Addressing cyber threats before they have a chance to strike or inflict serious damage is by far the best security approach any company can embrace. Achieving this takes a lot of research and proactive threat hunting. The problem here is that it is easy to get stuck in endless arrays of data and end up with no relevant intel.
To avoid this, use these five battle-tested techniques that are certain to improve your company's threat awareness and overall security.
Finding threats targeting orgs in your region
The most basic, yet high-impact way to learn about the current threat landscape for your company is to go and see what type of attacks other organizations in your region are experiencing.
In most cases, threat actors attempt to target dozens of businesses at the same time as part of a single campaign. This makes it possible to catch the threat early and make correct adjustments in your organization.
How it contributes to your security:
- More targeted and effective defense strategy.
- Accurate threat prioritization.
- Resource optimization.
How it works:
While there are several ways to find out about the current threat landscape in your country, ANY.RUN provides one of the most comprehensive and user-friendly solutions for this.
It runs a massive public database of analysis reports on the latest malware and phishing samples, which are uploaded to ANY.RUN's sandbox by over 500,000 security professionals worldwide.
Extensive data from each sandbox session is extracted and can be searched through by users via ANY.RUN's Threat Intelligence (TI) Lookup. The service offers over 40 different parameters, from IP addresses and file hashes to registry keys and mutexes, helping you pinpoint threats using the smallest indicators with accuracy.
Say we want to see what type of phishing threats are targeting organizations in Germany, while excluding URLs from the search (using the NOT operator), as we wish to focus on malicious files specifically. To do this, we can type the following query into TI Lookup:
threatName:"phishing" AND submissionCountry:"de" NOT taskType:"url"
 |
| You can explore each sandbox session shown by TI Lookup |
In seconds, we get a list of public sandbox sessions which include phishing documents, emails, and other types of content submitted to ANY.RUN by users in Germany.
You can observe each session closely completely for free to gain additional insights into the threats and collect invaluable intelligence.
 |
| One of the sandbox sessions from the TI Lookup results, showing analysis of a phishing email |
As shown in the image above, we can view the entire attack in action along with all network and system activities recorded during the analysis.
Get a 14-day FREE trial of TI Lookup to see how it can improve your organization's security.
Checking suspicious system and network artifacts with TI tools
On an average day, security departments at mid-size organizations get hundreds of alerts. Not all of them are properly followed through, which leaves a gap for attackers to exploit. Yet, simply adding one more layer of verifying all the suspicious artifacts with TI tools can potentially save organizations from considerable financial and reputational losses.
How it contributes to your security:
- Early detection of malicious activities.
- Understanding of the tactics and techniques used by attackers.
- Quick incident response to minimize impact.
How it works:
A common scenario for security departments is dealing with unusual IP connections. Since there are many instances of legitimate addresses generating alerts, it's easy for some employees to get complacent and let actual malicious ones slip off the hook.
To eliminate such situations, employees can check all IP addresses in TI Lookup. Here is an example of possible query:
destinationIP:"78[.]110[.]166[.]82"
 |
| TI Lookup provides additional info for every indicator, including domains, ports, and events |
The service instantly notifies us about the malicious nature of this IP and supplies more context: the name of the threat (Agent Tesla) and sandbox sessions where this IP was recorded.
Similarly, security professionals can check system events like the use of suspicious scripts. We can include more than one indicator at the same time, to see if any of them is linked to malicious activities.
Consider this query:
commandLine:"C:\\Users\\Public\\*.ps1" OR commandLine:"C:\\Users\\Public\\*.vbs"
It is set up to look for two types of scripts: .ps1 and .vbs format scripts that are placed in the Public directory.
Since we do not know the file names of these scripts, we can simply replace them with the * wildcard.
 |
| Scripts matching the query |
TI Lookup provides us with a list of matching scripts, found across numerous sandbox sessions.
 |
| List of sandbox sessions featuring the requested scripts |
Now, we can collect their names, see how they work as part of an attack, and take preventive measures based on the discovered intel.
Exploring threats by specific TTPs
While blocking known indicators of compromise (IOCs) is an important element of your security, they tend to change regularly. That is why a more sustainable approach is to rely on tactics, techniques, and procedures (TTPs) used by attackers to infect organizations in your industry.
With TI tools, you can track threats that use TTPs of your interest, observe their behavior, and gather invaluable information on them to enhance your company's detection capabilities.
How it contributes to your security:
- Detailed insights into attacker methods.
- Development of specific countermeasures.
- Proactive defense against emerging threats.
How it works:
TI Lookup provides an actionable MITRE ATT&CK matrix, which includes dozens of TTPs, which are accompanied by sandbox sessions featuring malware and phishing threats using these techniques in action.
 |
| TI Lookup offers an actionable MITRE ATT&CK matrix |
It is free and available even to unregistered users. You can explore how attacks are carried out and find specific threats that employ particular TTPs.
 |
| TI Lookup provides samples of threats for each TTP |
The image above shows how the service provides information on T1562.001, a technique used by attackers to modify security tools and avoid detection.
In the center, TI Lookup lists signatures related to this technique which describe specific malicious activities. On the right, you can explore reports on relevant threats.
Tracking evolving threats
Threats tend to change their infrastructure and evolve, as organizations adjust to their attacks. That is why it is vital to never lose track of the threats that once posed a risk to your company. This can be done by getting up-to-date information on the latest instances of this threat and its new indicators.
How it contributes to your security:
- Timely actions to mitigate emerging threats.
- Enhanced situational awareness for security teams.
- Better preparation for future attacks.
How it works:
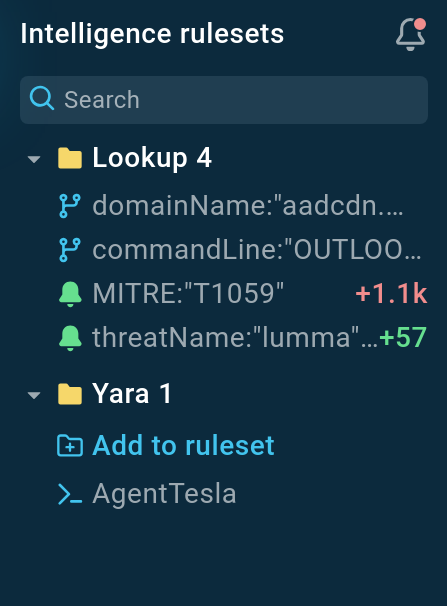
TI Lookup allows you to subscribe to receive notifications about updates on specific threats, indicators of compromise, indicators of behavior, as well as combinations of different data points.
 |
| To receive notifications, simply enter your query and click the subscribe button |
This lets you stay aware of new variants and evolving threats, adapting your defenses as needed almost in real time.
For instance, we can subscribe to a query to receive information on new domain names and other network activities related to the Lumma Stealer:
threatName:"lumma" AND domainName:""
 |
| TI Lookup notifies you about new results for each subscription |
Soon, we'll see how new updates start appearing.
 |
| TI Lookup showing new results |
By clicking on the subscribed query, the new results will be displayed. In our case, we can observe new ports used in attacks involving Lumma.
Enriching information from third-party reports
Reports on the current threat landscape are an essential source of intelligence on attacks that may target your organizations. Yet, the information they contain may be quite limited. You can build on the existing knowledge and do your own research to uncover additional details.
How it contributes to your security:
- Ensuring a more complete picture of the threat landscape.
- Threat data validation.
- More informed decision-making.
How it works:
Consider this recent attack targeting manufacturing companies with Lumma and Amadey malware. We can follow up on the findings outlined in the report to find more samples related to the campaign.
To do this, we can combine two details: the name of the threat and a .dll file used by attackers:
filePath:"dbghelp.dll" AND threatName:"lumma"
 |
| Sandbox sessions matching the query |
TI Lookup provides dozens of matching sandbox sessions, allowing you to significantly enrich the data provided in the original report and use it to inform your defenses against this attack.
Improve and Speed up Threat Hunting in Your Organization with TI Lookup
ANY.RUN's Threat Intelligence Lookup provides centralized access to the latest threat data from public malware and phishing samples.
It helps organizations with:
- Proactive Threat Identification: Search the database to proactively identify and update your defense based on the discovered intelligence.
- Faster Research: Accelerate threat research by quickly connecting isolated IOCs to specific threats or known malware campaigns.
- Real-Time Monitoring: Monitor evolving threats by receiving updates on new results related to your indicators of interest.
- Incident Forensics: Enhance forensic analysis of security incidents by searching for contextual information on existing artifacts.
- IOC Collection: Discover additional indicators by searching the database for relevant threat information.
Get a 14-day free trial of TI Lookup to test all of its capabilities and see how it can contribute to your organization's security.
Found this article interesting? This article is a contributed piece from one of our valued partners. Follow us on Twitter and LinkedIn to read more exclusive content we post.