
Steam the Webinar on demand HEREAs we look back on the cybersecurity landscape of 2024, 2024-11-1 03:19:51 Author: www.webroot.com(查看原文) 阅读量:10 收藏
Steam the Webinar on demand HERE
As we look back on the cybersecurity landscape of 2024, it’s clear that the world of digital threats continues to evolve at an alarming pace in parallel with AI. This year has seen ransomware groups adapt and innovate, pushing the boundaries of their malicious capabilities and evasiveness from law enforcement. In our annual “Nastiest Malware” report, now in its sixth year, we’ve observed a steady increase in both the number and sophistication of malware attacks. The ransomware sector, in particular, has witnessed the emergence of “business models,” with ransomware-as-a-service (RaaS) dominating the scene. Elite ransomware authors have concluded that profit sharing and risk mitigation are key contributors to their consistent success and evasion of authorities.
The saga of LockBit in 2024 exemplifies the resilience and adaptability of these cybercriminal groups. Despite a major law enforcement operation in February, dubbed “Operation Cronos,” which saw the FBI and international partners seize LockBit’s infrastructure and obtain over 7,000 decryption keys, the group managed to resurface within days. This cat-and-mouse game between LockBit and law enforcement agencies has continued throughout the year, with the group’s leader even taunting the FBI, claiming that their efforts only make LockBit stronger. The LockBit story underscores a crucial point: while law enforcement operations can disrupt cybercriminal activities, they often fall short of delivering a knockout blow. These groups have become adept at rebuilding their infrastructure, rebranding when necessary, and continuing their operations with minimal downtime.
As we detail our analysis of the six most notorious ransomware and malware groups that have dominated headlines in 2024, it’s important to note that the threat landscape extends beyond just these actors. The rise of AI-driven phishing and social engineering, increased targeting of critical infrastructure, and the emergence of more sophisticated fileless malware are all trends that have shaped the cybersecurity battlefield this year.
In this report, we’ll explore how these groups have evolved, their most significant attacks, and the broader implications for cybersecurity. We’ll also provide updated survival tips for both businesses and individual users, reflecting the ever-changing nature of these threats.
Ransomware
Over the past decade, ransomware has established itself as the pinnacle of cybercriminal exploits. It is the most successful and lucrative avenue for monetizing a breach of a victim. Every year we see more and more data stolen and higher ransom demands dominating headlines. Each ransomware group on our Nastiest Malware list utilizes the double-extortion method where the data stolen is leveraged for leak potential on dark web leak sites. The impending damage to brand and reputation that comes with the public disclosure of a breach are massive threats to companies of any size. Not to mention the impending regulatory fines that come with the breach. This strategy has shown it’s resilience over the past few years since it became mainstream and it seems to be as robust as ever. Let’s take a look at what the payment numbers look like so far in 2024.
Source: Coveware
We’ve seen a drop-off from the highs last year – fueled by Cl0p ransomware group making over $100 Million in a few months in late 2023. But when we zoom out you can see that it will be going up over time. This time next year we anticipate the amounts to be higher than what they are now. Some of this will be fueled by inflation, some will be an increase in effectiveness in tactics, and some by the anticipated 2025 “bull run” price spike in crypto – the only payment method these criminals accept.
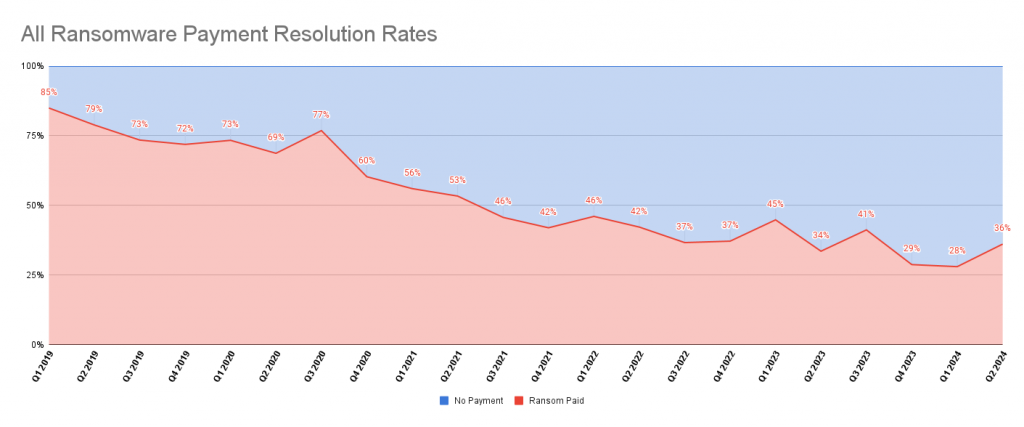
Looking at the payment resolution rates – meaning the percentage of people that end up paying the ransom, we can see a slight increase during this year. Zooming out the trend does indicate an overall decline which is good news and reflects that the industry is taking serious precautions in their security posture. We expect that this slight increase is only temporary and will continue the trend of decreasing for next year.
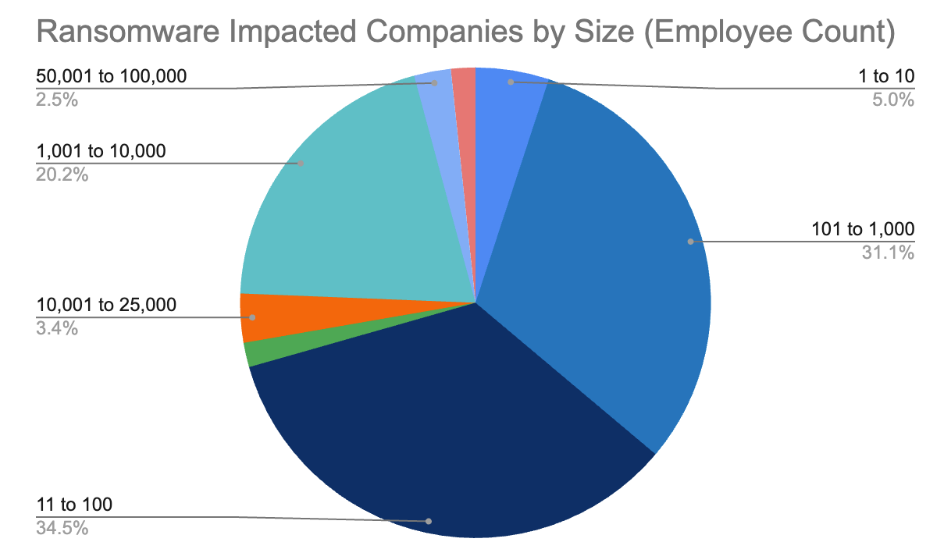
One nasty change this year is the increase of ransomware attacks on smaller sized businesses. The market share of ransomware attacks on business with under 100 employees is now almost 40%. While the media headlines of record breaking ransoms against fortune 500 companies will always take center stage, the small to mid market has always been the bread and butter for cybercriminals. The amount of effort and return on investment of time is too good for criminals not to be attracted to these easier and weaker targets. Now let’s take a look at this year’s Nastiest Malware.
LockBit: The Resilient Threat

One of the most notorious ransomware groups, LockBit, faced significant challenges and disruptions in 2024 due to coordinated international law enforcement efforts. The year began with “Operation Cronos,” a major strike against LockBit’s infrastructure in February. Led by the UK’s National Crime Agency (NCA) and involving agencies from multiple countries, including the FBI, this operation resulted in the seizure of LockBit’s leak sites and the exposure of information about nearly 200 affiliates. A pivotal moment came when the FBI obtained over 7,000 decryption keys, allowing victims to unlock their encrypted data for free. This dealt a severe blow to LockBit’s operations and credibility – remember that most of the success and money is from the affiliates that choose thier ransomware payload over another’s group so credibility and trust are paramount in this criminals scene.
Despite these setbacks, LockBit attempted to maintain its operations, quickly adapting by changing encryption methods and shifting its leak site strategy. However, law enforcement continued to apply pressure throughout the year. In May, authorities revealed the identity of LockBit’s alleged mastermind, Dmitry Yuryevich Khoroshev, and offered a $10 Million reward for information leading to his arrest. The culmination of these efforts came in October when law enforcement agencies announced additional arrests and disruptions. Four individuals connected to LockBit were arrested, including a major developer and two affiliates. Notably, Aleksandr Ryzhenkov, linked to both LockBit and the infamous Evil Corp group, was unmasked and sanctioned. These actions, part of the ongoing Operation Cronos, significantly impacted LockBit’s operations, leading to a noticeable decrease in their attack frequency and causing distrust within the cybercriminal community.
Despite LockBit’s attempts to maintain its fearsome reputation, including false claims of attacks, the group’s activities were impacted throughout 2024, marking a significant victory for global cybersecurity efforts. However, LockBit is still a major player in the RaaS scene and the leader and his affiliates are still making millions in ransoms. LockBit has proven its resilience in the face of law enforcement efforts, presenting the group’s adaptability and persistence. The leader has boasted that he loves the FBI and that they only make his group stronger, and he wants to hit one million businesses before retirement. This is a stark contrast from most ransomware groups when hit by law enforcement as they will quickly retire the brand and repivot to another. This RaaS has been on the Nastiest Malware for over three years maintaining its status as a top contender in the Ransomware scene in 2024.
Akira: The Healthcare Menace
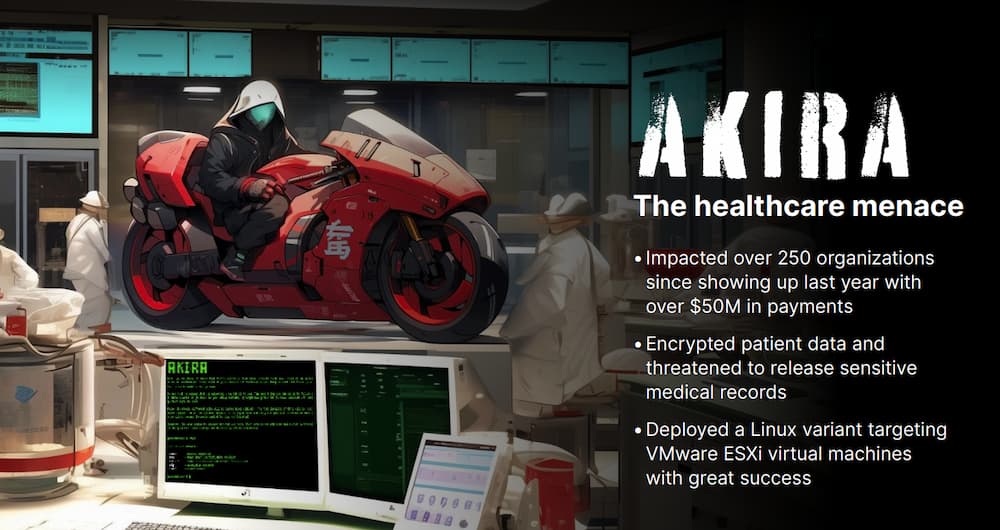
The Akira ransomware group was first observed in March 2023 and immediately became one of the most formidable threats in the threat landscape. By January 2024, the group had impacted over 250 organizations and claimed approximately $42 million in ransomware proceeds. Akira’s rapid rise to the top was marked by its versatility and constant evolution of tactics. In 2024, Akira expanded its capabilities significantly. Initially focused on Windows systems, the group deployed a Linux variant targeting VMware ESXi virtual machines in April. Throughout the year, Akira demonstrated a pattern of swift adaptation to new vulnerabilities. They actively exploited several critical vulnerabilities, including SonicWall SonicOS, Cisco Adaptive Security Appliance (ASA), and FortiClientEMS software. These exploits allowed Akira to gain initial access, escalate privileges, and move laterally within compromised networks.
A notable shift in Akira’s tactics occurred in early 2024 when they appeared to sideline encryption tactics, focusing primarily on data exfiltration. However, by September 2024, there were indications of a potential return to previous tactics using Windows and Linux payloads written in C++. This adaptability was further evidenced in a June 2024 attack on a Latin American airline, where Akira operators exploited vulnerable services to deploy ransomware and exfiltrate data.
Akira’s victims spanned a wide range of sectors, with a particular focus on manufacturing, professional services, healthcare, and critical infrastructure. The group’s success was attributed to its constant evolution, sophisticated attack methods, and the employment of double-extortion tactics. As of 2024, Akira had solidified its position as one of the most prevalent and dangerous ransomware operations in the cybersecurity threat landscape.
RansomHub: The High-Profile Attacker

RansomHub emerged as a formidable new player in the ransomware landscape in February 2024, quickly establishing itself as one of the most prolific and dangerous ransomware groups. Operating on a RaaS model, RansomHub attracted high-profile affiliates from other prominent groups like BlackCat/ALPHV following their FBI takedown in December 2023. This is likely due to its attractive payment structure where affiliates receive up to 90% of the ransom – compared to around 30-50% with other groups.
By August 2024, RansomHub had breached at least 210 victims across various critical U.S. infrastructure sectors, including healthcare, government services, financial services, and critical manufacturing. Notable attacks included breaches of Planned Parenthood, the Rite Aid drugstore chain, Christie’s auction house, and Frontier Communications, with the latter resulting in the exposure of personal information of over 750,000 customers. RansomHub’s tactics evolved throughout the year, employing sophisticated methods such as exploiting various software vulnerabilities, using intermittent encryption to speed up attacks, and leveraging double extortion techniques. The group’s data leak site became a significant threat, with stolen data being published for 3-90 days if ransom demands were not met.
The attack on Planned Parenthood not only demonstrated RansomHub’s capability to breach highly sensitive networks but also highlighted their willingness to target organizations with high reputational risks. This sparked widespread concern and discussions on cybersecurity measures within nonprofit organizations. By October 2024, RansomHub had overtaken LockBit as the most prolific ransomware group in terms of claimed successful attacks, solidifying its position as a major threat in the cybersecurity landscape.
Dark Angels: The Whaling Experts

Dark Angels emerged as one of the most formidable ransomware threats in 2024, gaining notoriety for their highly targeted “big game hunting” approach and record-breaking ransom demands. The group, which has been active since 2022, made headlines in early 2024 when they reportedly received a staggering $75 million ransom payment from a Fortune 50 company. This payment would be nearly double the previous record of $40 million paid by CNA Financial in 2021.The group’s modus operandi involves targeting a small number of high-value organizations, often exfiltrating massive amounts of data (typically 10-100 terabytes for large businesses) before considering encryption. This strategy allows Dark Angels to maintain a low profile while maximizing their profits.
In 2024, they continued to evolve their tactics, switching from a Babuk-ESXi-based ransomware to a variant of Ragnar Locker. Notable attacks attributed to Dark Angels in 2024 included a breach of a high-profile media company, where they stole proprietary information and engaged in lengthy negotiations before the ransom was paid. The group’s data leak site, named “Dunghill Leak,” is used to pressure victims into paying, though the group often prefers to avoid public attention. Dark Angels’ success in 2024, particularly the record-breaking ransom payment, has raised concerns that their tactics may be emulated by other cybercriminal groups, potentially leading to an increase in highly targeted, high-value ransomware attacks across various sectors.
RedLine: The Credential Thief

Not all of our Nastiest Malware are ransomware groups and RedLine Stealer has become one of the most prominent threats in 2024, particularly due to its capability to steal credentials and sensitive data across a wide array of sectors. Throughout 2024, RedLine demonstrated its effectiveness by stealing over 170 million passwords in just a six-month period, highlighting its massive impact. The malware’s capabilities expanded to include stealing not only passwords but also credit card details, cryptocurrency wallets, and browser data. Its adaptability and frequent updates allowed it to evade many security measures, making it a persistent threat across various sectors.
RedLine’s distribution methods remained diverse, with phishing emails and malicious websites being the primary vectors. The malware’s operators continued to refine their tactics, often disguising RedLine as legitimate software updates or enticing downloads. This approach allowed them to bypass traditional security measures and infect a large number of systems. The impact of RedLine extended beyond individual users to affect major corporations and critical infrastructure. Several high-profile breaches attributed to RedLine in 2024 resulted in significant financial losses and reputational damage for the affected organizations.
Breaking news!
In late October 2024 – RedLine suffered a takedown from a coordinated international law enforcement operation dubbed “Operation Magnus.” Led by the Dutch National Police and supported by agencies including the FBI, UK’s National Crime Agency, the operation successfully disrupted RedLine’s infrastructure and operations. The authorities gained full access to RedLine’s servers, obtaining crucial data including usernames, passwords, IP addresses, and even the source code of the malware. This breakthrough allowed law enforcement to retrieve a database of thousands of RedLine clients, paving the way for further investigations and potential legal actions against cybercriminals who used the malware. The U.S. Department of Justice charged Maxim Rudometov, a Russian national, as the suspected developer and leader of the RedLine malware operation. If convicted, Rudometov faces up to 35 years in prison on charges including access device fraud, conspiracy to commit computer intrusion, and money laundering.
Only time will tell if this seizure of assets is enough to shutdown the operations of RedLine and prevent them from bouncing back like we’ve seen time and time again from other resilient groups on this list.
Play Ransomware: The Versatile Threat

Play ransomware continued to be a significant threat in the cybersecurity landscape throughout 2024. The group, which first appeared in 2022, maintained its position as one of the most active ransomware operations, consistently ranking among the top threat actors. In 2024 a notable shift occurred when the group transitioned from its previous double-extortion tactics to specifically targeting ESXi environments. This change in focus allowed Play to exploit vulnerabilities in virtual machine infrastructures, increasing the impact of their attacks.
A significant attack attributed to Play Ransomware targeted a major utility provider, resulting in widespread service disruptions and raising concerns about critical infrastructure vulnerabilities. The attack began with the exploitation of unpatched FortiOS vulnerabilities in the company’s VPN infrastructure, allowing initial access to the network. From there, the attackers leveraged exposed RDP services to move laterally within the network, eventually gaining the access needed to deploy their ransomware payload.
The group’s use of intermittent encryption continued to be a defining characteristic, allowing them to evade many endpoint security solutions while still rendering files inaccessible to victims. Play’s attacks were particularly damaging in the IT services sector, suggesting a strategic focus on organizations that could lead to supply chain impacts.

AI-Driven Phishing and Social Engineering:
- The use of AI and machine learning in crafting phishing emails has made these lures more convincing and harder to detect. Cybercriminals are leveraging AI to personalize attacks, increasing their success rates
Targeting of Critical Infrastructure:
- There has been a noticeable increase in attacks targeting critical infrastructure, including utilities and healthcare sectors, raising concerns about national security and public safety
Fileless Malware:
- Fileless attacks aren’t new, and neither is bypassing security protections but there has been an increase in harder to detect kill chains, more sophisticated attacks, more complex persistence, that are more effective at bypassing security than ever.
New Malware Language:
- Malware written in Golang continues to trend in both scale and complexity

Businesses:
- Lock down Remote Desktop Protocols (RDP) – this infiltration tactic has been around for a while, but it’s still one of the top infection vectors!
- Enhance Employee Training: Go beyond basic awareness. Implement regular, interactive cybersecurity simulations and scenario-based training.
- PATCH OR DIE!
- Implement a Multi-layered security and defense in depth posture.
- Adopt a Comprehensive Backup Strategy: Implement the 3-2-1 backup rule with immutable backups to protect against ransomware attacks.
- Develop and Test Incident Response Plans: Create, regularly update, and practice cybersecurity incident response plans.
Individual Users:
- Use Password Managers: Employ a reputable password manager to create and store strong, unique passwords for all accounts – consider passphrases.
- Enable Multi-Factor Authentication (MFA): Activate MFA on all accounts that offer it, preferably using authenticator apps or hardware keys.
- Keep Software Updated: Enable automatic updates for your operating system, applications, and security software.
- Be Cautious with Smart Devices: Secure your IoT devices by changing default passwords and keeping firmware updated.
- Practice Safe Social Media: Be cautious about the personal information you share on social media platforms.
- Use Virtual Private Networks (VPNs): Employ a reliable VPN service, especially when using public Wi-Fi networks.
Download the infographic HERE
![]()
About the Author
Tyler Moffitt
Sr. Security Analyst
Tyler Moffitt is a Sr. Security Analyst who stays deeply immersed within the world of malware and antimalware. He is focused on improving the customer experience through his work directly with malware samples, creating antimalware intelligence, writing blogs, and testing in-house tools.
如有侵权请联系:admin#unsafe.sh
