
2024-11-16 23:24:18 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Despite advances in security technology, cybersecurity attacks and data breaches are increasingly common as attackers keep discovering new vulnerabilities and infiltration methods. Organizations now understand that a cyberattack or data breach is often inevitable—it’s typically a question of when, not if. The positive side is that cybersecurity crisis management plans can help businesses prepare effectively for these incidents. To grasp the meaning of crisis management in cybersecurity, it’s essential first to review concepts like crisis, crisis management, and cyberattacks. In this blog we will discuss about cyber crisis management plan in detail.
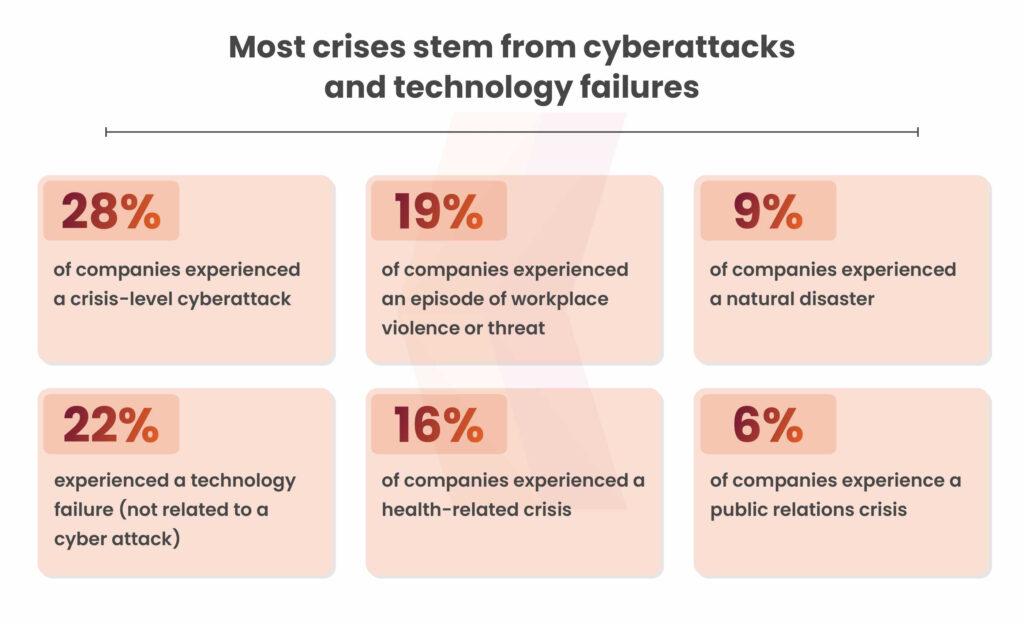
What is a Cyber Crisis Management Plan?
The term “crisis” comes from the Greek word “krisis,” meaning a decisive moment in illness, leading either to recovery or decline. Today, “crisis” generally refers to a challenging period faced by an individual, group, or—when it comes to IT issues—a company.
In France, the equivalent of the UK’s Home Office, IHEMI, defines a cyber crisis as a situation involving a cyberattack that specifically targets a company’s digital assets, technical infrastructure, or information systems.
Addressing cyber crises requires a multi-faceted crisis management approach, including:
- preventing crises before they arise,
- applying a crisis resolution process once an IT breach is confirmed,
- deploying tools and strategies to counter the breach,
- refining the crisis management procedure based on feedback.
Cyber crises have unique characteristics and risks:
- They are nearly always IT-related and inherently technical.
- They are often detected late, after the hacker may have been active for months.
- Their impact is generally significant, affecting internal and external perceptions and damaging both employee morale and the company’s reputation.
- They demand cross-functional management, involving teams unaccustomed to working together.
- Traditional communication channels may be compromised and unavailable.
- Resolving a cyber crisis is seldom a quick process.
Why Organizations Require Cyber Crisis Management Plan?
An effective cyber crisis management plan minimizes the impact of security incidents. Established playbooks promote calm, strategic decision-making, enabling swift and effective responses when threats arise. A key advantage is faster incident response: quickly identifying, isolating, and mitigating an attack significantly reduces damage. Engaging third-party experts, such as cybersecurity firms, can further accelerate threat containment.
Comprehensive response plans help lower costs and mitigate legal or regulatory penalties by preventing threat spread. Without a plan, breaches often escalate, affecting more employees, halting operations, and causing reputational harm. In the U.S., companies may face federal and state penalties if negligence is found to have allowed large-scale breaches.
How an organization handles a cyberattack also influences public perception and brand reputation. Companies that manage breaches transparently can still earn trust; for instance, the International Committee of the Red Cross (ICRC) received positive feedback after a cyberattack exposed employee and customer data by openly communicating and committing to strengthened security. Documenting a management plan provides evidence of due diligence, supporting audits and instilling confidence in preparedness for worst-case scenarios.
Book a Free Consultation with our Cyber Security Experts

Steps to Create a Cyebr Crisis Management Plan
Creating a strong cybersecurity crisis management plan usually takes weeks or even months and requires support from top leadership. Although plans vary by organization, here are some essential steps to consider.
Step 1: Assemble an Incident Response Team
Appoint the team or individuals responsible for leading your organization’s crisis response efforts, with ongoing involvement in developing and updating the plan as risks evolve.
Key roles on an incident response team may include:
- CISO or head of information security
- IT security engineers
- Legal counsel
- Communications lead
- Business continuity manager
- Third-party forensics firm
The team’s size and structure will depend on available resources and expected incident types, with external experts often offering essential support.
Step 2: Classify Crisis Safety
Not all cybersecurity incidents demand full crisis management. It’s important to establish thresholds based on potential business impacts, such as significant financial, legal, reputational, or operational disruptions beyond routine incidents.
Examples include:
- Major data loss requiring public disclosure
- Ransomware causing operational blackouts
- Safety risks from compromised industrial control systems
- CLOUD Act warrants potentially exposing intellectual property
Step 3: Map Out Escalation Process with Flowcharts
Visual aids simplify crisis response protocols. Use step-by-step flowcharts to outline key actions, such as assessment, containment, remediation, reporting, public communication, and recovery.
Create tailored flowcharts for specific incident types:
- Data breaches
- Denial-of-service attacks
- Critical IT infrastructure failures
- Supply chain disruptions
- Insider threats
- Third-party risks
- Common attack vectors
Step 4: Conduct Ongoing Risk Assessments
Continuous risk assessments are crucial for effective crisis communication management. Regular evaluations help teams:
- Identify potential threats
- Highlight significant risks
- Gather information for relevant stakeholders based on the RACI chart
- Collect feedback to guide next steps
Periodic risk assessments allow teams to identify and prioritize risks, vulnerabilities, and potential attack vectors, organizing them by threat level. Partnering with third-party penetration testing experts can also help uncover overlooked weaknesses.
Kratikal’s Approach to Cyber Crisis Management Plan
Kratikal’s approach to Cyber Crisis Management Plan focuses on proactive preparedness and swift response to minimize the impact of security incidents. Here are the key components:
Identification of Problem Statement
This is part of an enterprise resilience program that identifies critical business services to inform planning for potential disruptions. By understanding the organization’s cyber response capabilities and critical services, Kratikal enhances resilience and preparedness for cyber incidents and disruptions.
Developing a Communication Plan
The communication plan ensures timely, accurate, and consistent information sharing during a cyber incident. It includes defining the strategy, roles, and responsibilities of communication team members, along with specifying communication methods.
Creation of Response Procedures
Kratikal helps organizations prepare with response procedures. These procedures act as a roadmap, guiding teams through the steps of detecting, assessing, containing, and recovering from cyber incidents, minimizing damage, and getting organizations day to day operations back on track quickly.
Conducting Drill Exercise
Drill exercises within a cyber crisis management plan are vital for evaluating plan effectiveness, assessing incident response team readiness, identifying gaps, and enhancing overall cyber resilience. These exercises simulate different cyber crisis scenarios, enabling the team to practice response procedures in a controlled setting.
Review and Update the Plan
Regular reviews and updates are crucial to uphold the effectiveness and relevance of the cyber crisis management plan. This process should include a thorough evaluation of the plan’s components, response procedures, communication strategies, and incident response team readiness.
How can Kratikal Help in Cyber Crisis Management Plan?
Kratikal’s Cyber Crisis Management Plan focuses on preparing organizations for cyber incidents by developing comprehensive strategies, roles, and communication protocols. It emphasizes the identification of risks, the creation of response procedures, and the execution of crisis drills to ensure business continuity. The approach includes policy drafting, gap assessments, implementation, and certification, following ISO 27001 standards to enhance resilience. Kratikal helps organizations navigate cyber crises with tailored, efficient plans that reduce risks, minimize reputational damage, and ensure a swift recovery. For more details, visit Kratikal’s Cyber Crisis Management Plan.
FAQs
- What are the 5 P’s of cyber crisis management plan?
The National Crisis Management Framework outlines a structured approach to crisis management, focusing on the 5Ps: Predict, Prevent, Prepare, Perform, and Post-Action and Assessment. These components guide organizations through identifying, mitigating, responding to, and learning from crises to enhance resilience and readiness for future challenges.
- What is a crisis management plan?
A crisis management plan details how a business will respond to a crisis, specifying the actions and roles of individuals involved. Its primary goal is to minimize harm and quickly restore normal business operations. By clearly defining responsibilities and procedures, it ensures a more organized and effective response during crucial situations.
The post Cyber Crisis Management Plan: Shield for Brand Reputation appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/cyber-crisis-management-plan-shield-for-brand-reputation/
如有侵权请联系:admin#unsafe.sh

