
2024-9-6 17:44:14 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
NIST has released Version 2.0 of its widely used Cybersecurity Framework (CSF), a guidance document for mitigating cybersecurity risks. This update is not just a revision but a transformative approach to secure digital assets and infrastructures. The new version represents a significant advancement in addressing the evolving and complex cyber threats, offering a forward-looking perspective on cyber defense.
In this blog we will explore the changes in the framework, its key updates, and the enhanced focus on privilege access management (PAM) and identity security.
What is NIST CSF 2.0 Cyber Security Framework?
The NIST Cybersecurity Framework (NIST CSF) provides comprehensive guidance and best practices for private sector organizations to enhance information security and manage cybersecurity risks more effectively. Developed by the National Institute of Standards and Technology (NIST), a non-regulatory agency that advances measurement science, standards, and technology, the framework is designed to be adaptable, seamlessly integrating with existing security processes across various industries. The 2024 release of Version 2.0 marks the first major update since the framework’s initial launch, incorporating user feedback to better align with the evolving cybersecurity landscape and address emerging threats and technologies. This ensures that the NIST CSF remains relevant, effective, and continues to support organizations in strengthening their overall cybersecurity posture. It serves as an ideal foundation for implementing information security and cybersecurity risk management in virtually any private sector organization in the United States.
Book a Free Consultation with our Cyber Security Experts

NIST CSF 2.0: Enhanced Focus on PAM/IAM
The NIST 2.0 framework fundamentally acknowledges that Identity and Access Management (IAM) and Privileged Access Management (PAM) are more than just technical measures—they are strategic essentials that form the foundation of a modern organization’s security posture.
NIST CSF 2.0: Identity & Access Management (IAM)
IAM systems play a crucial role in ensuring that the right individuals have timely access to the appropriate resources for the right reasons, facilitating secure interactions with systems and data while enhancing productivity.
The concept of “Identity” has expanded significantly to include not just employees, but also customers, partners, devices, and automated services. This expansion necessitates robust IAM solutions to manage complex hierarchies of user rights and permissions across diverse environments. By prioritizing IAM, organizations can effectively manage digital identities, a critical measure for preventing data breaches and ensuring compliance with data protection regulations.
NIST CSF 2.0: Privileged Access Management (PAM)
PAM plays a vital role in controlling and auditing access privileges, and safeguarding identities. Access to privileged accounts can enable threat actors to make extensive changes to IT systems, access sensitive data, and execute critical tasks. Mismanagement or exploitation of these accounts represents a significant risk. PAM solutions address this risk by enforcing the principle of least privilege, monitoring and auditing privileged sessions, and implementing stringent authentication measures to verify the identities of those seeking access.
As cloud identities and access expand, managing various levels of privilege becomes more complex, and the distinction between “privileged” and “non-privileged” accounts becomes increasingly blurred. PAM capabilities are essential for securing all workforce identities and managing privileged access, regardless of how transient or fluid it may be.
Changes in NIST CSF 2.0
Below are the changes in the framework:
Updated Response and Recovery Functions:
One of the most significant updates in NIST CSF 2.0 is its enhanced focus on the Respond and Recover functions, which received relatively less emphasis in version 1.1. The Respond function now aligns with cyber incident response outcomes that are meaningful and practical, rather than merely addressing them at a high level.
Introduction to New Function: Govern
The most notable update in version 2 of the CSF is the introduction of the Govern function, which increases the total number of core functions to six. Although this function is a new addition to the original set, it is not entirely unprecedented. It consolidates elements from the version 1.1 categories, making the framework more streamlined and easier to understand—a key feature of the revamped NIST CSF.
For instance, in version 1.1, outcomes related to Roles and Responsibilities were dispersed across the PR.IP and ID.BE categories. In version 2.0, these outcomes are now conveniently unified within the Govern function.
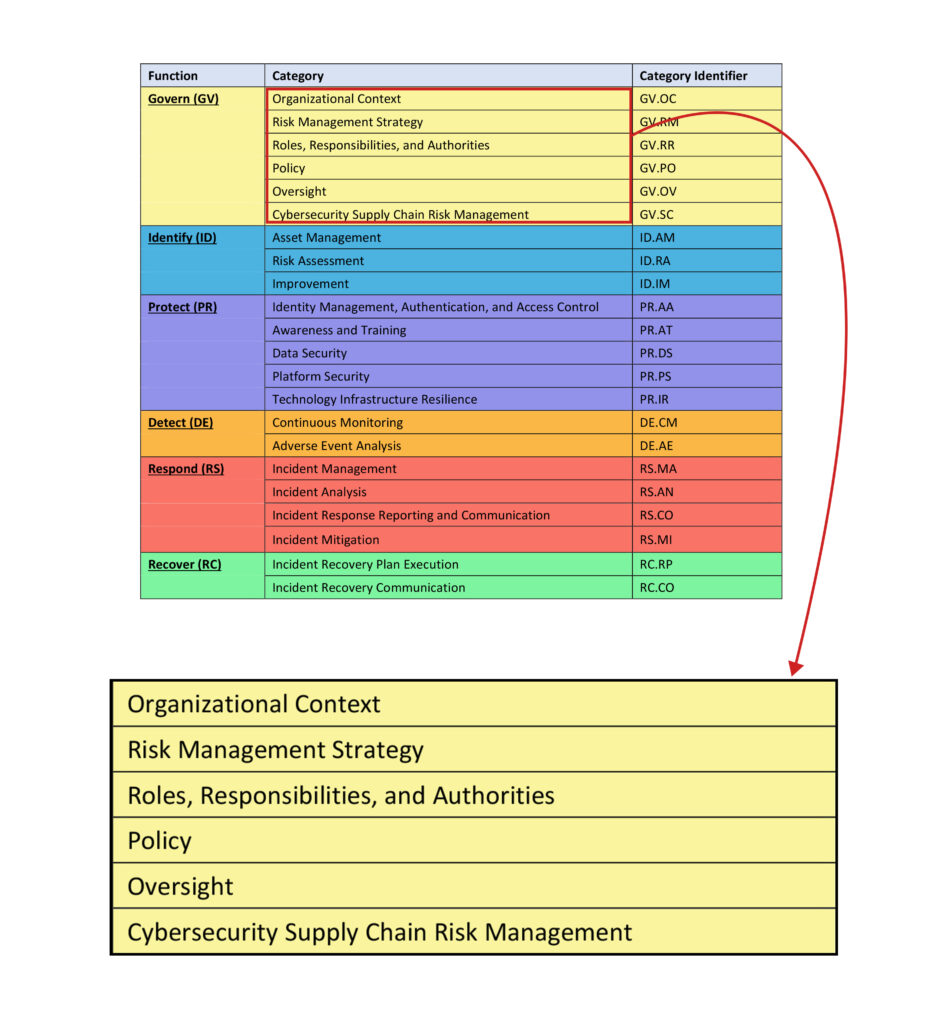
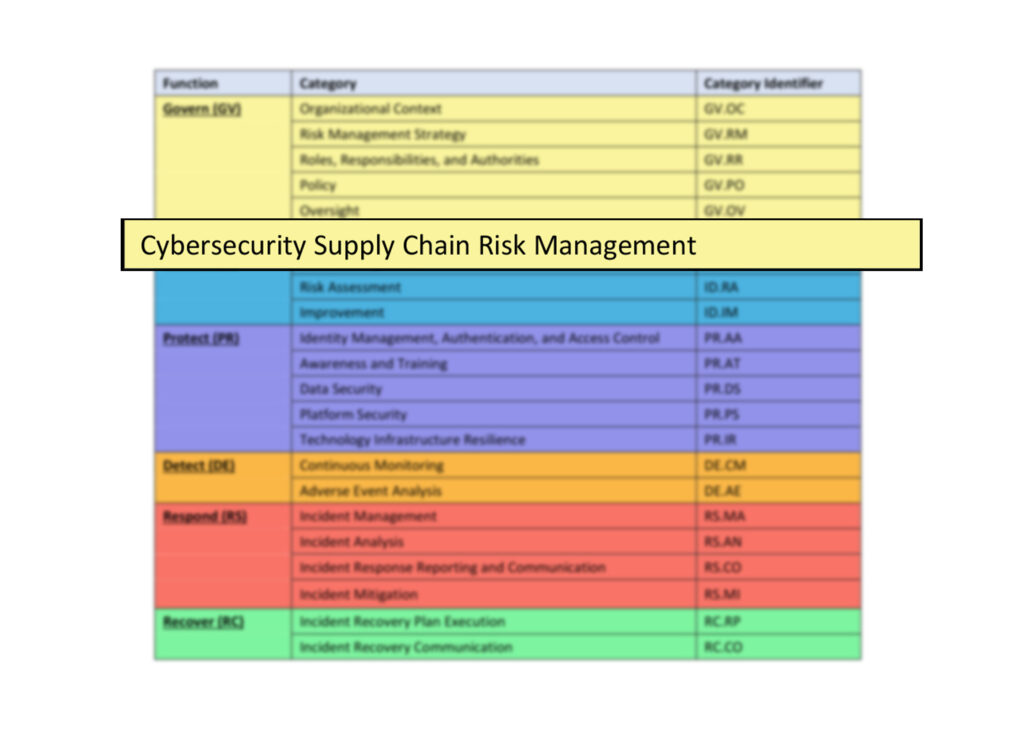
Increased Emphasis on Supply Chain Risk Management
Given the rise in supply chain attacks since the launch of NIST CSF in 2014, NIST has understandably intensified its focus on Cybersecurity Supply Chain Risk Management (SCR) in the new framework. Many of these outcomes are integrated into the Govern function, providing stakeholders and C-suite executives with greater visibility into this critical attack vector, which costs businesses an average of $4.76 million when compromised.
Broadened Industry Scope and More Explicit Guidelines
Originally developed to enhance cyber threat resilience for critical infrastructure in response to Executive Order 13636 in 2013, the NIST CSF has gained widespread adoption across various industries due to its proven effectiveness.
NIST CSF 2.0 represents a strategic shift from a framework focused primarily on critical infrastructure to one that is more broadly applicable across industries. This change is evident not only in the updated name (formerly “Framework for Improving Critical Infrastructure Cybersecurity,” now “The NIST Cybersecurity Framework (CSF) 2.0”) but also in the clearer communication and broader applicability of the framework.
How can Kratikal Secure You With NIST CSF 2.0?
Kratikal provides comprehensive support for implementing NIST Cybersecurity Framework (CSF) 2.0 to strengthen your organization’s cybersecurity posture. We conduct thorough assessments and gap analyses to identify areas for improvement, develop customized roadmaps to align your strategy with NIST CSF 2.0 requirements and assist in deploying the necessary controls and processes. Our services also include training programs to boost your team’s understanding of NIST CSF 2.0 and ongoing monitoring and reviews to adapt to emerging threats. Partner with Kratikal to ensure a robust, compliant cybersecurity framework that effectively protects your organization.
FAQs
- What is the difference between NIST CSF 2.0 and 800 53?
NIST CSF is a broad framework centered on risk management, whereas NIST SP 800-53 is a detailed collection of security controls. NIST CSF offers a wide range of best practices for organizations to adopt, while NIST SP 800-53 outlines specific security controls that need to be implemented.
- Is NIST CSF mandatory?
Compliance with the NIST CSF is required for federal agencies and their supply chain partners, while private sector businesses have the choice to adopt it on a voluntary basis.
The post NIST CSF 2.0 Cyber Security Framework appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/nist-csf-2-0-cyber-security-framework/
如有侵权请联系:admin#unsafe.sh