Welcome to ANY.RUN‘s monthly updates, where we share our latest achievements and improvements.
October has been another productive month here at ANY.RUN, filled with new features to enhance your cybersecurity toolkit. We’ve introduced TI Lookup Notifications for real-time threat updates, rolled out a newly improved Linux sandbox for smoother malware analysis, and added the ability to export STIX reports for seamless data sharing.
In addition, we’ve expanded our detection capabilities with a range of new signatures and YARA rules, empowering you with even stronger threat coverage.
And that’s just the beginning!
Let’s dive into all the exciting updates from ANY.RUN this month.
Product Updates
Upgraded Linux Sandbox
At ANY.RUN, we’re always working to improve our services, and this time, we’ve focused on making our Linux sandbox even better. This upgrade brings a seamless, stable experience on par with our Windows environment, making it easier than ever to analyze Linux malware in real time.
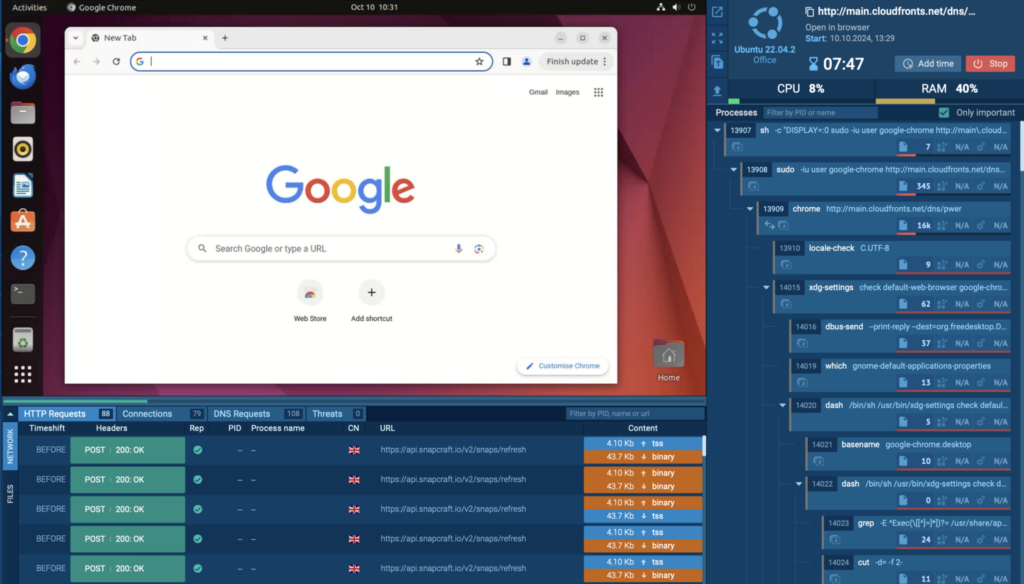
We’ve fine-tuned the Linux sandbox with new features and enhancements to boost both performance and usability. Here’s a quick overview of what’s new and how these updates benefit you:
- File events tracking: Monitor and log all file actions—whether malware is creating, modifying, or deleting files, you’ll see it all in the analysis report.
- Improved process tree: Navigating the process tree is now lag-free, letting you analyze malware behaviors more efficiently.
- Real-time file uploads: You can now upload files during an active session, adding flexibility to your investigation without needing to restart.
See all updates in our blog post.
STIX Reports
In October, we enhanced ANY.RUN’s capabilities by introducing the option to export threat analysis data in the Structured Threat Information eXpression (STIX) format. STIX is a standardized language that facilitates consistent and machine-readable sharing of cyber threat intelligence.
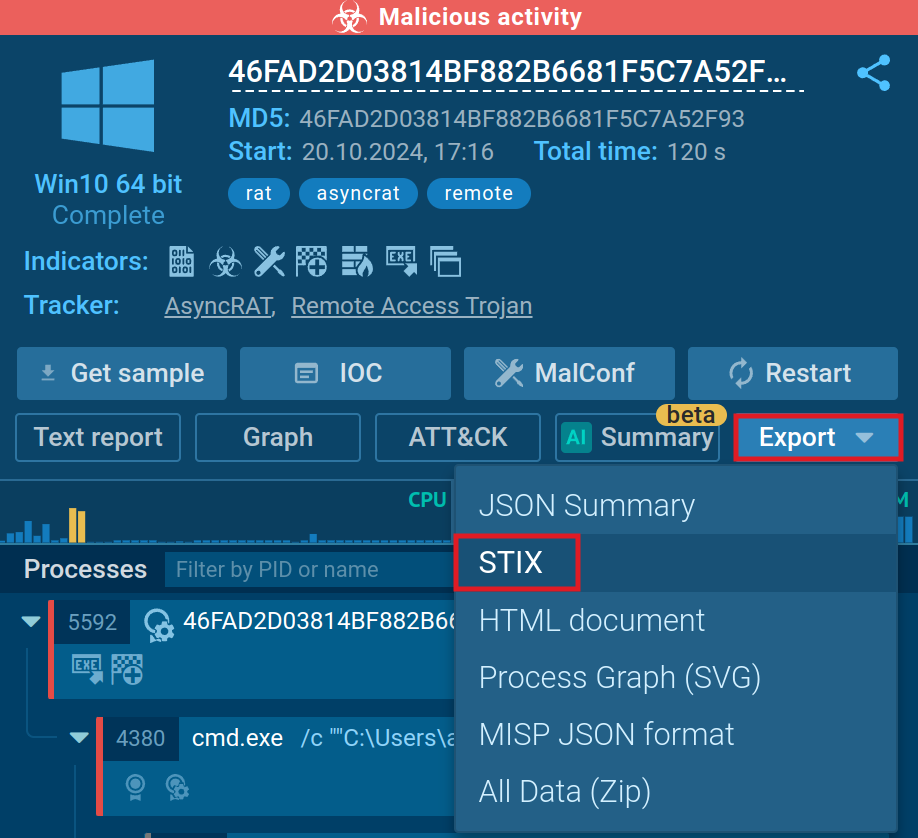
Key features of STIX reports:
- Comprehensive data inclusion: Each STIX report encompasses a wide range of information from your analysis, such as sandbox session links, file hashes, network traffic details, file system modifications, and Tactics, Techniques, and Procedures (TTPs).
- Seamless integration: These reports are compatible with Security Information and Event Management (SIEM) systems and other automated tools, promoting efficient threat detection and response.
- Enhanced collaboration: By utilizing STIX reports, analysts and incident response teams can effortlessly share threat data across various platforms, improving communication and coordination.
Discover all types of reports available in the ANY.RUN sandbox.
TI Lookup Notifications
We have enhanced Threat Intelligence Lookup with Notifications. The new functionality allows users to subscribe to real-time updates on new results related to their specific queries. This includes Indicators of Compromise (IOCs), Indicators of Attack (IOAs), and Indicators of Behavior (IOBs).
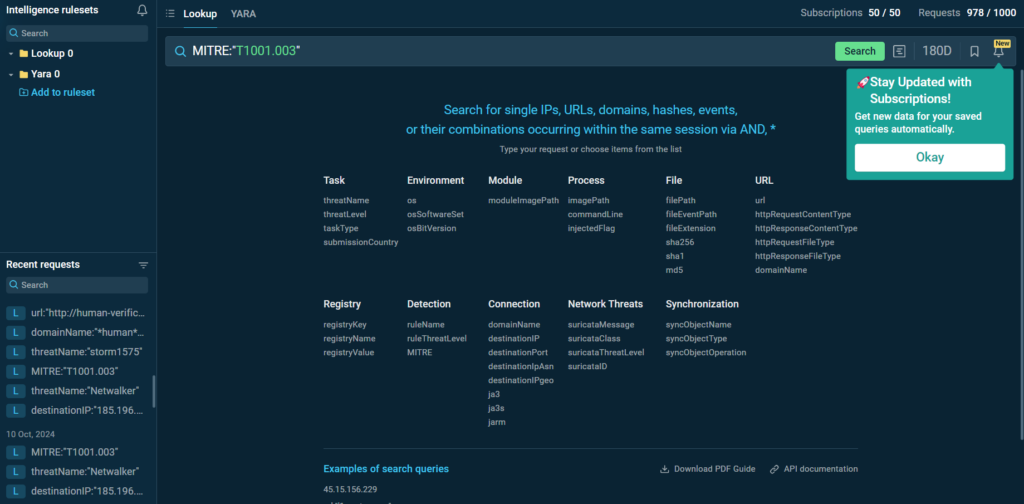
After subscribing to specific queries, the new results will appear in the dashboard, highlighted in green. This will make it easier for you to notice the fresh updates.
Why use Lookup Notifications?
- Automatically monitor and receive updates for your chosen queries, so you never miss critical threat information.
- Tap into threat data sourced from samples uploaded by over 500,000 security pros using ANY.RUN’s Interactive Sandbox, giving you a broad view of global cyber activity.
- Keep track of IOCs, IOAs, and IOBs relevant to your organization, helping you verify potential threats and proactively strengthen your defenses.
- Use real-time insights to refine detection rules, enrich your data, and stay prepared against emerging threats.
See a guide on how to set up notifications in TI Lookup.
Export Session Lists from Team History
We’ve introduced a new feature that allows you to export analysis session lists from your team’s history in a specific JSON format. This export provides a structured list of all sandbox sessions completed by your team.
This feature is designed to help with record-keeping and reporting, making it easier to manage and track your team’s activities over time.
Custom Tags for Analysis Sessions via API
We’ve added the ability to set custom tags for sandbox sessions via the API. Previously, you could assign personalized tags to sessions through the web interface, in addition to the system-generated tags. Now, you can do the same directly through the API, giving you more flexibility in organizing and categorizing your analyses.
Redesigned Threat Intelligence Home Screen with MITRE ATT&CK Matrix
We’ve redesigned our Threat Intelligence home screen to give you a clearer and more intuitive view of the threat landscape.
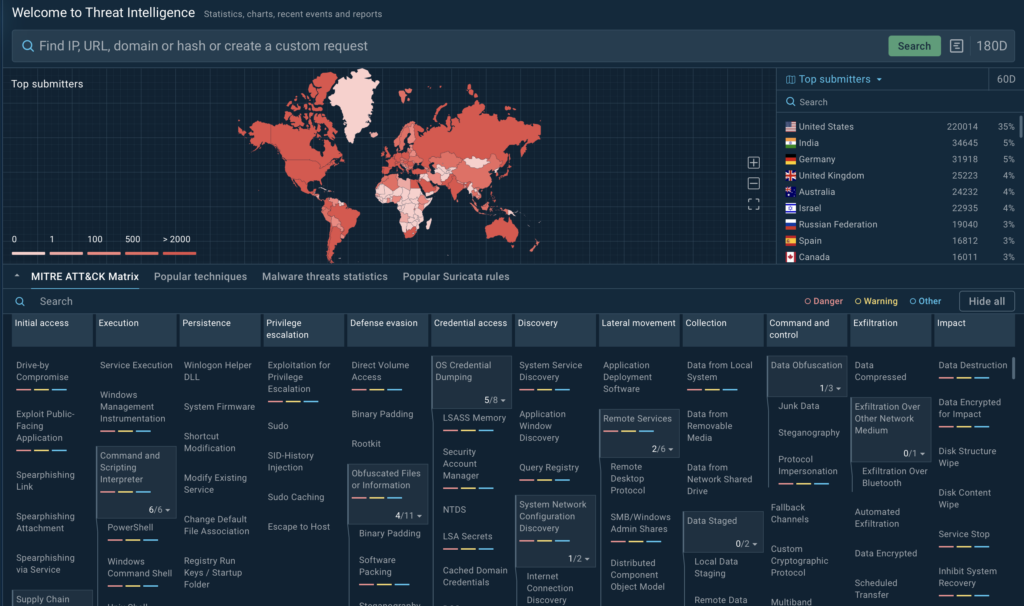
The updated home screen now features a MITRE ATT&CK matrix with refined techniques and tactics, helping you better assess and understand threats.
Threat Coverage Updates
In October, we’ve significantly expanded our detection capabilities with new and updated signatures and YARA rules.
New Signatures
This month, we’ve added 90 new signatures to improve detection and monitoring across various malware types and tools, including:
We added signatures for actions performed via PowerShell:
- Resets Windows Defender malware definitions to the base version
- Changes settings for sending potential threat samples to Microsoft servers
- Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- Changes Controlled Folder Access settings
- Changes settings for real-time protection
- Changes settings for checking scripts for malicious actions
- Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- Changes settings for protection against network attacks (IPS)
- Removes files via Powershell
- Renames file via Powershell
- Hides errors and continues executing the command without stopping
We also implemented detection for Pafish, aka Paranoid Fish, execution with cohost.exe as a parent process, and encrypted JSE scripts.
YARA Rules
This month, we’ve expanded our YARA rule set with several new and improved detections, enhancing the ability to identify and monitor specific threats.
In total, we’ve added 9 new YARA rules, covering various malware families, programming language-based detections, and refinements for better accuracy.
Network Detection Update
In October, we worked to enrich our database with phishing IOCs, leveraging advanced data analysis within TI Lookup. This effort led to the identification of nearly 6,000 domains, each generating a dedicated Suricata rule.
Most of the rules are now live, strengthening our phishing detection capabilities.
We also expanded our catalog of detected phishing kits with the addition of Mamba2FA, enhancing our overall threat coverage.
Our external threat intelligence this month focused on proactively detecting phishing campaigns by groups like Storm, allowing us to better track and respond to their evolving tactics.
Heuristic and Proactive Phishing Detection
This month, our phishing detection capabilities have been enhanced with advanced heuristics and proactive signatures. Here are some examples of recent detections:
- Heuristic signature detection: PHISHING [ANY.RUN] Domain chain identified as Phishing (challengepoint). View analysis session
- Statistical analysis detection: Using statistical processing of previously detected phishing patterns, we flagged PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain (logbook-annul-srt[.]click) as a high-risk domain. View analysis session
- External threat intelligence detection: Through threat intelligence from external sources, we identified PHISHING [ANY.RUN] Suspected AiTM Storm1575 Domain Phishing Infrastructure (eslebrrte[.]com, eslebrrte[.]de), linked to the Storm1575 phishing campaign. View analysis session
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
