2024-11-14 03:16:25 Author: securityaffairs.com(查看原文) 阅读量:2 收藏
China’s Volt Typhoon botnet has re-emerged
Pierluigi Paganini
November 13, 2024

China’s Volt Typhoon botnet has re-emerged, using the same core infrastructure and techniques, according to SecurityScorecard researchers.
The China-linked Volt Typhoon’s botnet has resurfaced using the same infrastructure and techniques, per SecurityScorecard researchers.
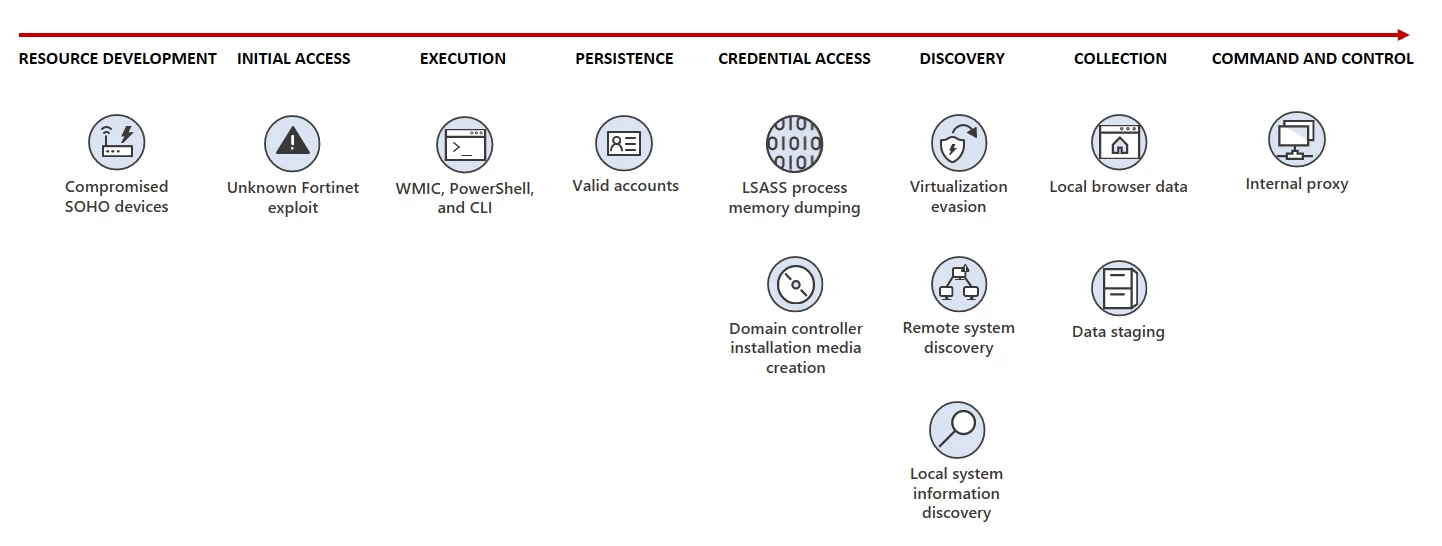
In May 2023, Microsoft reported that the Volt Typhoon APT infiltrated critical infrastructure organizations in the U.S. and Guam without being detected. The group managed to maintain access without being detected for as long as possible.
According to Microsoft, the campaign aimed at building capabilities that could disrupt critical communications infrastructure between the United States and Asia region in the case of future crises.
The Volt Typhoon group has been active since at least mid-2021 it carried out cyber operations against critical infrastructure. In the most recent campaign, the group targeted organizations in the communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors.
The APT group is using almost exclusively living-off-the-land techniques and hands-on-keyboard activity to evade detection.
Microsoft first noticed that to conceal malicious traffic, the threat actor routes it through compromised small office and home office (SOHO) network devices, including routers, firewalls, and VPN hardware. The group also relies on customized versions of open-source tools for C2 communications and stay under the radar.
In December 2023, the Black Lotus Labs team at Lumen Technologies linked a small office/home office (SOHO) router botnet, tracked as KV-Botnet to the operations of China-linked threat actor Volt Typhoon. The botnet is comprised of two complementary activity clusters, the experts believe it has been active since at least February 2022. The threat actors target devices at the edge of networks.
The KV-Botnet is composed of end-of-life products used by SOHO devices. In early July and August of 2022, the researchers noticed several Cisco RV320s, DrayTek Vigor routers, and NETGEAR ProSAFEs that were part of the botnet. Later, in November 2022, most of the devices composing the botnet were ProSAFE devices, and a smaller number of DrayTek routers. In November 2023, the experts noticed that the botnet started targeting Axis IP cameras, such as the M1045-LW, M1065-LW, and p1367-E.
At the end of 2023, the U.S. government neutralized the Volt Typhoon botnet taking over its C2 and deleting the bot from infected devices. However, despite the botnet disruption, Volt Typhoon remains active. with CISA warning that the group has been positioning itself within critical infrastructure networks, likely for potential disruption or sabotage.
In February, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Federal Bureau of Investigation (FBI) assessed that People’s Republic of China (PRC) state-sponsored cyber actors warned that the APT group had been pre-positioning itself on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with the United States.
In August 2023, Volt Typhoon exploited a zero-day vulnerability, tracked as CVE-2024-39717, in Versa Director, to deploy a custom webshell on breached networks.
The VersaMem web shell is a sophisticated, custom-tailored JAR web shell designed to target Versa Director systems. The malware is developed through Apache Maven, it was built on June 3, 2024, and attaches itself to the Apache Tomcat process on execution. The malicious code uses the Java Instrumentation API and Javassist toolkit to modify Java code in memory, avoiding detection.
The web shell supports two primary functions: capturing plaintext user credentials and dynamically loading Java classes in memory. It intercepts credentials by hooking into Versa’s “setUserPassword” method, encrypting and storing them on disk. It also hooks into the “doFilter” method of the Tomcat web server to inspect and dynamically load malicious Java modules based on specific parameters. The malware operates directly in memory, it doesn’t modify files on disk to avoid detection
Now SecurityScorecard warned that the botnet is back, it is composed of compromised Netgear ProSafe, Cisco RV320/325 and Mikrotik networking devices.
“Once thought dismantled, Volt Typhoon has returned, more sophisticated and determined than ever. Unlike attackers who vanish when discovered, this adversary digs in even deeper when exposed. According to the STRIKE Team, Volt Typhoon’s tactics are adaptive and multifaceted. They exploit legacy weaknesses in Cisco RV320/325 routers and Netgear ProSafe routers, devices long past their prime, using them as operational relay boxes.” reads the analysis published by SecurityScorecard. “These end-of-life devices become perfect entry points, and in just 37 days, Volt Typhoon compromised 30% of visible Cisco RV320/325 routers.
SecurityScorecard noticed that the APT group is still using the core infrastructure of its botnet and employed the same techniques of previous campaigns. The experts noticed that a compromised VPN device in New Caledonia, previously taken down, was again routing traffic between Asia-Pacific and America.
“New Caledonia is crucial to Volt Typhoon’s global operations. A compromised VPN device on this small Pacific island acts as a silent bridge, routing traffic between Asia-Pacific and American regions without detection. This covert hub enables Volt Typhoon to avoid scrutiny and extends the botnet’s reach.” continues the report.
While Volt Typhoon doesn’t use ransomware, its ecosystem benefits from Ransomware-as-a-Service (RaaS), where ransom payments fund advanced tools, escalating attack risks, especially through third-party and cloud dependencies.
“The STRIKE Team’s discoveries highlight the expanding threat posed by Volt Typhoon. As the botnet spreads and its tactics deepen, governments and corporations must urgently address weaknesses in legacy systems, public cloud infrastructures, and third-party networks.” concludes the report. “Volt Typhoon is both a resilient botnet—and a warning. Without decisive action, this silent threat could trigger a critical infrastructure crisis driven by vulnerabilities left unresolved.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, China)
如有侵权请联系:admin#unsafe.sh