2024-11-26 00:15:18 Author: www.bleepingcomputer.com(查看原文) 阅读量:6 收藏

The Chinese state-sponsored hacking group Salt Typhoon has been observed utilizing a new "GhostSpider" backdoor in attacks against telecommunication service providers.
The backdoor was discovered by Trend Micro, which has been monitoring Salt Typhoon's attacks against critical infrastructure and government organizations worldwide.
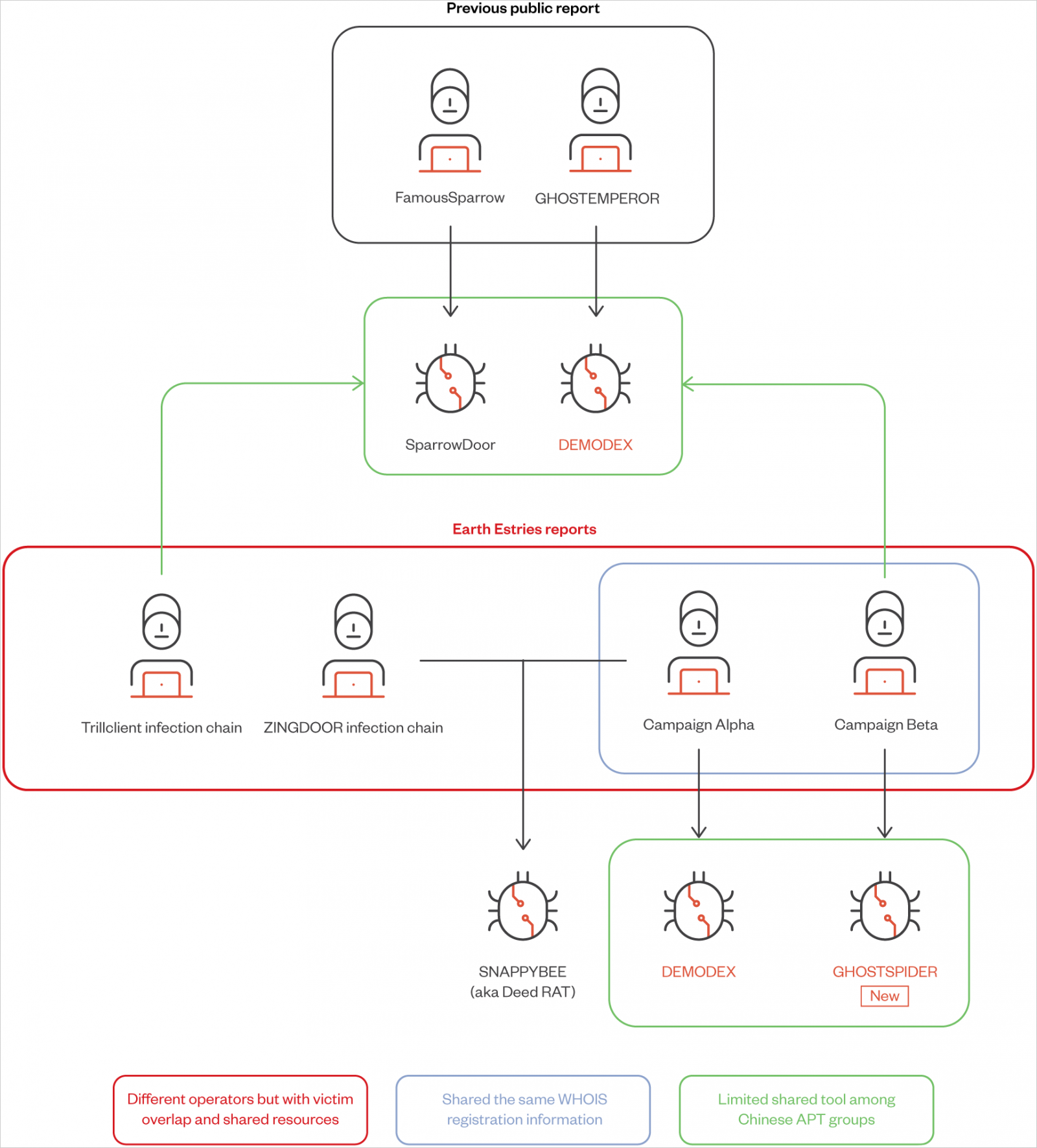
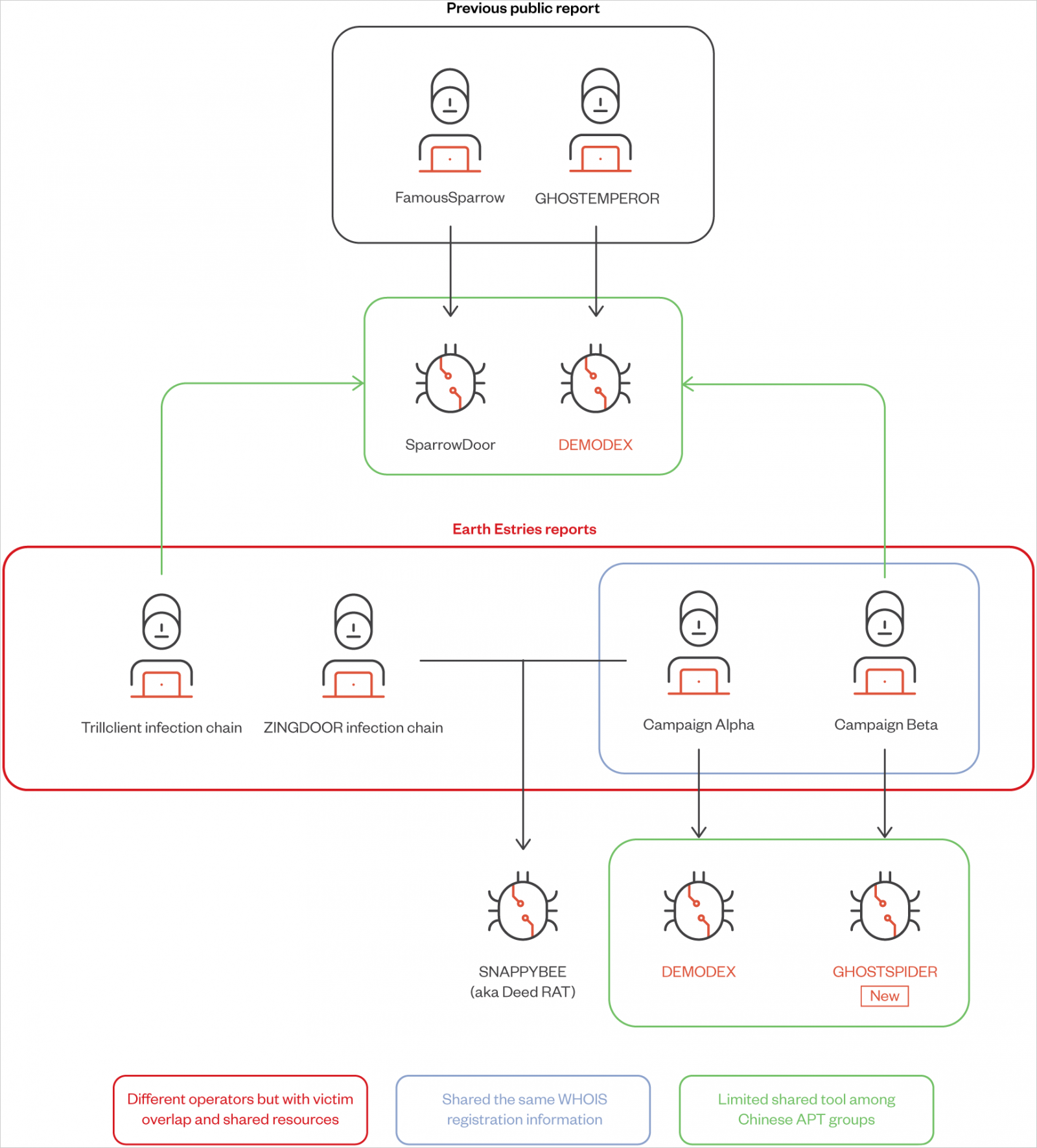
Along with GhostSpider, Trend Micro discovered that the threat group also uses a previously documented Linux backdoor named 'Masol RAT,' a rootkit named 'Demodex,' and a modular backdoor shared among Chinese APT groups named 'SnappyBee.'
Source: Trend Micro
Salt Typhoon's global campaigns
Salt Typhoon (aka 'Earth Estries', 'GhostEmperor', or 'UNC2286') is a sophisticated hacking group that has been active since at least 2019 and typically focuses on breaching government entities and telecommunications companies.
Recently, the U.S. authorities have confirmed that Salt Typhoon was behind several successful breaches of telecommunication service providers in the U.S., including Verizon, AT&T, Lumen Technologies, and T-Mobile.
It was later admitted that Salt Typhoon also managed to tap into the private communications of some U.S. government officials and stole information related to court-authorized wiretapping requests.
Earlier today, the Washington Post reported that the authorities in the U.S. notified 150 victims, mainly in the D.C. area, of the fact that Salt Typhoon had breached the privacy of their communications.
According to Trend Micro, Salt Typhoon has attacked telecommunications, government entities, technology, consulting, chemicals, and transportation sectors in the U.S., Asia-Pacific, Middle East, South Africa, and other regions.
The security researchers have affirmed at least twenty cases of Salt Typhoon successfully compromising critical organizations, including, in some instances, their vendors.
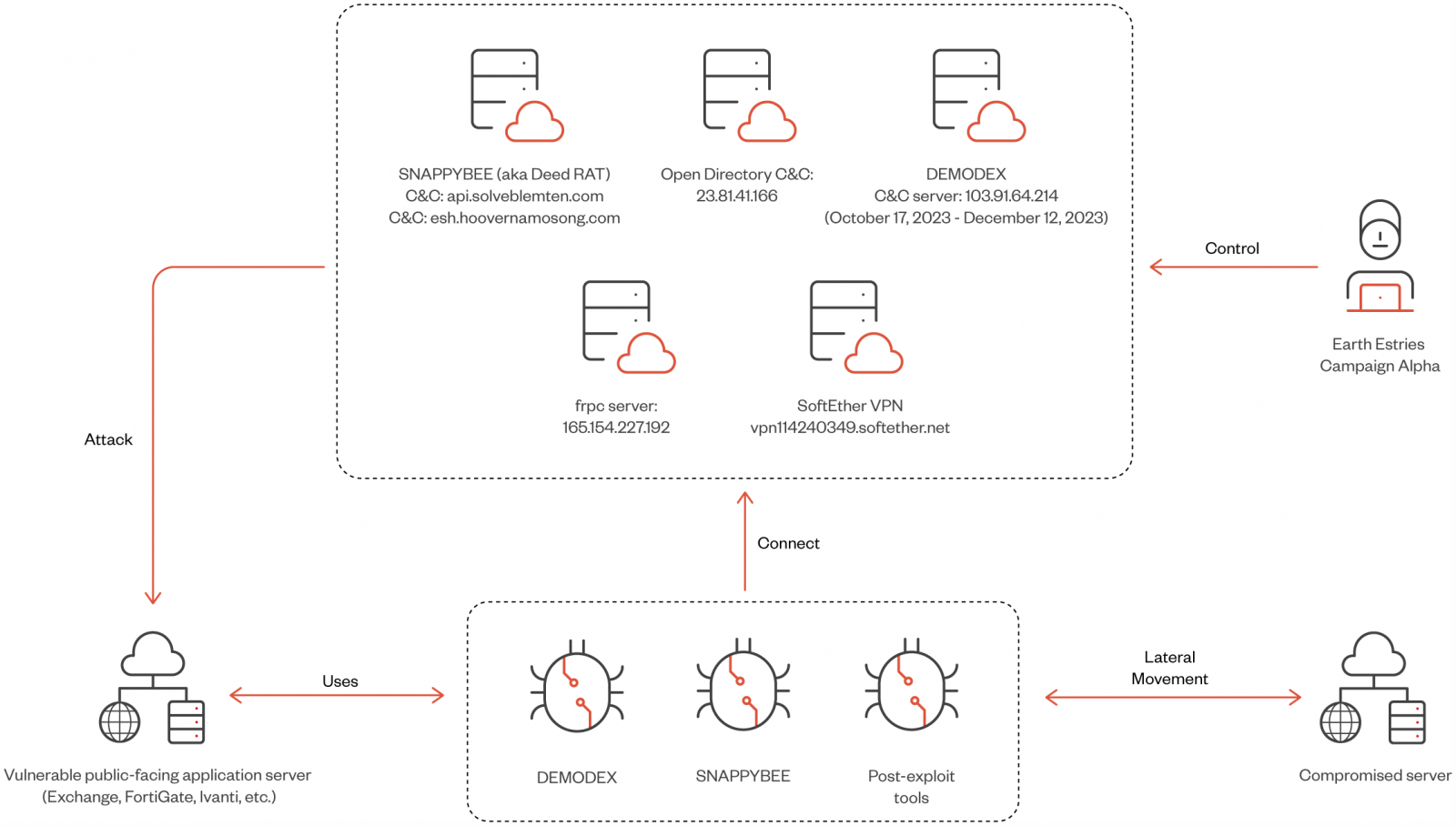
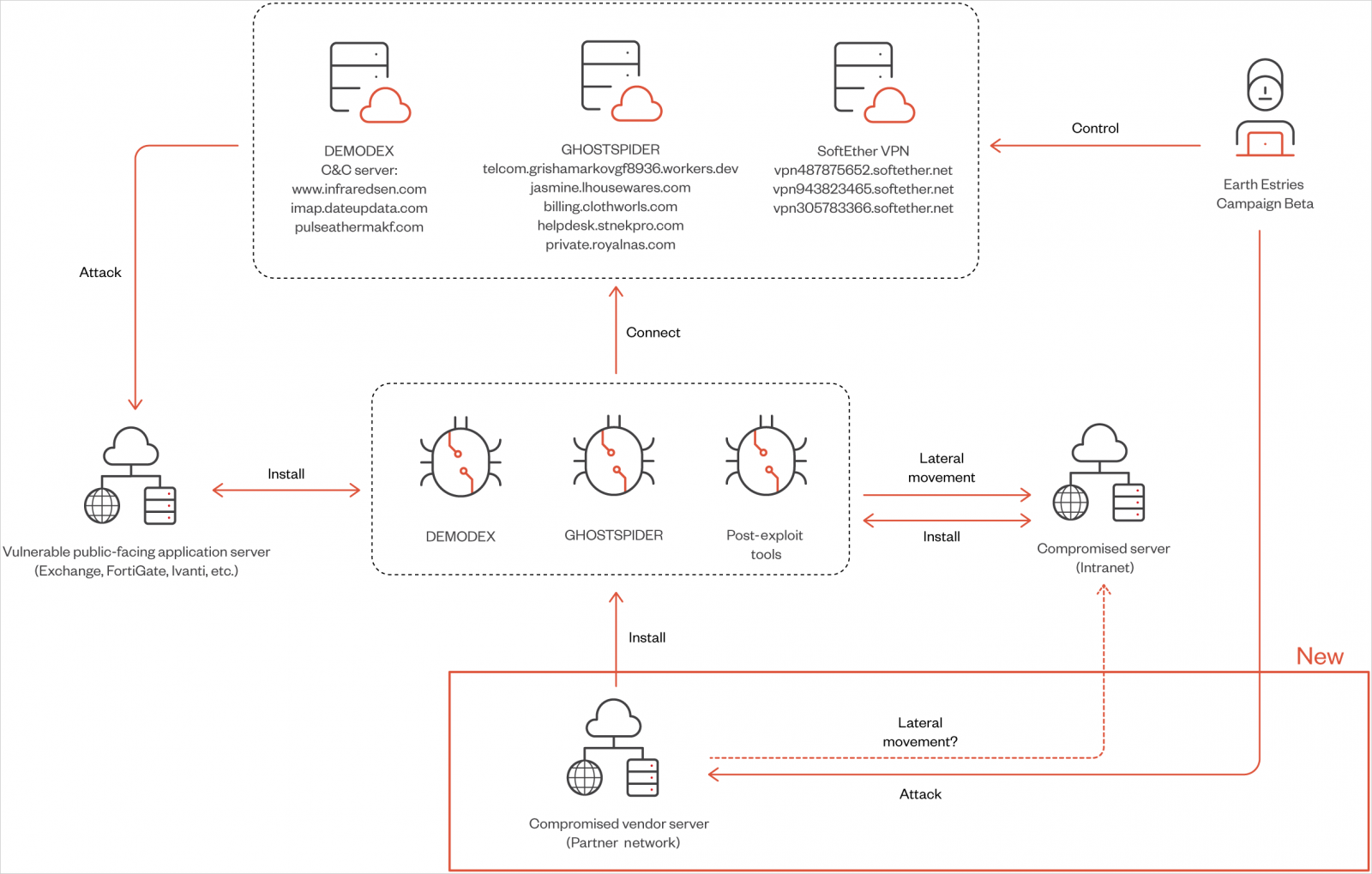
Two campaigns highlighted in the report are 'Alpha,' which targeted the Taiwanese government and chemical producers using Demodex and SnappyBee, and 'Beta,' a long-term espionage against Southeast Asian telecommunications and government networks, employing GhostSpider and Demodex.
Source: Trend Micro
Initial access is achieved through the exploitation of vulnerable public-facing endpoints, using exploits for the following flaws:
- CVE-2023-46805, CVE-2024-21887 (Ivanti Connect Secure VPN)
- CVE-2023-48788 (Fortinet FortiClient EMS)
- CVE-2022-3236 (Sophos Firewall)
- CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 (Microsoft Exchange – ProxyLogon)
Salt Typhoon uses LOLbin tools for intelligence gathering and lateral network movement in the post-compromise phase.
Source: Trend Micro
GhostSpider details
GhostSpider is a modular backdoor designed for long-term espionage operations requiring high levels of stealth, achieved through encryption and residing solely in memory.
It's loaded on the target system using DLL hijacking and registered as a service via the legitimate 'regsvr32.exe' tool, while a secondary module, the beacon loader, loads encrypted payloads directly in memory.
GhostSpider executes commands received from the command and control (C2) server, concealed within HTTP headers or cookies to blend with legitimate traffic.
The backdoor supports the following commands:
- Upload: Loads a malicious module into memory for execution of specific attacker-controlled tasks.
- Create: Activates the loaded module by initializing necessary resources for its operation.
- Normal: Executes the primary function of the loaded module, such as data exfiltration or system manipulation.
- Close: Removes the active module from memory to minimize traces and free system resources.
- Update: Adjusts the malware's behavior, such as communication intervals, to remain stealthy and effective.
- Heartbeat: Maintains periodic communication with the C&C server to confirm the system is still accessible.
The structure of these commands gives the backdoor versatility and allows Salt Typhoon to adjust their attack as needed depending on the victim's network and defenses.
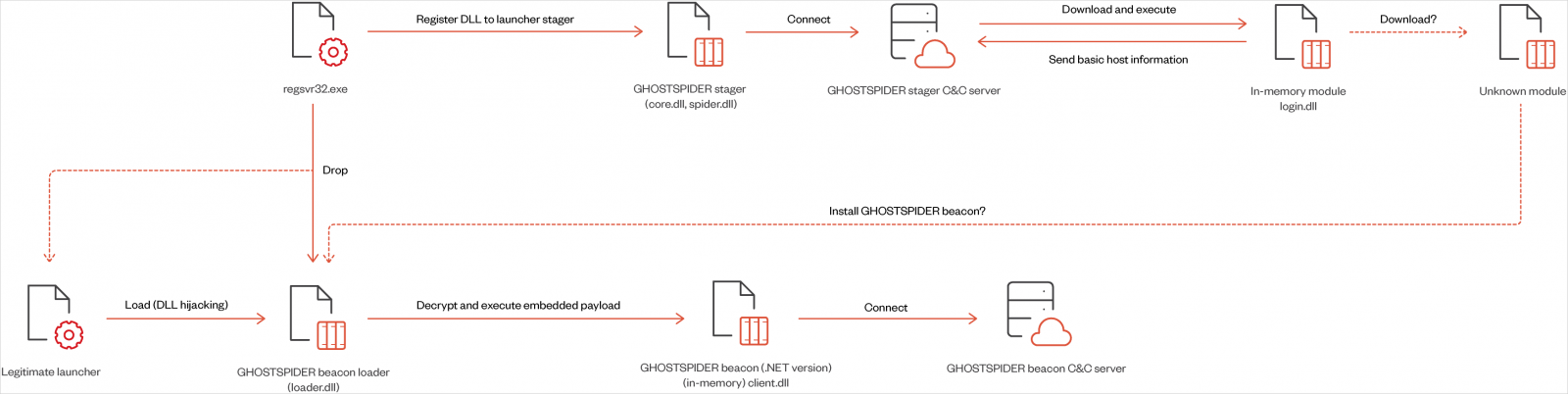
Source: Trend Micro
Other tools used by Salt Typhoon
Apart from GhostSpider, Salt Typhoon relies on a set of proprietary tools and ones shared among other Chinese threat actors that enable them to conduct complex, multi-stage espionage operations extending from edge devices to cloud environments.
- SNAPPYBEE: Modular backdoor (also called Deed RAT) used for long-term access and espionage. It supports functionalities like data exfiltration, system monitoring, and executing attacker commands.
- MASOL RAT: Cross-platform backdoor initially identified targeting Southeast Asian governments. It focuses on Linux servers, enabling remote access and command execution.
- DEMODEX: Rootkit used to maintain persistence on compromised systems. It leverages anti-analysis techniques and ensures the attacker remains undetected for extended periods.
- SparrowDoor: Backdoor providing remote access capabilities, used for lateral movement and establishing C&C communication.
- CrowDoor: Backdoor used for espionage, particularly targeting government and telecommunications entities, focused on stealth and data exfiltration.
- ShadowPad: Malware shared among Chinese APT groups, used for espionage and system control. It acts as a modular platform to deploy various malicious plugins.
- NeoReGeorg: Tunneling tool used for creating covert communication channels, allowing attackers to bypass network defenses and control compromised systems.
- frpc: Open-source reverse proxy tool used for creating secure connections to C&C servers, enabling data exfiltration and remote command execution.
- Cobalt Strike: Commercially available penetration testing tool co-opted by attackers to create beacons for lateral movement, privilege escalation, and remote control.
All in all, Salt Typhoon's arsenal is extensive, including widely used tools that can make attribution complicated when researchers have limited visibility.
Trend Micro concludes by characterizing Salt Typhoon as one of the most aggressive Chinese APT groups, urging organizations to remain vigilant and apply multi-layered cybersecurity defenses.
如有侵权请联系:admin#unsafe.sh