2024-9-10 07:1:0 Author: securityaffairs.com(查看原文) 阅读量:9 收藏
Experts demonstrated how to bypass WhatsApp View Once feature
Pierluigi Paganini
September 09, 2024

Users are exploiting a privacy flaw in WhatsApp to bypass the app’s “View once” feature, allowing them to re-view messages.
The ‘View Once‘ feature in WhatsApp allows users to send photos, videos, and voice messages that can only be viewed once by the recipient.
Recipients cannot forward, share, or copy the “View Once” media, and they cannot take screenshots or screen recordings of it.
However, a bug in the feature in its browser-based web app allows recipients to re-view the messages and save the picture and video, which should vanish immediately after being displayed on the recipient’s device. The popular instant messaging app also prevents users from taking screenshots.
The “View Once” feature is available only on mobile devices but not on the web app and was first supported in 2021.
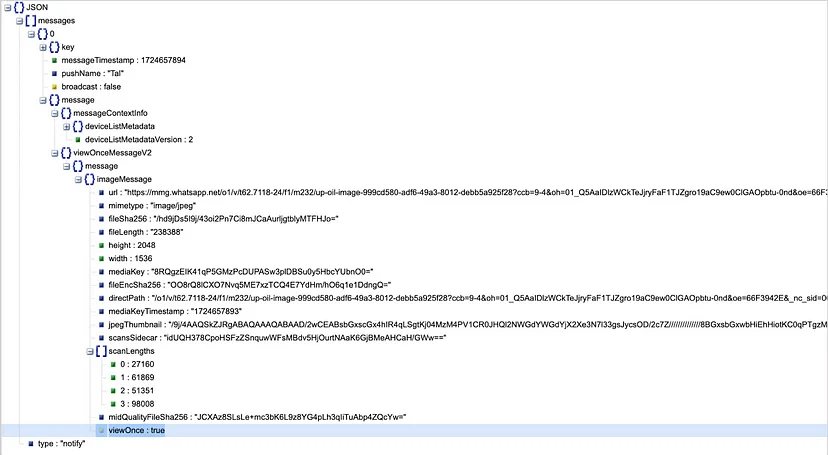
The researchers Tal Be’ery from Zengo X Research Team discovered the flaw and published technical details of the issue this week.
The researchers responsibly disclosed their findings to Meta but decided to publicly disclose the issue after discovering it was already being exploited in the wild. They aimed to protect the privacy of WhatsApp users and provided a more technical version of the blog for further details.
“The View once media messages are technically the same as regular media messages, only with the “view once” flag set. Which means it’s the virtual equivalent of putting a note on the picture that says “don’t look”. All that is required for attackers to circumvent it, is merely to set this flag to false and the “view once” media immediately becomes “regular” media and can be downloaded, forwarded and shared.” reads the post published by Tal Be’ery.
“Given its media URL, the View once media can be downloaded by any client, no authentication is needed (reader still needs the decryption key sent with the message). Again making the task of limiting the exposure of the media to controlled environments and platforms impossible “

The researchers built an unofficial WhatsApp client app using Baileys, an open-source implementation of the WhatsApp Web API, to demonstrate how to bypass the “View once” feature. They reported their findings to Meta but later discovered that others had already found and exploited the issue earlier in the year. These malicious users modified the message flag from “view once” to “false” using either a modified WhatsApp Android app or a web extension.
“To actually solve this issue, WhatsApp needs to apply a proper Digital Rights Management (DRM) solution that also verifies there is hardware support in place for such DRM. Such frameworks are provided by Android and iOS and other modern Operating Systems.” suggest the expert.
“A less robust but easier solution would be to have the sender send the “view once” message only to the primary device ( mobile ) and not to companion linked devices ( web, desktop). Please note it will only defeat extensions and is not relevant against patched mobile clients.”
WhatsApp has yet to reveal when it plans to address the issue.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, mobile)
如有侵权请联系:admin#unsafe.sh