2024-9-23 20:50:11 Author: securityaffairs.com(查看原文) 阅读量:17 收藏
North Korea-linked APT Gleaming Pisces deliver new PondRAT backdoor via malicious Python packages
Pierluigi Paganini
September 23, 2024

North Korea-linked APT group Gleaming Pisces is distributing a new malware called PondRAT through tainted Python packages.
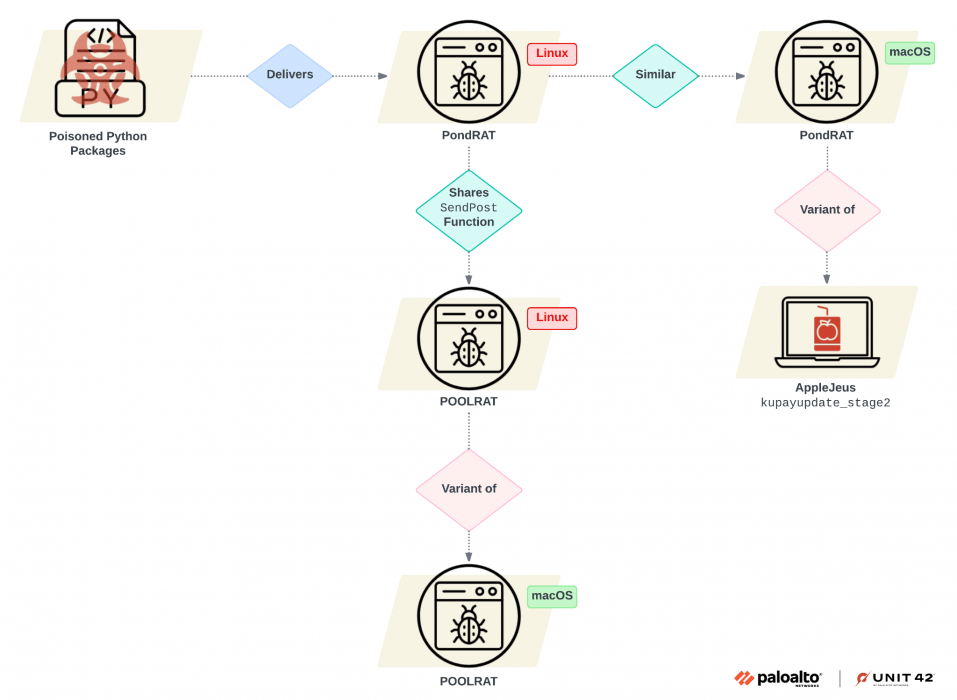
Unit 42 researchers uncovered an ongoing campaign distributing Linux and macOS malwar PondRAT through poisoned Python packages. The campaign is attributed to North Korea-linked threat actor Gleaming Pisces (also known as Citrine Sleet), who previously distributed the macOS remote administration tool POOLRAT (aka SIMPLESEA). PondRAT appears to be a lighter variant of POOLRAT. The attackers uploaded malicious packages to the Python repository PyPI. Threat actors attempted to compromise developers’ systems and, in turn, the supply chain vendors and their customers.
North Korea-linked APT Gleaming Pisces has been active since at least 2018, it is known for sophisticated attacks against the cryptocurrency industry.
Researchers discovered that the PondRAT malware shares significant similarities with macOS malware used in a previous AppleJeus campaign attributed to the Gleaming Pisces APT group. These similarities include overlapping code structures, identical function names, encryption keys, and similar execution flows. The attribution of this campaign to the same threat actor is based on the fact that PondRAT is closely related to POOLRAT macOS remote access tool.
The researchers identified the following malware-laced packages in PyPI repository, which have been already removed:
- real-ids (893 downloads)
- coloredtxt (381 downloads)
- beautifultext (736 downloads)
- minisound (416 downloads)
The infection chain relies on several poisoned Python packages to decode and execute encoded code. Once the Python is installed and the malicious package is loaded, a malicious code ran several bash commands to download the RAT, modifying its permissions and executing it.

The analysis of the POOLRAT revealed that the Linux and macOS versions use an identical function structure for loading their configurations, including similar method names and functionality. Experts speculate the Linux versions borrow the code from the macOS malware one.
Analysis of PondRAT samples revealed that its command handler shares similarities with POOLRAT. PondRAT supports basic commands to upload and download files, check if the implant is active, pause operations (“sleep”), and execute commands, with the option to retrieve output. The PondRAT’s functionality is similar but more limited compared to POOLRAT, for this reason, researchers labeled PondRAT is a lighter version of POOLRAT.
“The evidence of additional Linux variants of POOLRAT showed that Gleaming Pisces has been enhancing its capabilities across both Linux and macOS platforms.” concludes the report.
“The weaponization of legitimate-looking Python packages across multiple operating systems poses a significant risk to organizations. Such attacks pose a great risk because they can easily remain under the radar and pose detection challenges. Successful installation of malicious third-party packages can result in malware infection that compromises an entire network.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Gleaming Pisces)
如有侵权请联系:admin#unsafe.sh