The ransomware attack that hit supply chain management platform Blue Yonder and its customers l 2024-12-7 02:45:48 Author: cyble.com(查看原文) 阅读量:14 收藏
The ransomware attack that hit supply chain management platform Blue Yonder and its customers last month was the work of a new ransomware group called “Termite.”
Cyble Research and Intelligence Labs (CRIL) researchers have examined a Termite ransomware binary and determined that Termite is essentially a rebranding of the notorious Babuk ransomware. The Termite leak site claims seven victims so far (geographic distribution below).

We’ll cover the technical details of the new Termite ransomware strain, which was first identified by PCrisk, along with MITRE ATT&CK techniques, indicators of compromise (IoCs) and recommendations.
Technical Details of Termite Ransomware
Upon execution, the ransomware invokes the SetProcessShutdownParameters(0, 0) API to ensure that its process is one of the last to be terminated during system shutdown. This tactic is used to maximize the time available for the ransomware to complete its encryption process.
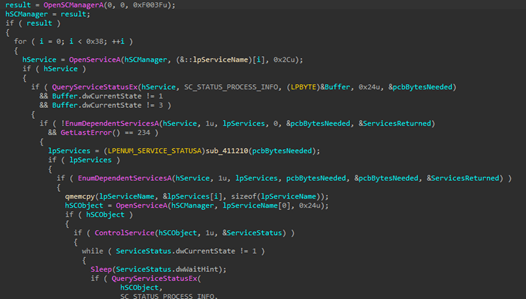
The ransomware then attempts to terminate services on the victim’s machine to prevent interruptions during the encryption process. It uses the OpenSCManagerA() API to establish a connection with the Service Control Manager, granting access to the service control manager database (image below).

After gaining access, the ransomware enumerates the services on the victim’s machine to retrieve their names. It specifically looks for services such as veeam, vmms, memtas and others, and terminating them if they are found to be actively running.
The ransomware enumerates running processes using the CreateToolhelp32Snapshot(), Process32FirstW(), and Process32NextW() APIs. It checks process names such as sql.exe, oracle.exe, firefox.exe and others and terminates them if they are actively running.

After that, the ransomware launches the vssadmin.exe process to delete all Shadow Copies, as shown in the below figure. This action is performed to prevent system recovery after the files have been encrypted.

The ransomware also uses the SHEmptyRecycleBinA() API to delete all items from the Recycle Bin, ensuring that no deleted files can be restored after encryption. After execution, Termite Ransomware attempts to retrieve system information using the GetSystemInfo() API, which collects details like the number of processors, as shown in the below figure.

The ransomware then creates a separate thread for each detected CPU, generates ransom notes named “How To Restore Your Files.txt”, and encrypts files on the victim’s machine.
It avoids encrypting certain system folders such as AppData, Boot, Windows, Windows.old etc. Additionally, it specifically excludes system files such as autorun.inf, boot.ini, bootfont.bin etc., as well as file extensions like .exe, .dll, and .termite from the encryption process to ensure that essential system functions remain intact.
Similar to Babuk ransomware, Termite appends the signature “choung dong looks like hot dog” at the end of the encrypted file.

The figure below shows the ransom note dropped by the ransomware, titled ” How To Restore Your Files.txt,” which instructs victims to visit the onion site for additional information.

After dropping the ransom notes, the malware encrypts the files on the victim’s machine and appends the “.termite” extension, as shown in the figure below.

The Termite ransomware can also spread through network shares and paths of the infected machine, as shown below.

If the command-line argument is “shares,” the ransomware uses the NetShareEnum() API to locate network shares and retrieve information about each shared resource on the server. It then checks for the $ADMIN share and begins encrypting the files. If the command-line argument is “paths,” the ransomware calls the GetDriveTypeW() API to identify network drives connected to the infected machine, and once located, it starts encrypting the files. If neither “-paths” nor “-shares” are provided, and the mutex named “DoYouWantToHaveSexWithCuongDong” is not found on the infected machine, the ransomware recursively traverses all local drives and encrypts the files.
Conclusion
Termite ransomware represents a new and growing threat in the cyber landscape, leveraging advanced tactics such as double extortion to maximize its impact on victims. By targeting businesses and demanding substantial ransoms, it not only disrupts operations but also exposes organizations to significant financial, legal, and reputational risks. The emergence of Termite underscores the critical need for robust cybersecurity measures, proactive threat intelligence, and incident response strategies to counter the evolving tactics of ransomware groups.
Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices below:
Safety Measures to Prevent Ransomware Attacks
- Do not open untrusted links and email attachments without first verifying their authenticity.
- Conduct regular backup practices and keep those backups offline or in a separate network.
- Turn on the automatic software update feature on your computer, mobile, and other connected devices wherever possible and pragmatic.
- Use a reputable antivirus and Internet security software package on your connected devices, including PC, laptop, and mobile.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Execution | T1204.002 (User Execution) | User executes the ransomware file |
| Defense Evasion | T1070.004 (Indicator Removal: File Deletion) | Ransomware deletes itself after execution |
| Discovery | T1083 (File and Directory Discovery) | Ransomware enumerates folders for file encryption and file deletion. |
| Discovery | T1135 (Network Share Discovery) | Targets Network Shares and Paths |
| Impact | T1486 (Data Encrypted for Impact) | Ransomware encrypts the data for extortion. |
| Impact | T1490 (Inhibit System Recovery) | Disable automatic Windows recovery |
IOC
| Indicators | Indicator Type | Description |
| f0ec54b9dc2e64c214e92b521933cee172283ff5c942cf84fae4ec5b03abab55 | SHA-256 | Termite Ransomware |
Related
如有侵权请联系:admin#unsafe.sh