2024-8-2 12:57:19 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
With the recent changes and regulatory shifts happening in cybersecurity, it’s no secret that the Cyber Resilience Act (CRA) is set to revolutionize cybersecurity standards across the European Union. This mandate calls for higher levels of protection for all products with digital elements, which has compelled organizations to reassess and adjust their strategies. As AI technologies continue to advance and organizations gear up for its official implementation, being prepared is crucial. According to the CRA, proactively integrating a “security-by-design” approach is essential to ensure compliance and safeguard against emerging cyber threats. We’ve seen how a single vulnerability in a product can rapidly escalate, potentially crippling an entire organization within minutes. While the average time to exploit such vulnerabilities is about 22 days, the exposure can persist from a few days to several weeks or even months, depending on the circumstances.
To gain a deeper insight into the impact of these changes, we partnered with Sapio Research to survey 500 cybersecurity decision-makers from large enterprises in the US and UK. Download the full report: 2024 Regulation vs. Reality: Are the Fed’s Attempts at Wrangling Incident Disclosure Effective?
Read on for a detailed look at the CRA and eight tips to help your organization prepare and stay ahead in the evolving cybersecurity landscape.
Industry Confidence and Preparedness
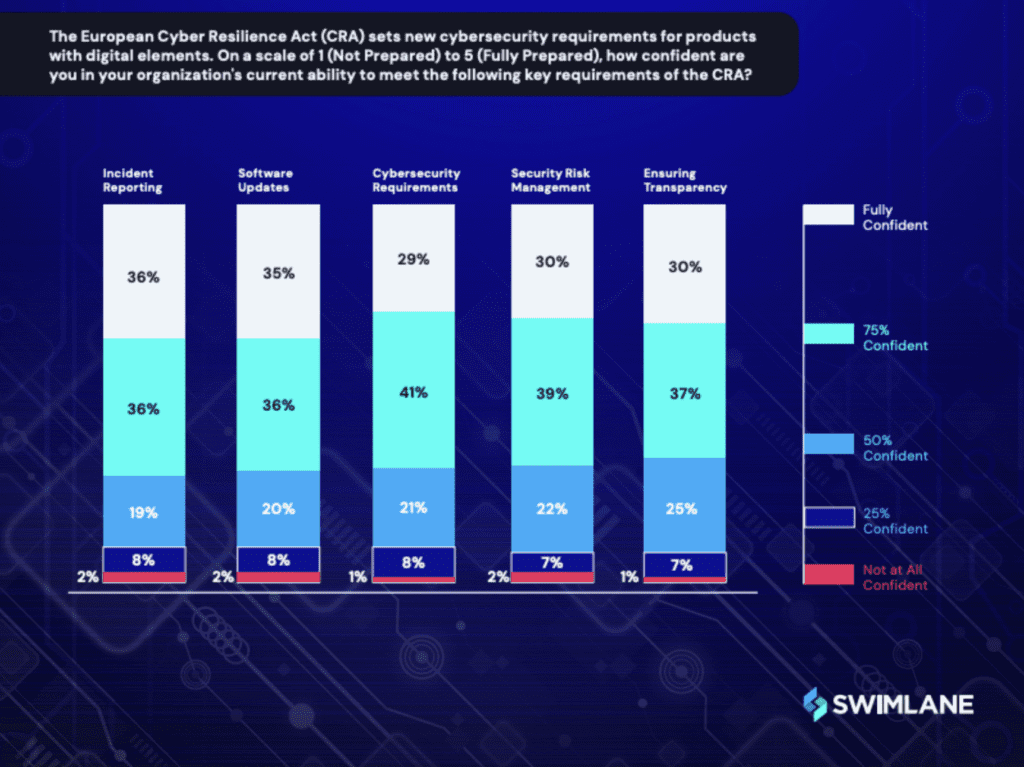
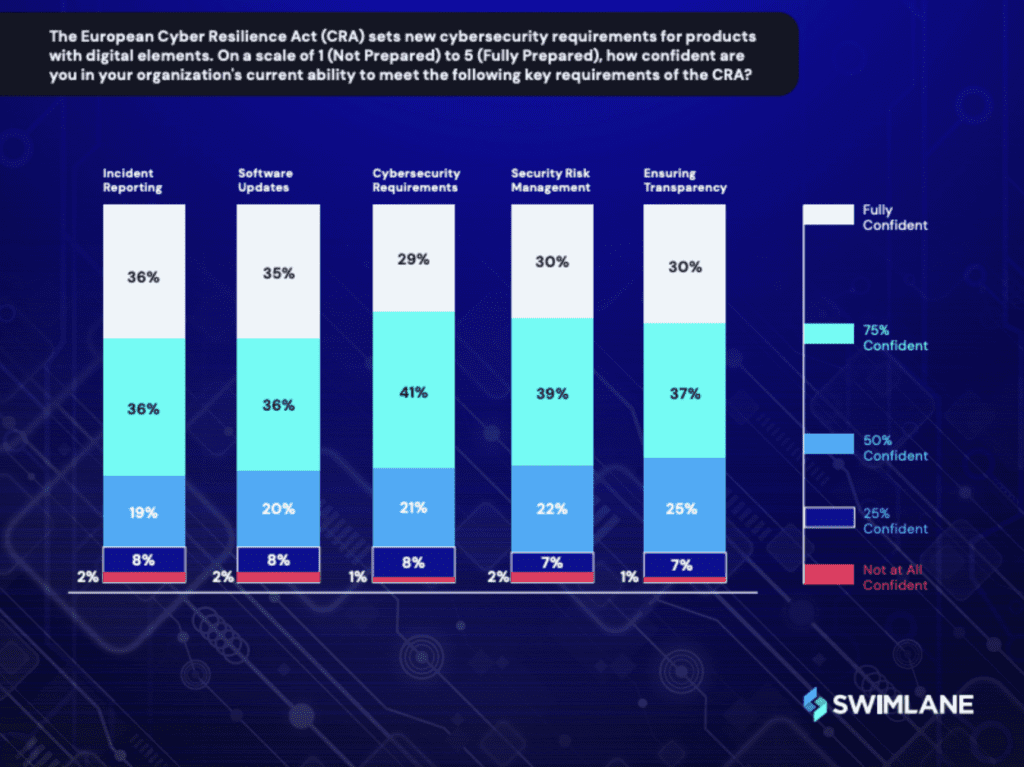
Despite the benefits of the CRA industry confidence in meeting its stringent requirements varies. Only about one-third of respondents surveyed expressed full confidence in their organization’s ability to comply with the CRA’s key mandates.While the majority of respondents indicated they were 75% confident or more, when it comes to governance, risk and compliance, organizations should never settle for less than 100% confidence. For example, the Ticketmaster data breach exposed 500 million users, highlighting that full compliance with the CRA isn’t just about meeting regulations, but crucial to protecting your organization’s digital ecosystem and managing risks accordingly.
Maturity models like ISACA’s CMMI, have helped organizations across various industries achieve sustainable business results. CMMI provides a framework for assessing and enhancing organizational capabilities and performance, with a product suite that offers best practices and a roadmap for optimizing key capabilities and benchmarking performance.
The Proactive “Security-by-Design” Approach
At the heart of the CRA is the principle of “security-by-design.” This proactive approach mandates that cybersecurity measures are not an afterthought but a fundamental aspect of the deployment and development lifecycle. From initial design to final deployment, every stage must consider and address potential security vulnerabilities. This strategy aims to mitigate risks before they become threats, ensuring a robust defense against various types of cyber attacks.
Tips for a Security-by-Design Approach
The path forward involves a thorough reassessment of their cybersecurity strategies and practices. Integrating the “security-by-design” approach requires a cultural shift and an investment in advanced security measures and technologies. It also requires ongoing education and training to ensure that all stakeholders, from developers to top executives, are aware of their SOC roles and responsibilities in maintaining cybersecurity. The CRA is a call to action for a more secure digital future.
Here are some tips for organizations to implement a “security-by-design” approach, ensuring robust protection and compliance:
- Embed Security from the Start: Integrate cybersecurity early in product design and collaborate with security experts to address vulnerabilities from the outset.
- Conduct Regular Risk Assessments: Continuously evaluate and update risk assessments to keep pace with evolving threats.
- Implement Robust Security Controls: Use strict access controls, strong encryption, and secure coding practices to protect data and systems.
- Automate Security Testing: Integrate automated testing tools into your CI/CD pipeline and use static and dynamic analysis to detect vulnerabilities.
- Foster a Security-First Culture: Provide regular training, promote a security mindset, and encourage reporting of security concerns.
- Maintain Compliance Documentation: Document security measures and maintain audit trails to demonstrate compliance with the CRA.
- Invest in Security Automation to Monitor and Respond to Threats: Implement an AI-enhanced automation tool to continuously monitor, respond, and keep an updated incident response plan to handle security incidents swiftly.
- Engage with Third-Party Experts: Conduct external audits and seek professional consultation to align with industry standards and regulatory requirements.
Swimlane’s AI-enhanced low-code security automation platform exemplifies this approach. By automating routine tasks and enabling quick integration, Swimlane Turbine lets security professionals concentrate on complex, judgment-driven issues. This boosts SOC efficiency and ensures organizations stay compliant and resilient against evolving cyber threats.
How AI-Enhanced Security Automation Can Help
The Cyber Resilience Act represents a major shift towards proactive cybersecurity, emphasizing “security-by-design” to ensure more secure products and organizations. Achieving compliance is crucial for true cyber resilience and protecting our interconnected world. AI-enhanced automation plays a key role in this transformation by streamlining security operation center functions, improving response times, and optimizing resources. Swimlane utilizes AI-enhanced automation in its security operations center (SOC) to tackle these challenges effectively.
Are the Fed’s Attempts at Wrangling Incident Disclosure Effective?
Download the full research report now to understand how these regulatory shifts are impacting security practices and compliance strategies. Read the report to learn more about how the regulatory environment is impacting cybersecurity strategies, priorities, and budgets.
如有侵权请联系:admin#unsafe.sh