Dive into the evolution of phishing and malware evasion techniques and understand how attackers are using increasingly sophisticated methods to bypass security measures.
The Evolution of Phishing Attacks
"I really like the saying that 'This is out of scope' said no hacker ever. Whether it's tricks, techniques or technologies, hackers will do anything to evade detection and make sure their attack is successful," says Etay Maor, Chief Security Strategist at Cato Networks and member of Cato CTRL. Phishing attacks have transformed significantly over the years. 15-20 years ago, simple phishing sites were sufficient for capturing the crown jewels of the time - credit card details. Today, attacks and defense methods have become much more sophisticated, as we'll detail below.
"This is also the time where the "cat-and-mouse" attack-defense game began," says Tal Darsan, Security Manager and member of Cato CTRL. At the time, a major defense technique against credit card phishing sites involved flooding them with large volumes of numbers, in hopes of overwhelming them so they couldn't identify the real credit card details.
But threat actors adapted by validating data using methods like the Luhn algorithm to verify real credit cards, checking issuer information via Bank Identification Numbers (BIN), and performing micro-donations to test if the card was active.
Here's an example of how attackers validated credit card numbers inputted to phishing sites:
Anti-Researcher Techniques
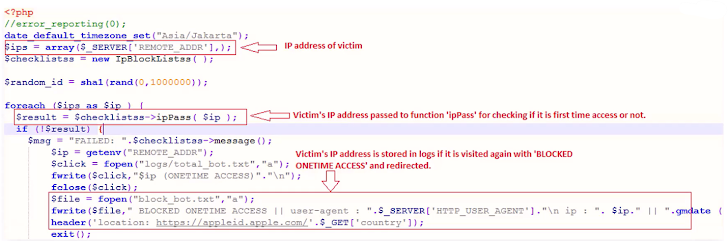
As phishing grew more advanced, attackers added anti-research techniques to prevent security analysts from studying and shutting down their operations. Common strategies included IP blocking after one-time access to create a false pretense that the phishing site was shut down, and detecting proxy servers, as researchers often use proxies when investigating.
The attacker code for one-time IP address access:
The attacker code for proxy identification:
Attackers have also been randomizing folder structures in their URLs during the past decades, deterring researchers from tracking phishing sites based on common directory names used in phishing kits. This can be seen in the image below:
Evading Anti-Virus
Another way to evade security controls in the past was to modify malware signatures with crypting services. This made it undetectable by signature-based antivirus systems. Here's an example of such a service that was once very popular:
Evading Device Verification
Let's move on to other modern evasion techniques. First, a phishing attack that targets victims by gathering detailed device information—such as Windows version, IP address, and antivirus software—so attackers can better impersonate the victim's device.
This data helps them bypass security checks, like device ID verification, which organizations, like banks, use to confirm legitimate logins. By replicating the victim's device environment (e.g., Windows version, media player details, hardware specs), attackers can avoid suspicion when logging in from different locations or devices.
Some dark web services even provide pre-configured virtual machines that mirror the victim's device profile (see image below), adding an extra layer of anonymity for attackers and enabling safer access to compromised accounts. This demonstrates how data science and customization have become integral to criminal operations.
Evading Anomaly Detection
Another case is when defenders faced a gang using malware to exploit live bank sessions, waiting for victims to log in before swiftly performing unauthorized transactions. The challenge was that these actions appeared to come from the victim's own authenticated session, making detection difficult.
This resulted in a cat-and-mouse game between attackers and defenders:
- Initially, defenders implemented a velocity check, flagging transactions completed too quickly as likely fraudulent.
- In response, attackers modified their code to simulate human typing speed by adding delays between keystrokes. This can be seen in the code below:
- When defenders adjusted for this by adding random timing checks, attackers countered with variable delays, blending further into legitimate behavior.
This illustrates the complexity of detecting sophisticated, automated banking fraud amidst legitimate transactions.
Evasive Phishing Attacks
Now let's move on to more recent attacks. One of the most prominent attacks analyzed by Cato CTRL included a clever phishing attack designed to mimic Microsoft support. The incident began with a 403 error message that directed the user to a page claiming to be "Microsoft support", complete with prompts to "get the right help and support." The page presented options for "Home" or "Business" support, but regardless of which option was chosen, it redirected the user to a convincing Office 365 login page.
This fake login page was crafted as part of a social engineering scheme to trick users into entering their Microsoft credentials. The attack leveraged psychological triggers, such as mimicking error messages and support prompts, to build credibility and exploit the user's trust in Microsoft's brand. This was a sophisticated phishing attempt, focusing on social engineering rather than relying solely on advanced evasion techniques.
Deceptive Redirection Chain
In this next analysis, Cato CTRL investigated a phishing attack that employed complex redirection techniques to evade detection. The process began with a deceptive initial link, disguised as a popular search engine in China, which redirected through multiple URLs (using HTTP status codes like 402 and 301) before eventually landing on a phishing page hosted on a decentralized web (IPFS) link. This multi-step redirection sequence complicates tracking and logging, making it harder for cybersecurity researchers to trace the true origin of the phishing page.
As the investigation continued, the Cato CTRL researcher encountered multiple evasion techniques embedded within the phishing site's code. For example, the phishing page included Base64-encoded JavaScript that blocked keyboard interactions, effectively disabling the researcher's ability to access or analyze the code directly. Additional obfuscation tactics included breakpoints in the developer tools, which forced redirection to the legitimate Microsoft homepage to hinder further inspection.
By disabling these breakpoints in Chrome's developer tools, the researcher eventually bypassed these barriers, allowing full access to the phishing site's source code. This tactic highlights the sophisticated, layered defenses attackers implement to thwart analysis and delay detection, leveraging anti-sandboxing, JavaScript obfuscation and redirection chains.
Phishing Resources-based Detection
Attackers are constantly adapting their own defense techniques to avoid detection. Researchers have relied on static elements, such as image resources and icons, to identify phishing pages. For instance, phishing sites targeting Microsoft 365 often replicate official logos and icons without altering names or metadata, making them easier to spot. Initially, this consistency gave defenders a reliable detection method.
However, threat actors have adapted by randomizing almost every element of their phishing pages.
To evade detection, attackers now:
- Randomize Resource Names - Image and icon filenames, previously static, are heavily randomized on each page load.
- Randomize Page Titles and URLs - The titles, subdomains and URL paths constantly change, creating new randomized strings each time the page is accessed, making it more challenging to track.
- Implement Cloudflare Challenges - They use these challenges to verify that a human (not an automated scanner) is accessing the page, which makes automated detection by security tools harder.
Despite these techniques, defenders have found new ways to bypass these evasions, although it's an ongoing game of adaptation between attackers and researchers.
The masterclass reveals many more malware and phishing attacks and how they evade traditional measures, including:
- Malware droppers for payload distribution.
- HTML files in phishing emails to initiate a multi-step malware download involving password-protected zip files.
- File smuggling and magic byte manipulation.
- SVG smuggling and B64 encoding.
- Leveraging trusted cloud applications (e.g., Trello, Google Drive) for command and control to avoid detection by standard security systems.
- Prompt injections within malware to mislead AI-based malware analysis tools.
- Repurposing the TDSS Killer rootkit removal tool to disable EDR services, specifically targeting Microsoft Defender.
- Telegram bots as a means of receiving stolen credentials, allowing attackers to quickly create new drop zones as needed.
- Generative AI used by attackers to streamline the creation and distribution of attacks.
- Network-based threat hunting without endpoint agents.
What's Next for Defenders?
How can defenders gain the upper hand in this ongoing cat-and-mouse game? Here are a few strategies:
- Phishing Training & Security Awareness - While not foolproof, awareness training raises the likelihood of recognizing and mitigating cyber threats.
- Credential Monitoring - Leveraging tools that analyze connection patterns can preemptively block potentially malicious activities.
- Machine Learning & Threat Detection - Advanced tools to identify sophisticated threats.
- Unified Threat Hunting Platform - A single, converged platform approach (rather than multiple point solutions) for expanded threat hunting. This includes network-based threat hunting without endpoint agents and using network traffic analysis to detect IoCs.
- Attack Surface Reduction - Proactively reducing attack surfaces by auditing firewalls, tuning configurations and reviewing security settings regularly. Addressing misconfigurations and following vendor advisories can help secure the organization's defenses against new threats.
- Avoiding Platform Bloat - Multiple attack chokepoints along the threat kill chain are essential, "but this does not mean adding many point solutions," emphasizes Maor. "A converged platform with one interface that actually can look at everything: the network, the data, through a single pass engine running through each packet and understanding whether it's malicious or not."
Watch the entire masterclass here.
Found this article interesting? This article is a contributed piece from one of our valued partners. Follow us on Twitter and LinkedIn to read more exclusive content we post.