Today’s adversaries relentlessly probe for weaknesses in organizations’ digital defenses, seeking 2024-12-6 04:2:7 Author: flashpoint.io(查看原文) 阅读量:13 收藏
Today’s adversaries relentlessly probe for weaknesses in organizations’ digital defenses, seeking to leverage vulnerability exploits to install ransomware, information-stealing malware, and to perform other cyber attacks. With over 32,928 vulnerabilities disclosed in 2024 alone, organizational attack surfaces are rapidly expanding, making prioritization more critical than ever.
There are simply too many vulnerabilities for organizations to triage all at once. However, not every issue requires immediate attention. And although security professionals know this, they often do not have the vulnerability intelligence (VI) they need to make informed decisions. While organizations have traditionally relied on VI sources like the Common Vulnerability Exposures (CVE) and National Vulnerability Database (NVD), time has shown that they have fallen short in providing the necessary actionable insights and context. Organizations need enriched vulnerability intelligence beyond CVE and NVD to take action that drives change.
Flashpoint Vulnerability Intelligence: Going Beyond CVE and NVD
The sheer volume of vulnerabilities facing organizations today is staggering. Over 380,000 vulnerabilities have been disclosed since the CVE program began—a 3,129% increase. Making matters worse is that there are over 104,000 vulnerabilities that are missed by CVE and NVD, affecting a wide variety of major vendors, as well as widely-used third-party libraries.
Consequently, security operations that rely solely on public data sources may have less than 70% visibility into the actual vulnerability landscape. This limitation, coupled with the dynamic nature of threat actor tactics, makes the prioritization of vulnerabilities for remediation the crux of an efficient exposure and vulnerability management operation. However, the real challenge lies in identifying which of them are actively being targeted by threat actors.
Enriching Vulnerability Intelligence with Real-Time Threat Insights
Flashpoint’s researchers relentlessly hunt for vulnerabilities across the internet, from public disclosures to the darkest corners of the web. Our intelligence teams monitor billions of discussions taking place amongst illicit marketplaces, forums, and communities where malicious actors converse or solicit vulnerability exploits—aggregating them into an easy to use platform via weekly vulnerability reports.
| CVE ID | Vendor | CVSSv3 | Exploit Details |
|---|---|---|---|
| CVE-2024-3094 | XZ Utils | 9.8 | Remote / Network Access |
| CVE-2024-21762 | Fortinet | 9.8 | Remote / Network Access |
| CVE-2024-6387 | OpenSSH | 8.1 | Remote / Network Access |
| CVE-2024-38062 | Microsoft | 9.8 | Remote / Network Access |
| CVE-2024-23113 | Fortinet | 9.8 | Remote / Network Access |
This multi-faceted approach, which includes proactively monitoring thousands of websites and developer resources, ensures that Flashpoint delivers the most comprehensive, timely, and actionable vulnerability intelligence available, enriched with real-time threat insights.
This allows us to deliver the largest, deepest, and broadest collection of publicly disclosed vulnerabilities, and the most detailed. The unique details of vulnerability metadata provides security teams with a multi-dimensional view of each issue, providing insights into:
- Severity: Our experts refine CVSSv2 and v3 scores by correcting any inaccuracies in CVE/NVD assessments, providing detailed explanations and analysis to ensure the most accurate vulnerability assessment possible.
- Exploitability: Flashpoint vulnerability intelligence identifies vulnerabilities with known exploit code or proof-of-concept exploits, while also clarifying if threat actors can leverage them remotely. Users can also access the exploit’s exact post (if known) saving valuable time and resources.
- Threat Likelihood: Leveraging best-in-class threat intelligence, vulnerability intelligence cn provide additional layers of insight and analysis of issues that are being actively discussed by threat actor groups and communities, as well as the probability of an exploit being used in ransomware operations.
How Flashpoint Can Enable Better Prioritization
Teams that rely heavily on vulnerability intelligence benefit greatly from intelligence that streamlines the workflows of vulnerability management teams, Security Operation Center (SOC) teams, Cyber Threat Intelligence (CTI) teams, threat hunters, and others.
A metadata-rich vulnerability database enables organizations to efficiently source, prioritize, and remediate relevant threats, including those not found in public sources. Organizations can search for the exact vulnerabilities that affect their systems, software, and bundled third-party libraries—and then prioritize them according to their own VM frameworks.
For example, security teams that emphasize exploitability can filter their entire workload and backlog, showing only remote code executions, issues with known public exploits, or vulnerabilities that are being exploited-in-the-wild. Or, if organizations value severity, they can simplify vulnerability reports to show only issues with CVSSv2 or v3 scores above 9.0.
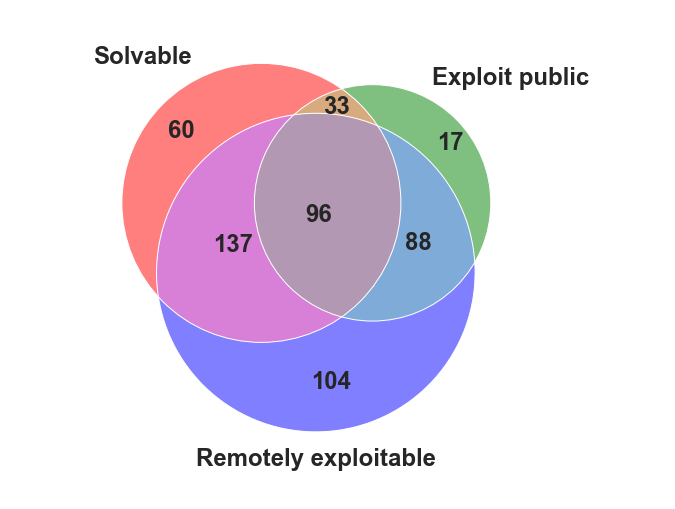
Flashpoint recommends that security professionals focus on high severity vulnerabilities with public exploits that have a known solution. Taking this approach, organizations ensure that they save time and resources, by focusing on dangerous vulnerabilities that they can actually fix or mitigate. Leveraging this, critical vulnerability workloads can be reduced by nearly 83%.
Compared to the CISA KEV, Flashpoint’s KEV catalog provides a far more extensive view of actively exploited vulnerabilities, with over 216% greater coverage. While the original is limited by CVE/NVD’s shortcomings, our catalog spans Flashpoint’s entire vulnerability collection.
This includes our coverage of non-CVEs, as well as our monitoring of threat intelligence sources—such as dark web and botnet monitoring, malware analysis, and more. In addition, our intelligence teams provide weekly vulnerability reports, highlighting specific CVEs that warrant attention due to their potential impact or wide-spread discussion amongst threat actors. Security teams can efficiently focus their remediation efforts and reduce their attack surface with metadata-rich intelligence.
Elevate Vulnerability Management with Flashpoint
Organizations need an intelligence-led approach that combines best-in-class vulnerability and threat intelligence. Leveraging the highest quality data and insights to drive action, security professionals can achieve a robust security operation that provides value across vulnerability management programs, purple team exercises, incident response and more to safeguard critical assets against adversary exploitation. Request a demo today to see how Flashpoint can transform your vulnerability management program.
如有侵权请联系:admin#unsafe.sh