Finding information on specific cyber threats in a vast amount of data can be challenging. Threat Intelligence Lookup from ANY.RUN simplifies this task with wildcards and operators that provide you with the ability to create flexible and precise search queries.
Let’s take a look at how you can use them to identify and collect intel on malware and phishing attacks more effectively.
About Threat Intelligence Lookup
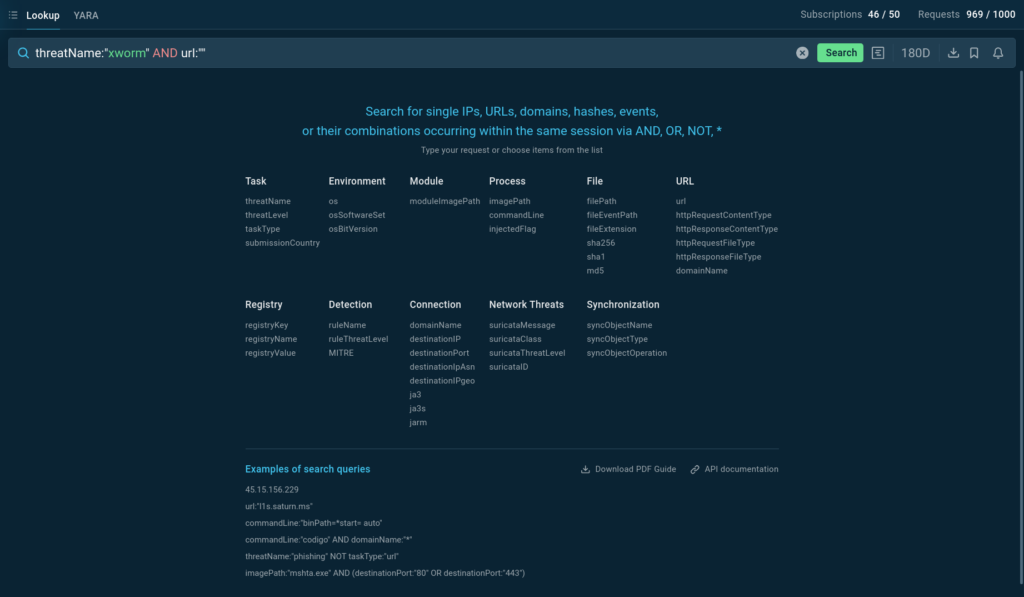
Threat Intelligence (TI) Lookup is a fast and efficient tool designed to simplify cyber threat investigations. It allows for flexible searches for Indicators of Compromise (IOCs), Indicators of Attack (IOAs), and Indicators of Behavior (IOBs).
TI Lookup provides access to a constantly updated database of threat data collected from millions of public malware and phishing samples analyzed in ANY.RUN’s Interactive Sandbox.
Each sandbox session contains detailed logs of system and network events that occur while a threat is executing. By searching through this comprehensive data, you can easily find connections between seemingly unrelated pieces of information and tie them to a specific threat.
Here’s how TI Lookup can help you and your organization:
- Investigate Threats Quickly: Gather extensive and in-depth information on emerging and persistent cyber threats with over 40 search parameters (e.g. threat names, command lines, registry logs, etc.).
- Receive Real-Time Updates: Stay informed with real-time updates on results for your search queries.
- Enrich Threat Intelligence: Get relevant context, indicators, and samples manually analyzed by threat analysts.
Search Operators in TI Lookup
Search operators are essential tools in TI Lookup that allow you to combine several indicators to refine your search queries effectively. They act as logical connectors that help you specify the relationships between different conditions in your search and achieve greater flexibility and precision in your searches.
TI Lookup supports logical operators like AND, OR, and NOT, as well as grouping with parentheses. Let’s take a closer look at each of these.
AND
What it does
The AND operator helps you combine multiple conditions.
Why use it
AND is great for narrowing down your search to find threats by including as many unique indicators as possible.
It is equally effective in situations when you have several completely disparate artifacts, like an IP address and a mutex, and want to link them to a particular threat.
Example
This query is designed to search for sandbox sessions where both thum[.]io and logo[.]clearbit[.]com domains were found.
- Thum[.]io is a real-time website screenshot generator.
- logo[.]clearbit[.]com is a service for fetching company logos.
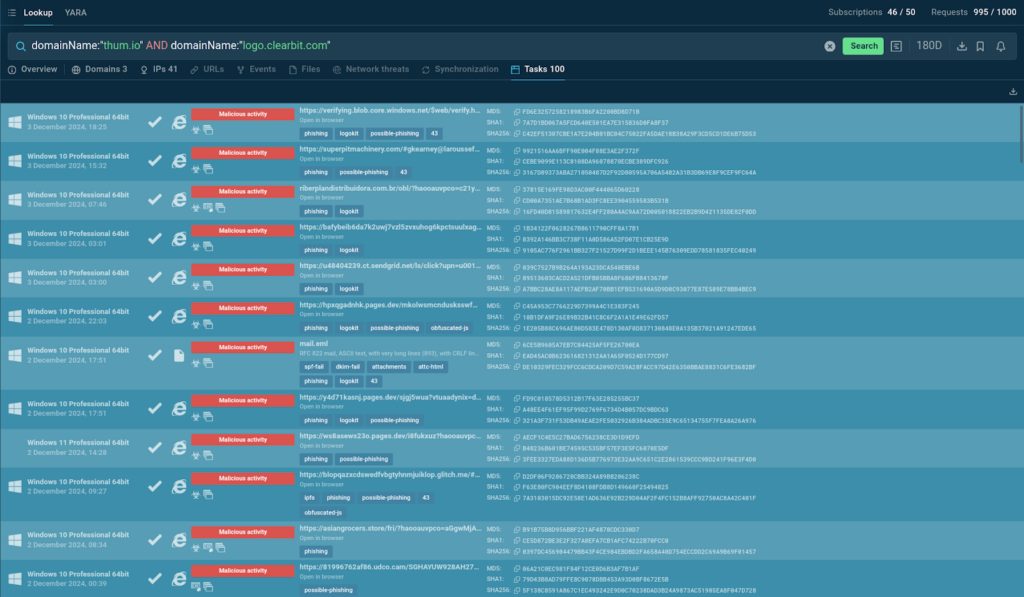
TI Lookup almost instantly provides results: associated IP addresses and sandbox sessions, all of which contain a “malicious activity” label and a “phishing” tag.
We can click any session of our interest to investigate the threat further.
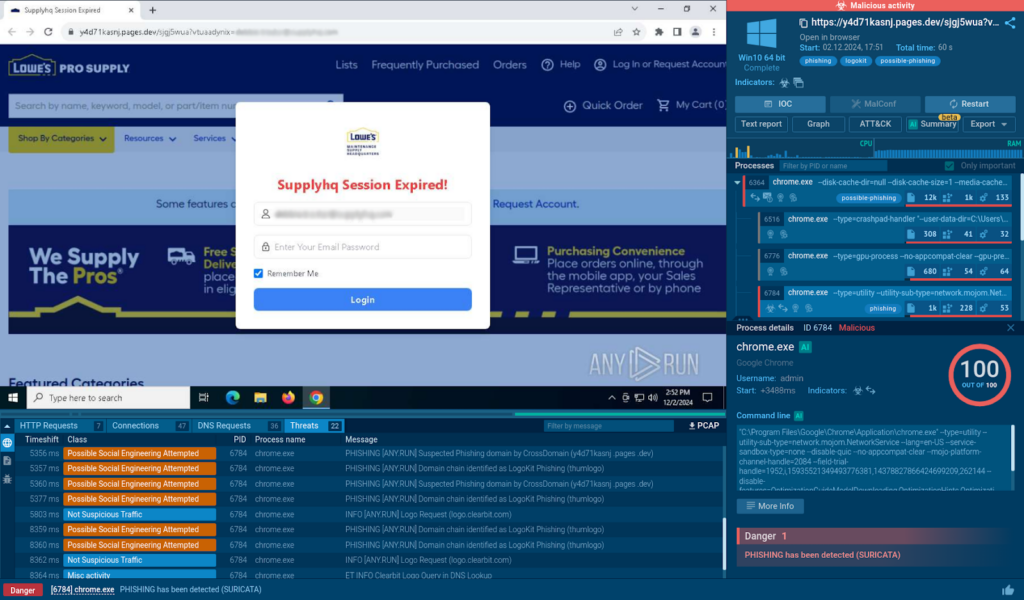
By reviewing the analysis report, we can spot that this is a cyber attack which uses thum[.]io to dynamically generate phishing pages with the backgrounds of a website that coincides with that of the victim. Attackers also use logo[.]clearbit[.]com to add corresponding company logos to make fake pages appear more legitimate.
OR
What it does
The OR operator helps return matches where at least one of the given conditions is found.
Why use it
OR is excellent in situations when you are not sure which one of two indicators is related to a threat. It is also useful for broadening your search to include results where both indicators are found, but necessarily together in the same session.
Example
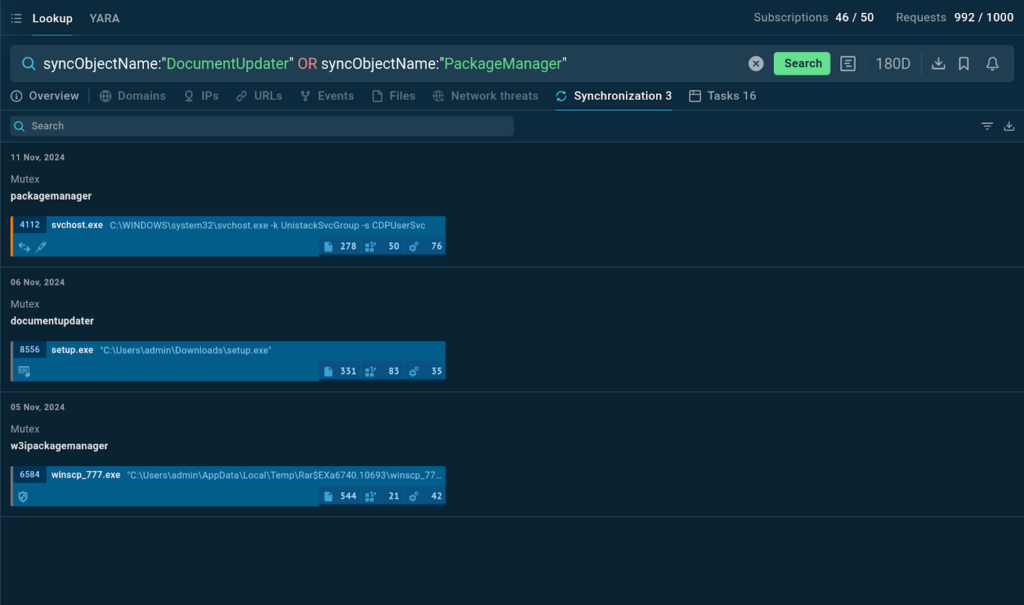
It searches for entries where the synchronization object name is “DocumentUpdater” or “PackageManager”. If you’re investigating a threat that could be using either of these sync objects, this query ensures you don’t miss any relevant information.
TI Lookup shows that the synchronization objects are mutexes and provides sandbox sessions where they were previously discovered.
NOT
What it does
The NOT operator excludes results that match the specified condition.
Why use it
NOT is helpful when you want to refine your search and see sandbox sessions where no certain item, like a domain or file name, was observed.
Example
This query is looking for phishing samples but excludes any entries where the initial submission uploaded to the ANY.RUN sandbox was a URL.

It helps us find email, html, zip, exe, or other types of files, used in phishing attacks.
Parentheses ()
What they do
Parentheses group conditions and control the order of operations to ensure they are processed in the order you specify.
Why use them
Parentheses are essential for creating complex queries, making your search more precise and effective.
Example
This query searches for sandbox sessions and their related data where the process “mshta.exe” was observed along with connections to destination ports of either 80 or 443. The parentheses ensure that the OR condition is processed first, making the search more precise.
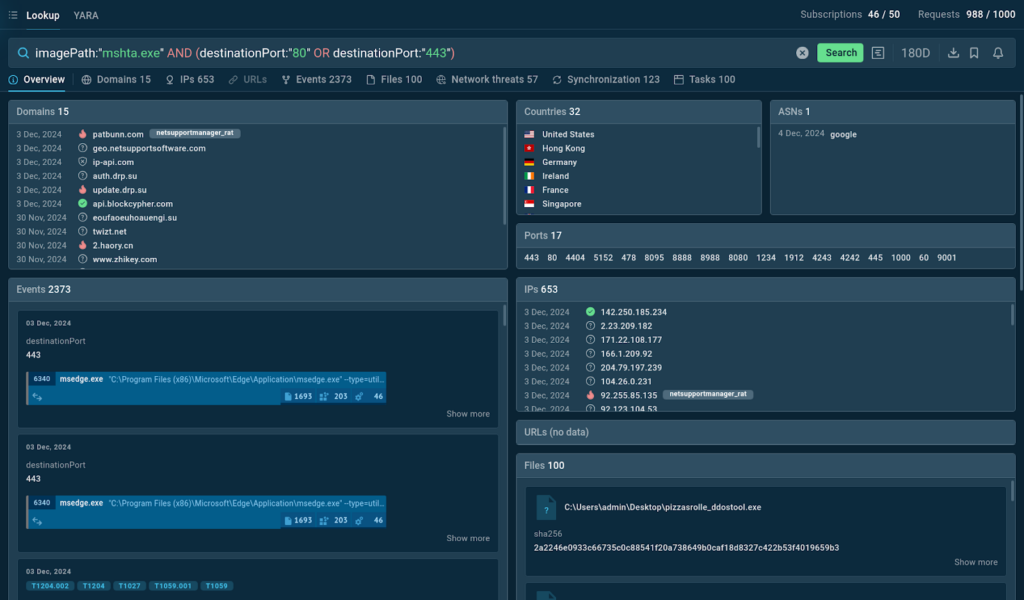
TI Lookup returns a wealth of threat data related to our query. Some of the results include malicious domains and IP addresses, as well as a list of network threats detected during analyses.
Wildcard Characters
Wildcards in TI Lookup act as placeholders in your search queries. They can represent different types of character sequences.
Asterisk (*)
What it does
The asterisk represents any number of characters, including none. This means it can stand in for zero, one, or multiple characters. The asterisk is added by default at the start and end of each query, so you in most cases there is no need to enter it manually.
Why use it
The asterisk is great for when you’re not sure about the exact content of a string. It helps you find matches even if there are unknown parts or certain variations in your query string.
Example
This query searches for sandbox sessions where the command line includes paths to specific script files located in the C:\Users\Public directory. The scripts must be of types .vbs (Visual Basic Script), .bat (Batch file), and .ps1 (PowerShell script).
Yet, the names of these scripts are replaced with the asterisk wildcard, representing any string of characters, as they can vary.
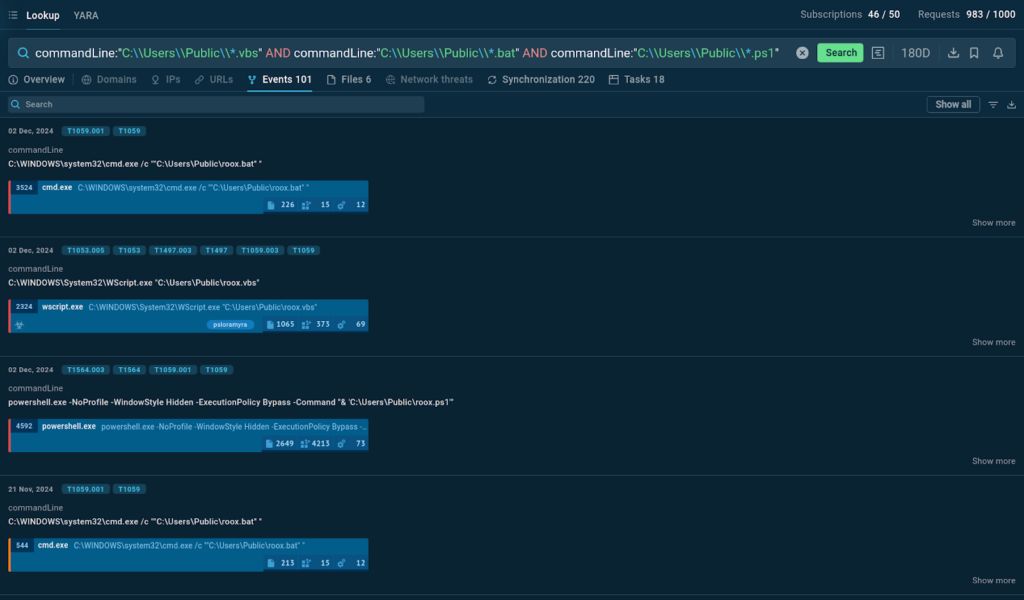
This helps us discover scripts with different file names and see how each of them fits into a wider context of the entire attack analyzed in the sandbox.
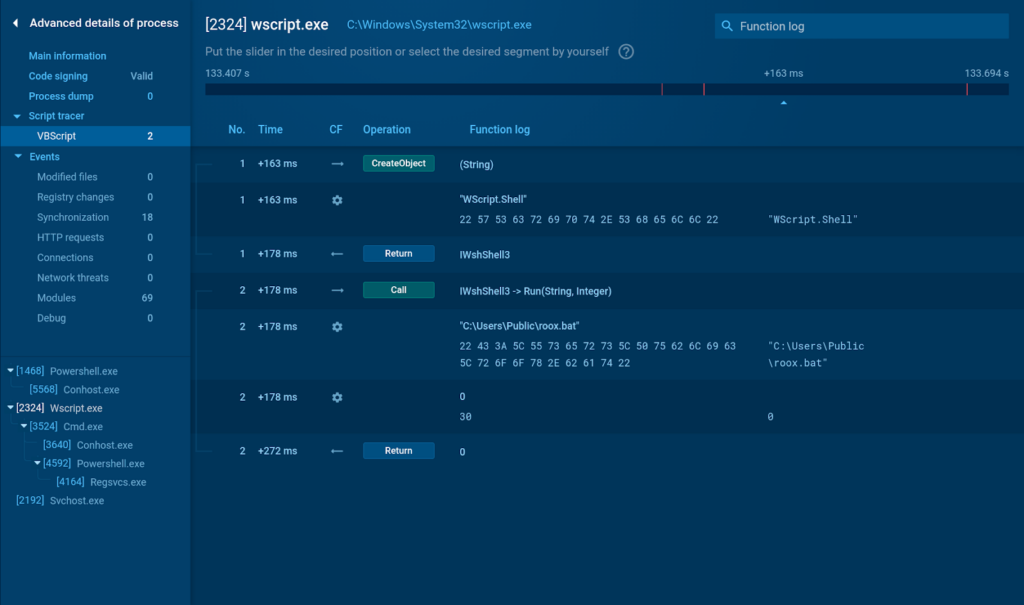
In the image above, you can see the execution of one of the found scripts inside the ANY.RUN sandbox.

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup
Read full guide
Question Mark (?)
What it does
The question mark represents any single character or its absence. This means it can stand in for exactly one character or none at all.
Why use it
The question mark is perfect for situations when you are not sure about a certain character in your string or know that it varies.
Example
Here, we can borrow a query from Jane_0sint’s article on phishing investigations, which is intended for identifying samples of Mamba2FA attacks.
A notable part of this query is that we can see the question mark being used twice. Yet, there is a difference between these two instances:
- The first one is the wildcard that serves as a stand-in for the characters “m”, “n”, and “o” that are commonly used in Mamba2FA URLs.
- The second question mark is a part of the address. To escape it, we use the \ slash symbol.
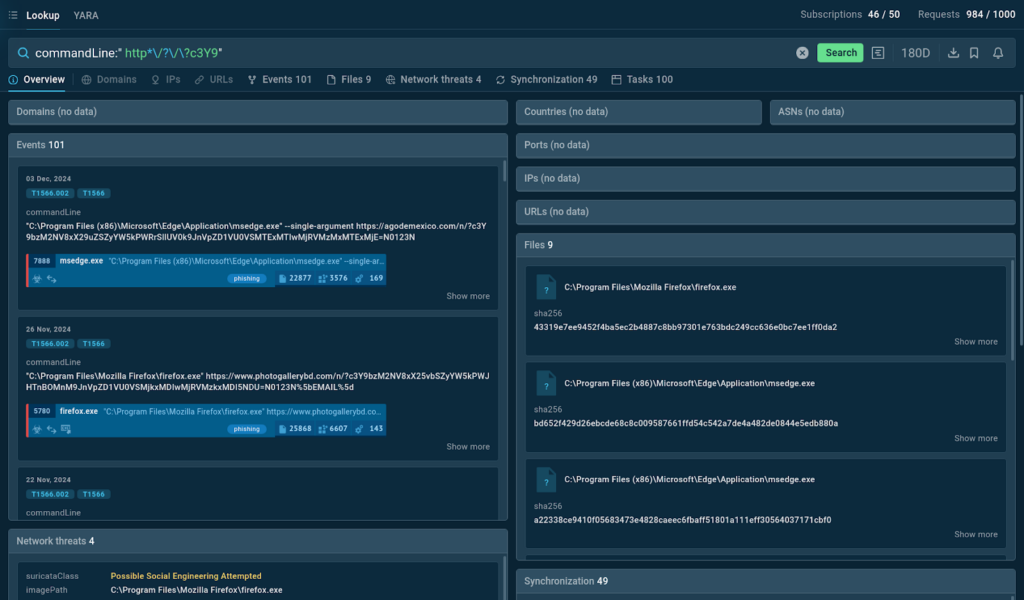
We once again can observe a variety of results, including command lines that contain different URLs matching our query.
Dollar Sign ($)
What it does
The dollar sign ensures that the search term must appear at the end of the string. It excludes matches with any characters after the specified content.
Why use it
The dollar sign is useful when you know the exact ending of a string but are unsure about the beginning. It helps you find matches that end with your specified term.
Example
This query searches for any synchronization object whose name ends with _STOP.
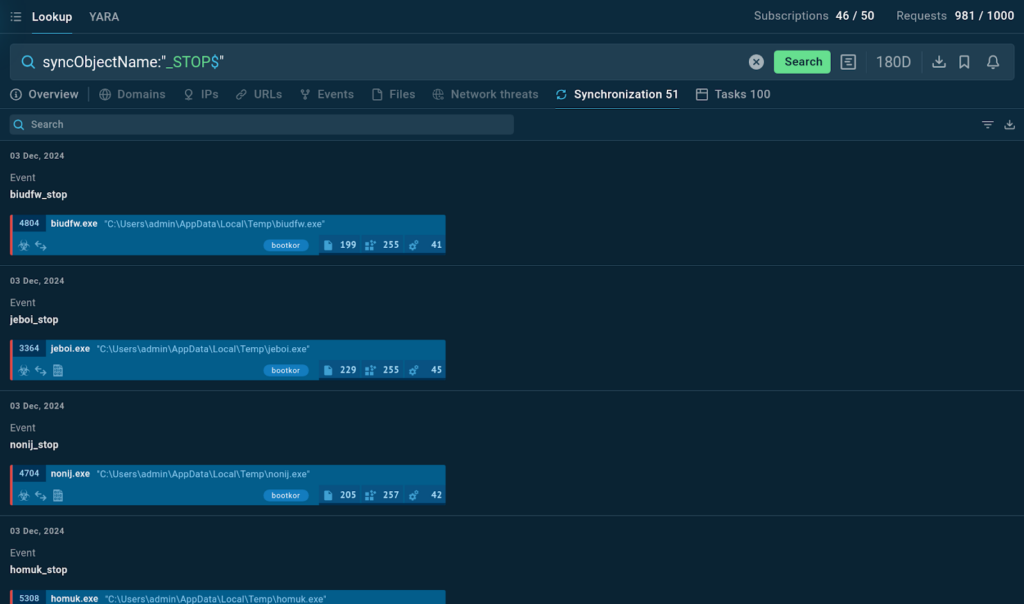
Among the results, we can see mutex names such as biudfw_stop, jeboi_stop, and nonij_stop. As always, we can explore each of them in detail by navigating to their corresponding sandbox sessions.
Caret (^)
What it does
The caret ensures that the search term must appear at the beginning of the string. It prevents matches with any characters before the specified query content.
Why use it
The caret is helpful when you know the exact starting point of a string but are unsure about the rest. It narrows down your search to items that begin with your specified term.
Example
This query finds domain names that start with 0ffice and end with .com, with any characters allowed in between. The caret (^) and dollar sign ($) ensure the exact start and end.
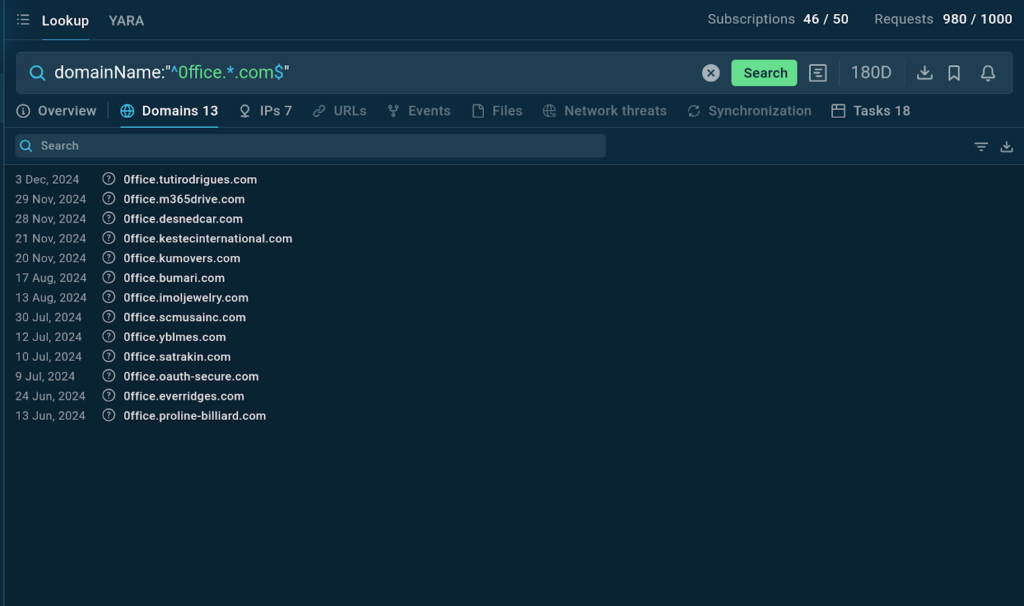
TI Lookup provides us with domains that match our query along with sandbox sessions, where they were found.
Conclusion
wildcards and operators in TI Lookup provide the flexibility and precision needed to perform threat intelligence searches. By learning how to use these tools, you can make your threat hunting efforts more effective.
Give it a try by requesting a free trial of TI Lookup.
About ANY.RUN
ANY.RUN’s Threat Intelligence Lookup and YARA Search services allow for precise threat hunting and the extraction of valuable insights into current cyber threat trends. What’s impressive is how fast these scans are—they significantly speed up the analysis process, allowing for quick detection of threats and malware.
See Black Friday deals for ANY.RUN’s Interactive Sandbox and Threat Intelligence Lookup →
