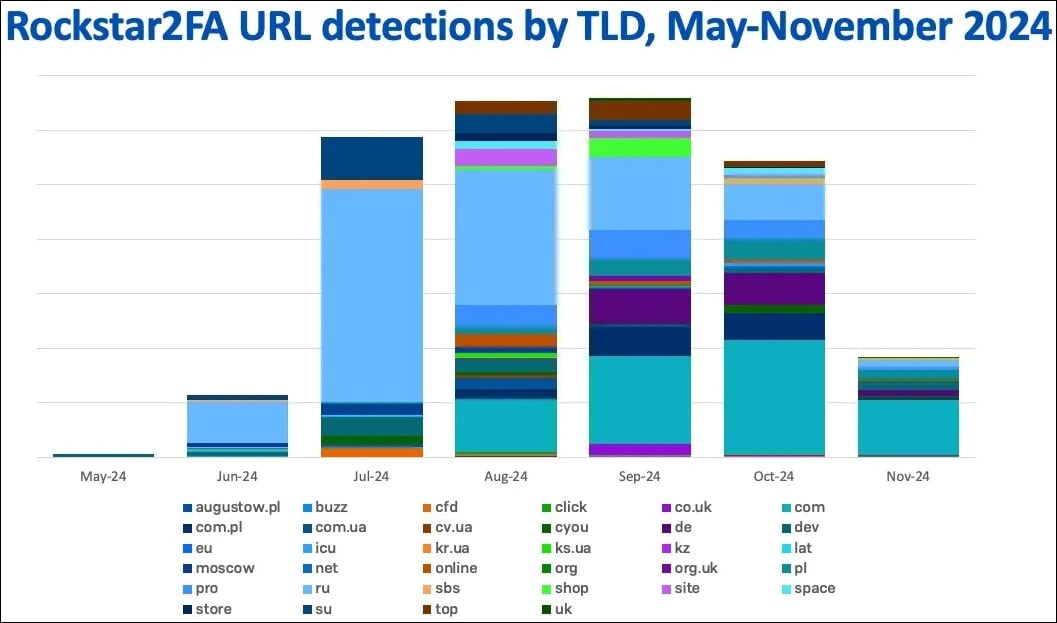
A few weeks later, FlowerStorm, which first appeared online in June 2024, started quickly gaining traction.
Source: Sophos
A possible rebrand of Rockstar2FA?
Sophos has found that the new service, FlowerStorm PhaaS, shares many features previously seen in Rockstar2FA, so it is possible that operators rebranded under a new name to reduce exposure.
Sophos identified several similarities between Rockstar2FA and FlowerStorm, suggesting a shared ancestry or operational overlap:
- Both platforms use phishing portals mimicking legitimate login pages (e.g., Microsoft) to harvest credentials and MFA tokens, relying on backend servers hosted on domains like .ru and .com. Rockstar2FA used randomized PHP scripts, while FlowerStorm standardized with next.php.
- The HTML structure of their phishing pages is highly similar, featuring random text in comments, Cloudflare "turnstile" security features, and prompts like "Initializing browser security protocols." Rockstar2FA used automotive themes, while FlowerStorm shifted to botanical themes, but the underlying design remains consistent.
- Credential harvesting methods align closely, using fields like email, pass, and session tracking tokens. Both platforms support email validation and MFA authentication through their backend systems.
- Domain registration and hosting patterns overlap significantly, with heavy use of .ru and .com domains and Cloudflare services. Their activity patterns showed synchronized rises and falls through late 2024, indicating potential coordination.
- The two platforms made operational mistakes that exposed backend systems and demonstrated high scalability. Rockstar2FA managed over 2,000 domains, while FlowerStorm rapidly expanded after Rockstar2FA's collapse, suggesting a shared framework.
Source: Sophos
"We cannot with high confidence link Rockstar2FA and FlowerStorm, other than to note that the kits reflect a common ancestry at a minimum due to the similar contents of the kits deployed," concludes Sophos.
"The similar patterns of domain registration could be a reflection of FlowerStorm and Rockstar working in coordination, though it is also possible that these matching patterns were driven by market forces more than the platforms themselves."
A new danger rises
Whatever the story is behind FlowerStorm's sudden rise, for users and organizations, it's yet another enabler of damaging phishing attacks that could lead to full-blown cyberattacks.
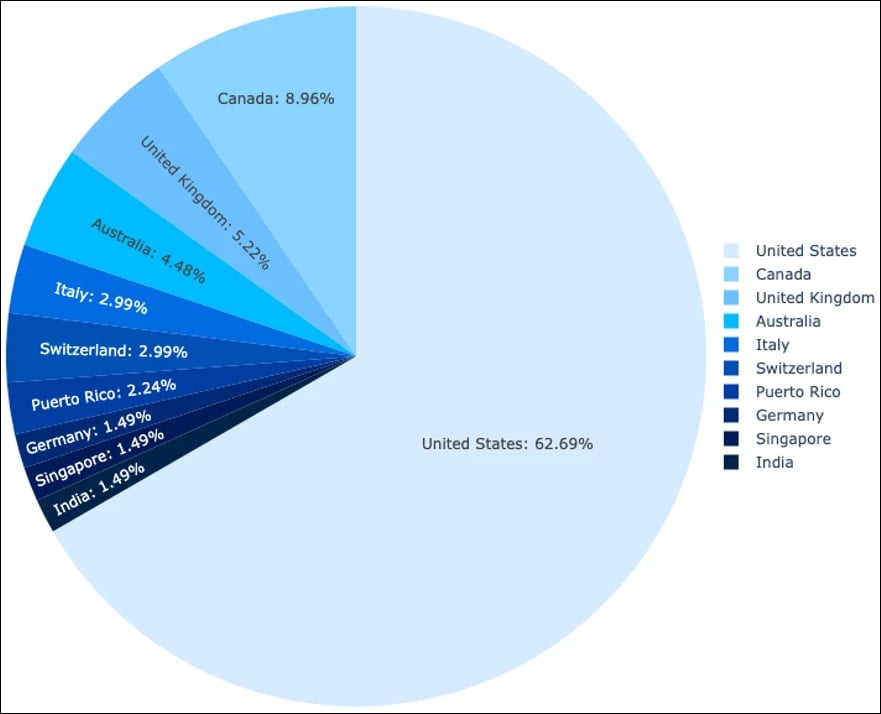
Sophos' telemetry shows that roughly 63% of the organizations and 84% of users targeted by FlowerStorm are based in the United States.
Source: Sophos
The most targeted sectors are services (33%), manufacturing (21%), retail (12%), and financial services (8%).
To protect against phishing attacks, use multi-factor authentication (MFA) with AiTM-resistant FIDO2 tokens, deploy email filtering solutions, and use DNS filtering to block access to suspicious domains like .ru, .moscow, and .dev.
如有侵权请联系:admin#unsafe.sh