read file error: read notes: is a directory 2024-10-29 18:0:31 Author: securelist.com(查看原文) 阅读量:15 收藏
Attackers are increasingly distributing malware through a rather unusual method: a fake CAPTCHA as the initial infection vector. Researchers from various companies reported this campaign in August and September. The attackers, primarily targeting gamers, initially delivered the Lumma stealer to victims through websites hosting cracked games.
Our recent research into the adware landscape revealed that this malicious CAPTCHA is spreading through a variety of online resources that have nothing to do with games: adult sites, file-sharing services, betting platforms, anime resources, and web apps monetizing through traffic. This indicates an expansion of the distribution network to reach a broader victim pool. Moreover, we discovered that the CAPTCHA delivers not only Lumma but also the Amadey Trojan.
To avoid falling for the attackers’ tricks, it’s important to understand how they and their distribution network operate. The ad network pushing pages with the malicious CAPTCHA also includes legitimate, non-malicious offers. It functions as follows: clicking anywhere on a page using the ad module redirects the user to other resources. Most redirects lead to websites promoting security software, ad blockers, and the like – standard practice for adware. However, in some cases, the victim lands on a page with the malicious CAPTCHA.
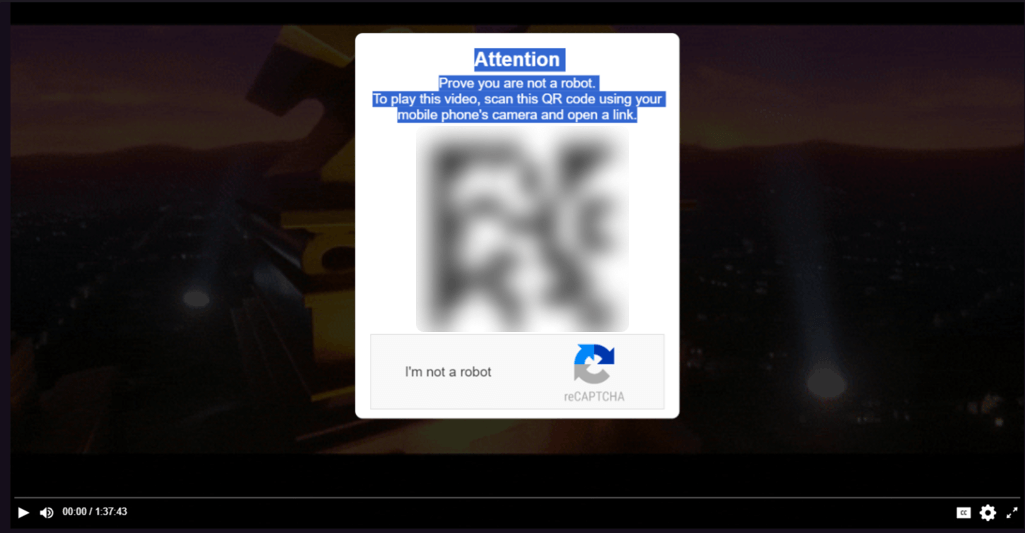
Unlike genuine CAPTCHAs designed to protect websites from bots, this imitation serves to promote shady resources. As with the previous stage, the victim doesn’t always encounter malware. For example, the CAPTCHA on one of the pages prompts the visitor to scan a QR code leading to a betting site:
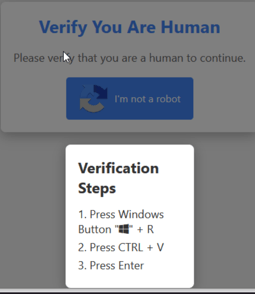
The Trojans are distributed through CAPTCHAs with instructions. Clicking the “I’m not a robot” button copies the line powershell.exe -eC bQBzAGgAdABhA<…>MAIgA= to the clipboard and displays so-called “verification steps”:
- Press Win + R (this opens the Run dialog box);
- Press CTRL + V (this pastes the line from the clipboard into the text field);
- Press Enter (this executes the code).
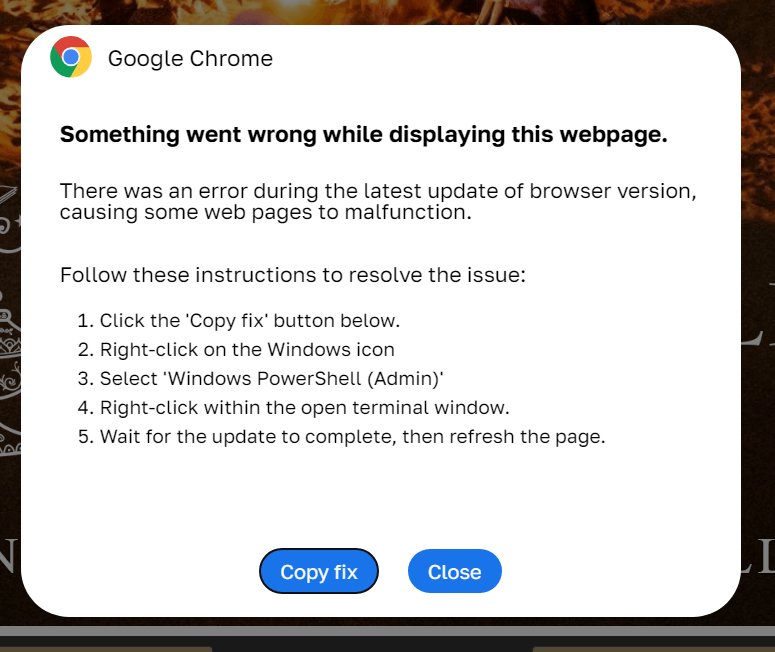
We’ve also come across similar instructions in formats other than CAPTCHAs. For instance, the screenshot below shows an error message for a failed page load, styled like a Chrome message. The attackers attribute the problem to a “browser update error” and instruct the user to click the “Copy fix” button. Although the page design is different, the infection scenario is identical to the CAPTCHA scheme.
The line from the clipboard contains a Base64-encoded PowerShell command that accesses the URL specified there and executes the page’s content. Inside this content is an obfuscated PowerShell script that ultimately downloads the malicious payload.
Payload: Lumma stealer
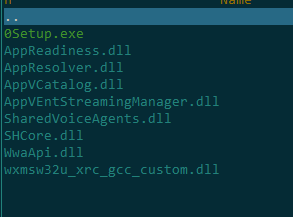
Initially, the malicious PowerShell script downloaded and executed an archive with the Lumma stealer. In the screenshot below, the stealer file is named 0Setup.exe:
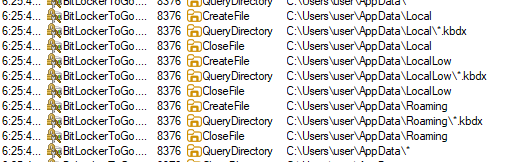
After launching, 0Setup.exe runs the legitimate BitLockerToGo.exe utility, normally responsible for encrypting and viewing the contents of removable drives using BitLocker. This utility allows viewing, copying, and writing files, as well as modifying registry branches – functionality that the stealer exploits.
Armed with BitLocker To Go, the attackers manipulate the registry, primarily to create the branches and keys that the Trojan needs to operate:
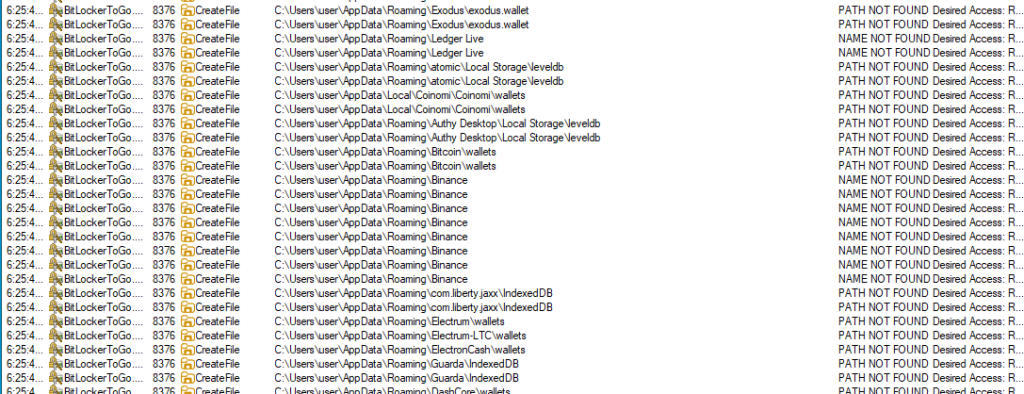
That done, Lumma, again using the utility, searches the victim’s device for files associated with various cryptocurrency wallets and steals them:
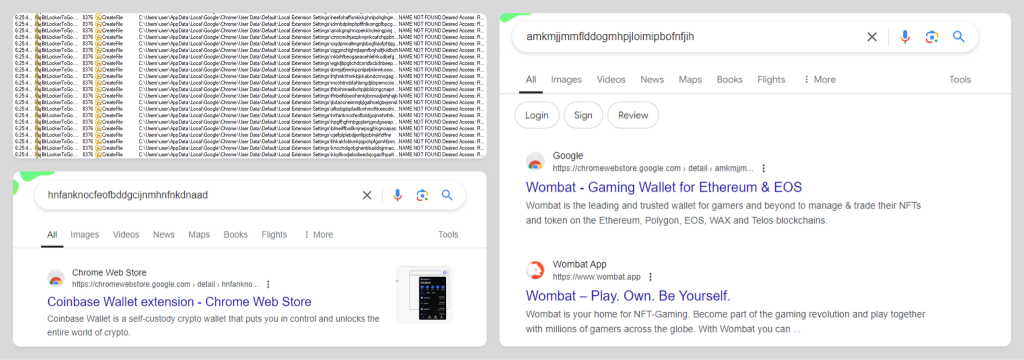
Then, the attackers view browser extensions related to wallets and cryptocurrencies and steal data from them:
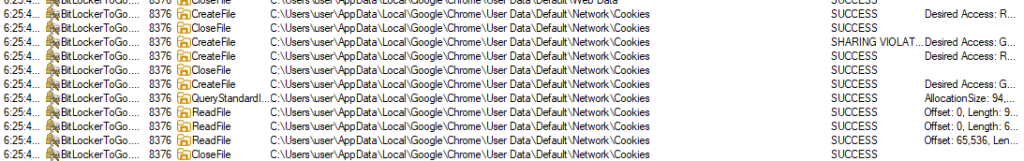
Following this, the Trojan attempts to steal cookies and other credentials stored in various browsers:
Finally, the malware searches for password manager archives to steal their contents as well:
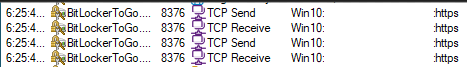
Throughout the data collection process, the Trojan tries to use the same BitLocker To Go to send the stolen data to the attackers’ server:
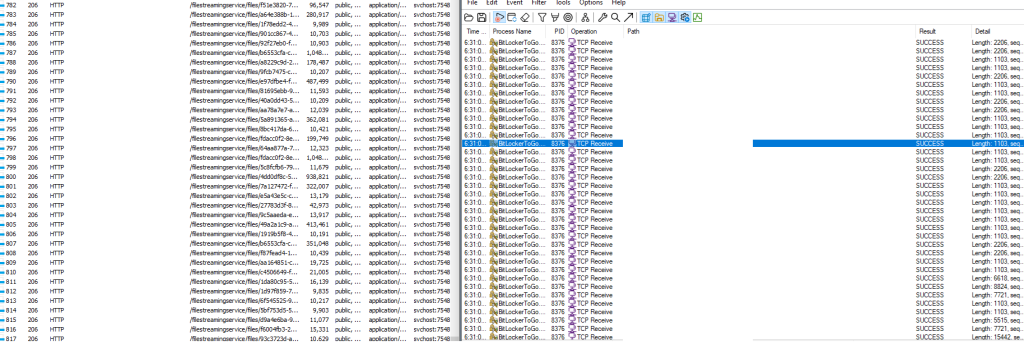
Once the malware has found and exfiltrated all valuable data, it starts visiting the pages of various online stores. The purpose here is likely to generate further revenue for its operators by boosting views of these websites, similar to adware:
Payload: Amadey Trojan
We recently discovered that the same campaign is now spreading the Amadey Trojan as well. Known since 2018, Amadey has been the subject of numerous security reports. In brief, the Trojan downloads several modules for stealing credentials from popular browsers and various Virtual Network Computing (VNC) systems. It also detects crypto wallet addresses in the clipboard and substitutes them with those controlled by the attackers. One of the modules can also take screenshots. In some scenarios, Amadey downloads the Remcos remote access tool to the victim’s device, giving the attackers full access to it.
Statistics
From September 22 to October 14, 2024, over 140,000 users encountered ad scripts. Kaspersky’s telemetry data shows that out of these 140,000, over 20,000 users were redirected to infected sites, where some of them saw a fake update notification or a fake CAPTCHA. Users in Brazil, Spain, Italy, and Russia were most frequently affected.
Conclusion
Cybercriminals often infiltrate ad networks that are open to all comers. They purchase advertising slots that redirect users to malicious resources, employing various tricks to achieve infections. The above campaign is of interest because (a) it leverages trust in CAPTCHA to get users to perform unsafe actions, and (b) one of the stealers makes use of the legitimate BitLocker To Go utility. The malware works to enrich its operators both by stealing victims’ credentials and crypto wallets, and by exploiting online stores that pay money for traffic to their websites.
Indicators of compromise
e3274bc41f121b918ebb66e2f0cbfe29
525abe8da7ca32f163d93268c509a4c5
ee2ff2c8f49ca29fe18e8d18b76d4108
824581f9f267165b7561388925f69d3av
如有侵权请联系:admin#unsafe.sh