2024-10-10 22:40:25 Author: securityaffairs.com(查看原文) 阅读量:3 收藏
E-skimming campaign uses Unicode obfuscation to hide the Mongolian Skimmer

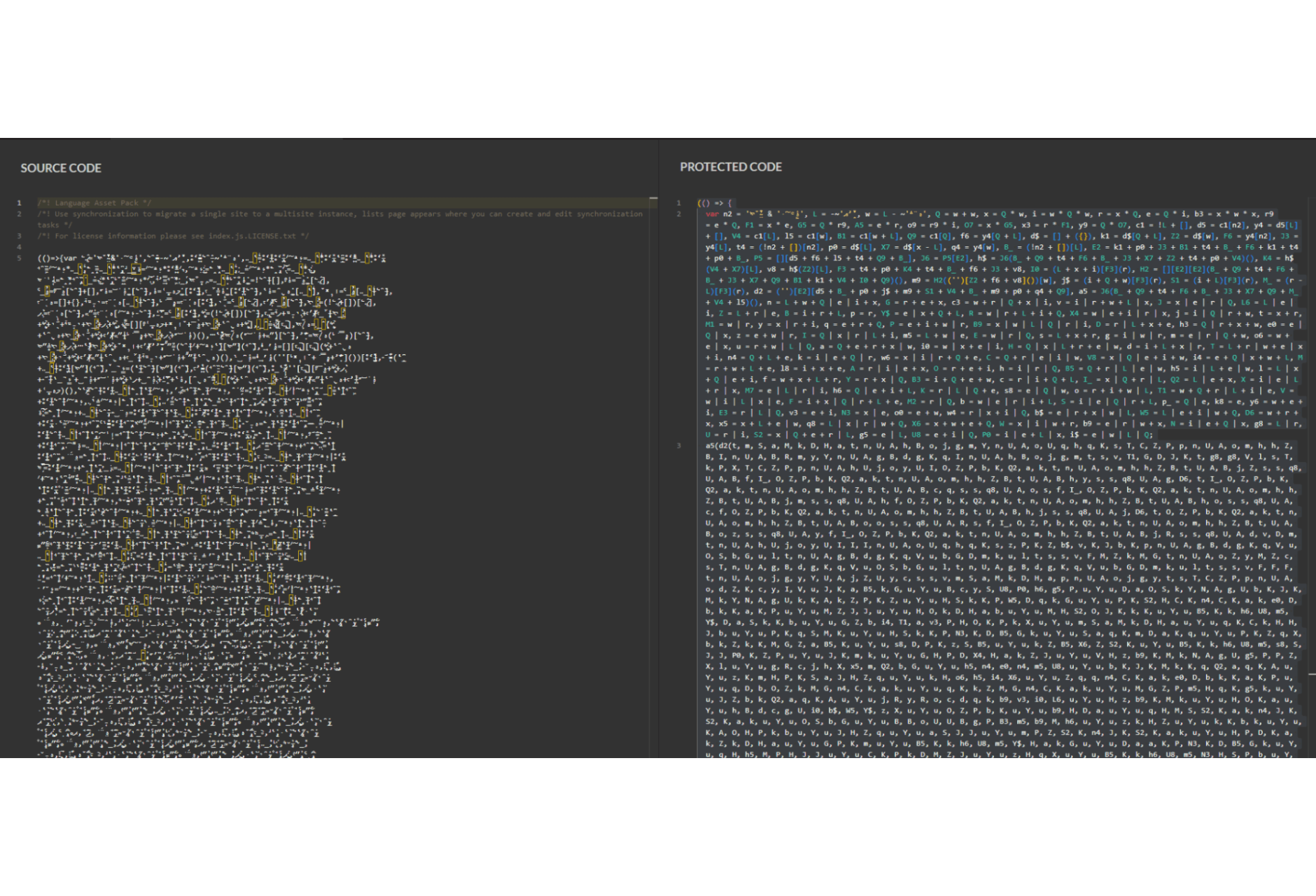
Jscrambler researchers found a skimming campaign using unique JavaScript obfuscation with accented characters to hide a skimmer named Mongolian Skimmer.
Jscrambler researchers uncovered a skimming campaign using unique JavaScript obfuscation with accented characters to hide a skimmer dubbed ‘Mongolian Skimmer.’
The attackers used unusual Unicode characters for variables and function names.
The skimmer was named “Mongolian Skimmer” after researchers found it used the Unicode character “Mongolian Letter OE” as an identifier in the code.
Jscrambler researchers analyzed a malware sample employed in this skimming campaign that was shared from Sansec threat intel.
The use of accented Unicode characters is unusual and makes the code difficult for humans to read and analyze.
“But the minute Jscrambler researchers started looking at the obfuscation, they realized immediately that it wasn’t a new fancy technique — it was simply leveraging a well-known JavaScript language capability: the ability to use any Unicode character in identifiers (e.g. variable names), as per the ECMAScript Standard.” reads the report published by Jscrambler. “The added obfuscation does introduce confusion (we call this obfuscation potency) but it does not add any resiliency (how hard it is to reverse engineer, using manual or automated methods). “
The Mongolian Skimmer uses common techniques: DOM monitoring for sensitive input changes, data exfiltration via encoded tracking pixels, DevTools detection to evade debugging, data collection on page unload, cross-browser compatibility, and anti-debugging measures to avoid code tampering.
The Mongolian Skimmer loads from an inline homepage script that fetches it from an external server. However, one variant found in a Magento 2 Google Tag Manager plugin loader only activates upon user interaction (e.g., scrolling, mouse movement), a trick implemented by threat actors likely to evade bots and avoid impacting page performance.
The Mongolian Skimmer captures final data entries using the beforeunload event, ensures cross-browser compatibility with various event-handling techniques, and employs anti-debugging tactics by monitoring formatting changes to detect and evade debugging attempts.
“The obfuscation techniques found on this skimmer may have looked to the untrained eye as a new obfuscation method, but that was not the case. It was just another Tuesday in cyberspace. It used old techniques to appear more obfuscated, but they are just as easy to reverse.” concludes the report. “A simple code transformer can remove all the weird characters automatically for you. Underneath the skin, it was just a very common type of skimmer code, commonly found in misconfigured or vulnerable Magento installations in the wild.”
Follow me on Twitter: @securityaffairs and Facebook
(SecurityAffairs – hacking, Mongolian Skimmer)
如有侵权请联系:admin#unsafe.sh