A primer on how to best prepare for the migration to PQCThe United Nations has proclaimed 2025 the 2024-8-1 22:6:19 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
A primer on how to best prepare for the migration to PQC
The United Nations has proclaimed 2025 the International Year of Quantum Science and Technology—and for good reason. Across the globe, the quantum community is making monumental strides toward building stable, commercially viable quantum computers. As the vision of quantum technology entering mainstream applications solidifies, a palpable tension hangs in the air. Knowing that a large-scale quantum computer could effortlessly break today’s cryptographic algorithms like RSA, DSA, ECDH, ECDSA, and EdDSA and expose sensitive, confidential data is a looming nightmare for many CISOs.
The only hope for a secure quantum future lies in Post-Quantum Cryptography (PQC). PQC algorithms are being developed specifically to withstand quantum attacks, ensuring that data remains secure even with a powerful quantum computer. These algorithms are designed using mathematical problems that are believed to be resistant to quantum computing capabilities. The National Institute of Standards and Technology (NIST) has been at the forefront of this effort, leading a global initiative with the international cryptography community to standardize PQC algorithms.
As we already know, after three rounds of evaluation, NIST announced the first four algorithms in July 2022: CRYSTALS-Kyber for key establishment and CRYSTALS-Dilithium, FALCON, and SPHINCS+ for digital signatures. Additionally, NIST identified four more candidates (subsequently reduced to three now) for further analysis and evaluation in the fourth round.
According to NIST’s timeline, the standardization of all post-quantum algorithms is expected to reach the finish line this year (anytime now). This milestone is pivotal, as it will set the stage for organizations worldwide to begin the arduous yet essential process of migrating to post-quantum cryptography, as the PQC algorithms will be integrated into various standards and products worldwide.
PQC Migration Is Not a Mere Technical Upgrade; It Is a Fundamental Shift to a Whole New Generation of Cryptography.
Migration to PQC is a much more complex undertaking when compared to other cryptographic migrations from the past. The new PQC algorithms have significantly different properties from the current algorithms in terms of key sizes, signature sizes, key exchange, computational requirements, entropy, and others. Naturally, the challenges in migration are multifaceted, involving changes to infrastructure, algorithms, applications, and compliance frameworks. Organizations must plan extensively, ensuring that their systems are robust enough to handle the demands of PQC while maintaining seamless operations.
Given the threat of “harvest now, decrypt later” attacks and the estimated migration time for a small-mid size organization of 8-9 years, the need for immediate preparation is clear. Cybersecurity experts and analysts strongly recommend that security and risk management leaders start preparing for a move to PQC today.
AppViewX can help you implement crypto-agility and start preparing today for Post-Quantum Cryptography
As you start your post-quantum cryptography migration journey, here are eight critical factors you must consider to ensure a seamless and secure transition:
1. Bandwidth
PQC algorithms typically produce larger key sizes and longer signatures and ciphertexts than conventional algorithms, such as RSA and Diffie-Hellman.
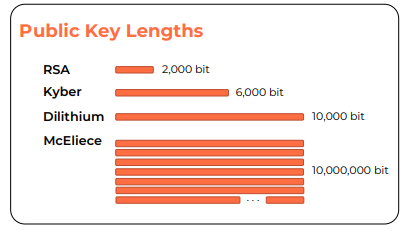
As stated in Eviden’s PQC Migration Guide – The Essentials – “The public keys of CRYSTALS-Kyber (6,000 bit) and CRYSTALS-Dilithium (10,000 bit) are several times larger than the ones of RSA and Diffie-Hellman (2,000 bit). Other proposed post-quantum algorithms even require hundreds of thousands of public-key bits more. The situation is not much different when it comes to private keys.”

As a consequence, data traffic and latency increase. To avoid the impact on network performance, you must ensure your network can handle the additional load. This might require upgrading your network infrastructure, optimizing data flow, and possibly increasing bandwidth capacity.
2. Storage
Again, as PQC algorithms come with larger key sizes, PQC certificates will require more storage space. You may need additional storage for maintaining hybrid and traditional cryptographic systems during the transition. Evaluate your existing storage solutions and plan for expansions to accommodate the increased data volume. Ensure that your data backup and recovery systems can manage the larger volumes efficiently.
3. Protocols
Existing communication protocols, such as TLS, SSH, S/MIME, and IPsec, must be updated to support PQC algorithms. This includes configuring the existing protocols to use PQC algorithms for key exchange and signature mechanisms. Do a comprehensive review of the existing protocols, conduct rigorous testing, and plan for any changes to the underlying infrastructure to ensure secure communication.
4. Application/Software Upgrades
The transition to post-quantum cryptography requires significant updates to software and applications as they need to support PQC algorithms and new
cryptographic standards. Existing software may require extensive modifications to ensure compatibility with PQC libraries and protocols. This process can be complex and time-consuming. Start by building a comprehensive inventory of existing cryptography and associated applications and software. Identify mission-critical assets that need to be migrated on priority. Thoroughly test and validate PQC algorithms in these entities to prevent service disruptions and ensure security.
5. Hardware Upgrades
Post-quantum cryptography can impose greater demands on processing power, necessitating hardware upgrades. You may have to invest in new servers and processors that can handle the increased computational load and specialized hardware accelerators to optimize performance. Additionally, you may have to update or replace hardware security modules (HSMs) that currently support classical cryptographic algorithms with models supporting post-quantum algorithms. First, build a thorough inventory of your current hardware and classify components involved in critical data protection for immediate upgrades or replacement.
6. Third-Party Applications and Services
If your organization relies on third-party vendor technology, applications, and services, such as email and VPNs, you must ensure that they support post-quantum cryptography. Engage with your vendors to understand their PQC integration roadmap and timelines. Work with them to get new products/applications delivered with PQC built-in and legacy ones upgraded with PQC. This collaboration is essential to address the performance impact and interoperability issues that may arise during or after PQC migration.
7. Standards and Guidelines
Compliance with emerging PQC-related RFCs, standards, and guidelines will be a crucial step in the transition process. You will need to integrate and maintain up-to-date PQC libraries and random number generators (RNG). So, stay abreast of emerging standards from bodies such as the National Institute of Standards and Technology (NIST) and the European Telecommunications Standards Institute (ETSI). Adhering to these standards ensures interoperability and security across different systems and platforms.
8. Regulatory Compliance
Regulatory bodies will likely update compliance requirements to include post-quantum cryptographic standards. You will need to ensure that your cryptographic practices align with new regulations and standards related to PQC. This involves updating compliance policies, conducting regular audits, and maintaining documentation to demonstrate adherence to post-quantum security standards. Stay informed about evolving regulations and make necessary amends in your security practices to avoid compliance issues.
PQC Migration Solutions from AppViewX
To facilitate a seamless and efficient transition to PQC, AppViewX offers the following solutions:
- AppViewX PQC Test Center: A dedicated free online resource built to help organizations assess their PQC readiness by generating and testing quantum-safe certificates prior to their integration into existing systems, workloads and machines. You can quickly set up your own quantum-safe PKI hierarchy and generate PQC ready certificates and keys to test their compatibility in your environment.
Visit the AppViewX PQC Test Center and begin your PQC journey today. - PQC Certificate Lifecycle Management: The AVX ONE platform offers a comprehensive certificate lifecycle management solution to help enable PQC readiness and crypto agility with complete certificate discovery and inventory, full certificate lifecycle automation, and total certificate control across the enterprise.
The transition to post-quantum cryptography (PQC) is inevitable. As the countdown to the final round of NIST’s PQC standardization starts, it is time to start getting quantum ready. As NIST’s Matthew Scholl said: “It’s no time to panic. It’s time to plan wisely.” Investing time and resources now in strategic planning and leveraging solutions like those offered by AppViewX can help greatly resolve the challenges along the migration journey and be secure in the quantum era.
*** This is a Security Bloggers Network syndicated blog from Blogs Archive - AppViewX authored by Krupa Patil. Read the original post at: https://www.appviewx.com/blogs/8-essential-considerations-for-post-quantum-cryptography-migration/
如有侵权请联系:admin#unsafe.sh