
2024-8-9 18:46:36 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
Penetration testing plays a key role in evaluating a company’s infrastructure security, and this blog focuses on web penetration testing. The process has an impact on four main steps: gathering information, researching and exploiting vulnerabilities, writing reports with suggestions, and fixing issues while providing ongoing support. These tests are vital to ensure secure software development throughout an app’s life cycle.
Both manual and automated web application security testing are essential components of a robust security strategy. Organizations should select the appropriate approach based on the specific needs of their web applications, considering factors such as size, complexity, and security requirements.
IT Governance’s study in January 2024 found 4,645 reported cybersecurity incidents leading to the theft of 29,530,829,012 records. Also, Statista noted a major Yahoo data breach in the United States that same month, which affected more than 3 billion online users. This post will explore the contrasts between manual and automated web penetration testing.
Difference between Manual and Automated Web Penetration Testing
| Basis | Manual Web Penetration Testing | Automated Web Penetration Testing |
| Methodology | Human testers examine the application to find vulnerabilities. This includes code review and penetration testing. | Software tools scan the application to find vulnerabilities through static analysis, dynamic analysis, and interactive testing. |
| In-Depth Analysis | Testers perform a thorough analysis of the application’s code and functionality. They can uncover complex vulnerabilities, including those in business logic, which tools might miss. | It detects common vulnerabilities that tools can predefine. It has limits to the issues the tools can identify and might miss more complex or new flaws. |
| Attack Simulation | Security experts can think creatively and simulate real-world attack scenarios, mimicking the actions of malicious hackers to uncover potential security flaws. | While capable of simulating certain types of attacks, it lacks the human creativity and adaptability to fully replicate real-world scenarios. |
| Efficiency and Scalability | Time-consuming and labor-intensive, requiring skilled testers. It may not be scalable for large or complex applications due to the high cost and time required. | Fast and scalable, capable of quickly scanning large and complex applications. It can be integrated into the software development lifecycle (SDLC) for continuous testing and feedback. |
| Accuracy and False Positives | Generally results in fewer false positives, as human testers can accurately assess and verify potential issues. | Can produce false positives, requiring human intervention to verify and remediate reported issues. |
Process of Web Penetration Testing
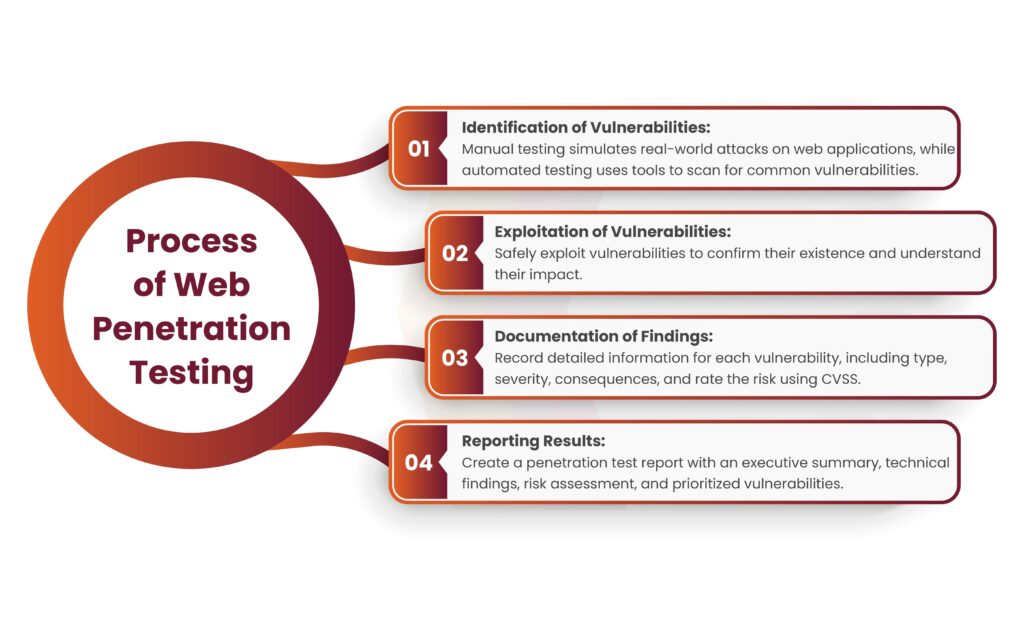
Identification of Vulnerabilities
Manual Testing
- Manual testing is conducted by simulating real-world attacks on the web application.
- Use techniques such as testing for input validation, manipulating parameters, and analyzing session management to uncover vulnerabilities.
- Focus on identifying common issues like SQL injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and security misconfiguration.
Automated Testing
- Use automated vulnerability scanning tools to enhance manual testing efforts.
- Conduct dynamic application security testing (DAST) scans to detect issues like those in the OWASP Top 10.
- Implement static application security testing (SAST) to identify code-level vulnerabilities in the source code.
Exploitation of Vulnerabilities
Safely exploit identified vulnerabilities to confirm their existence and understand their impact. Be careful to avoid damaging the web application or disrupting its availability. Record all steps taken during the exploitation process for future analysis and reporting. Also analyze the potential consequences of each vulnerability on data confidentiality, integrity, and system resource availability. Consider the business implications and possible outcomes of a successful attack.
Documentation of Findings
To document vulnerabilities comprehensively, record detailed information about each, including its type, location, severity, and potential consequences. Include visual evidence like screenshots or session logs and provide technical details for developers. For risk assessment, assign a risk rating based on severity, exploitability, and business impact, using standardized scoring systems like CVSS to quantify the risk.
Reporting Results
Prepare a thorough penetration test report that features an executive summary, technical findings, risk assessment, and recommended remediation steps. Clearly explain the impact of identified vulnerabilities for non-technical stakeholders in the executive summary. Prioritize vulnerabilities based on their risk rating and potential impact on the web application and organization, providing guidance on which issues to address first. Offer specific, actionable recommendations for mitigating vulnerabilities, including advice on configuration changes, code fixes, or additional security controls.
Comparison Between Automated and Manual Penetration Testing
Manual web penetration testing involves a trained security consultant simulating attacks to find in-depth vulnerabilities, including business logic issues, and provides verified findings and proofs of concept. Automated vulnerability scanning uses tools to identify common, easily detectable flaws, like missing HTTP headers, but may produce false positives and miss complex vulnerabilities. While manual testing offers a thorough assessment, automated scanning is efficient for ongoing monitoring and can be used to complement manual efforts. Both methods play crucial roles in maintaining robust web application security.
Book a Free Consultation with our Cyber Security Experts

Best Penetration Testing Service Provider
As a CERT-In empanelled organization, Kratikal is equipped to enhance your understanding of potential risks. Our manual and automated Vulnerability Assessment and Penetration Testing (VAPT) services proficiently discover, detect, and assess vulnerabilities within your IT infrastructure.
AutoSecT: Powered by Kratikal is a vulnerability management tool that goes beyond traditional methods to protect the digital assets of your company. It uses advanced Vulnerability Management Detection and response (VMDR) techniques to systematically manage rigorous testing projects and stay updated on security advancements at every step. It’s the ultimate solution for keeping your organization’s digital assets secure.
Conclusion
Web penetration testing is a crucial process for safeguarding modern businesses from cyber threats. Both manual and automated testing approaches play significant roles, each offering unique strengths and limitations. Manual testing provides a detailed, creative analysis of vulnerabilities that automated tools may miss, while automated testing offers efficiency and scalability for ongoing security assessments.
By combining these methods, organizations can achieve a comprehensive security posture, effectively identifying and addressing vulnerabilities. Proper documentation and reporting of findings are essential to communicate risks and remediation strategies clearly. As cyber threats evolve, ongoing penetration testing and prompt remediation remain vital to protecting sensitive data and ensuring the resilience of web applications against potential attacks.
FAQs
- What is the difference between manual and automated web app testing?
Human testers work with software to spot vulnerabilities in manual testing. On the flip side automated testing relies on computer programs or scripts to run predefined tests without human input.
- What are the 5 phases of penetration testing?
Penetration testing consists of five stages: reconnaissance, scanning, vulnerability assessment, exploitation, and reporting.
The post Automated vs Manual: Web Penetration Testing appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/automated-vs-manual-web-penetration-testing/
如有侵权请联系:admin#unsafe.sh