2024-8-8 10:20:41 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Overview
Leveraging NSFOCUS’s Global Threat Hunting System, NSFOCUS Security Labs (NSL) captured an attack campaign targeting Azerbaijan and Israel on July 1, 2024. By analyzing the tactics, attack vectors, weapons, and infrastructure of the attack in this incident, it was found that the exposed attack characteristics have no direct connection with known APT groups. Therefore, NSL attributes the attackers of this campaign to a new APT group, marking the group as Actor240524 and naming the new type of Trojan program used by the group as ABCloader and ABCsync.
In this attack incident, Actor240524 attackers used spear-phishing emails to launch attacks on Azerbaijani and Israeli diplomats, intending to steal sensitive data through new weapons.
Introduction to Actor240524
Actor240524 possesses the ability to steal secrets and modify file data, using a variety of countermeasures to avoid overexposure of attack tactics and techniques.
Activity Description
In this incident, the attackers used a Word document embedded with malicious macro code as bait, with the file name “iden.doc”. The content consists of three blurry images, as shown below:
- An official document issued by government websites or news organizations.
- An official page of Azerbaijan, displaying the national emblem, name, and some links of Azerbaijan.
- An official page of Azerbaijan, displaying the cabinet building and a list of administrative personnel.
NSL found that the bait document first appeared in the Israeli region, and all the languages in the above bait images are Azerbaijani.
Azerbaijan and Israel are allied countries with close economic and political exchanges. Actor240524’s operation this time is likely aimed at the cooperative relationship between the two countries, targeting phishing attacks on diplomatic personnel of both countries.
Attack Process
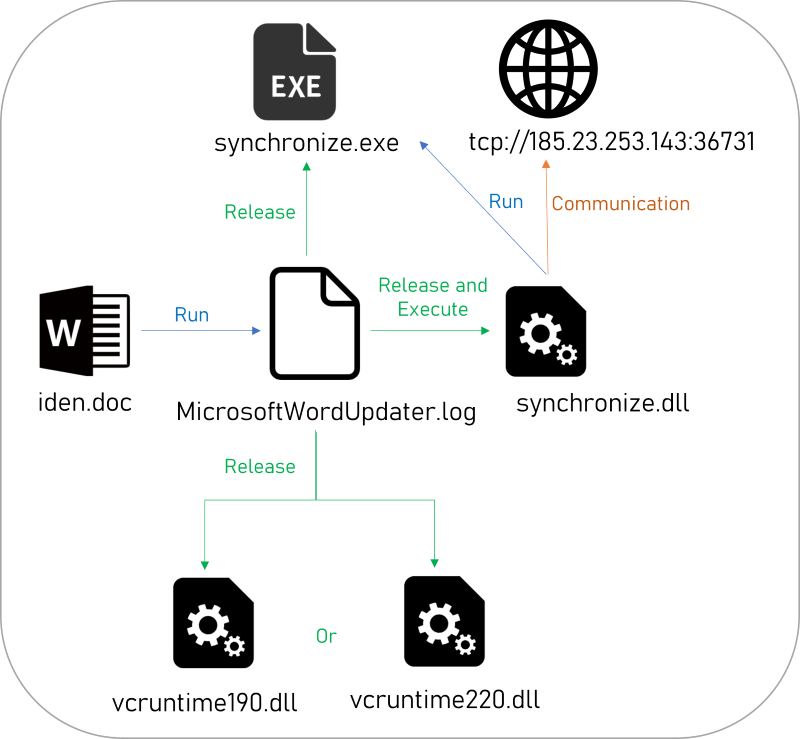
The attacker lured the target into clicking “Enable Content” through the malicious document containing blurry images, which upon execution, reads encrypted data from within itself, releases three executable files, and executes ABCsync. The attack process of this incident is summarized as follows:
- After opening the document, the user is prompted to click “Enable Content.” Upon clicking, the macro code is executed, utilizing the embedded VBA program in the doc to decode and store the malicious payload to a specified path and execute ABCloader.
- Execute “MicrosoftWordUpdater.log” (ABCloader) to decrypt and release three executable files and load the subsequent “synchronize.dll” (ABCsync).
- ABCsync connects to the C2 server, receives remote commands, and performs the corresponding functions of the commands.
The VBA script executed after the victim runs the phishing document functions as follows: It decodes the malicious payload stored within itself to a specified path “C:\Users\Public\Documents\MicrosoftWordUpdater.log” (this file is an .exe file, and the attacker has changed its extension to .log to confuse the user), then executes the command to run the program, with the code as shown below:
“MicrosoftWordUpdater.log” (ABCloader) is a loader. Its main function is to determine the running environment, decrypt the program, and load the subsequent DLL (ABCsync).
After the program runs, it initializes, executes the decryption function, and dynamically obtains the function address, storing it in a global structure array for subsequent use.
It then performs various anti-sandbox and anti-analysis techniques for environmental detection. If a sandbox environment or analysis behavior is detected, it will jump to the exit function and execute this function to terminate the current process.
After passing the anti-analysis detection, it decrypts the encrypted data stored in the current program and writes the decrypted data to a specified location (C:\Users\AppData\Local\Microsoft\Edge\User Data\Synchronize). Depending on whether the value at the memory location 0x7ffe0260 is less than 0x4E20, it decrypts either “vcruntime220.dll” or “vcruntime190.dll,” and then decrypts two files fixedly, “synchronize.dll” and “synchronize.exe.” Finally, it loads the “synchronize.dll” dynamic link library (ABCsync).
Adversarial Technique Analysis
The ABCloader and the malicious payload ABCsync employ similar adversarial analysis detection methods. The following is a detailed description of the adversarial techniques of the Trojan.
API Encryption
Important strings within the program (file paths, file names, keys, error messages, C2 addresses) and key API functions are encrypted to counteract sandbox detection and static analysis.
PEB Detection
The BeingDebugged field and the NtGlobalFlag flag are checked to determine if the process is being debugged. The BeingDebugged field in the PEB, if set to 1, indicates that the process is being debugged.
By calling the NtQueryInformationProcess function, it checks for the presence of a debugger, using ProcessDebugPort(0x7) and ProcessDebugObjectHandle(0x1E) to determine if the process is in a debugging state.
Hardware Breakpoint Detection
It determines the presence of debugging behavior by checking whether hardware breakpoints have been set.
Screen Resolution Detection
It checks the screen resolution to determine whether the environment is a virtual machine or sandbox: by determining if the display uses standard resolutions (1920, 2560, 1440, 1080, 1200, 1600, 900) to judge whether the process is running in a sandbox or virtual machine environment.
Process Count Detection
It determines if the number of processes running in the system is less than 200, and if so, it exits the process.
Specific Permission Detection
Whether the current process’s access token has specific permissions (built-in domain and administrator group). It determines the running environment by checking for special permissions.
Attack Payload Analysis
“ABCsync” is the attack payload of the attack process, with its main functions being to execute remote shells, modify user data, steal user files, etc.
“ABCsync” uses the same adversarial techniques as “ABCloader” for encrypted communication. Multiple communication commands combine to complete a function, suggesting that the program is still in the testing phase.
First, “ABCloader” will load “ABCsync,” then use the same adversarial techniques for anti-debugging. It then initializes strings and the AES encryption key, creates registry entries and values to achieve COM component hijacking. Finally, it connects to the C2 to receive commands and execute them.
Communication
After decrypting the C2 address “185.23.253.143,” it connects and sends a fixed data packet. After sending the data packet, the server automatically sends the command “aaaa” (after decryption). It executes the function to obtain basic computer information. It continuously receives commands and sends online packages until the next command is updated.
The program uses the UDP protocol for communication, and during the communication process, it uses the encryption algorithm AES-256 (with the encryption mode ChainingModeCBC) to encrypt the communication data.
Functionality
The main functions of the Trojan program are to execute remote shells, modify user data, and steal user files through pipe communication. The C2 end issues command functions in steps, and the client will return error information. Therefore, it is speculated that this program is still in the testing phase. Because the commands are detailed and each step is well-ordered, it is speculated that this Trojan program has a very complex control end, capable of combining functions for more diverse operations.
To execute a remote shell, the server first issues the command “aaaaaa aaaaa-” as needed, establishing pipe communication between CMD and the current process. Then, by sending “aaaa aaaaaaa” plus “CMD”, the desired command is sent to the client to execute the remote shell command.
To obtain file data, the server first sends “bbbbbbbb-,” the client creates a file to get the handle and obtain the size of the file. The file location is identified through the parameters following the command. Then, the command “aaaa-aaaaa-” is sent to read the file data through the handle and send it to the server.
To rewrite the content of a specified file in the computer, the server first issues the command “aaaaaa-” to set the file to be modified, and then uses the “aaaaaaaa-” command to set the data to be modified for the specific modification operation. The specified file is modified through the API.
Specific function parameters are shown in the table 6.1. Parameters follow the command, forming a long string.
Table 6.1 Function Parameters
| Instruction | Parameter | Function | Sent Value |
| aaaa | – | Send system information | Encrypted system information |
| aaa aaaaa- | – | Parse instruction | – |
| aaaaaa aaaaa- | – | Establish pipe communication between CMD and the current process (Create a pipe for subsequent execution of cmd instructions) | Send bbbbbb on failure Send aaaaaaa on success |
| aaaa aaaaaaa | Command to execute | Write the CMD instruction to be executed | Send bbbbbb on failure Send aaaaaaa on success |
| aaaaa aaaaaa | – | Read the output information after executing the CMD instruction | Return –aa aaaa– on failure |
| aaaa aaaaa | – | Exit the process | – |
| aaaaaa- | Specified file path to retrieve | Get the handle of the specified file (open the file for subsequent writing) | Send bbbbbb on failure Send aaaaaaa on success |
| aaaaaaaa- | Data to write to the file | Write the specified content to the file obtained by the handle from the aaaaaa- instruction | – |
| bbbbbbbb- | Specified file path to retrieve | Get the handle of the specified file and the file size (open the file and get the size for subsequent sending) | Send bbbbbb on failure |
| aaaa-aaaaa- | – | Send the file specified by the bbbbbbb- instruction | – |
| ccccc | – | Reconnect to the network | – |
| aa aaaaa | – | Execute synchronize.exe | – |
| bbbbb | – | Interactive instruction | aaaaaaaaaa |
| – | – | Receive data with a length of 0 | aaaaaaaaaa |
There are also other behaviors in ABCsync, such as initializing program execution detection; if some initialization fails, a forged error message pops up to deceive the victim.
The Trojan also determines the system version based on the value stored at the address 0x7ffe0260, confirming which COM component to hijack.
Other Component Functions
synchronize.exe
synchronize.exe is a loader with functions essentially identical to ABCloader, with the main difference being that synchronize.exe removes the encrypted data used to decrypt the synchronize.exe program itself, meaning that the program will not decrypt itself repeatedly.
vcruntime190.dll
ABCsync implements COM component hijacking, replacing the originally called LanguageComponentsInstaller.dll with the malicious vcruntime190.dll, achieving persistent residency capabilities.
When the system calls LanguageComponentsInstaller.dll, it results in the execution of vcruntime190.dll, whose main function is to create a thread to run synchronize.exe, thus achieving persistence (the normal component is located at C:\Windows\System32\LanguageComponentsInstaller.dll).
vcruntime220.dll
vcruntime220.dll has the same functionality as vcruntime190.dll. It replaces the originally called executable file with a malicious dll to achieve persistent residency capabilities. The difference lies in that Vcruntime220.dll hijacks the COM component Windows.UI.FileExplorer.dll. Windows.UI.FileExplorer.dll is mainly used to support certain features and interface elements of the File Explorer and the normal component is located at C:\Windows\System32\Windows.UI.FileExplorer.dll.
IoC
Decoy Document: iden.doc
HASH: 1ee73b17111ab0ffb2f62690310f4ada
C2: 185.23.253.143: 36731
The post New APT Group Actor240524: A Closer Look at Its Cyber Tactics Against Azerbaijan and Israel appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
*** This is a Security Bloggers Network syndicated blog from NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks. authored by NSFOCUS. Read the original post at: https://nsfocusglobal.com/new-apt-group-actor240524-a-closer-look-at-its-cyber-tactics-against-azerbaijan-and-israel/
如有侵权请联系:admin#unsafe.sh




















