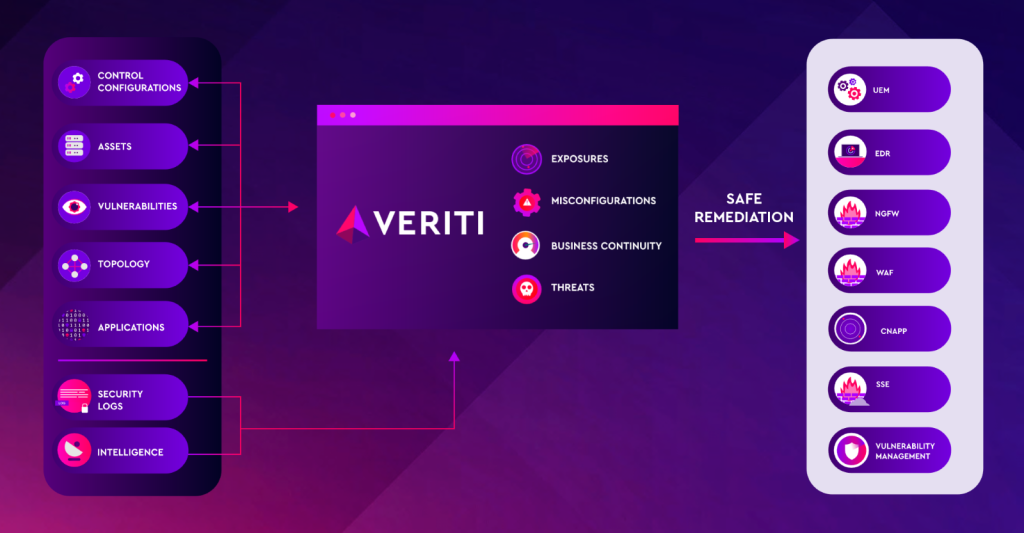
Managing multiple tools and platforms can create blind spots that leave your organization vulnerable to threats. But with Veriti’s 50+ integrations, you can eliminate these gaps and achieve total security control. By seamlessly connecting every aspect of your security stack—from network security to endpoint protection—Veriti provides you with real-time insights and safe remediation across your entire infrastructure. No guesswork, no chaos—just streamlined, efficient protection.
Why 50+ Integrations Matter: Complete Context, Complete Coverage
Veriti’s 50+ integrations aren’t just a number—they’re the key to achieving comprehensive, context-driven security. In contrast to other vendors that provide a prioritized list of vulnerabilities, Veriti’s deep integration with the entire security stack means that we don’t just tell you what’s wrong—we give you the most accurate, actionable remediation paths based on real-time data from all your security tools.
But why is this so important? Here’s the reality: if your vulnerability list doesn’t take the whole security stack into consideration, how accurate could it be? The gaps that appear when tools don’t talk to each other can leave you exposed to threats you didn’t even realize were there. Veriti changes the game by integrating everything, ensuring that you have the full context you need to make informed decisions and take fast, effective action.

With so many tools in play, the security landscape often becomes chaotic, requiring security teams to juggle multiple platforms, each with its own set of data and alerts. This fragmentation slows response times and makes it difficult to get a clear picture of your organization’s security posture. Veriti’s vast integrations simplify your security stack by connecting all of your tools into one cohesive solution, giving you a bird’s eye view of threats and real-time active remediation options.
When every second counts, having all of your tools working in sync is critical. Veriti doesn’t just identify vulnerabilities—it empowers you to remediate them instantly. Our platform integrates 50+ security solutions into a single, streamlined system, allowing you to execute safe remediation paths across all levels of your security stack—network, endpoint, operating system, and more.
Unlike other platforms that require you to wade through a list of vulnerabilities or recommendations, Veriti provides immediate, actionable remediation options. Once a safe remediation path is identified, you can populate it across your entire security environment—at the network level, endpoint level, OS level, etc., with just a few clicks. And the best part? It’s all agentless, meaning there’s no need to deploy additional software or agents on your systems.
One of the standout features of Veriti’s platform is its agentless architecture. This means you can deploy and execute remediation actions without having to install agents on individual endpoints or systems. Many security tools rely on agents to carry out tasks, which can be a drain on resources and cause delays. Veriti bypasses this problem by working directly with your existing infrastructure, allowing for faster remediation without the complexity or overhead of agents.
Here’s what this means for you:
- Faster Remediation: With no agents to deploy, remediation actions happen instantly across all tools and levels, minimizing response times.
- No Resource Drain: Agentless means fewer performance impacts on your systems and less overhead for your security team to manage.
- Seamless Integration: Veriti integrates directly into your existing infrastructure, working with your current tools to ensure that remediation happens in real-time, with no need for manual intervention.
Eliminate Blind Spots and Take Control
The key advantage of Veriti’s 50+ integrations is that they eliminate blind spots in your security posture. Every tool in your stack, whether it’s focused on endpoint protection, network security, or vulnerability management feeds into Veriti’s platform, providing you with a complete, real-time view of your organization’s vulnerabilities and risks. This level of integration ensures that no threat goes unnoticed, and no vulnerability is left unaddressed.
By providing full context, Veriti empowers security teams to make smarter decisions. Instead of reacting to isolated alerts from individual tools, you can see how different threats and vulnerabilities interact across your entire infrastructure. This holistic view allows you to prioritize and address the most critical issues without the confusion that often comes with managing multiple platforms.
In today’s fast-paced business environment, security can’t afford to be slow or fragmented. When you have all your tools connected, you can fix anything. Veriti doesn’t just identify problems—it gives you the power to solve them, fast. By automating and streamlining the remediation process, Veriti ensures that you stay ahead of threats and keep your business running smoothly.

Get your security controls assessment now
Recommended Articles
Subscribe to our BLOG
Get the latest security insights, news and articles delivered to your inbox.
*** This is a Security Bloggers Network syndicated blog from VERITI authored by Yair Herling. Read the original post at: https://veriti.ai/blog/security-posture/50-integrations-with-veriti/