2024-9-25 14:11:50 Author: securityaffairs.com(查看原文) 阅读量:8 收藏
New Android banking trojan Octo2 targets European banks
Pierluigi Paganini
September 25, 2024

A new version of the Android banking trojan Octo, called Octo2, supports improved features that allow to takeover infected devices.
ThreatFabric researchers discovered a new version of the Android banking trojan Octo, called Octo2, that supports more advanced remote action capabilities needed for Device Takeover attacks.
The new malware has already targeted users in European countries, including Italy, Poland, Moldova, and Hungary.
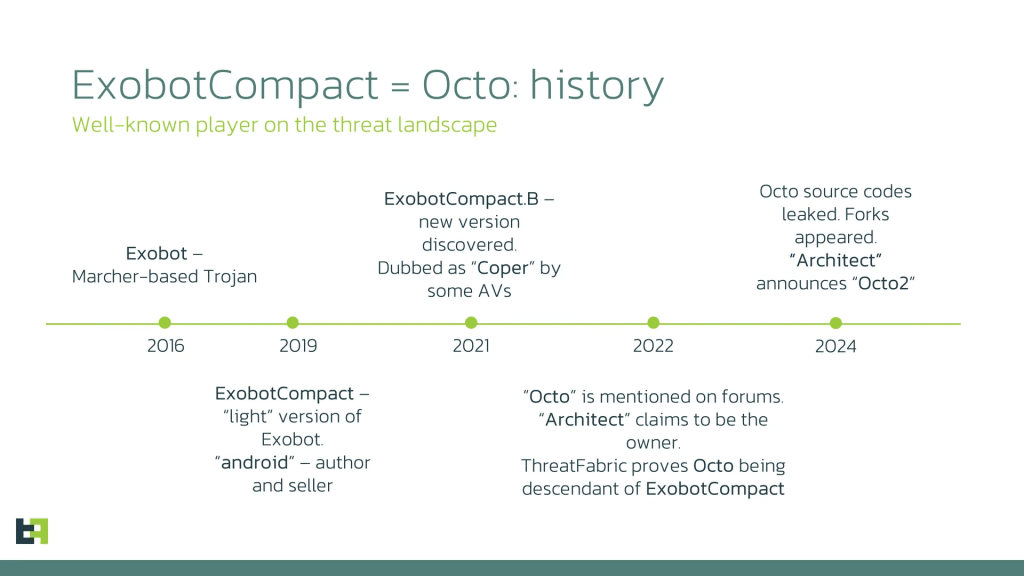
Octo2 is linked to the Exobot malware, first identified in 2016, which also gave rise to another variant called Coper in 2021.
In 2024, the Octo’s source code was leaked online, allowing other threat actors to create their own version. This leak likely prompted the original threat actor’s release of a new version, Octo2.

Over the years, Octo malware campaigns targeted regions worldwide, including Europe, the USA, Canada, the Middle East, Singapore, and Australia. Octo operates as Malware-as-a-Service, and its new version, Octo2, is being offered to existing users at the same price with early access. The researchers believe that many threat actors using Octo1 will switch to Octo2, expanding its global reach. Research indicates that Octo2 can block push notifications from specific apps, suggesting that cybercriminals are already targeting users of these apps as part of their attacks.
“These samples from the first campaigns observed were masquerading as Google Chrome, NordVPN, and “Enterprise Europe Network” applications.” reads ThreatFabric’s report. “However, as we said previously, we can expect threat actors behind Octo2 to not limit their activity and continue targeting users of mobile banking all over the world.”
ThreatFabric observed Zombinder serving as the first stage of the installation in Octo2 campaigns they have monitored. Upon launch, Zombinder will request the installation of an additional “plugin” which is Octo2, thus successfully bypassing Android 13+ restrictions.
Octo2 has been significantly improved, the authors enhanced stability during remote control sessions and improved its anti-detection and anti-analysis techniques. Key improvements include:
- Domain Generation Algorithm (DGA): Octo2 uses a proprietary DGA to generate dynamic C2 server names, allowing criminals to update domains easily. The malware also generates new encryption keys for every request, to improve the security of the C2 communication.
- Increased RAT stability: The malware now allows operators to reduce data transmission and improve connection stability on poor networks by lowering the quality of screenshots sent to the C2 server.
- Enhanced anti-analysis techniques: Octo2 employs more sophisticated obfuscation, making detection harder by using a multi-step process to decrypt and load malicious code.
There is presently no evidence to suggest that Octo2 is propagated via the Google Play Store, indicating that users are likely either downloading them from untrusted sources or being tricked into installing them via social engineering.
“The emergence of this Octo2 variant represents a significant evolution in mobile malware, particularly in the context of banking security. With enhanced remote access functionality, sophisticated obfuscation methods, and the wide availability of its predecessor’s source code, Octo2 is poised to remain a dominant force in the mobile malware landscape together with its older variants based on the leaked source code.” concludes the report. “This variant’s ability to invisibly perform on-device fraud and intercept sensitive data, coupled with the ease with which it can be customised by different threat actors, raises the stakes for mobile banking users globally. “
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Android)
如有侵权请联系:admin#unsafe.sh