2024-11-7 23:37:33 Author: securityboulevard.com(查看原文) 阅读量:22 收藏
Threat actors are becoming increasingly creative, using vulnerabilities to infiltrate organizations in ways that might not immediately raise alarms. Veriti’s research team recently discovered a targeted email campaign utilizing CVE-2024-38213, cleverly disguised to appear associated with the Gas Infrastructure Europe (GIE) Annual Conference in Munich. By taking advantage of this vulnerability, attackers managed to bypass standard security protocols and deploy dangerous malware, including LummaStealer, to steal sensitive data.
Targeted Attack on the GIE Annual Conference
Our team uncovered an email campaign specifically targeting attendees of the GIE Annual Conference in Munich. This attack exploits CVE-2024-38213, deploying LummaStealer to infiltrate systems and steal data.

Here’s a breakdown of the attack:
- The attacker used CVE-2024-38213 to download a malicious file that deployed LummaStealer.
- The attack was initiated through an email attachment (LNK file) leveraging CVE-2024-38213.
- The attachment file contained a download function:

- A connection was established to a malicious domain designed to resemble the conference’s official URL:
- Domain Creation Date: October 3, 2024
- Malicious Domain: gieannualconferenceinmunich[.]com

Inspecting the Crumbs: CVE-2024-38213 in Detail
Over the past year, we’ve seen a sharp increase in the use of CVE-2024-38213, also known as Copy2Pwn. This vulnerability appears to be an evolution of CVE-2024-21412, previously exploited by the APT group Water Hydra. For more on Water Hydra, refer to Trend Micro’s analysis.
CVE-2024-38213 is designed to bypass the Mark-of-the-Web (MotW) feature in Microsoft Windows, which typically flags files originating from the internet, prompting additional scrutiny by Microsoft Defender SmartScreen. MotW acts as an additional security layer, warning users when high-risk extensions are opened, but CVE-2024-38213 bypasses this, creating a dangerous gap in defenses.
Real World Exploitation and Threat Actors
In recent months, Veriti’s research linked CVE-2024-38213 to multiple threat actors, including AsyncRAT and XWorm, notorious for remote control capabilities that allow attackers to gain unauthorized access, steal information, and deploy further malicious payloads. Here are some statistics on the frequency and spread of these attacks across different campaigns.

Timeline of CVE-2024-38213 Exploitation
Here’s a timeline that showcases how different threat actors have used CVE-2024-38213:
| December 2023 | March 2024 | May 2024 | July 2024 | August 2024 | August 2024 | September 2024 |
| Water Hydra utilizes a “crumb” technique in attacks, setting the stage for Copy2Pwn’s widespread use. | DarkGate RAT begins using CVE-2024-38213. | VenomRAT appears in the wild with this vulnerability. | XWorm incorporates CVE-2024-38213 into its campaigns. | FormBook attacks emerge. | Microsoft issues a patch following Trend Micro’s research. | AsyncRAT is observed leveraging this vulnerability for attacks. |
Example of AsyncRAT and XWorm Exploiting CVE-2024-38213
AsyncRAT and XWorm are particularly concerning due to their capabilities for remote control, data theft, and deployment of additional payloads. These attacks often start with phishing emails containing malicious attachments, leading to a series of downloads that culminate in the installation of XWorm. From there, the malware establishes a connection to a command-and-control (C2) server, siphoning off sensitive data.
A recent example of XWorm exploiting CVE-2024-38213 can be viewed on VirusTotal.

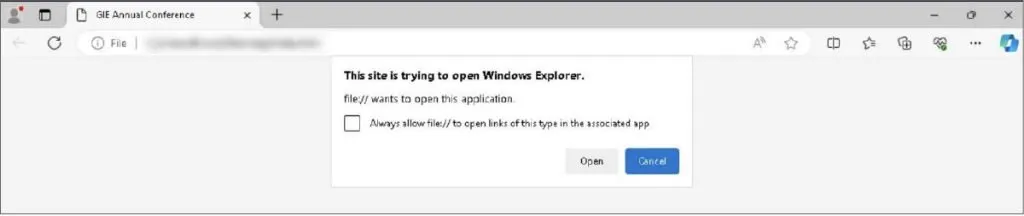
When victims open the attachment, they are prompted to open Windows Explorer, which triggers a malicious file download using the crumb function from the destination folder.


Continuing Campaigns: LummaStealer’s Role in the Attack
Our analysis also uncovered additional files related to this campaign that deploy LummaStealer. This malware uses a multi-stage payload that drops an executable file, dccw.exe, posing as a legitimate file to avoid detection. Details of this file can be seen on VirusTotal.

Here’s the process LummaStealer follows:
- The PDF attachment drops an executable named dccw.exe.
- The execution parent file for this attachment can be traced here.
Further analysis revealed the script demonstrates a sophisticated use of forfiles.exe and PowerShell to manipulate a Windows environment, potentially for malicious purposes. Starting with forfiles.exe in C:\Windows\System32, the script appears to scan the root directory (/p C:\) for instances of “Windows” files or directories (/m Windows) to execute further commands. Within its payload, a PowerShell command constructs a complex, obfuscated file path using *i*\*2\msh*e, targeting an external URL: hxxps://gurt.duna[.]ua/programy-nauczania/GIEAnnualConferenceStage2.
The script then combines Get-Location and Join-Path to create a deceptive link file named GIE Annual Conference 2024 in Munich Participant Form Event Agency.pdf.lnk, which appears like a legitimate PDF but could launch further payloads or commands if clicked. Finally, it uses del to remove traces of this shortcut, suggesting a careful approach to hiding its activities, while also referencing a specific Security Identifier (S-1-5-21-3129671405-2799430066-3803874638-1000), potentially targeting a specific user context. This layered approach showcases how attackers can leverage standard system utilities to create persistent, undetected threats by exploiting directory traversal, external payloads, and file obfuscation.

Picking up the Crumbs: Key Action Items
To protect against similar attacks, Veriti recommends the following steps:
- Restrict Attachments: Disallow URL, HTML, and HTM file types as email attachments within your organization. These formats are often used in malicious campaigns.
- Deploy SIGMA Rules: Use SIGMA rules to detect malicious activity related to CVE-2024-38213. Veriti provides a SIGMA rule that translates easily into common EDRs and SIEMs, automatically pushing detections for this threat.
- Block Indicators of Compromise (IoCs):
- 84[.]32[.]189[.]74
- 89.23.107[.]75
- fxbulls[.]ru
- ledgeronbill[.]com
- robshippings[.]cloud
- shippingmentnotice[.]xyz
- trackmyshipeng[.]site
As attackers evolve, vulnerabilities like CVE-2024-38213 present unique challenges to organizations. From deploying remote access tools to executing multi-stage attacks, cybercriminals are using increasingly sophisticated techniques to bypass security. Veriti’s research into CVE-2024-38213 highlights the need for proactive defense strategies and a continuous review of security controls to counter these threats effectively.
By implementing strong controls, such as restricting vulnerable attachment types, deploying SIGMA detection rules, and blocking critical IoCs, organizations can harden their defenses. For those looking to stay informed and prepared, subscribe to the Veriti blog for the latest insights on emerging threats and effective remediation strategies.
Subscribe to our BLOG
Get the latest security insights, news and articles delivered to your inbox.
如有侵权请联系:admin#unsafe.sh

