Key Takeaways Cybercriminals have leveraged the Sora branding to create convincing phishin 2024-8-1 01:1:33 Author: cyble.com(查看原文) 阅读量:93 收藏
Key Takeaways
- Cybercriminals have leveraged the Sora branding to create convincing phishing sites, demonstrating their strategic use of popular or anticipated technologies to deceive users
- The targeting of an unreleased Sora application suggests that cybercriminals are actively seeking new and emerging technologies to exploit, even before they are officially available to the public.
- The campaigns show a high level of sophistication, with Threat Actors (TAs) employing multiple vectors, such as phishing sites and compromised social media accounts, to maximize their reach and effectiveness.
- By utilizing compromised social media accounts to promote fake platforms and distribute phishing links, the TAs increase the perceived legitimacy of their phishing schemes, making them more likely to succeed.
- The information-stealer malware used in these campaigns employs techniques that successfully evade detection by mainstream antivirus solutions, highlighting the need for advanced security measures.
- After exfiltrating the data, TAs deploy open-source mining software like XMRig and lolMiner, indicating a dual objective of both data theft and cryptocurrency mining to monetize their activities further.
Overview
In February, OpenAI introduced Sora, an advanced AI model set to revolutionize content creation by producing realistic and imaginative scenes from textual descriptions. This groundbreaking technology promises to transform how users generate and visualize content, facilitating the realization of complex and creative ideas. As the tech community eagerly awaits Sora’s official release, the excitement has been accompanied by a surge in malicious activity.
Despite Sora’s yet-to-be-launched status, cybercriminals have already targeted it, creating numerous phishing sites that impersonate official Sora platforms to trick users and distribute various forms of malware.
After the announcement of Sora, Cyble Research and Intelligence Labs (CRIL) observed several phishing sites that mimic Sora and deploy different types of malware families.
Below is the list of phishing sites:
- hxxps://sorics-ai[.]web.app
- hxxps://sora-6b494[.]web.app
- hxxps://sorics-ai.web[.]app
- hxxps://soraai-pro-kit[.]web.app
- hxxps://sora-openai-generation[.]com
- hxxps://openai-soravideo[.]com
- hxxps://opensora-ai.web[.]app
- hxxps://opensora[.]info

Figure 1 – Phishing site impersonating Sora
On July 22, 2024, we identified a phishing site, “openai-soravideo[.]com,” which was created on July 20, 2024. Shortly after its creation, on July 21, 2024, the threat actor began using a compromised social media account to promote Sora AI and distribute the phishing site, aiming to deliver malware.

Figure 2 – Compromised social media page with high follower count promoting Sora via a phishing site

Figure 3 – Post on compromised social media page
While investigating this compromised page, we discovered several other compromised social media pages with the name “Sora AI – Creating Video From Text.” These pages were distributing numerous phishing sites impersonating Sora and delivering malware.

Figure 4 – Compromised pages distributing phishing sites
On OpenAI’s community page, numerous users reported falling victim to this campaign by downloading malware. Many were directed to phishing sites through ads for Sora promoted by the threat actor, resulting in data compromise. We observed that few downloaded zip files had zero detections, and antivirus software failed to identify the malware when victims were infected.

Figure 5 – Zip file downloaded from phishing site “sorics-ai.web[.]app” with zero detection

Figure 6 – User posted about advertisement running phishing campaign on the Open AI community

Figure 7 – Users’ comments related to the Sora phishing campaign (Source – OpenAI community)
Campaign Analysis
We have identified multiple campaigns leveraging Sora-themed phishing websites as a vector for malware distribution. Our initial analysis suggests that a single TA may not necessarily orchestrate these campaigns. However, a commonality across these campaigns is the use of phishing sites that lure victims into downloading files disguised as legitimate Sora software. When users attempt to install these seemingly authentic applications, the files trigger malicious processes that compromise the victim’s system.
CRIL has identified a phishing website with the URL “hxxps[://]sora-openai-generation[.]com/,” which masquerades as a platform offering Sora AI services for converting video from text. The site is cleverly designed to deceive visitors into believing it provides legitimate services, encouraging them to click on a download button under the pretense of offering a free application. The sophistication of the disguise aims to lower users’ suspicions and increase the likelihood of them downloading the malicious software. The below figure shows the phishing Sora phishing site.

Figure 8- Phishing Site
After the victim clicks the download button, a zip file is downloaded containing an obfuscated batch script. This script runs several PowerShell commands to carry out malicious activities stealthily. Initially, it downloads another zip file from “hxxps[://]special-create-studio[.]com/studio.zip” and extracts its contents, including Python scripts, to the “C:/Users/Public/VIDEOHD” directory. It then executes a malicious Python file named “godady.py” from the extracted files, which serves as the primary malicious payload. The “godady.py” script employs multiple layers of compression, including zlib, bz2, gzip, and lzma, along with hexadecimal encoding to obscure its payload. The image below displays a code snippet of the malicious Python script.

Figure 9 – Layered decompression and Python payload extraction
The decompressed Python stealer, known as Braodo Stealer, targets six browsers—Chrome, Firefox, Edge, Opera, Brave, and Chromium—to extract sensitive information, including cookies, login credentials, web data, and local state. Once the data is collected, it is compressed into a ZIP archive and sent to two separate Telegram chat IDs via HTTP POST requests to the Telegram API. The image below illustrates how Telegram Bot IDs are used to transmit the stolen data.

Figure 10 – Braodo Stealer targets multiple browsers
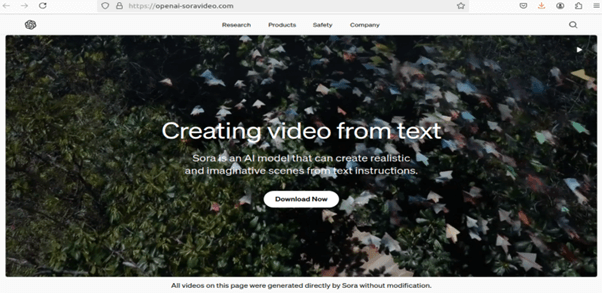
In another campaign, we’ve observed TAs using the phishing website “hxxps://openai-soravideo[.]com.” This website prompts users to download a zip file containing an executable. The infection begins when the user clicks on the executable file. The figure below shows the malicious website.

Figure 11 – Phishing site
The downloaded file performs multiple tasks related to information stealing. The image below outlines the operations carried out by this stealer.

Figure 12 – Core Functionality
The stealer can capture a wide spectrum of information, from screenshots to sensitive data such as login credentials, cookies, and autofill data from various browsers, including Microsoft Edge, Google Chrome, CocCoc, Brave, Opera, and Firefox.

Figure 13 – Targeted browsers
All the collected data from the targeted browsers is compressed into a zip file, which is named using the following format.
- <country id>_<botnet id>_<date time>.zip

Figure 14 – Zip File Creation
After creating the ZIP file, the stealer sends the data to the TA’s Telegram chat ID using the Telegram Bot API.

Figure 15 – TA’s Telegram Chat ID
Another notable campaign we’ve uncovered involves impersonating Sora. When users download a zip file from the phishing website, it contains a PyInstaller executable named “setup-x86_64.exe.” Upon execution, this executable runs a Python script protected by PyArmor, an obfuscation tool designed to hide the script’s true functionality. The malicious Python script’s primary action is to download a .bat file from the URL “https://sealingshop.click/bat/loc” and save it to the location “C:\Users\Public\manifest.bat.” Once downloaded, the Python script proceeds to execute the .bat file.

Figure 16 – Similar phishing website
Notably, the de-obfuscated PyArmor file includes code that performs screen capturing, interacts with the system’s mouse and keyboard, and potentially transmits data over a network. The figure below shows the partially de-obfuscated Python code to monitor the mouse events from the victim’s machine.

Figure 17 – Mouse Simulation Functionality
The executed batch file downloads a Python setup and runs a malicious script named “document.py,” which is designed to collect sensitive information. This includes usernames, the victim’s IP address, and browser data such as cookies and login credentials from Chrome and Edge. Notably, the stealer is configured to exclude users from certain countries, preventing infection in those regions.
The stealer sends all collected information in JSON format to a ngrok domain (hxxps://f34f-103-14-48-195.ngrok-free.app) via a POST request. Following data exfiltration, the stealer downloads and installs two open-source miners, XMRig and lolMiner, on the victim’s machine.

Figure 18 – Code snippet for downloading and executing miners
Conclusion
The Sora-themed campaigns highlight a concerning trend in cyber threats, showcasing the adaptation and creativity of TAs. By exploiting the anticipation surrounding OpenAI’s Sora, TAs have crafted sophisticated phishing sites and malware disguised as legitimate software. These campaigns use compromised social media accounts and deceptive tactics to distribute harmful payloads, including data stealers and cryptocurrency miners. The obfuscation methods employed, such as layered compression and disguised executables, illustrate the advanced techniques used to evade detection and maximize impact.
Recommendations
Here are some recommendations to mitigate and respond to malware campaigns exploiting the Sora theme:
- Educate users about phishing scams and the risks of downloading software from unverified sources. Emphasize the importance of verifying URLs and checking for signs of legitimacy before downloading or installing applications.
- Implement advanced threat detection solutions, including updated antivirus software and intrusion detection systems, to identify and block malicious activities.
- Actively monitor social media platforms for compromised accounts promoting malicious content. Quickly respond to and report suspicious activities to prevent further spread.
- Enforce MFA across all accounts and systems to add an extra layer of security and reduce the risk of unauthorized access.
- Regularly back up critical data and ensure that backups are stored securely. Test the restoration process to ensure data can be quickly recovered in case of a ransomware attack.
- Use web filtering solutions to block access to known malicious sites and prevent users from downloading harmful files.
MITRE ATT&CK® Techniques
| Tactics | Techniques | Procedure |
| Execution (TA0002) | User Execution: Malicious Link (T1204.001) | execution begins when a user downloads a zip file from a phishing website |
| Execution (TA0002) | User Execution: Malicious File (T1204.002) | The victim is required to execute the .bat or .exe from zip file |
| Execution (TA0002) | Command and Scripting Interpreter: PowerShell (T1059.001) | Batch script uses PowerShell to execute commands |
| Command and Control (TA0011) | Ingress Tool Transfer (T1105) | script downloads files from remote servers |
| Command and Control (TA0011) | Application Layer Protocol: Web Protocols (T1071.001) | use of HTTPS for downloading files |
| Defense Evasion (TA0005) | Obfuscated Files or Information: Binary Padding (T1027.001) | Null characters added in the exe |
| Defense Evasion (TA0005) | Obfuscated Files or Information: Command Obfuscation (T1027.010) | Downloads base64 encoded python script |
| Defense Evasion (TA0005) | Masquerading: Match Legitimate Name or Location (T1036.005) | Malicious files are disguised with names like “OpenAI” or “GoDaddy” to appear legitimate |
| Collection (TA0009) | Data from Local System (T1005) | Exfiltrate data from browser database files |
| Exfiltration (TA0010) | Automated Exfiltration (T1020) | Data is exfiltrated after collection |
| Exfiltration (TA0010) | Exfiltration Over Web Service (T1567) | Telegram API and ngrok used for data exfiltration |
IOCs
| Indicators | Indicator Type | Description |
| hxxps[://]sora-openai-generation[.]com/ | URL | Phishing site |
| f371955bb96fa9aeefc5a6f2b9140100821ac3ab9e04a229c2184e1ea2551392 | SHA256 | Manual_installer_Sora_OpenaiPro_v4.1.zip |
| 8a307a9c08b38946fd124de1ddccbdbbe706589580dabc078b7009689e209248 | SHA256 | setup_soraai_pro_v4.2.zip |
| 114d633c45a845dbef182462aab6ec03fa5d0cf3271e61272a7e37dd94ec9865 | SHA256 | Manual_installer_Sora_OpenaiPro_v4.1.bat |
| f8ad660704b998733c33cab8caaff4304608aea29ec348bbecfb084875bd9c27 | SHA256 | setup_soraai_pro_v4.2.bat |
| d7025e1ee86815374bc13d1bf6b5351205428b31a70048b1ea5c1308c3bf1a96 8ef6934bd42de33ed4d9e40e9ed3ee8d980112be372fe5e5aac2290ee74590fb | SHA256 | VIDEOHD.zip |
| 29f34032457b4af0b806c502a4394bbf499a9c1af6dfe06b46d40121e76f9a27 | SHA256 | Run batch script |
| 3b792058454ea7824a5341905bd3d65aa58898c6fe26305bbc59c3801aba161b | SHA256 | Setup-Createstudio.bat |
| 028004fadc270c7892303156fb9e9a3d8edb241b4d51cdb319bd275fbc7fe047 | SHA256 | Braodo Stealer |
| hxxps[://]sorics-ai[.]web.app/ | URL | Phishing site |
| 64ac9fd8a09929afa0e65130ff3d494296559190a0d16fdb87cb6ace282166b6 | SHA256 | setup-x86_64.zip |
| 6bfb47fd85a099b5bb6bbcbd559373659f7a12cd4bb9e493a9b5e9046026b6dc | SHA256 | setup-x86_64.bat |
| 41a9c3bc563d03c73755e314c05d414886af587b9cdc1bb0339b86107443dbd1 | SHA256 | python39.zip |
| c355806ac67ea8f79c984ef255b3b363607555100604e4f109fd1e0a9d518af4 | SHA256 | xmrig3.zip |
| f3e46db62fe954be9c0403854722a04d07bb521114709e426f842fd74418619e | SHA256 | lolMiner.zip |
| hxxps[://]soraai-pro-kit[.]web[.]app/ | URL | Phishing site |
| 831f0474c8048992edf1e19c46a6de1784aa86b17752a35e816bb128d8240091 | SHA256 | setup-x86_64.zip |
| 2c33b80b51c8ba0971117a60627a6920f557a99c8e4aa5a0382358a66fa25a52 | SHA256 | setup-x86_64.exe |
| hxxps[://]openai-soravideo[.]com/ | URL | Phishing site |
| aab58fa552f5acfd3c7001b7ddb05cdb553d1f1d42733b0446052dad9c476e1c | SHA256 | Open AI Sora 4.0 Version 4.56.zip |
| 898fa8ead5fcab0f0f64fbc57d8ca73bad4947352318dca75b359e677e71e931 | SHA256 | Open AI Sora 4.0 Version 4.56.exe |
| hxxps[://]sora-6b494[.]web[.]app hxxps[://]sorics-ai[.]web[.]app hxxps[://]opensora-ai.web[.]app hxxps[://]opensora[.]info | URL | Phishing sites |
| hxxps[://]special-create-studio[.]com/loki/fileavu hxxps[://]special-create-studio[.]com/run hxxps[://]special-create-studio[.]com/loki/soraavu[.]zip hxxps[://]special-create-studio[.]com/studio[.]zip hxxps[://]special-create-studio[.]com/run | URL | Malicious URL |
| hxxps[://]sealingshop[.]click/pyen/adsteam hxxps[://]sealingshop[.]click/bat/adsteam hxxps[://]sealingshop[.]click/config/stu hxxps[://]sealingshop[.]click/app/python39[.]zip hxxps[://]sealingshop[.]click/py/adsteam hxxps[://]sealingshop[.]click/host/adsteam hxxps[://]sealingshop[.]click/miner/c hxxps[://]sealingshop[.]click/miner/g | URL | Malicious URLs |
| f34f-103-14-48-195[.]ngrok-free[.]app | Domain | ngrok domain |
Related
如有侵权请联系:admin#unsafe.sh