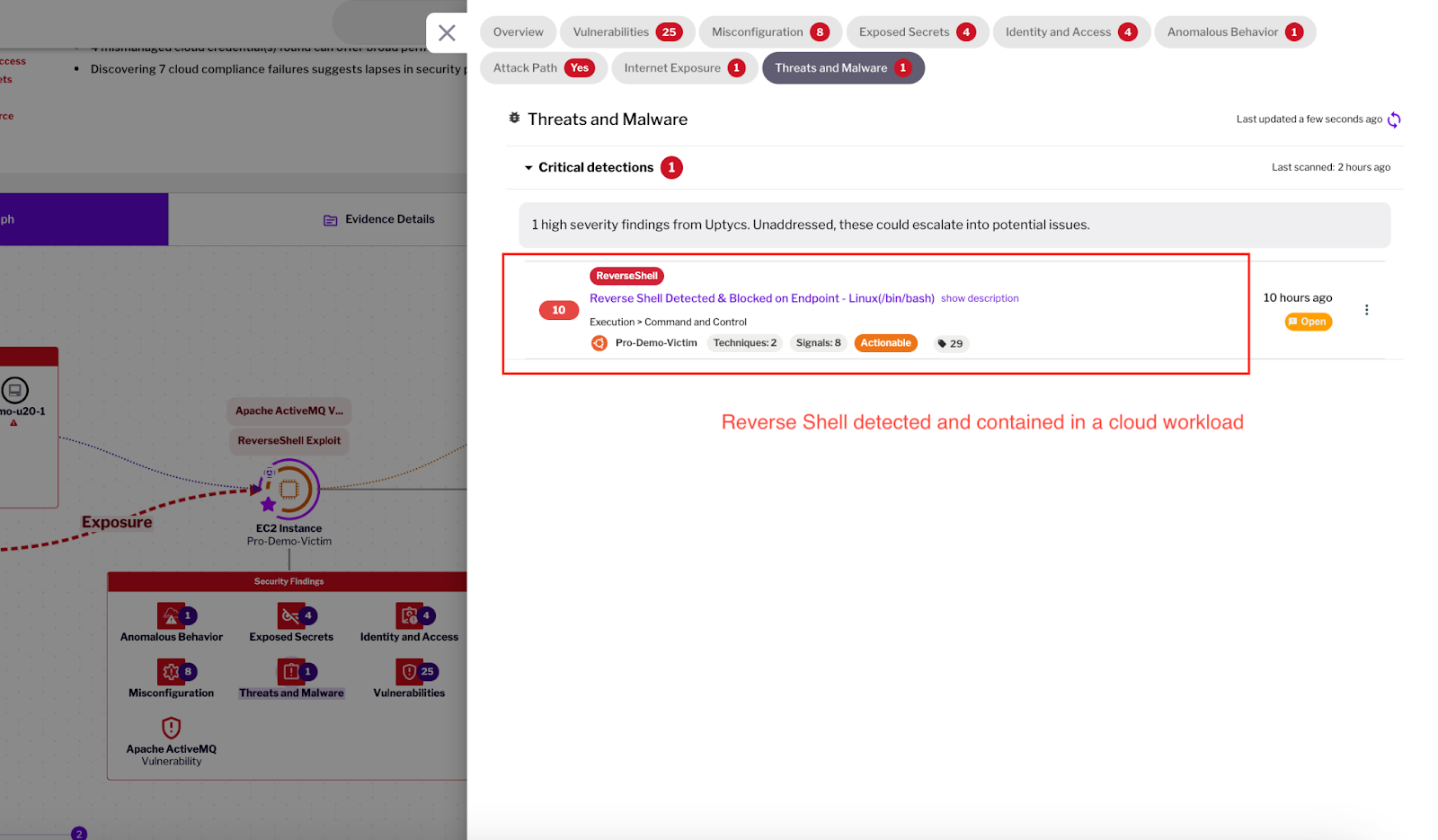
For effective enforcement at runtime, security systems can incorporate generic behaviors based on the premise that attacks tends to exhibit certain common behaviors: By writing protection policies that focus on these generic behaviors, security systems can identify malware (any type) or exploit activity without needing to know the exact exploit in advance (zero day attacks). Figure (1) provides an example of eBPF based detection and policy based containment of a typical cloud workload. Figure (1) - Attack contained through policy enforcement We’ll detail how Uptycs’ Blast Radius Mitigation Framework provides robust, immediate protection during such active threat incidents in your cloud workloads. Malware and exploit activity pose continuous risks to cloud workloads. Uptycs’ eBPF sensor efficiently detects and contains threats against these key attack types. Cryptocurrency mining attacks, where attackers hijack a cloud system’s resources to mine cryptocurrencies, are on the rise. These attacks are often stealthy, using minimal resources until the system is significantly impacted. Uptycs can detect mining activity, such as Coinminer processes that consume abnormal CPU and memory usage patterns. By continuously monitoring cloud workload resource usage, Uptycs identifies when processes attempt to mine cryptocurrency, enabling security teams to act and protect cloud resources from being siphoned for malicious purposes. Network scanning techniques such as IP Scan and Port Scan are commonly used by attackers to discover vulnerable systems, identify open ports, or facilitate lateral movement within a network. These scanning activities are often precursors to larger attacks, such as exploits or ransomware. By detecting behaviors early, Uptycs helps prevent attackers from discovering and exploiting vulnerable cloud systems. Ransomware attacks are highly damaging, as they encrypt valuable files and demand payment for decryption. Uptycs detects ransomware activity by identifying processes that attempt to encrypt files on a system. File encryption is often rapid and widespread, making it a key indicator of ransomware. By monitoring file system changes and process behaviors, Uptycs can detect and block ransomware attacks before they cause irreversible damage to cloud data. Information stealer attacks, such as Keyloggers and Credential Stealers, are designed to capture sensitive information from compromised systems. By detecting information stealers, Uptycs helps prevent data theft and breaches. A Web Shell is a script that attackers use to control a compromised web server, often with a remote connection. Reverse Shells allow attackers to remotely execute commands on a compromised system. Uptycs detects both these activities by monitoring for suspicious web traffic and unexpected outbound connections that could indicate the presence of a web shell or reverse shell. Figure (2) - Detection attribution to a specific command line and container Fileless malware is a type of malware that runs directly in memory, making it harder to detect through traditional file-based antivirus solutions. Uptycs is designed to detect Fileless Malware by monitoring system processes and behaviors rather than relying on file signatures. By analyzing runtime behavior, Uptycs can identify anomalies that suggest the presence of fileless malware, helping to prevent attacks that would otherwise bypass conventional security defenses. Malicious Toolkits like malware and exploit kits, including those detected by Yara rules, are often used by attackers to launch a variety of malicious activities. Uptycs integrates signature-based detection (e.g., Yara rules) with behavioral analysis to identify malicious toolkits and prevent their execution within cloud workloads. Having an effective unified enforcement strategy to contain attacks is beneficial for the following reasons. Figure (3) shows an example of how a unified enforcement strategy can help Security Operations drive better efficiency. Figure 3 - eBPF based protection policy profiles After containing threats, the Uptycs Blast Radius Mitigation Framework moves into Root Cause Analysis for deep insights—keep reading to see how each step drives resilient, secure cloud environments. The Uptycs Blast Radius Mitigation Framework is a five-step journey to cloud security resilience. Read the guide to learn more.
1. Malware and exploits
2. Cryptocurrency Mining
3. Network Scanning
4. Ransomware
5. Information Stealers
6. Web Shells and Reverse Shells
7. Fileless Malware
8. Malicious Toolkits
The Comprehensive Benefit
All these attack types often share similar Indicators of Compromise (IoCs), such as unusual network traffic, unauthorized access attempts, or abnormal system processes. Grouping these attacks together allows security tools to more effectively recognize patterns across multiple vectors.
By combining these attack types, we can improve the efficacy of detection systems that look for signatures or anomalous activity indicative of exploitation.
Treating these activities under a single policy driven enforcement model enables security teams to respond faster. Rather than spending time distinguishing between different types of attacks, teams can focus on identifying exploit activity, triaging it, and mitigating the threat before it escalates.
For example, patch management, which is a common defense against exploit-based attacks, can be prioritized across all types of vulnerabilities—whether they affect a web server or an operating system.
Blast Radius Mitigation Framework: Uptycs' Policy Enforcement
For effective enforcement at runtim 2024-12-6 08:35:40 Author: www.uptycs.com(查看原文) 阅读量:5 收藏
For effective enforcement at runtim 2024-12-6 08:35:40 Author: www.uptycs.com(查看原文) 阅读量:5 收藏
文章来源: https://www.uptycs.com/blog/blast-radius-mitigation-framework-policy-enforcement
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh
