2024-10-19 22:7:10 Author: securityaffairs.com(查看原文) 阅读量:26 收藏
North Korea-linked APT37 exploited IE zero-day in a recent attack

North Korea-linked group APT37 exploited an Internet Explorer zero-day vulnerability in a supply chain attack.
A North Korea-linked threat actor, tracked as APT37 (also known as RedEyes, TA-RedAnt, Reaper, ScarCruft, Group123), exploited a recent Internet Explorer zero-day vulnerability, tracked as CVE-2024-38178 (CVSS score 7.5), in a supply chain attack.
Threat intelligence firm AhnLab and South Korea’s National Cyber Security Center (NCSC) linked the attack to the North Korean APT.
The vulnerability is a scripting engine memory corruption issue that could lead to arbitrary code execution.
“This attack requires an authenticated client to click a link in order for an unauthenticated attacker to initiate remote code execution.” reads the advisory published by Microsoft, which addressed the flaw in August. “Successful exploitation of this vulnerability requires an attacker to first prepare the target so that it uses Edge in Internet Explorer Mode.”
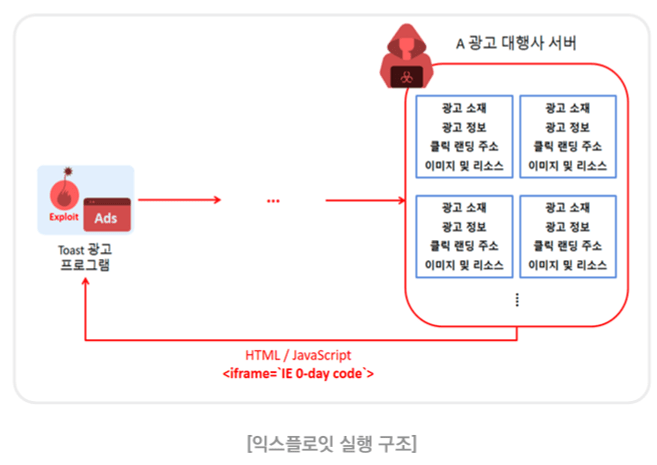
APT37 compromised the online advertising agency behind the Toast ad program to carry out a supply chain attack.
The attackers exploited the zero-day Internet Explorer vulnerability in the toast ad program, which used an outdated IE-based WebView for initial access in a supply chain attack.
The researchers pointed out that despite IE’s end of support in June 2022, the vulnerability still impacted certain Windows applications.
The threat actors compromised a Korean online ad agency server, injecting vulnerability code into ad content scripts. This led to a zero-click attack, requiring no user interaction, as the ad program automatically downloaded and rendered the malicious content.
“This operation exploited a zero-day vulnerability in IE to utilize a specific toast ad program that is installed alongside various free software. [Toast is] A type of popup notification that appears at the bottom (usually right bottom) of the desktop screen.” reads the advisory published by AhnLab.
“Many toast ad programs use a feature called WebView to render web content for displaying ads. However, WebView operates based on a browser. Therefore, if the program creator used IE-based WebView to write the code, IE vulnerabilities could also be exploited in the program. As a result, TA-RedAnt exploited the toast ad program that were using the vulnerable IE browser engine (jscript9.dll), which is no longer supported, as an initial access vector. Microsoft ended its support for IE in June 2022. However, attacks that target some Windows applications that still use IE are continuously being discovered, so organizations and users need to be extra cautious and update their systems with the latest security patches.”
The root cause of the vulnerability is the erroneous treatment of a type of data during the optimization process of IE’s JavaScript engine (jscript9.dll), allowing type confusion to occur. APT37 exploited this flaw to trick victims into downloading malware on their desktops with the toast ad program installed. Once the systems are infected, attackers can perform multiple malicious activities such as executing remote commands.
The report published by AhnLab includes details on the attack and indicators of compromise (IoCs).
APT37 has been active since at least 2012, it made the headlines in early February 2028, when researchers revealed that the APT group leveraged a zero-day vulnerability in Adobe Flash Player to deliver malware to South Korean users.
Cyber attacks conducted by the APT37 group mainly targeted government, defense, military, and media organizations in South Korea.
In December 2022, the APT37 group actively exploited another Internet Explorer zero-day vulnerability, tracked as CVE-2022-41128, in attacks aimed at South Korean users. Google Threat Analysis Group researchers discovered the zero-day vulnerability in late October 2022, it was exploited by APT37 using specially crafted documents.
In February 2018, FireEye linked the APT37 group to the North Korean government based on the following clues:
- the use of a North Korean IP;
- malware compilation timestamps consistent with a developer operating in the North Korea time
zone (UTC +8:30) and follows what is believed to be a typical North Korean workday; - objectives that align with Pyongyang’s interests(i.e. organizations and individuals involved in Korean
Peninsula reunification efforts);
Researchers from FireEye revealed that the nation-state actor also targeted entities in Japan, Vietnam, and even the Middle East in 2017. The hackers targeted organizations in the chemicals, manufacturing, electronics, aerospace, healthcare, and automotive sectors.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, APT)
如有侵权请联系:admin#unsafe.sh
