2024-8-1 17:46:35 Author: labs.yarix.com(查看原文) 阅读量:8 收藏
Reading Time: 13 minutes
Introduction
As Yarix Cyber Threat Intelligence (YCTI) team, we keep a close eye on and track phishing and scam campaigns on a daily basis. Protecting the reputation and image of client companies is one of the main goals of YCTI’s Brand Abuse team. This includes determining whether and how their officially registered trademarks are being used to spread fraudulent campaigns that deceive people into divulging their personal and financial information in what are known as “fake shops”.
Fake shops are scam websites designed to imitate a legitimate online store, often of well-known brands. They entice users with discounted goods, but after payment is made in advance, the products are never delivered. For this reason, we monitor daily to see if any newly registered domains could be used for phishing or scam activities.
Tracking and analyzing as many malicious infrastructures as possible in the early stages is one of the aims of our team, in order to compare their efficacy and proactively identify similarities ahead of time.
While investigating these kinds of websites, we discovered something quite intriguing: generally, based on the type of phishing kit or Threat Actor that initiated the campaign, we are able to determine, upon first glance, whether or not we have previously dealt with that kind of questionable site. In this instance, a number of them had the exact same layout, different from other websites we had already tracked. At that point, we really got into those sites.
Bit by bit, we found out that Threat Actors were using legitimate Chinese e-commerce platforms, such as SHOPOEM, to create phony websites that falsely used the official Trademarks of famous retail businesses to deceive people all over the world.
By making advertisements to market deals and discounts on social media platforms like Facebook, Instagram, and others, the Threat Actors might take advantage of these platforms and redirect users to bogus websites.
This blog article aims to explain the modus operandi of this widely used campaign, including how Threat Actors operate and why this type of operation is both risky and very successful.
Overview
As previously said, we monitor daily the registration of newly registered domains to detect as soon as we can if some could potentially be used for phishing activities or scam campaigns.
In fact, during our activities, we were investigating a dubious domain that posed as the official online store of a well-known fashion brand. It was offering goods at an absurdly low price, with up to 90% off. After examining the domain, its creation date and information contained in its Whois record, it became evident that the website was a copy of the fashion brand’s original online store.
As you have understood so far, we sadly come across a lot of fake shops every day. Sometimes they have a distinct structure, whereas other times we see a particular pattern that is utilized to replicate different ones. That pattern is what makes us happy – like, big smiles happy – and lets us realize that those sites are probably made by the same Threat Actor(s). So, now is the right time to begin our more thorough investigation.
Hereafter are two examples of what a fraudulent website might look like:

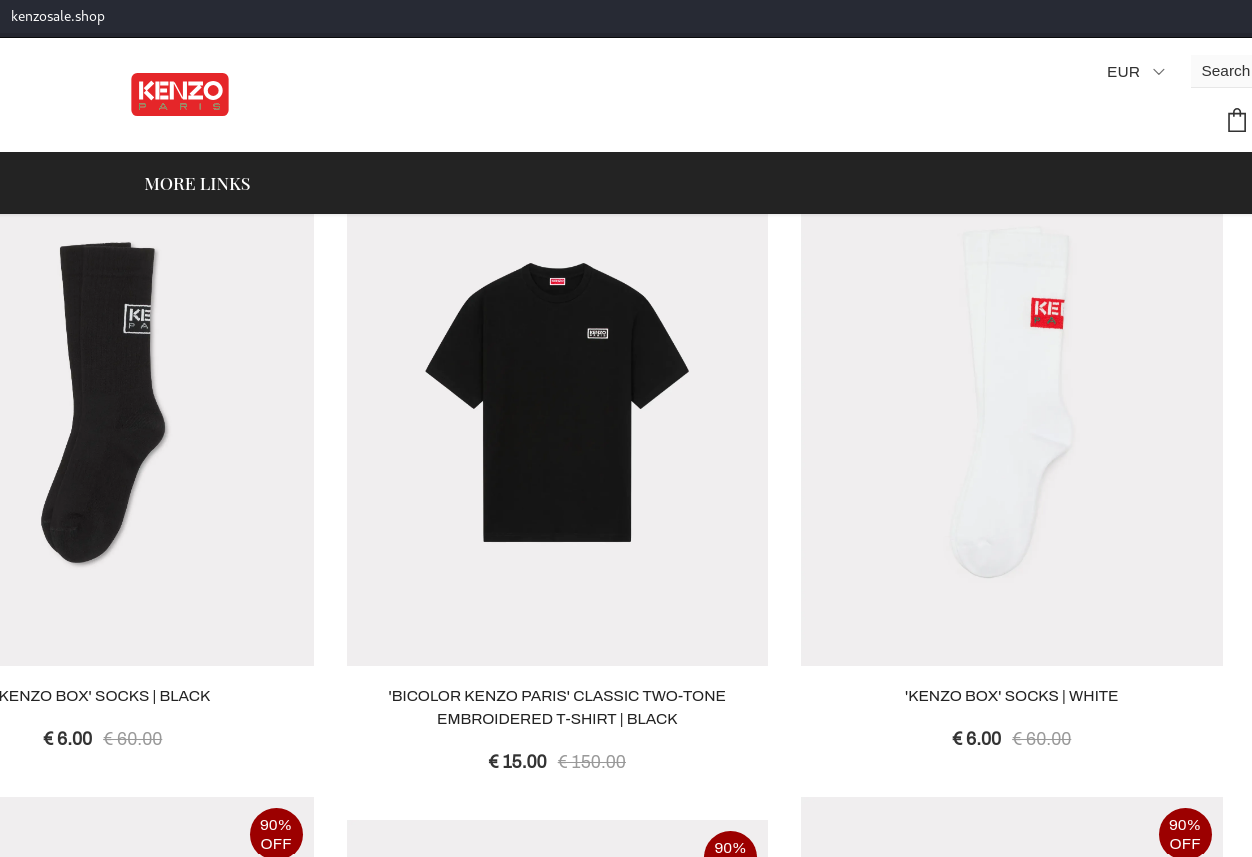
Are they familiar? These days, it is not that hard to come across clone websites and fraudulent stores. It is most likely one of the simplest methods Threat Actors use to take advantage of people financially. Using their shiny, deeply discounted websites, they entice users – frequently succeeding in doing so – given that anyone is drawn to deals, right? Threat Actors are well aware of it as well! And, let’s be honest, it is not always that simple to distinguish a fraudulent website from the real one, isn’t it?
The Investigation
We may now proceed to discuss how we ultimately looked into the matter, having demonstrated that it is easier than we imagine to be duped.
Once we encounter the same pattern used for various fake online shops, we examine the distinctive characteristics that we can subsequently link to the same Threat Actors and how they utilize them to propagate the fraud whenever we come across the same pattern utilized for numerous phony web stores.
It was challenging to continue the study in this instance in particular because a large number of the sites appeared to be undergoing maintenance. Well, needless to say, we didn’t give up. As a result, we found that it was a façade employed by the Threat Actors, and that if we visited the websites using a different user-agent, such as a smartphone, we could actually see the fraudulent content:


When we browse the websites, we frequently focus on the “Contact us” part since this is where Threat Actors usually leave email addresses they created specifically for the campaign, which they then use as customer service contact of the targeted brand.
We have examined nearly 14,000 bogus domains detected in the last two months as part of this campaign and over 1800 email addresses established by the Threat Actors and reported in these websites have been found.
Some of the email addresses the Threat Actors created for this campaign that have been discovered thus far are listed below:
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
Even if the e-mail addresses are meant to be for customer care, the majority of them does not have an active mail server (MX record), which prevents them from receiving emails.
By examining the website’s html code, we were able to determine that the Threat Actors were hosting their new websites on CDNs (Content Delivery Networks) where they probably also managed their database.
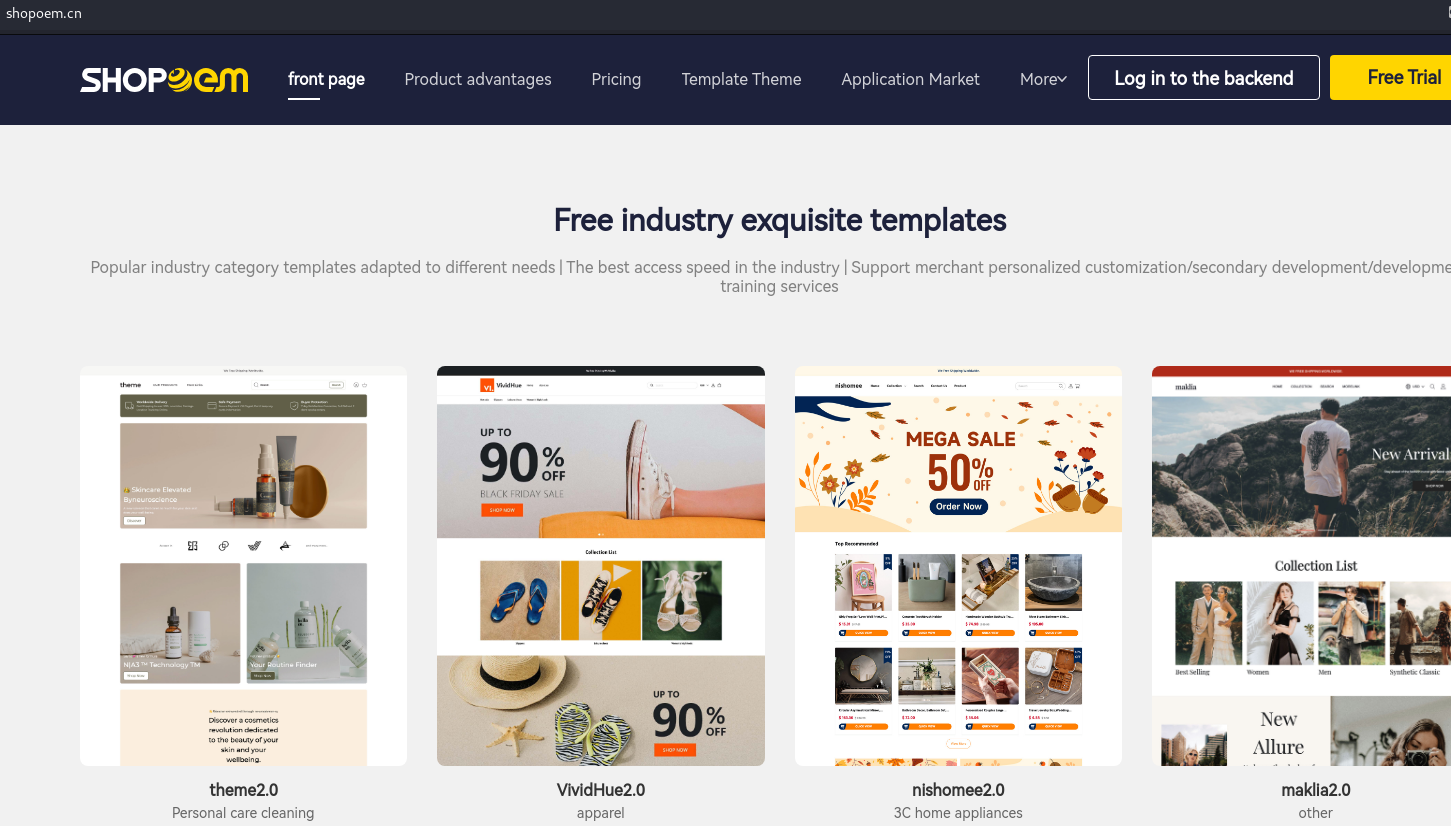
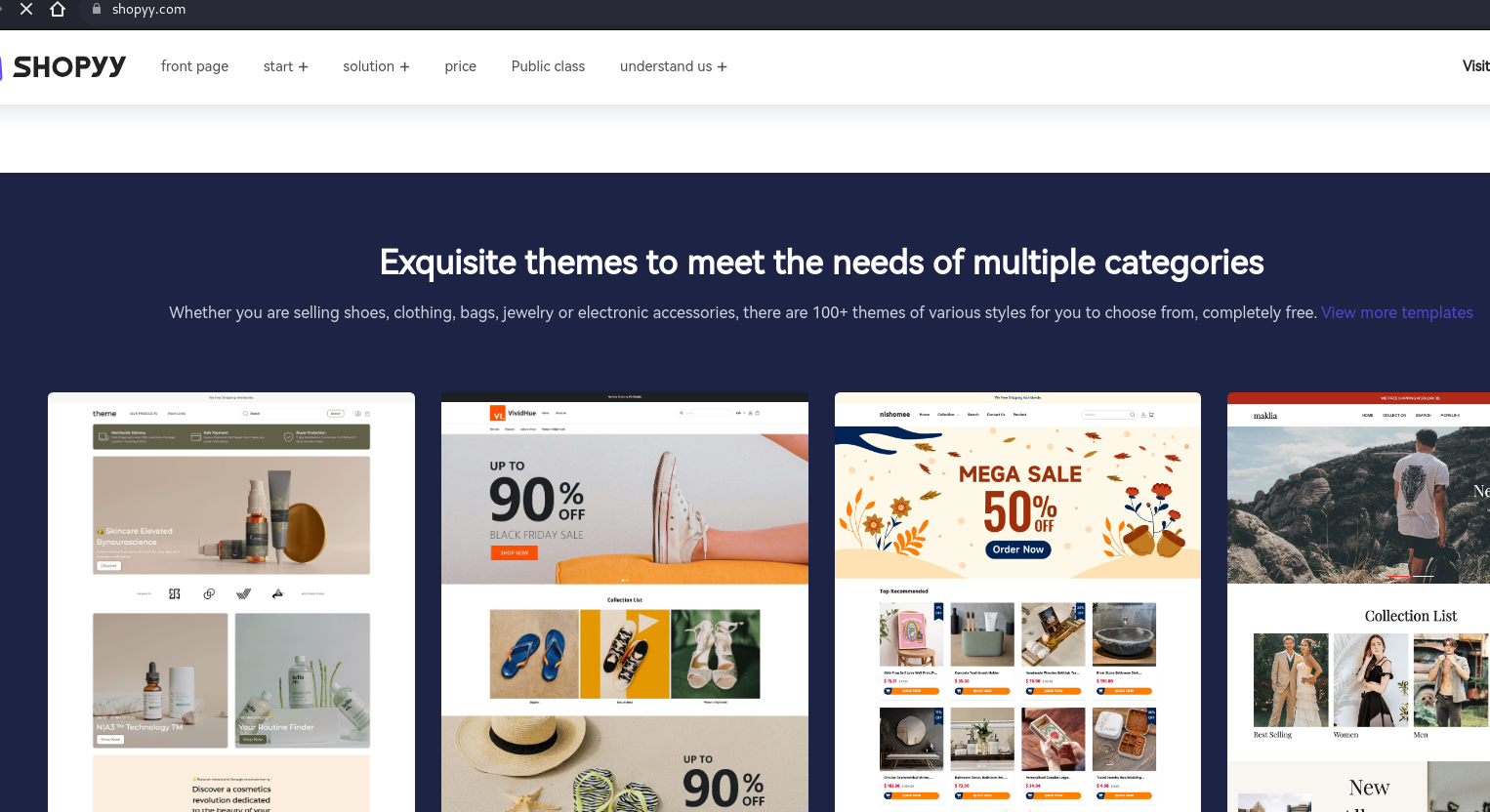
These CDNs are connected to the Chinese e-commerce platform SHOPOEM, which allows customers to register, develop custom websites, and choose from a variety of site themes. The Shopoem platform seems to have links to other platforms – listed below – that appear to be part of the same infrastructure
The two sample screenshots below illustrate how major Chinese e-commerce companies’ websites offer the same templates for building a personalized online store:
Furthermore, as demonstrated by the following example, the admin interface of the sites appears the same on all platforms where the account is registered:
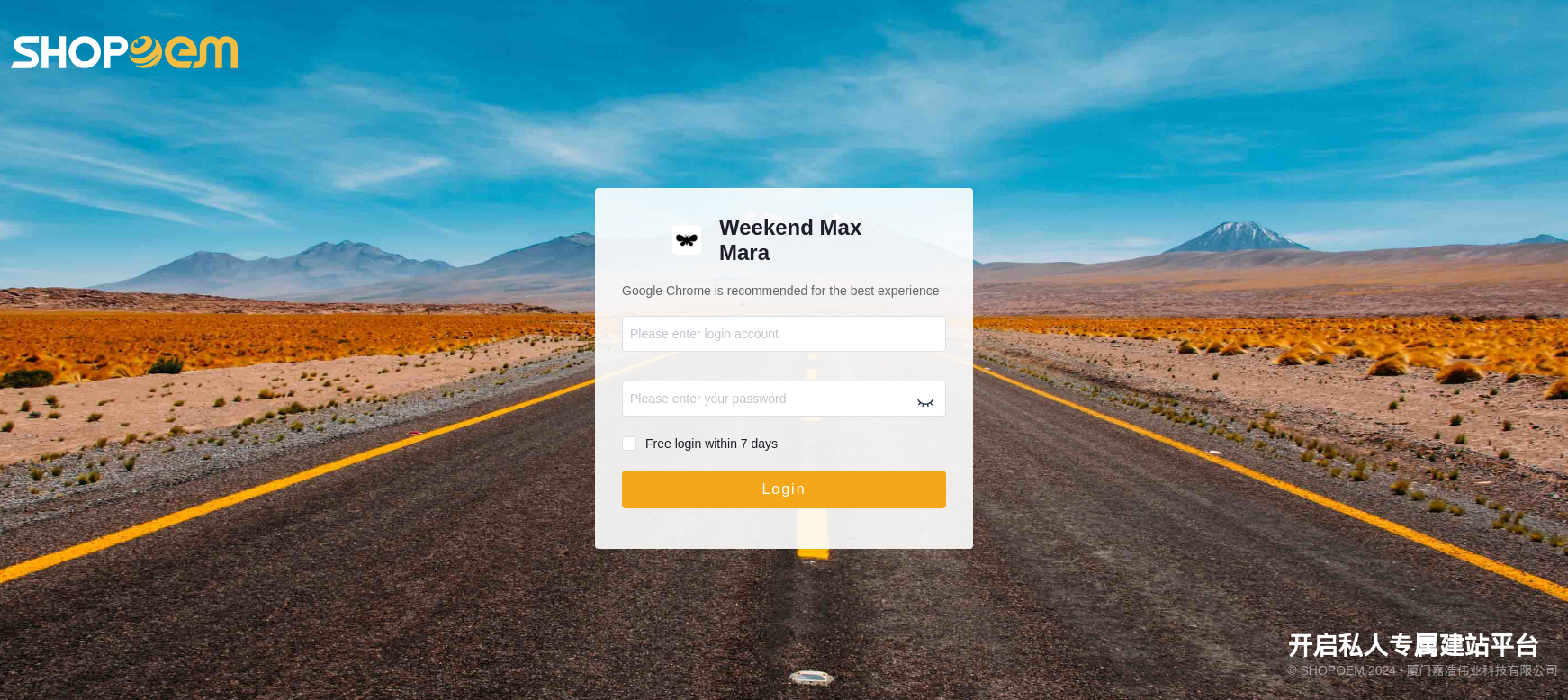
By registering for an account on the Shopoem platform, you can alter the features and configuration of your site(s), as well as manage its exposure and efficacy:
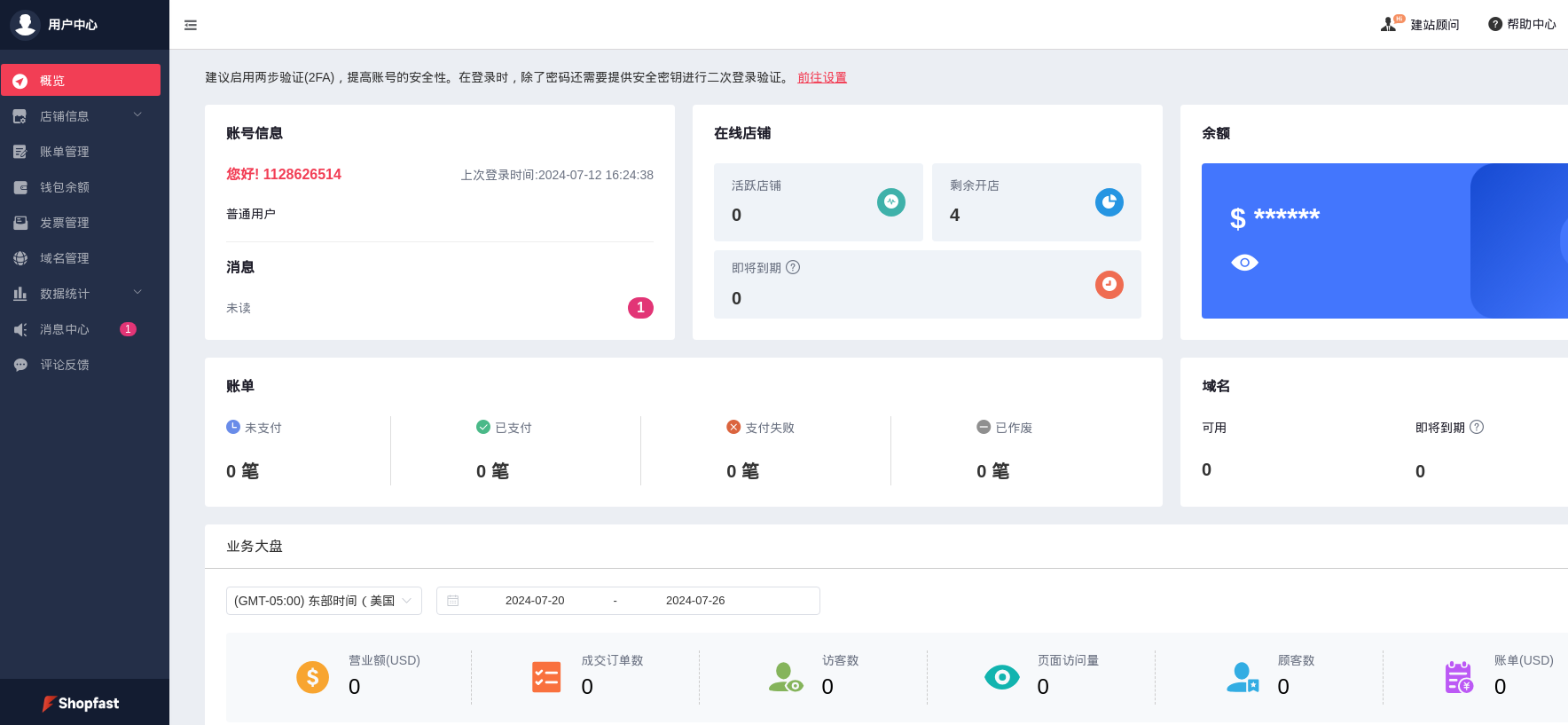
We found through OSINT research that users can be led to one of the other linked platforms, regardless of the platform they register on.
This is a list of websites that we have reason to think they are all part of the same infrastructure based on the way their page structures are organized, how they offer the same templates for starting personal online stores, and how their “about us” sections essentially contain the same information:
- shopiass.com
- shoplinks.com.cn
- myshoplinks.cn
- shopoem.cn
- shopoem.com
- shopfast.cn
- shopyy.com
- saasoem.cn
- shoplinks.cn
- haitunlink.com
- b.shopyy.com
- shopname.cn
- oemsaas.vip
- iadminshop.cn
- staticym.com
- staticswe.com
- staticsoe.com
- staticyy.com
- oemcartapp.com
- staticswin.com
- staticszh.com
On certain of these platforms, visitors can only browse the main page, while attempting to navigate a particular other section results in a 404 error message.
Additionally, we have identified Chinese blog sites that provide instructions for building a customized SaaS architecture, recommending Shopoem and its associated platforms as better options and offering guidance on maximizing their potential.
To make it even more juicy, we have come across articles – possibly written by the same site owners – that describe precisely how to sell online counterfeit goods from overseas without running into many issues with network restrictions and domain shutdowns.
The previously mentioned Shopoem platform is one of the recommended tools, along with social network marketing, AB-CLOAK solutions for payments and traffic management, and other technologies.
These traits match the ongoing scam effort that we are dealing with, though this could just be a coincidence.
Even if the aforementioned platforms and CDNs in general are not malicious, they appear to be extensively utilized to produce phony websites that are then used to disseminate scam campaigns. Thousands of distinct genuine retail businesses’ clone or phony websites have been seen to be hosted and shared nearly solely by these CDNs.
Below, the list of CDNs so far located:
- cdn.staticsoem.com
- cdn.staticsoe.com
- cn01-cdn.staticsyy.com
- cdn.staticsim.com
- cdn.staticswin.com
- cdn.staticszh.com
- cdn.staticswe.com
- cdn.shopycdn.com
- cdn.statics-cdn-abc.com
- cdn.statics-flys.com
- cdn.statics-cdn-nbcloud.com
- cdn.statics-yiyang.com
- cdn.statics-cdn-im.com
- cdn.staticsuee.com
- cdn.staticsaa.com
- cdn.staticscc.com
- cdn.staticsbb.com
- cdn.statics-cdn-amz.com
- cdn.nicestatic.com
- cdn.staticscd.com
- cdn.assetorz.com
- cdn.prshopimg.com
- cdn.shopide.online
- cdn.statics-cdn-go.com
- cdn.shopysimg.com
- cdn.shopidetoday.com
The Analysis
Now that we know Threat Actors are building malicious websites using legitimate platforms and their site design, it is time for us to turn our attention to the sites themselves and conduct a more thorough internal structure analysis.
To illustrate the procedures used to go deeper into the investigation, let’s use the fictitious online store weekendmaxmarait.com as an example.
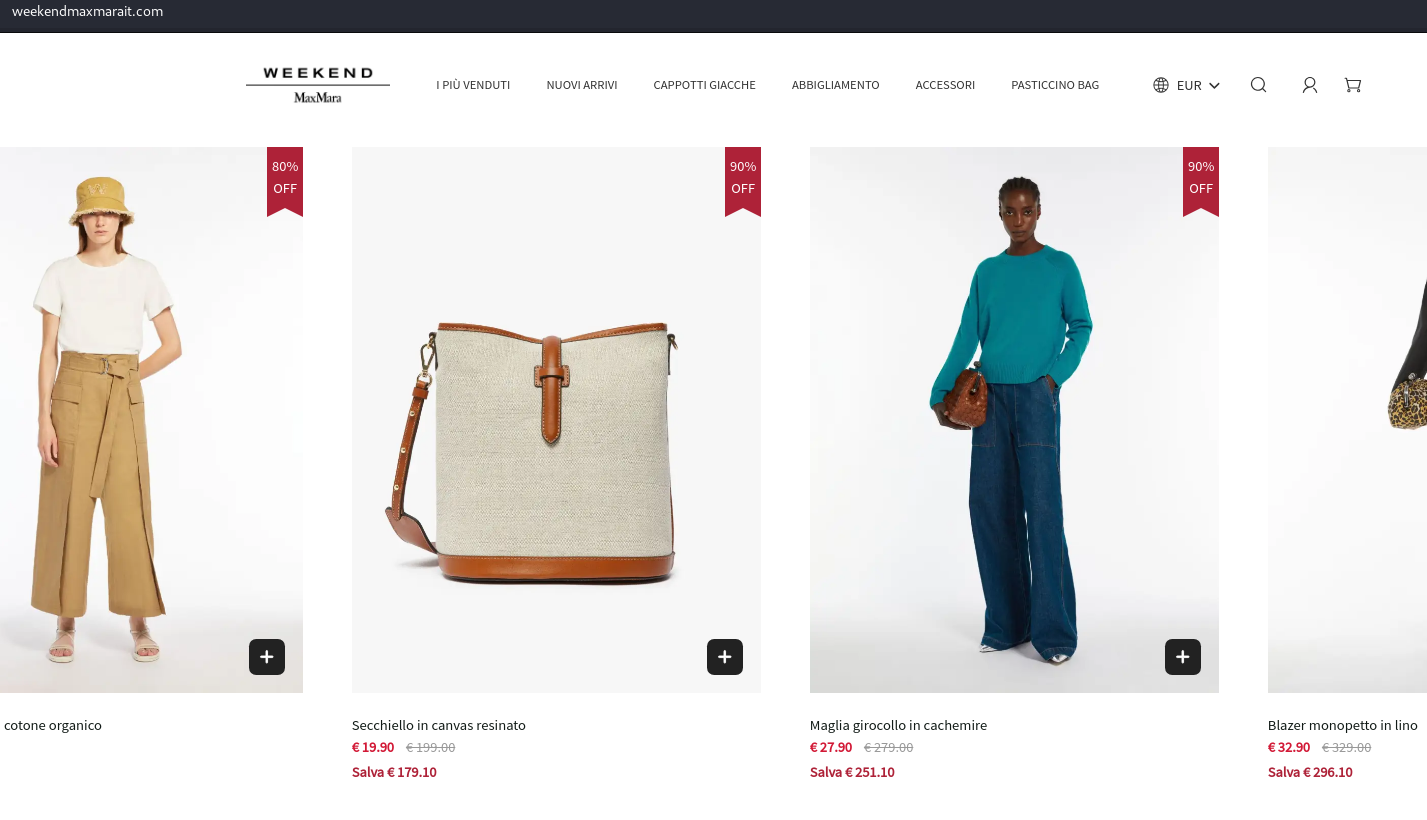
On May 23rd 2024, the domain was created. We can see the domain was registered by a Chinese registrant by looking at the Whois record data. Regretfully, more details on the domain owner were shielded by privacy laws set forth by the recently adopted European privacy Directive (i.e. GDPR).
Examining the domain’s html code reveals that it does not match the features of the original Italian website (www.maxmara.com .)
On the contrary, we note that some sections refer to oemcart and others reroute to cdn.staticsaa.com:
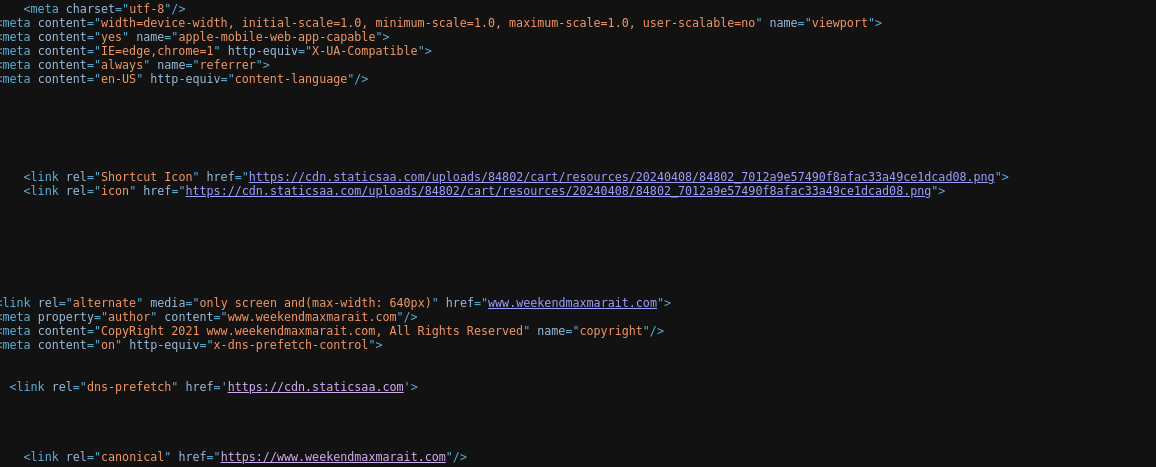
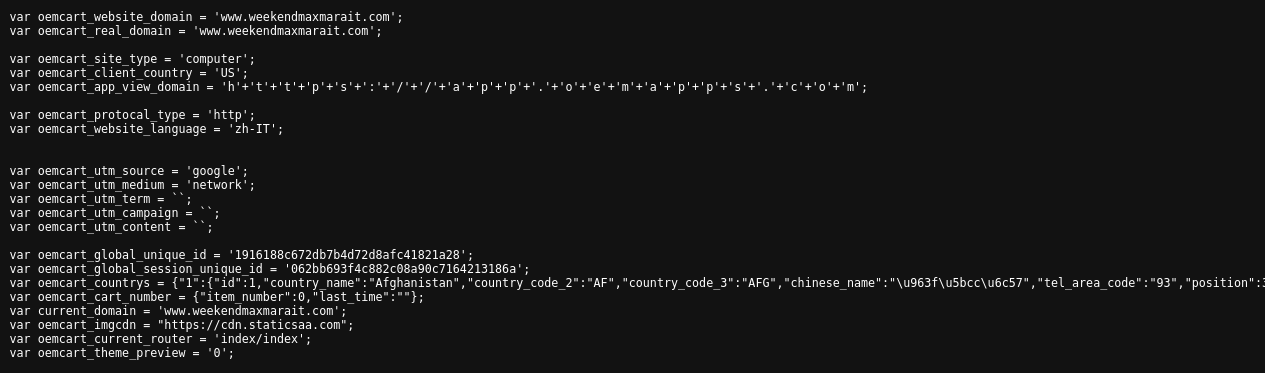
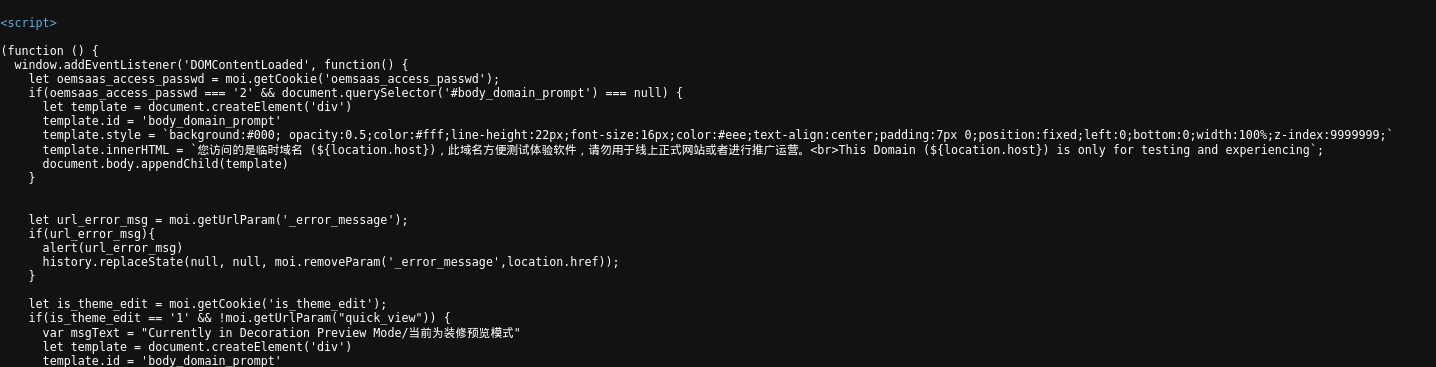
We presume that “Oemcart” may be a function that Shopoem and its affiliated platforms have built into the coding of the template sites that they provide.
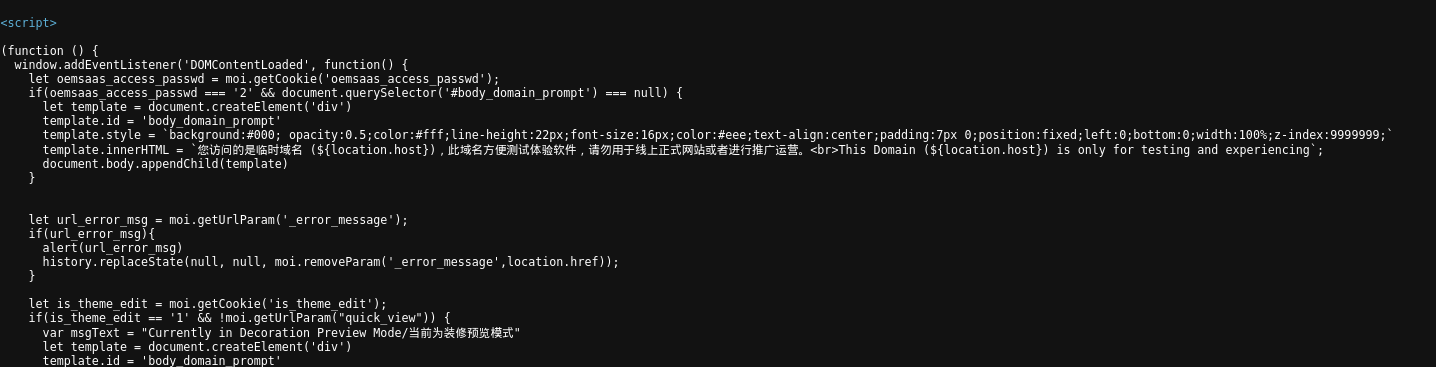
Scrolling down the code, we find a few Chinese sentences that translate the text that appears when a user opens the website in their browser (“This domain is only for testing and experiencing“):
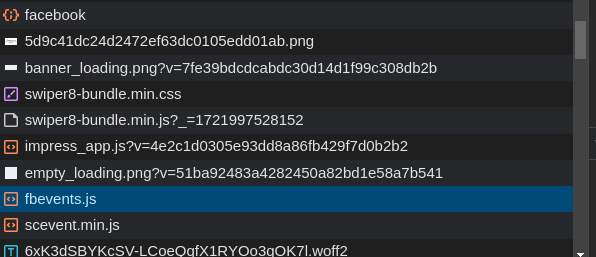
Upon further examination of the requests sent by the website, we found that it calls a valid script named “fbevents.js”, which is connected to Facebook Pixel event tracking and was created by Meta. This script seems to track an advertising campaign’s effectiveness so the owner may keep an eye on the trend on meta platforms.
EUREKA, I thought! This could actually demonstrate that the Threat Actors might be using social media to reveal the harmful campaign and monitor meta platforms for information, such as the number of users who visit the site, the number of sales made, etc.
After gaining a better understanding of the campaign’s development, we looked more closely at the CDNs. We were able to locate the first registered CDN back to March 2022 using Urlscan and other cutting-edge OSINT and scanning tools, indicating that the Threat Actors have been running this fraud for two years. The last CDN we tracked is as recent as July 2024.
The timeline for the CDNs’ domain creation, which runs from March 2022 to July 2024, is displayed in the chart below:
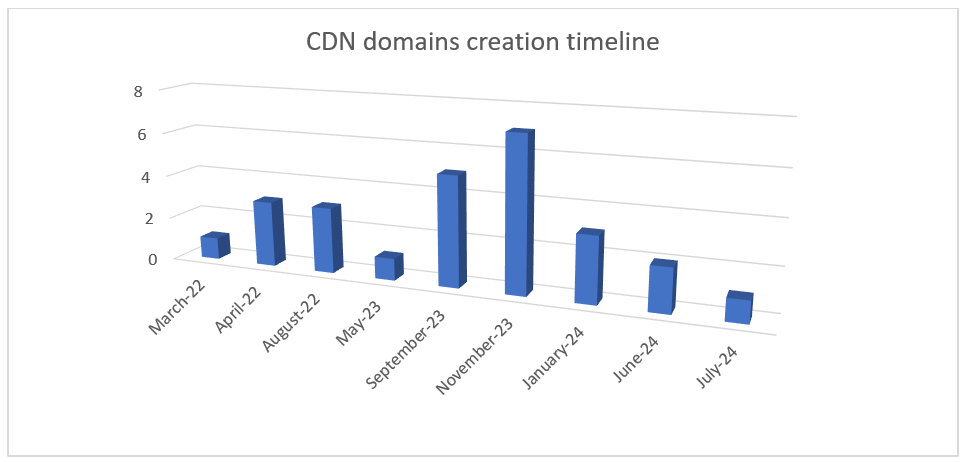
Here are the detailed creation dates and domain names of the CDNs, to be more precise:
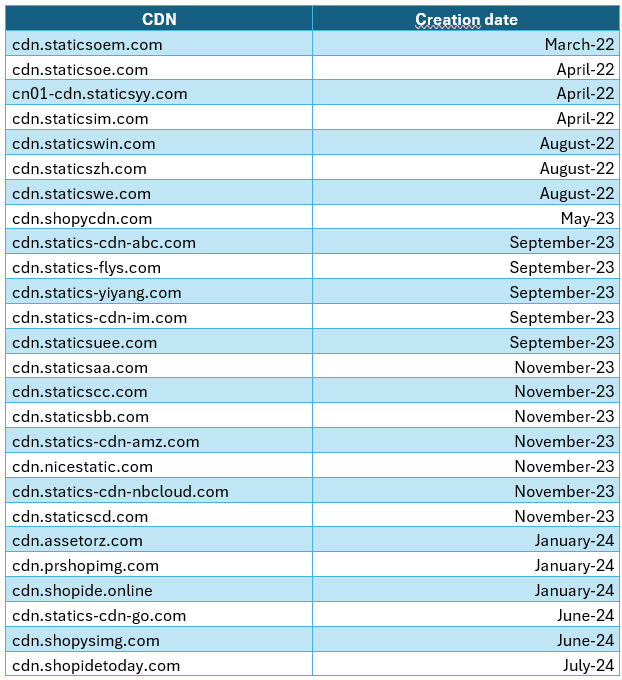
As can be seen, in 2023, the activity has increased. The various CDNs’ domains appear to have been developed throughout distinct time frames that either slightly preempt or align with holidays (like Christmas and Easter) and shopping seasons (like Black Friday and seasonal deals).
We haven’t been able to locate the Threat Actors’ network as of yet because they use the Cloudflare proxy service to conceal the infrastructure they are utilizing.
Furthermore, the fact that the Threat Actors alter the content delivery network (CDN) where the domains are hosted and make it harder to access the content further demonstrates their skill and organization and makes it more difficult for researchers, analysts, and targeted companies to track and suspend the scam domains.
Victimology
Every discovered CDN hosts from hundreds to thousands domains, most of which contains fake content. This indicates that the Threat Actors are illegally utilizing the trademarks of well-known retail companies (e.g., logos, goods, photos, etc.) on thousands of fraudulent websites to trick customers into disclosing sensitive financial information in order to profit financially.
We have traced the start of this campaign back to 2022, as we originally stated. We have chosen to focus the victimology analysis on the last two months of activity – from May 1st 2024 to July 7th 2024 – due to the massive volume of data.
About 14,000 domains related to this infrastructure have only been detected in the last two months; the top fifteen registrars that the Threat Actors utilized to establish fictitious domains are shown in the accompanying table.
The vast majority of these domain names were registered using Alibaba Cloud, an ICANN Accredited Registrar. As you can see, over half of all domains are registered with the top fifteen registrars:
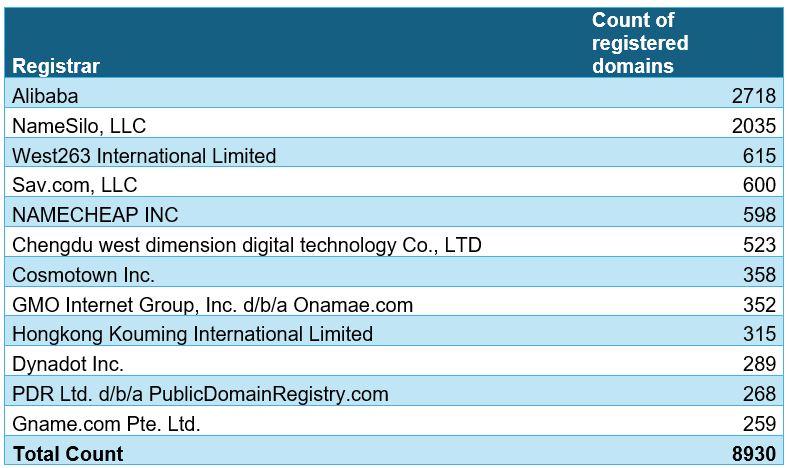
Our telemetry indicates that the fashion industry is the most affected by this malicious campaign, since it targets over 80 well-known fashion brands, the majority of which are based in Western nations and are mostly well-known American and European firms.
The domain name and the website’s HTML response, which contain terms associated with a certain industry sector, have formed the basis for the research.
Many of the domains had no reference to specific brands, were unreachable/redirects or shielded by Cloudflare proxy, and as a consequence, were untraceable. According to the statistics provided, we have categorized them as “Unknown.”
The first 30 identified more impacted brands are displayed in the following chart:
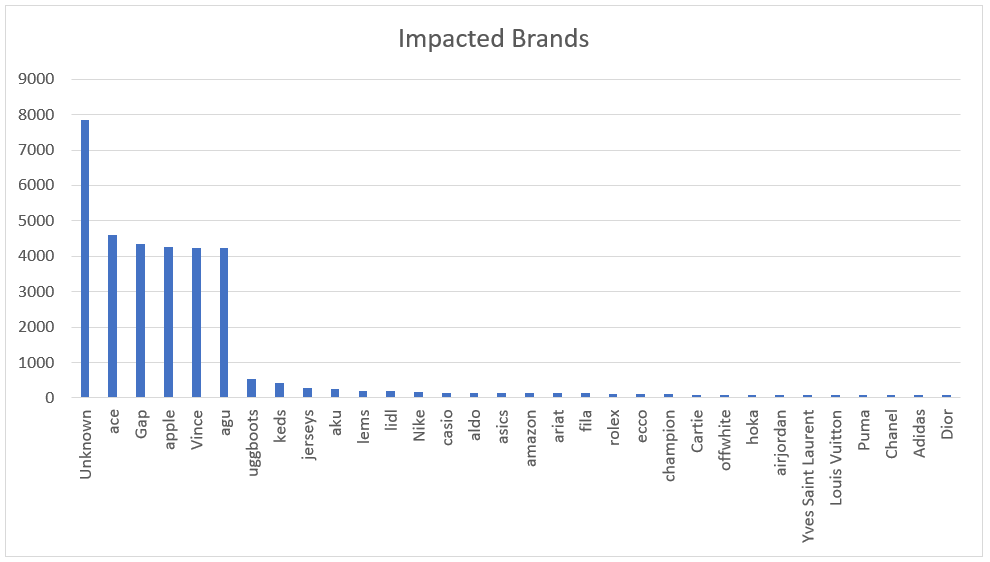
As you can see, the “unknown” classed domains represent about half of all the evaluated domains with over 7,000 websites. As previously predicted, one of the causes is that a large number of domain names just identify the industry in which the goods are sold, rather than mentioning any particular brand.
The majority of the websites actually “sell” a variety of goods, much like there are numerous kinds of stores in outlets. However, the Threat Actors frequently utilized specific keywords – such as “home,” “sport,” “merchandise,” etc. – possibly to hint at the kinds of products visitors may find on the websites. The chart below displays the most popular keywords that were found:

The figures only include the brands we were able to identify because of the large number of redirect domains. Redirect domains are simply generic domain names that point to specific ones.
Useful Tips
The following are a few brief suggestions that could be useful in identifying phony stores.
First tip:
Always pay close attention to the domain name of the site you are visiting. It does not come as a given that you are safe if you are an online shopaholic who frequently visits your preferred store. But what does pay attention to the domain name mean? For instance, let’s say you see a Nike advertisement and you need to buy shoes. You look around the website and notice deals. That is pleasant, isn’t it? You should now confirm that this is the official Nike website. It is possible that a Threat Actor developed a website strikingly identical to the original Nike website, nike.com.
Examining the domain, you discover that the domain is actually shoesnike.store.
Now, you may quickly check its WHOIS information by using WHOIS lookup resources such as centralops.net, whois.domaintools.com, and others. These can help you determine WHEN and BY WHOM the domain has been registered, as shown in the screenshot below:
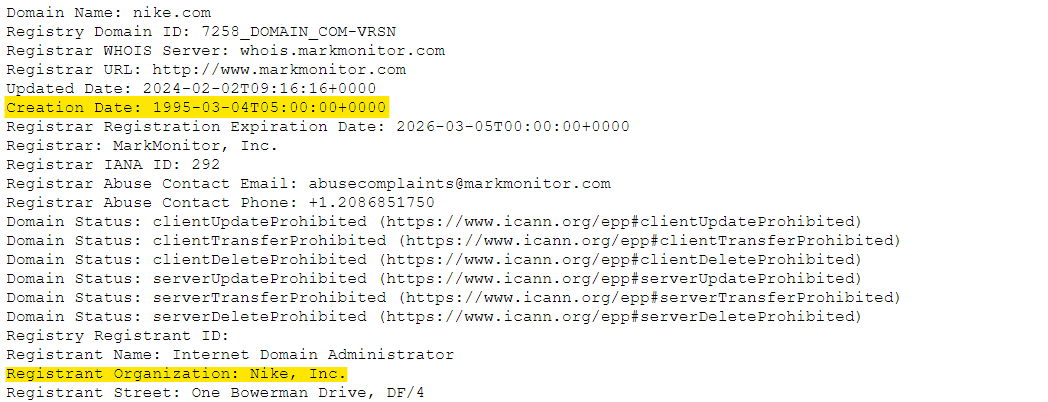
As you can see, Nike Inc. registered the domain name more than 30 years ago; just to be clear, the registrant (i.e. nike Inc. as of this example) is the domain owner.
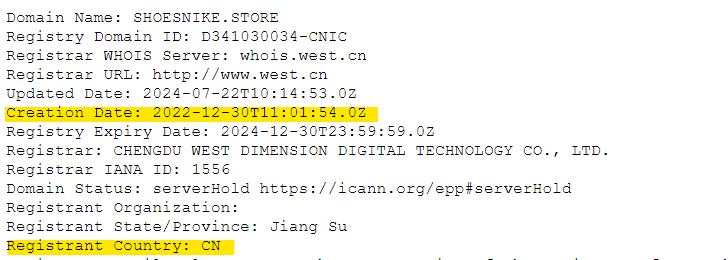
The next screenshot, instead, shows the WHOIS record of the fraudulent domain, which was created two years ago by a registrant located in China:
Second tip:
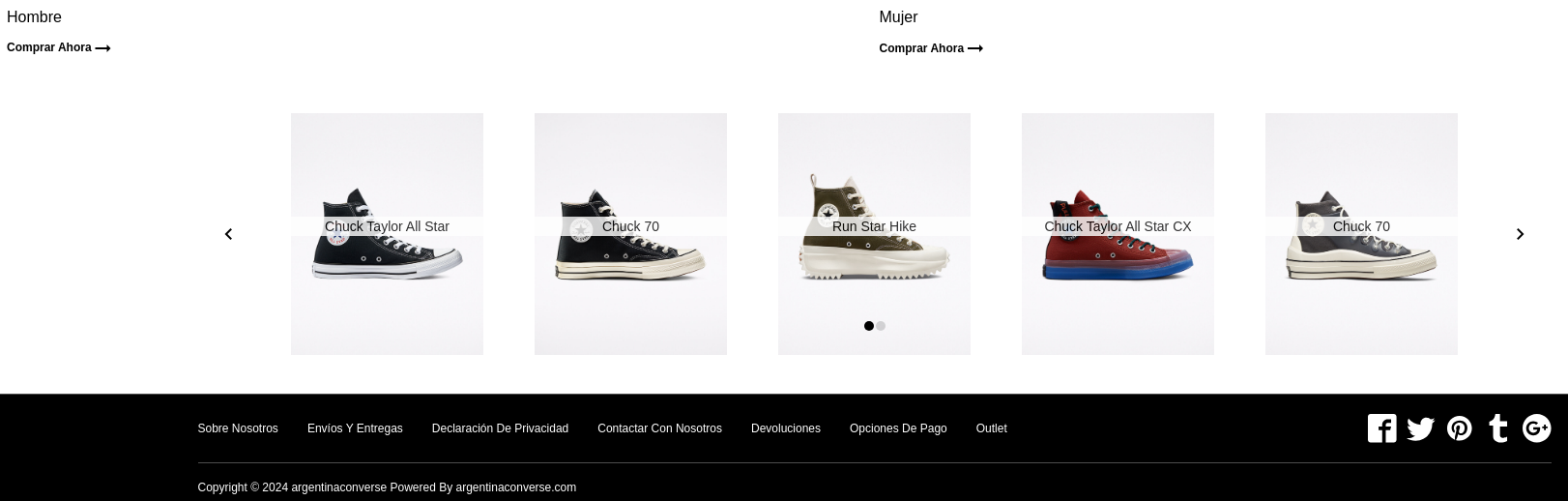
Pay attention to the details about the company that are provided on the website, such as the VAT number or contact details. Online retrieval of this kind of data is simple.
Scam sites typically do not provide firm information; instead, they use generic email addresses (gmail.com, mail.com, etc.) or phony official brand domains that are intended for malicious purposes such as phishing or scam campaigns, IF there is contact information available. The screenshot below displays a standard fake shop’s footer page with no information about the business:
Third tip:
Check the store’s and/or the website’s reputation; perhaps a report has already been filed. Online retailers and e-commerce platforms are proliferating these days, with some being more well-known than others. It is a very good idea to read the reviews of any online store you come across if you are unfamiliar with it. It is likely that users or review organizations have already given it a thought.
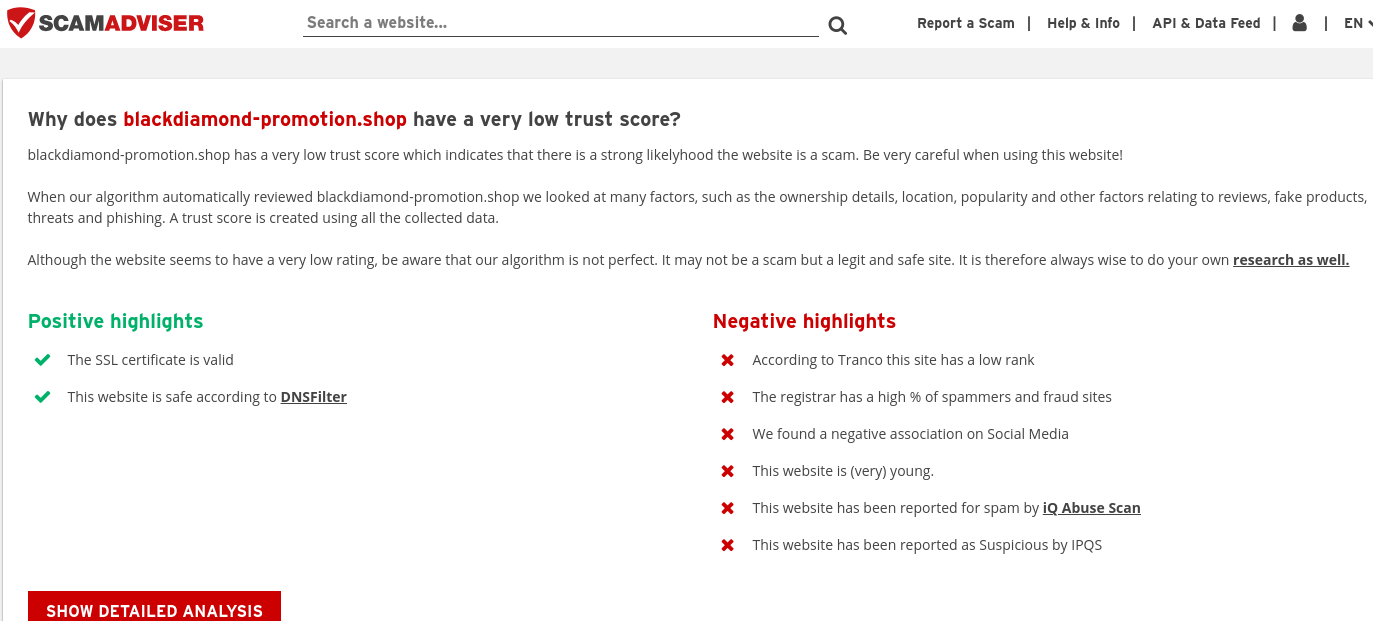
Using blackdiamond-promotion.shop, a fictitious store made specifically for the campaign under analysis, as an example, you may immediately determine the website’s reliability by looking up reviews.

ScamAdviser and similar websites help customers avoid scam sites by evaluating them and providing a thorough analysis of the problem, as exemplified below:
Conclusion
These days, the Internet is a magical place where anyone can accomplish anything they want to, whether it be for legit or fraudulent purposes.
It is crucial to understand that ransomware demands and Internet blocking are not the only effects of cyberattacks; phishing scams and fraudulent online stores are also increasing and becoming more and more sophisticated due to artificial intelligence, making it harder to identify them.
For this reason, I hope that both outsiders who happen to stumble onto this paper and security researchers following down a fresh fraud campaign will find it useful.
Author
Caterina Pesce is a member of the Yarix Cyber Threat Intelligence Team. She holds a master’s degree in Criminology and International Security in addition to her bachelor’s degree in Foreign Languages. She enjoys the outdoors, animals, and sometimes asking a bit too many questions – to which she NEEDS to find the answers.
如有侵权请联系:admin#unsafe.sh