A Critical Guide to Securing Large Language Models
glenn.hamilton…
Securing large language models (LLMs) presents unique challenges due to their complexity, scale, and data interactions. Before we dive into securing them, let’s touch on the basics.
- What are LLMs? LLMs are Large Language Models that are advanced artificial intelligence systems designed to understand and generate human-like text.
- How popular are LLMs? Incredibly, as they generate text, images, answer questions, and write creative content for you.
- How do businesses use LLMs? They enhance customer service, create content, summarize research, analyze large datasets, and translate languages.
Securing LLMs is critical as they are trained on massive datasets that contain sensitive information. Protecting LLMs from unauthorized access or misuse is vital.
The Thales Solution for LLM Security
- CTE agent: The CTE (CipherTrust Transparent Encryption) agent is a software component installed at the kernel level on a physical or virtual machine. It encrypts and protects data on that machine. Once installed, the CTE agent enables encryption for any number of devices or directories on the machine, ensuring that only authorized users and processes can access the encrypted data at file system level transparent to the application.
- CTE-U agent: The CTE-U (CipherTrust Transparent Encryption UserSpace) agent is a user-space level encryption solution that serves the same fundamental purpose, as the CTE agent. Unlike the CTE agent, the CTE-U agent operates at the user-space level.
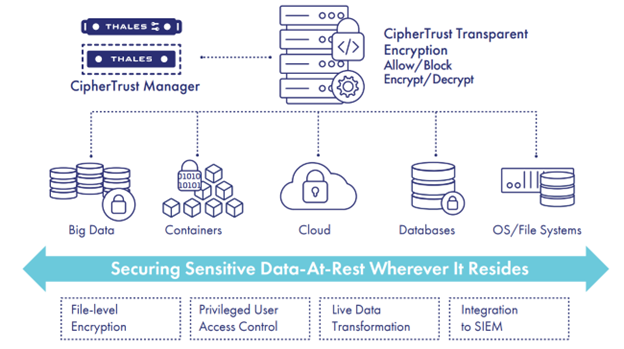
What is CipherTrust Transparent Encryption?
CipherTrust Transparent Encryption (CTE), is part of the CipherTrust Data Security Platform (CDSP) which delivers data-at-rest encryption with centralized key management, privileged user access control and detailed data access audit logging. Protecting data wherever it resides, on-premises, across multiple clouds and within big data, and Kubernetes environments. The deployment is simple, scalable, and fast, with agents installed at operating, filesystem or device layer, and encryption and decryption are transparent to all applications that run above it. CipherTrust Transparent Encryption is designed to meet data security compliance and best practice requirements with minimal disruption, effort, and cost. Implementation is seamless keeping both business and operational processes working without changes even during deployment and roll out. The solution works in conjunction with the FIPS 140-2 up to Level 3 compliant CipherTrust Manager, which centralizes encryption key and policy management for CDSP.
Benefits of CipherTrust Transparent Encryption
Simplified Management: CipherTrust Manager provides a unified management console that enables you to discover and classify sensitive data and protect data using integrated Thales Data Protection Connectors across on-premises data stores and multi-cloud deployments. It offers advanced self-service licensing for improved visibility and control of licenses.
Cloud-friendly Deployment: CipherTrust Manager offers users additional hosting options, and can run as a native virtual machine on AWS, Microsoft Azure, Google Cloud, VMware, Microsoft HyperV and more. Additionally, native support for CipherTrust Cloud Key Management is available on CipherTrust Manager to streamline key management across multiple cloud infrastructures and SaaS applications.
Flexible Form Factors:
CipherTrust Manager is available in both virtual and physical form factors. Flexible deployment options can easily scale to provide key management at remote facilities or in cloud infrastructures. CipherTrust Manager supports managing keys in the FIPS 140 L3 boundary of Luna Network HSM.
Protect LLMs with Thales
To Protect LLMs, the Thales CipherTrust Data Security Platform with Transparent Encryption is used, whereas enterprises can leverage Thales’ advanced data protection features within the CipherTrust platform. Thales is a trusted brand in the LLM Security Industry. View our comprehensive White Paper for information on LLM Security. We’ll continue to innovate with LLM Security and continue publishing updates in future articles.

Securing large language models (LLMs) presents unique challenges due to their complexity, scale, and data interactions. Before we dive into securing them, let’s touch on the basics.
- What are LLMs? LLMs are Large Language Models that are advanced artificial intelligence systems designed to understand and generate human-like text.
- How popular are LLMs? Incredibly, as they generate text, images, answer questions, and write creative content for you.
- How do businesses use LLMs? They enhance customer service, create content, summarize research, analyze large datasets, and translate languages.
Securing LLMs is critical as they are trained on massive datasets that contain sensitive information. Protecting LLMs from unauthorized access or misuse is vital.
The Thales Solution for LLM Security
- CTE agent: The CTE (CipherTrust Transparent Encryption) agent is a software component installed at the kernel level on a physical or virtual machine. It encrypts and protects data on that machine. Once installed, the CTE agent enables encryption for any number of devices or directories on the machine, ensuring that only authorized users and processes can access the encrypted data at file system level transparent to the application.
- CTE-U agent: The CTE-U (CipherTrust Transparent Encryption UserSpace) agent is a user-space level encryption solution that serves the same fundamental purpose, as the CTE agent. Unlike the CTE agent, the CTE-U agent operates at the user-space level.
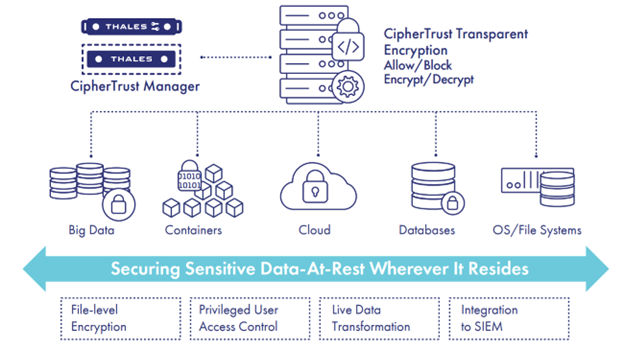
What is CipherTrust Transparent Encryption?
CipherTrust Transparent Encryption (CTE), is part of the CipherTrust Data Security Platform (CDSP) which delivers data-at-rest encryption with centralized key management, privileged user access control and detailed data access audit logging. Protecting data wherever it resides, on-premises, across multiple clouds and within big data, and Kubernetes environments. The deployment is simple, scalable, and fast, with agents installed at operating, filesystem or device layer, and encryption and decryption are transparent to all applications that run above it. CipherTrust Transparent Encryption is designed to meet data security compliance and best practice requirements with minimal disruption, effort, and cost. Implementation is seamless keeping both business and operational processes working without changes even during deployment and roll out. The solution works in conjunction with the FIPS 140-2 up to Level 3 compliant CipherTrust Manager, which centralizes encryption key and policy management for CDSP.

Benefits of CipherTrust Transparent Encryption
Simplified Management: CipherTrust Manager provides a unified management console that enables you to discover and classify sensitive data and protect data using integrated Thales Data Protection Connectors across on-premises data stores and multi-cloud deployments. It offers advanced self-service licensing for improved visibility and control of licenses.
Cloud-friendly Deployment: CipherTrust Manager offers users additional hosting options, and can run as a native virtual machine on AWS, Microsoft Azure, Google Cloud, VMware, Microsoft HyperV and more. Additionally, native support for CipherTrust Cloud Key Management is available on CipherTrust Manager to streamline key management across multiple cloud infrastructures and SaaS applications.
Flexible Form Factors:
CipherTrust Manager is available in both virtual and physical form factors. Flexible deployment options can easily scale to provide key management at remote facilities or in cloud infrastructures. CipherTrust Manager supports managing keys in the FIPS 140 L3 boundary of Luna Network HSM.
Protect LLMs with Thales
To Protect LLMs, the Thales CipherTrust Data Security Platform with Transparent Encryption is used, whereas enterprises can leverage Thales’ advanced data protection features within the CipherTrust platform. Thales is a trusted brand in the LLM Security Industry. View our comprehensive White Paper for information on LLM Security. We’ll continue to innovate with LLM Security and continue publishing updates in future articles.
Schema
{
“@context”: “https://schema.org”,
“@type”: “BlogPosting”,
“headline”: “A Critical Guide to Securing Large Language Models”,
“description”: “Explore the complexities of securing large language models (LLMs) and learn how Thales’ CipherTrust Transparent Encryption (CTE) provides advanced protection for sensitive data and compliance across cloud and on-premises environments.”,
“datePublished”: “2024-11-07”,
“author”: {
“@type”: “Person”,
“name”: “Doug Bies”,
“url”: “https://cpl.thalesgroup.com/blog/author/dbies”,
“sameAs”: “https://www.linkedin.com/in/doug-bies-440487a/”
},
“publisher”: {
“@type”: “Organization”,
“name”: “Thales Group”,
“description”: “The world relies on Thales to protect and secure access to your most sensitive data and software wherever it is created, shared, or stored. Whether building an encryption strategy, licensing software, providing trusted access to the cloud, or meeting compliance mandates, you can rely on Thales to secure your digital transformation.”,
“url”: “https://cpl.thalesgroup.com”,
“logo”: “https://cpl.thalesgroup.com/sites/default/files/content/footer/thaleslogo-white.png”,
“sameAs”: [
“https://www.facebook.com/ThalesCloudSec”,
“https://www.twitter.com/ThalesCloudSec”,
“https://www.linkedin.com/company/thalescloudsec”,
“https://www.youtube.com/ThalesCloudSec”
]
},
“mainEntityOfPage”: “https://cpl.thalesgroup.com/blog/data-security/securing-llms”
}
studio
*** This is a Security Bloggers Network syndicated blog from Thales CPL Blog Feed authored by [email protected]. Read the original post at: https://cpl.thalesgroup.com/blog/data-security/securing-llms