
2024-8-16 21:0:0 Author: www.tenable.com(查看原文) 阅读量:12 收藏

NIST has released the first encryption algorithms that can protect data against quantum attacks. Plus, MIT launched a new database of AI risks. Meanwhile, the CSA published a paper outlining the unique risks involved in building systems that use LLMs. And get the latest on Q2’s most prevalent malware, the Radar/Dispossessor ransomware gang and CVE severity assessments!
Dive into six things that are top of mind for the week ending August 16.
1 - NIST releases first quantum-resistant algos
Three encryption algorithms that can protect data from quantum computer attacks are ready, a significant step in the efforts to prevent a global data-theft disaster when these powerful systems become available around 2030.
The post-quantum encryption standards are designed to secure “a wide range of electronic information,” including email messages and e-commerce transactions, the U.S. National Institute of Standards and Technology (NIST) announced this week.
Here’s the problem: Cybercriminals are eagerly waiting to get their hands on quantum computers, which will be able to decrypt data protected with existing public-key cryptographic algorithms.

While NIST is evaluating more post-quantum algorithms, the agency is urging system administrators to start transitioning to this first set of encryption tools right away because the integration process will take time.
“There is no need to wait for future standards,” said Dustin Moody, NIST mathematician and leader of the standardization project. “Go ahead and start using these three.”
These are the three encryption standards, called Federal Information Processing Standard (FIPS):
- FIPS 203 is intended to be the primary standard for general encryption. Its advantages include its speed of operation and its small encryption keys.
- FIPS 204 is envisioned as the primary standard for protecting digital signatures.
- FIPS 205 is also designed for digital signatures.
The standards contain the encryption algorithms’ computer code, implementation instructions and their intended uses.
To get more details, check out:
- The announcement “NIST Releases First 3 Finalized Post-Quantum Encryption Standards”
This video
For more information about the quantum computing cyberthreat:
- “CISA: Critical infrastructure must prep for quantum computing threat” (Tenable)
- “Think you can ignore quantum computing? Think again” (CIO)
- “Cybersecurity of Quantum Computing: A New Frontier” (Carnegie Mellon University)
- “Will Quantum Computers Become the Next Cyber-Attack Platform?” (InformationWeek)
- “Quantum computing could threaten cybersecurity measures. Here’s why – and how tech firms are responding” (U.S. National Security Agency)
2 - MIT launches database of AI risks with 700-plus entries
The Massachusetts Institute of Technology (MIT) this week unveiled the AI Risk Repository, a database that aims to consolidate in a single place all risks associated with the use of artificial intelligence.
To compile the initial set of 700-plus risks, MIT analyzed 43 existing AI risk frameworks, and found that even the most comprehensive framework overlooked about 30% of all risks currently listed in the database.
“Since the AI risk literature is scattered across peer-reviewed journals, preprints, and industry reports, and quite varied, I worry that decision-makers may unwittingly consult incomplete overviews, miss important concerns, and develop collective blind spots,” project leader and MIT postdoctoral researcher Peter Slattery said in a statement.
The AI Risk Repository’s risk domains include:
- AI system safety, failures, and limitations
- Socioeconomic and environmental harms
- Discrimination and toxicity
- Privacy and security
- Malicious actors and misuse
The risk domains are further subdivided into 23 subdomains. The AI Risk Repository is a “living database” that’ll be expanded and updated, according to MIT.
To get more details, check out:
- The AI Risk Repository’s announcement
- The AI Risk Repository’s home page and FAQ
This explainer video
For more information about AI risks:
- “4 Types of Gen AI Risk and How to Mitigate Them” (Harvard Business Review)
- “World leaders still need to wake up to AI risks” (Science Daily)
- “To understand the risks posed by AI, follow the money” (The Conversation)
- “Why can’t anyone agree on how dangerous AI will be?” (Vox)
- “Too Much Trust in AI Poses Unexpected Threats to the Scientific Process” (Scientific American)
3 - CSA: Beware of unique risks when building systems with LLMs
If your organization is building systems that use large language models (LLMs), your system architects and engineers need to be aware of special risks and challenges that impact security.
That’s the main topic of the Cloud Security Alliance’s new report “Securing LLM Backed Systems: Essential Authorization Practices,” published this week. It offers guidance and best practices for securely building systems that leverage LLMs.
“LLMs used as system components pose several new challenges for architects and engineers regarding predictability, security, and authorization,” reads the report, which is aimed at systems engineers and architects, and at privacy and security professionals.
The report also outlines essential components of systems that use LLMs:
- Vector databases, which are used for AI-system retrieval and processing
- Orchestrators, which coordinate LLM inputs and outputs
- LLM caches, which cache LLM content for faster retrieval, but need access controls
- Validators, which protect the input / output process against attacks like SQL injection, command injection and cross-site scripting
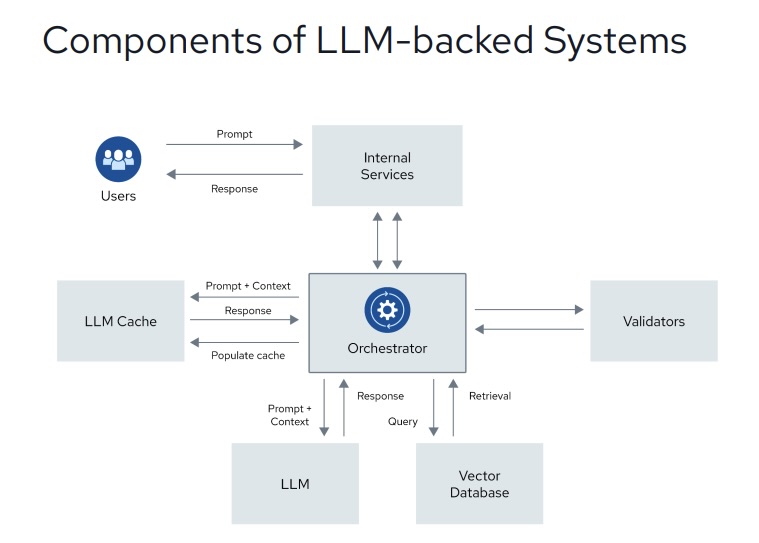
(Source: Cloud Security Alliance’s “Securing LLM Backed Systems: Essential Authorization Practices” report, August 2024)
To get more details, check out:
- The report’s announcement “Cloud Security Alliance Issues Paper Detailing Unique Challenges and Risks Presented by Use of Large Language Models (LLMs)”
- The full report “Securing LLM Backed Systems: Essential Authorization Practices”
For more information about AI risks to cybersecurity, check out these Tenable blogs:
- “How to Discover, Analyze and Respond to Threats Faster with Generative AI”
- “Never Trust User Inputs -- And AI Isn't an Exception: A Security-First Approach”
- “AI Is About To Take Cybersecurity By Storm: Here's What You Can Expect”
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood”
- “Do You Think You Have No AI Exposures? Think Again”
4 - A Tenable poll on CVE severity assessments
During a recent webinar about Tenable Security Center, we polled attendees about how they assess the severity of Common Vulnerabilities and Exposures (CVEs.)
Check out what they said about their current and future use of the Common Vulnerability Scoring System (CVSS), the Vulnerability Priority Rating (VPR) and the Exploit Prediction Scoring System (EPSS).
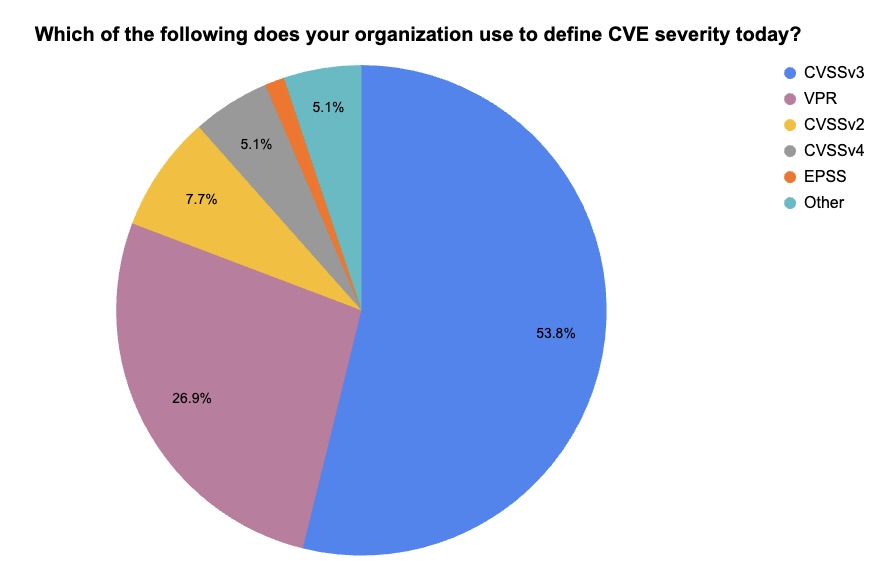
(59 respondents polled by Tenable, August 2024. Respondents could choose more than one answer.)
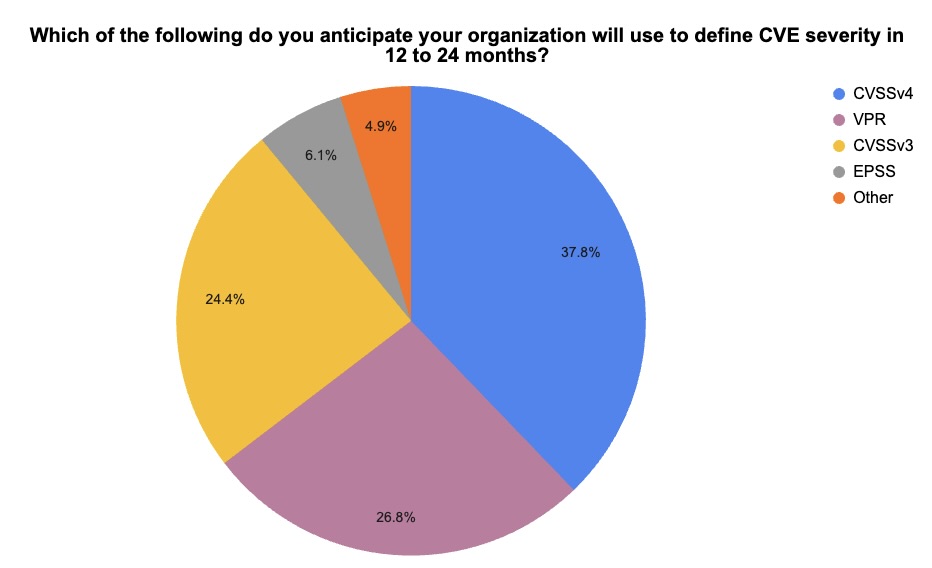
(55 respondents polled by Tenable, August 2024. Respondents could choose more than one answer. CVSSv2 was an option but no one chose it.)
If you’re interested in the latest about Tenable Security Center and in vulnerability management best practices, watch the on-demand webinar “Tenable Security Center Customer Update, August 2024.”
5 - SocGholish again tops quarterly list of malware incidents
For the fourth straight time, the SocGholish malware variant – used in fake software-update attacks – ranked first on the Center for Internet Security’s quarterly report of malware infections.
SocGholish accounted for 60% of malware incidents in the second quarter of 2024, a sign that the popularity of fake software-update attacks remains strong. It first topped the list in the third quarter of 2023, with a 31% share of malware incidents.
In fake software-update attacks, users get tricked into installing a legitimate-looking update for, say, their preferred browser, that instead infects their computers with malware.
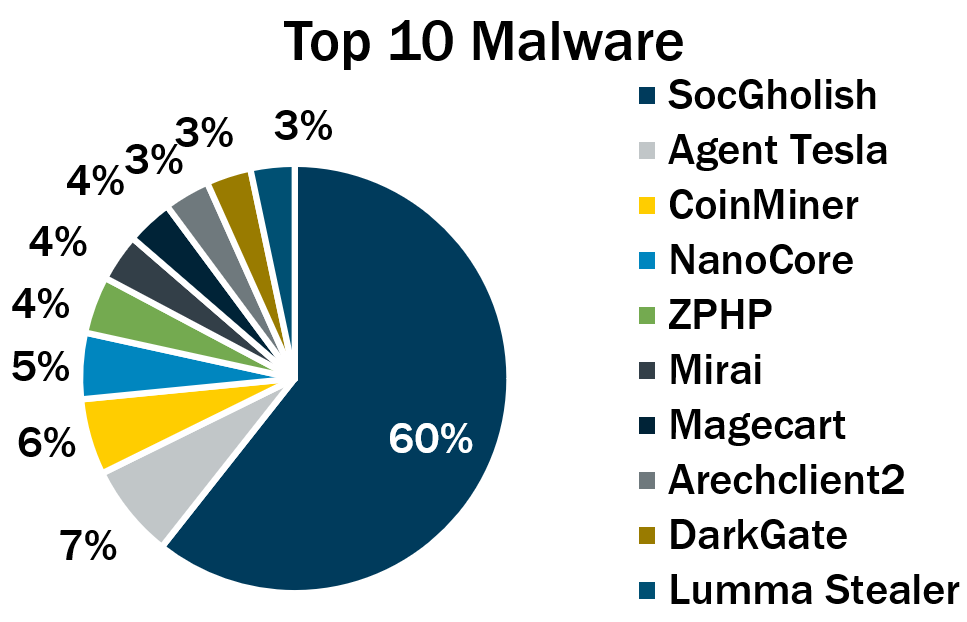
(Source: Center for Internet Security, August 2024)
Here’s the full list, in descending order:
- SocGholish, a downloader distributed through malicious websites that tricks users into downloading it by offering fake software updates
- Agent Tesla, a remote access trojan (RAT) that captures credentials, keystrokes and screenshots
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI)
- NanoCore, a RAT that spreads via malspam as a malicious Excel spreadsheet
- ZPHP, a JavaScript downloader that’s distributed via fake browser updates
- Mirai, a malware botnet that compromises IoT devices to launch DDoS attacks
- Magecart, a credit card skimming and point-of-sale malware that steals payment data from forms on vulnerable websites
- Arechclient2, also known as SectopRAT, is a .NET RAT whose capabilities include multiple stealth functions
- DarkGate, a downloader and keylogger that steals financial data and personally identifiable information (PII), and delivers other malware
- Lumma Stealer, an infostealer used to swipe PII, credentials, cookies and banking information
To get more information, check out the CIS blog “Top 10 Malware Q2 2024,” where you’ll find more details, context and indicators of compromise for each malware strain.
For details on fake update attacks:
- “The Fake Browser Update Scam Gets a Makeover” (Krebs on Security)
- “Watch Out: Attackers Are Hiding Malware in 'Browser Updates'” (Bleeping Computer)
- “Hackers Use Fake Browser Updates for AMOS Malware Attacks Targeting Mac Users” (MSSP Alert)
- “Malware crooks find an in with fake browser updates, in case real ones weren't bad enough” (Bleeping Computer)
- “Hackers have been spreading malware via fake Chrome updates” (TechRadar)
VIDEOS
Fake Chrome Update Malware (The PC Security Channel)
Apple Mac OS users falling for fake browser update that installs malware (Windows, Computers and Technology)
6 - Radar/Dispossessor ransomware gang hit by int’l police operation
Law-enforcement agencies from Germany, the U.K. and the U.S. disrupted the Radar/Dispossessor ransomware group, shutting down its servers and domains in these three countries.
Radar/Dispossessor targets small- and medium-sized businesses (SMBs), looking for systems with unpatched vulnerabilities, weak passwords and no multi-factor authentication, the FBI announced this week. It uses a double-extortion model, exfiltrating victims’ data as well as encrypting it.
Although it initially targeted the U.S., law enforcement agencies found evidence that it has struck victims in about 15 other countries in Europe, Asia and Latin America. Launched in August 2023, it is led by an individual known as “Brain,” according to the FBI.

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
Related Articles
- Anti-malware
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- NIST
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Tenable Vulnerability Management trials created everywhere except UAE will also include Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose your subscription option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Tenable Vulnerability Management trials created everywhere except UAE will also include Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose your subscription option:
Thank you
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Tenable Vulnerability Management trials created everywhere except UAE will also include Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose your subscription option:
Thank you
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Web App Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a sales representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank you
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Get the Operational Technology security you need.
Reduce the risk you don’t.
Request a demo of Tenable Identity Exposure
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
in action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management in action
Know the exposure of every asset on any platform.
Try Tenable Nessus Professional free
Free for 7 days
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
now available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Nessus Expert free
Free for 7 days.
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh